W3AF:Utilisation console
Utilisation
Modes d'utilisation
- Mode console : w3af_console
- Mode graphique : w3af_gui
Mode console
Lancer W3AF en mode console
Pour lancer W3AF, il suffit d'entrer les commandes suivantes :
# cd /usr/local/w3af/ # ./w3af_console
Afficher l'aide
Une fois dans W3AF, il est possible d'afficher l'aide sur le répertoire courant avec la commande help :
w3af>>> help |-----------------------------------------------------------------------------| | start | Start the scan. | | plugins | Enable and configure plugins. | | exploit | Exploit the vulnerability. | | profiles | List and use scan profiles. | |-----------------------------------------------------------------------------| | http-settings | Configure the HTTP settings of the framework. | | misc-settings | Configure w3af misc settings. | | target | Configure the target URL. | |-----------------------------------------------------------------------------| | back | Go to the previous menu. | | exit | Exit w3af. | | assert | Check assertion. | |-----------------------------------------------------------------------------| | help | Display help. Issuing: help [command] , prints more | | | specific help about "command" | | version | Show w3af version information. | | keys | Display key shortcuts. | |-----------------------------------------------------------------------------|
Il est possible d'obtenir de l'aide sur un paramètre comme suit :
w3af>>> help plugins Enable and configure plugins.

Naviguer dans les menus de configuration
Entrer dans un menu
Pour entrer dans un menu, il suffit d'entrer le nom du menu comme suit :
w3af>>> http-settings
Dans les menus de configuration, les options disponibles sont les suivantes :
w3af/config:http-settings>>> help |-----------------------------------------------------------------------------| | view | List the available options and their values. | | set | Set a parameter value. | |-----------------------------------------------------------------------------| | back | Go to the previous menu. | | exit | Exit w3af. | | assert | Check assertion. | |-----------------------------------------------------------------------------|
Il est possible d'obtenir la liste des paramètres et leurs valeurs pour chaque paramètre :
w3af/config:http-settings>>> view |----------------------------------------------------------------------------| | Setting | Value | Description | |----------------------------------------------------------------------------| | timeout | 10 | The timeout for | | | | connections to the | | | | HTTP server | | headersFile | | Set the headers | | | | filename. This file | | | | has additional headers | | | | that are added to each | | | | request. | |----------------------------------------------------------------------------| | ignoreSessCookies | False | Ignore session cookies | | cookieJarFile | | Set the cookiejar | | | | filename. | |----------------------------------------------------------------------------| | maxFileSize | 400000 | Maximum file size | | userAgent | w3af.sourceforge.net | User Agent header | | maxRetrys | 2 | Maximum number of | | | | retries | |----------------------------------------------------------------------------| | byDirectoryAndExtension404 | True | Perform 404 page | | | | detection based on the | | | | knowledge found in the | | | | directory of the file | | | | AND the file extension | | always404 | | A comma separated list | | | | that determines what | | | | URLs will ALWAYS be | | | | detected as 404 pages. | | autodetect404 | False | Perform 404 page | | | | autodetection. | | byDirectory404 | False | Perform 404 page | | | | detection based on the | | | | knowledge found in the | | | | directory of the file | | 404exceptions | | A comma separated list | | | | that determines what | | | | URLs will NEVER be | | | | detected as 404 pages. | |----------------------------------------------------------------------------| | proxyPort | 8080 | Proxy TCP port | | proxyAddress | | Proxy IP address | |----------------------------------------------------------------------------| | basicAuthUser | | Set the basic | | | | authentication | | | | username for HTTP | | | | requests | | basicAuthPass | | Set the basic | | | | authentication | | | | password for HTTP | | | | requests | | basicAuthDomain | | Set the basic | | | | authentication domain | | | | for HTTP requests | |----------------------------------------------------------------------------|
Revenir au niveau inférieur
Pour revenir à un niveau inférieur de menu, utiliser la commande back.
w3af/config:http-settings>>> back w3af>>>
Modifier la valeur d'un paramètre
Pour modifier la valeur d'un paramètre, utiliser le mot clé set. L'exemple qui suit montre comment paramétrer un proxy avec authentification.
