The-FLARE-On-Challenge-01/Challenge-1
| You are here | Challenge 1
|
Uncompress
The individual file is available here: http://www.flare-on.com/files/C1.exe
It is mentionned on the flare-on.com website that "the first challenge is a self-extracting zip file that requires you to accept the EULA before continuing".
You can uncompress it using 7zip:
$ 7z x C1.exe 7-Zip [64] 9.20 Copyright (c) 1999-2010 Igor Pavlov 2010-11-18 p7zip Version 9.20 (locale=fr_FR.utf8,Utf16=on,HugeFiles=on,4 CPUs) Processing archive: C1.exe Extracting Challenge1.exe Everything is Ok Size: 120832 Compressed: 285184 $ md5sum * 4121e589529626fb14feafb828619286 C1.exe 66692c39aab3f8e7979b43f2a31c104f Challenge1.exe
What does it look like?
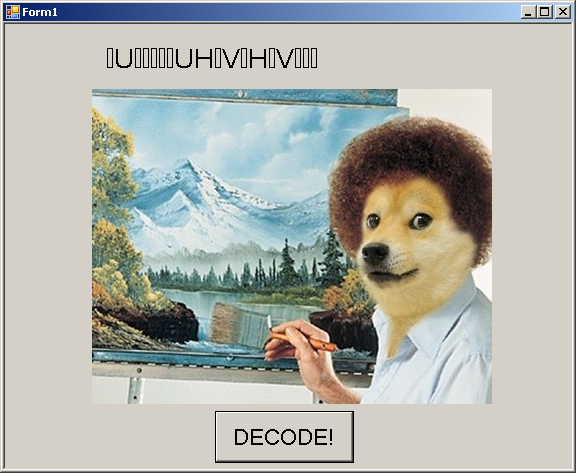
When we start the uncompressed executable (Challenge1.exe), we see the below window:
If we press the "Decode" button, the window becomes:
We have to identify the code that is behind the "Decode" button.
Decompile the .Net
A simple "file" command informs us we have to handle a .Net executable:
$ file /data/tmp/challenge1/Challenge1.exe /data/tmp/challenge1/Challenge1.exe: PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows
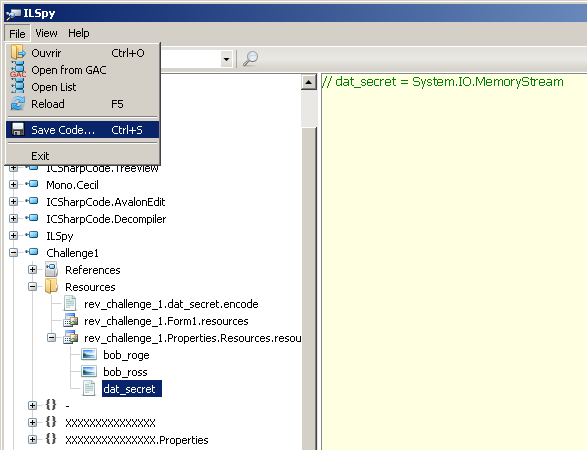
Let's download ILSpy, an open-source .NET assembly browser and decompiler.
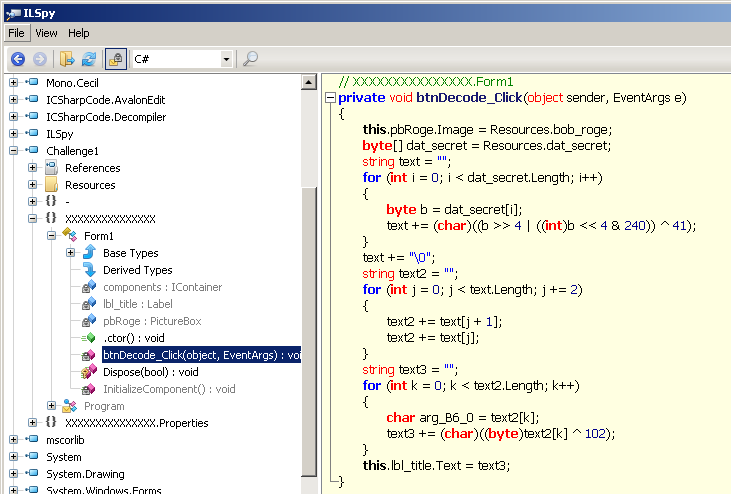
The code associated to the button is in the btnDecode_Click function:
We see that it processes a file named "dat_secret", available from the "Resources" section. Let's save this file
Decode dat_secret
Now, let's decode the resource. It can be easily achieved with the following lines of python:
#!/usr/bin/env python
ba = bytearray(open('dat_secret', 'rb').read())
print ''.join(chr((b >> 4 | (b << 4 & 240)) ^ 41) for b in ba)
Solution to challenge 1
The solution to challenge one is:
[email protected]
Comments
Keywords: reverse-engineering challenge flare fireeye