Suricata/Installation-and-basic-configuration/Alternate-Installation
Jump to navigation
Jump to search
| You are here: | Alternate installation: Security Onion
|
Description
Security Onion LiveDVD "is a bootable DVD that contains software used for installing, configuring, and testing Intrusion Detection Systems. It is based on Xubuntu 10.04 and contains Snort, Suricata, Sguil, Squert, Xplico, nmap, metasploit, Armitage, scapy, hping, netcat, tcpreplay, and many other security tools." It makes setting up Suricata very easy.
Download
Download the latest Security Onion .iso file from here: http://sourceforge.net/projects/security-onion/files/ and write the iso to a DVD.
Setup
- It is recommended that you install Security Onion to your harddrive
- After installation, double click on the "Setup" icon on the desktop
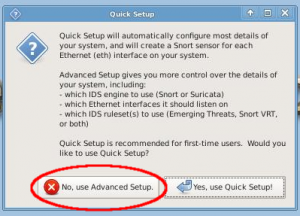
- Choose "No, use Advanced Setup"
- Add the primary username and password you want to use for Sguil when prompted
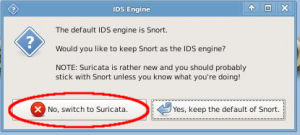
- Choose "No switch to Suricata" when asked about default IDS Engine
- Choose which interface you want Suricata to listen on (ie. eth0)
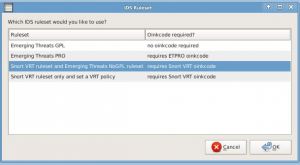
- Choose which IDS ruleset you would like to use. We recommend "Snort VRT ruleset and Emerging Threats NoGPL ruleset"
If you choose this option, you will need a Snort VRT oinkcode. If you do not already have one, you can signup for one here: https://www.snort.org/login
- After entering your Snort oinkcode, setup will then ask you to confirm the changes it's about to make. If you are ok with this, choose "Yes, proceed with the changes!"
- If everything went ok, you will receive a confirmation message that Security Onion setup is complete
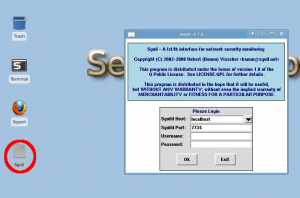
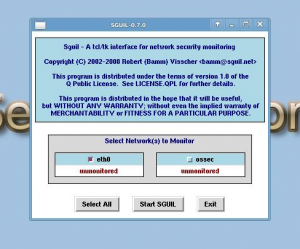
- Now click the "Sguil" icon on the desktop and login with the account info you created during setup
- Now select the network that you want to monitor, for example, if you chose eth0 during the Security Onion setup, then you want to choose "eth0" here. Choose "Start SGUIL"
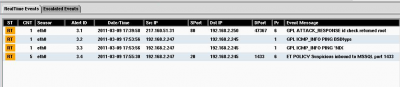
- If you did everything right, you should now receive events under the "RealTime Events" tab. You will want to generate some traffic to cause an alarm. We recommend using [Scapy]. Here is a command "sr1(IP(dst="192.168.1.1")/TCP(dport=1433)/"0"*1000)" that you can use that will generate the alert "ET Policy Suspicious inbound to MSSQL port 1433" if everything is configured correctly
- You can also use the web interface "Squert" by clicking on the icon on the desktop
Configuration Files
Here are where some of the important configuration files are located in Security Onion:
- Suricata config files are located: /etc/nsm/<interface>
- Suricata log file is located: /nsm/sensor_data/<interface> directory
- Suricata rule directory: /etc/nsm/rules/