Valeur des paramètres avant la modification :
|----------------------------------------------------------------------------| | proxyPort | 8080 | Proxy TCP port | | proxyAddress | | Proxy IP address | |----------------------------------------------------------------------------| | basicAuthUser | | Set the basic | | | | authentication | | | | username for HTTP | | | | requests | | basicAuthPass | | Set the basic | | | | authentication | | | | password for HTTP | | | | requests | | basicAuthDomain | | Set the basic | | | | authentication domain | | | | for HTTP requests | |----------------------------------------------------------------------------|
Modification de la valeur des paramètres :
w3af/config:http-settings>>> set proxyPort 3128 w3af/config:http-settings>>> set proxyAddress 192.168.1.1 w3af/config:http-settings>>> set basicAuthUser myuser To properly configure the basic authentication settings, you should also set the auth domain. If you are unsure, you can set it to the target domain name. w3af/config:http-settings>>> set basicAuthPass myP4ssw0rd To properly configure the basic authentication settings, you should also set the auth domain. If you are unsure, you can set it to the target domain name. w3af/config:http-settings>>> set basicAuthDomain aldeid.com

Valeur des paramètres après la modification :
|----------------------------------------------------------------------------| | proxyPort | 3128 | Proxy TCP port | | proxyAddress | 192.168.1.1 | Proxy IP address | |----------------------------------------------------------------------------| | basicAuthUser | myuser | Set the basic | | | | authentication | | | | username for HTTP | | | | requests | | basicAuthPass | myP4ssw0rd | Set the basic | | | | authentication | | | | password for HTTP | | | | requests | | basicAuthDomain | aldeid.com | Set the basic | | | | authentication domain | | | | for HTTP requests | |----------------------------------------------------------------------------|
Sélectionner et paramétrer des plugins
Obtenir des informations sur un plugin
Pour obtenir des informations complémentaires sur un plugin, utilisez le mot clé desc :
w3af/plugins>>> audit desc blindSqli
This plugin finds blind SQL injections.
Two configurable parameters exist:
- equAlgorithm
- equalLimit
The equAlgorithm parameter configures how the comparison of pages is done, the options for equAlgorithm are:
- stringEq
- setIntersection
The classic way of matching two strings is "stringEq" , in Python this is "string1 == string2" , but other ways have been
developed for sites that have changing banners and random data on their HTML response. "setIntersection" will create
two different sets with the words inside the two HTML responses, and do an intersection. If number of words that are
in the intersection set divided by the total words are more than "equalLimit", then the responses are equal.
