The-FLARE-On-Challenge-2015/Challenge-1
| You are here | Challenge 1
|
File
The first level can be downloaded here. It is a Win32 Cabinet Self-Extractor archive. All you need to do is to launch the executable, accept the EULA and choose a destination folder where the executable to analyze will be uncompressed.
The uncompressed file name is i_am_happy_you_are_to_playing_the_flareon_challenge.exe.
| MD5 | 7c0f16de595ae03e2928d3fa6b73b235 |
|---|---|
| SHA1 | 150e2be31483d1d7942bb0727479cc493d3e85d3 |
| SHA256 | 5d35789ac904bc5f4639119391ad1078f267a157ca153f2906f05df94e557e11 |
The executable imports following functions from kernel32.dll:
When we open the executable into IDA-Pro, we get a message that could be an indication that the executable is packed. However, it is not and we can easily locate the cross reference to the strings "You are success" and "You are failure":
Code analysis
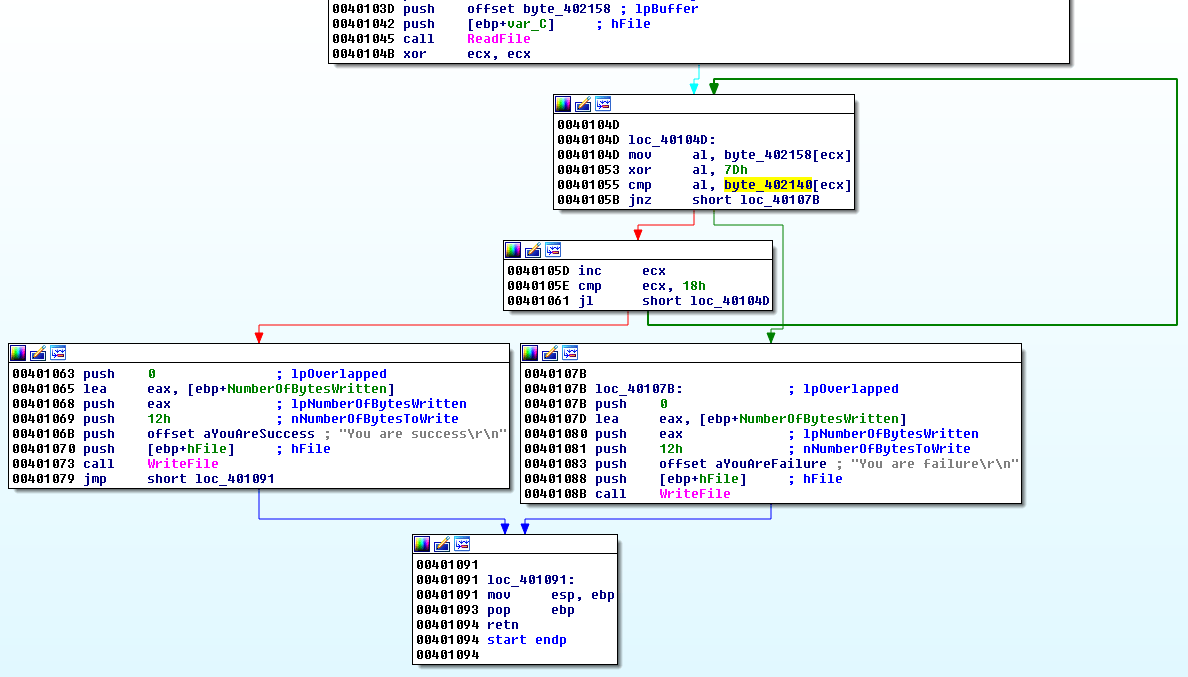
The user input is read by ReadFile at offset 0x401045 and saved to a buffer (byte_402158):
.text:0040103A push eax ; lpNumberOfBytesRead
.text:0040103B push 32h ; nNumberOfBytesToRead
.text:0040103D push offset byte_402158 ; lpBuffer
.text:00401042 push [ebp+var_C] ; hFile
.text:00401045 call ReadFile ; Read user input
Then, there is a loop that reads each character of this buffer and XOR's them with the key 0x7D
.text:0040104B xor ecx, ecx ; Set ECX to 0 (counter)
.text:0040104D
.text:0040104D loc_40104D:
.text:0040104D mov al, byte_402158[ecx] ; Save character of user input to AL
.text:00401053 xor al, 7Dh ; XOR's character with 0x7D
.text:00401055 cmp al, byte_402140[ecx] ; Compare XOR result with expected value at byte_402140[ecx]
.text:0040105B jnz short loc_40107B ; if not equal, exit loop
.text:0040105D inc ecx ; increment counter
.text:0040105E cmp ecx, 18h ; Loop thru 24 characters
And below is the content of the expected values:
.data:00402140 byte_402140 db 1Fh
.data:00402141 db 8
.data:00402142 db 13h
.data:00402143 db 13h
.data:00402144 db 4
.data:00402145 db 22h ; "
.data:00402146 db 0Eh
.data:00402147 db 11h
.data:00402148 db 4Dh ; M
.data:00402149 db 0Dh
.data:0040214A db 18h
.data:0040214B db 3Dh ; =
.data:0040214C db 1Bh
.data:0040214D db 11h
.data:0040214E db 1Ch
.data:0040214F db 0Fh
.data:00402150 db 18h
.data:00402151 db 50h ; P
.data:00402152 db 12h
.data:00402153 db 13h
.data:00402154 db 53h ; S
.data:00402155 db 1Eh
.data:00402156 db 12h
.data:00402157 db 10h
Script and solution
Here is the script I've written to solve this challenge:
#!/usr/bin/env python
s = [0x1F,0x8,0x13,0x13,0x4,0x22,0x0E,0x11,0x4D,0x0D,0x18,0x3D,0x1B,0x11,0x1C,0x0F,0x18,0x50,0x12,0x13,0x53,0x1E,0x12,0x10]
print ''.join([chr(i ^ 0x7d) for i in s])
Execute it to solve this challenge:
$ ./script.py [email protected]
Just send a mail to this email address and you will receive the following answer along with a 728 bytes attachment:
Congrats! I've attached the next challenge for your reversing pleasure. The password to this zip archive is "flare". This challenge looks a lot like the last one so hopefully you'll knock this one out too, Good luck! -FLARE
Comments
Keywords: reverse-engineering challenge flare fireeye