Sysinternals/Pstools/PsExec
Jump to navigation
Jump to search
| You are here: | PsExec
|
Description
PsExec is part of the PsTools toolkit developed by Sysinternals. It enables to remotely execute commands on a Windows machine (e.g. Windows XP) from another Windows machine (e.g. Windows 7).
Installation
PsExec is part of the PsTools suite. To install it, please refer to this section.
Usage
Syntax
Usage: psexec [\\computer[,computer2[,...] | @file]][-u user [-p psswd][-n s][-l] [-s|-e][-x][-i [session]][-c [-f|-v]][-w directory][-d][-<priority>] [-a n,n,...] cmd [arguments]
Options
- -a
- Separate processors on which the application can run with commas where 1 is the lowest numbered CPU. For example, to run the application on CPU 2 and CPU 4, enter: "-a 2,4"
- -c
- Copy the specified program to the remote system for execution. If you omit this option the application must be in the system path on the remote system.
- -d
- Don't wait for process to terminate (non-interactive).
- -e
- Does not load the specified account's profile.
- -f
- Copy the specified program even if the file already exists on the remote system.
- -i
- Run the program so that it interacts with the desktop of the specified session on the remote system. If no session is specified the process runs in the console session.
- -h
- If the target system is Vista or higher, has the process run with the account's elevated token, if available.
- -l
- Run process as limited user (strips the Administrators group and allows only privileges assigned to the Users group).
- On Windows Vista the process runs with Low Integrity.
- -n
- Specifies timeout in seconds connecting to remote computers.
- -p
- Specifies optional password for user name. If you omit this you will be prompted to enter a hidden password.
- Note that the password is transmitted in clear text to the remote system.
- -s
- Run the remote process in the System account.
- -u
- Specifies optional user name for login to remote computer.
- Specify a valid user name in the Domain\User syntax if the remote process requires access to network resources or to run in a different account.
- -v
- Copy the specified file only if it has a higher version number or is newer on than the one on the remote system.
- -w
- Set the working directory of the process (relative to remote computer).
- -x
- Display the UI on the Winlogon secure desktop (local system only).
- -priority
- Specifies -low, -belownormal, -abovenormal, -high or -realtime to run the process at a different priority. Use -background to run at low memory and I/O priority on Vista.
- computer
- Direct PsExec to run the application on the remote computer or computers specified. If you omit the computer name PsExec runs the application on the local system, and if you specify a wildcard (\\*), PsExec runs the command on all computers in the current domain.
- @file
- PsExec will execute the command on each of the computers listed in the file.
- program
- Name of application to execute.
- You can enclose applications that have spaces in their name with quotation marks e.g. psexec \\marklap "c:\long name app.exe".
- arguments
- Arguments to pass (note that file paths must be absolute paths on the target system).
Examples
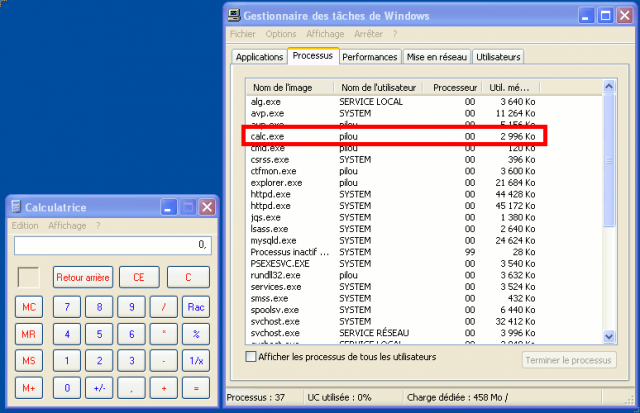
Interactive mode: remotely start calc.exe
Following command will start calc.exe in interactive mode on the targeted device:
C:\pstools>psexec \\192.168.1.27 -u pilou -p oopsoops -i "c:\windows\system32\calc.exe" PsExec v1.98 - Execute processes remotely Copyright (C) 2001-2010 Mark Russinovich Sysinternals - www.sysinternals.com
Non interactive mode: antivirus status
C:\pstools>psexec \\192.168.1.27 -u pilou -p oopsoops "C:\Program Files\Kaspersky Lab\Kaspersky Internet Security 2012\avp.com" STATUS PsExec v1.98 - Execute processes remotely Copyright (C) 2001-2010 Mark Russinovich Sysinternals - www.sysinternals.com Starting C:\Program Files\Kaspersky Lab\Kaspersky Internet Security 2012\avp.com Task State Completion Description --------------------------------------------------------------------- AdBlocker disabled AdBlockService stopped AdvDis stopped Anti_Spam stopped AntiPhishingEx stopped AntiPhishingService stopped AppCat stopped AVService running AVZ_PrivacyCleaner stopped AVZ_RunScript stopped AVZ_Scan_Vulnerabilities stopped AVZ_SecurityTweaker stopped Avz_Troubleshoot stopped CfResponseProvider stopped CustomUrlProcess stopped File_Monitoring stopped Firewall stopped FTP stopped Geo_Security stopped GreenZone stopped Hips stopped HipsRequester stopped HipsTask stopped HTTP stopped httpscan stopped ICQ stopped ids stopped IM_Monitoring stopped IMAP stopped IRC stopped Jabber stopped KASFltService stopped KSN running KSN_client stopped LocalizationManager stopped Mail_Monitoring stopped MMP stopped MSN stopped NetDetails stopped NetWatch running NNTP stopped OnlineBanking stopped ParCtl disabled ParCtlService_Filters stopped ParCtlService_Time stopped ParCtlService_URL stopped ParCtlService_Words stopped pdm stopped POP3 stopped ProcMon running Protection stopped QB stopped RDUpdater stopped Rollback stopped RollbackPatch stopped SafeSearch stopped SandBox running sc stopped Scan_IdleScan completed Scan_My_Computer completed Scan_Objects stopped Scan_Qscan completed Scan_Quarantine completed Scan_Startup stopped Scan_Vulnerabilities stopped SMTP stopped SNA stopped SW2 stopped SW2U stopped ThreatsDisinfector stopped TimeControl stopped TrafficMonitor stopped UDS stopped Updater stopped VerCheck completed VirtualKeyboard stopped Web_Monitoring stopped WebNetStat stopped WebToolBar stopped WMUF stopped YHO stopped C:\Program Files\Kaspersky Lab\Kaspersky Internet Security 2012\avp.com exited on 192.168.1.27 with error code 0.
Run a shell like a telnet session
Psexec has the ability to run a shell like if you were connected via a telnet session.
The machine from which psexec is run has the IP 192.168.1.2:
C:\pstools>ipconfig | find "192.168.1"
Adresse IPv4. . . . . . . . . . . . . .: 192.168.1.2
192.168.1.254
Now, let's remotely connect to host 192.168.1.27 and run a remote prompt:
C:\Users\william>psexec \\192.168.1.27 -u pilou -p oopsoops cmd
PsExec v1.98 - Execute processes remotely
Copyright (C) 2001-2010 Mark Russinovich
Sysinternals - www.sysinternals.com
Microsoft Windows XP [version 5.1.2600]
(C) Copyright 1985-2001 Microsoft Corp.
C:\WINDOWS\system32>ipconfig | find "192.168.1"
Adresse IP. . . . . . . . .á. . . : 192.168.1.27
Passerelle par dÚfaut . . .á. . . : 192.168.1.254
Run a program on multiple computers
Now, let's say you want to run a removal tool (let's say the remote computers are infected) on 2 computers and log the output to results.log, just issue following command;
C:\pstools>psexec \\192.168.1.26,192.168.1.27 -c removal.exe -s 2> results.log