Sélectionner des plugins
Rendez-vous dans le menu plugins
w3af>>> plugins
Puis utilisez l'aide afin de lister les familles de plugins
w3af/plugins>>> help |-----------------------------------------------------------------------------| | list | List available plugins. | |-----------------------------------------------------------------------------| | back | Go to the previous menu. | | exit | Exit w3af. | | assert | Check assertion. | |-----------------------------------------------------------------------------| | grep | View, configure and enable grep plugins | | mangle | View, configure and enable mangle plugins | | output | View, configure and enable output plugins | | evasion | View, configure and enable evasion plugins | | bruteforce | View, configure and enable bruteforce plugins | | discovery | View, configure and enable discovery plugins | | audit | View, configure and enable audit plugins | |-----------------------------------------------------------------------------|
Pour obtenir la liste des plugins associés à la famille de plugins retenue, utilisez le mot clé list :
w3af/plugins>>> list audit |----------------------------------------------------------------------------| | Plugin name | Status | Conf | Description | |----------------------------------------------------------------------------| | LDAPi | | | Find LDAP injection bugs. | | blindSqli | | Yes | Find blind SQL injection | | | | | vulnerabilities. | | buffOverflow | | | Find buffer overflow vulnerabilities. | | dav | | | Verify if the WebDAV module is | | | | | properly configured. | | eval | | Yes | Find insecure eval() usage. | | fileUpload | | Yes | Uploads a file and then searches for | | | | | the file inside all known directories. | | formatString | | | Find format string vulnerabilities. | | frontpage | | Yes | Tries to upload a file using frontpage | | | | | extensions (author.dll). | | generic | | Yes | Find all kind of bugs without using a | | | | | fixed database of errors. | | globalRedirect | | | Find scripts that redirect the browser | | | | | to any site. | | htaccessMethods | | | Find misconfigurations in the | | | | | "<LIMIT>" configuration of Apache. | | localFileInclude | | | Find local file inclusion | | | | | vulnerabilities. | | mxInjection | | | Find MX injection vulnerabilities. | | osCommanding | | | Find OS Commanding vulnerabilities. | | phishingVector | | | Find phishing vectors. | | preg_replace | | | Find unsafe usage of PHPs | | | | | preg_replace. | | remoteFileInclude | | Yes | Find remote file inclusion | | | | | vulnerabilities. | | responseSplitting | | | Find response splitting | | | | | vulnerabilities. | | sqli | | | Find SQL injection bugs. | | ssi | | | Find server side inclusion | | | | | vulnerabilities. | | sslCertificate | | | Check the SSL certificate validity( if | | | | | https is being used ). | | unSSL | | | Find out if secure content can also be | | | | | fetched using http. | | xpath | | | Find XPATH injection vulnerabilities. | | xsrf | | | Find the easiest to exploit xsrf | | | | | vulnerabilities. | | xss | | Yes | Find cross site scripting | | | | | vulnerabilities. | | xst | | | Find Cross Site Tracing | | | | | vulnerabilities. | |----------------------------------------------------------------------------|
Enfin, pour sélectionner des plugins, utilisez la commande suivante :
w3af/plugins>>> audit LDAPi,blindSqli,buffOverflow w3af/plugins>>> audit |----------------------------------------------------------------------------| | Plugin name | Status | Conf | Description | |----------------------------------------------------------------------------| | LDAPi | Enabled | | Find LDAP injection bugs. | | blindSqli | Enabled | Yes | Find blind SQL injection | | | | | vulnerabilities. | | buffOverflow | Enabled | | Find buffer overflow vulnerabilities. | | dav | | | Verify if the WebDAV module is | | | | | properly configured. | | eval | | Yes | Find insecure eval() usage. | | fileUpload | | Yes | Uploads a file and then searches for | | | | | the file inside all known | | | | | directories. | ...

Paramétrer des plugins
Pour paramétrer un plugin, utilisez le mot clé config :
w3af/plugins>>> audit config blindSqli
Tout comme pour le paramétrage de W3AF, utiliser les options :
- view : pour voir la valeur des paramètres
- set : Pour modifier la valeur d'un paramètre
L'exemple suivant montre comment modifier le paramètre checkStored du plugin xss :
w3af/plugins>>> audit config xss w3af/plugins/audit/config:xss>>> view |-----------------------------------------------------------------------------| | Setting | Value | Description | |-----------------------------------------------------------------------------| | numberOfChecks | 3 | Set the amount of checks to perform for each | | | | fuzzable parameter. Valid numbers: 1 to 14 | | checkStored | True | Identify stored cross site scripting | | | | vulnerabilities | |-----------------------------------------------------------------------------| w3af/plugins/audit/config:xss>>> set checkStored False w3af/plugins/audit/config:xss>>> view |-----------------------------------------------------------------------------| | Setting | Value | Description | |-----------------------------------------------------------------------------| | numberOfChecks | 3 | Set the amount of checks to perform for each | | | | fuzzable parameter. Valid numbers: 1 to 14 | | checkStored | False | Identify stored cross site scripting | | | | vulnerabilities | |-----------------------------------------------------------------------------|
Paramétrer et lancer le scan
Spécifier la cible
Avant d'exécuter le scan, spécifiez la cible comme suit :
w3af>>> target w3af/config:target>>> help |-----------------------------------------------------------------------------| | view | List the available options and their values. | | set | Set a parameter value. | |-----------------------------------------------------------------------------| | back | Go to the previous menu. | | exit | Exit w3af. | | assert | Check assertion. | |-----------------------------------------------------------------------------| w3af/config:target>>> view |------------------------------------------------------------------------------| | Setting | Value | Description | |------------------------------------------------------------------------------| | targetOS | unknown | Target operating system (unknown/unix/windows) | | targetFramework | unknown | Target programming framework | | | | (unknown/php/asp/asp.net/java/jsp/cfm/ruby/perl) | | target | | A comma separated list of URLs | |------------------------------------------------------------------------------| w3af/config:target>>> set target http://www.aldeid.com/ w3af/config:target>>> view |---------------------------------------------------------------------------------------------| | Setting | Value | Description | |---------------------------------------------------------------------------------------------| | targetOS | unknown | Target operating system (unknown/unix/windows) | | targetFramework | unknown | Target programming framework | | | | (unknown/php/asp/asp.net/java/jsp/cfm/ruby/perl) | | target | http://www.aldeid.com/ | A comma separated list of URLs | |---------------------------------------------------------------------------------------------|
Lancer le scan
Revenez au menu principal :
w3af/config:target>>> back
Enfin, exécutez le scan :
w3af>>> start Auto-enabling plugin: grep.error500 Found 2 URLs and 2 different points of injection. The list of URLs is: - http://www.aldeid.com/ - http://www.aldeid.com/index.php The list of fuzzable requests is: - http://www.aldeid.com/ | Method: GET - http://www.aldeid.com/index.php | Method: GET | Parameters: (search, title) Starting blindSqli plugin execution. ...
Découverte et exploitation de vulnérabilités
Découverte de vulnérabilité
Soit le code PHP suivant :
<html>
<body>
<?php
if(isset($_POST['v'])){
$v=$_POST["v"];
exec("grep $v /etc/passwd",$r);
echo("<pre style=\"border:solid 2px #ff0000;
background:#eeeeee;\">");
print_r($r);
echo("</pre>");
}
?>
<form method="post" action="index.php">
<input type="text" name="v" value="<?php
if(isset($_POST['v'])) { echo($_POST['v']); } ?>" />
<input type="submit" />
</form>
</body>
</html>
|
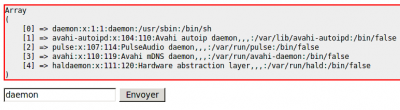
Ce code permet d'afficher les lignes du fichier /etc/passwd qui contiennent la chaîne fournie en paramètre. |
Tentons de découvrir si ce code est vulnérable :
# ./w3af_console w3af>>> plugins w3af/plugins>>> output console textFile w3af/plugins>>> audit osCommanding w3af/plugins>>> back w3af>>> target w3af/config:target>>> set target http://127.0.0.1/index.php w3af/config:target>>> back w3af>>> start Found 1 URLs and 2 different points of injection. The list of URLs is: - http://127.0.0.1/index.php The list of fuzzable requests is: - http://127.0.0.1/index.php | Method: GET - http://127.0.0.1/index.php | Method: POST | Parameters: (v) Starting osCommanding plugin execution. OS Commanding was found at: "http://127.0.0.1/index.php", using HTTP method POST. The sent post-data was: "v=%60+ping+-c+9+localhost%60". This vulnerability was found in the request with id 19. Finished scanning process.
Tout semble indiquer que le code est vulnérable.
Exploitation de vulnérabilité
Tentons maintenant d'exploiter la vulnérabilité découverte :