Write-AlienVault-Plugins
Introduction
Purpose
This document explains how to write a plugin for AlienVault in order to integrate logs from an external device (and for which a plugin does not exist yet) to generate SIEM events, and make correlation to generate alarms based on these events.
The current example is to integrate logs from a 3Com ADSL 11g WiFi router and write a correlation directive to track authentication bruteforce attempts.
Environment
In the current case here is our environment:
- Remote device: 3Com ADSL 11g WiFi router: 192.168.1.51
- AlienVault: all in one (sensor, SIEM, logger and collector): 192.168.1.2
Send syslog to AlienVault
Point to AlienVault device
First of all, set up your remote device to send syslogs to your AlienVault device (if you have separate boxes, point to the collector).
Once done, you should begin to see logs from the remote device in the syslog file:
# tail -f /var/log/syslog | grep 192\.168\.1\.51 Feb 12 21:02:59 192.168.1.51 3Com ADSL 11g[9]:192.168.1.29 login success Feb 12 22:39:16 192.168.1.51 3Com ADSL 11g[10]:User from 192.168.1.29 timed out Feb 12 23:37:32 192.168.1.51 3Com ADSL 11g[11]:192.168.1.29 login fail Feb 12 23:37:34 192.168.1.51 3Com ADSL 11g[12]:192.168.1.29 login fail Feb 12 23:37:38 192.168.1.51 3Com ADSL 11g[13]:192.168.1.29 login fail Feb 12 23:37:49 192.168.1.51 3Com ADSL 11g[14]:192.168.1.29 login success Feb 12 23:37:54 192.168.1.51 3Com ADSL 11g[15]:192.168.1.29 logout Feb 13 18:07:11 192.168.1.51 3Com ADSL 11g[16]:192.168.1.29 login fail Feb 13 18:07:14 192.168.1.51 3Com ADSL 11g[17]:192.168.1.29 login fail Feb 13 18:07:21 192.168.1.51 3Com ADSL 11g[18]:192.168.1.29 login fail
Log segregation
Now it’s time to segregate these logs in a separate file. This is achieved by a configuration file as follows:
alienvault:/etc/rsyslog.d# cat 3com-adsl-11g.conf if $fromhost-ip startswith '192.168.1.51' then /var/log/3com-adsl-11g.log

Log rotation
Ensure log rotation (example given for a weekly rotation):
alienvault:/etc/logrotate.d# cat 3com-adsl-11g
/var/log/3com-adsl-11g.log {
weekly
missingok
rotate 7
compress
notifempty
}
Then, restart rsyslogd:
# /etc/init.d/rsyslogd restart
Plugin creation
List syslog messages
Now we can create our plugin. At this stage it’s important to list all syslog messages the remote device can send (refer to the device’s technical documentation).
Write plugin
Create a regular expression pattern for each message with distinct sections as follows:
alienvault:/etc/ossim/agent/plugins# cat 3com-adsl-11g.cfg
;; 3Com ADSL 11g
;; plugin_id: 9001
;; type: detector
;;
[DEFAULT]
plugin_id=9001
[config]
type=detector
enable=yes
source=log
location=/var/log/3com-adsl-11g.log
create_file=false
process=
start=no
stop=no
startup=
shutdown=
[3com-adsl-11g-login-success]
#Feb 12 20:37:09 192.168.1.51 3Com ADSL 11g[3]:192.168.1.29 login success
event_type=event
regexp="(?P<date>\w{3}\s+\d{1,2}\s\d\d:\d\d:\d\d)\s+(?P<sensor>\S+)\s+3Com\sADSL\s11g\[\d{1,2}\]:+(?P<src>\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3})\s+login\ssuccess"
date={normalize_date($date)}
sensor={resolv($sensor)}
plugin_sid=1
src_ip={$src}
[3com-adsl-11g-login-failed]
#Feb 12 12:14:54 192.168.1.51 3Com ADSL 11g[2]:192.168.1.38 login fail
event_type=event
regexp="(?P<date>\w{3}\s+\d{1,2}\s\d\d:\d\d:\d\d)\s+(?P<sensor>\S+)\s+3Com\sADSL\s11g\[\d{1,2}\]:+(?P<src>\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3})\s+login\sfail"
date={normalize_date($date)}
sensor={resolv($sensor)}
plugin_sid=2
src_ip={$src}
[3com-adsl-11g-forced-logout]
#Feb 12 20:52:18 192.168.1.51 3Com ADSL 11g[4]:192.168.1.29 forced logout
event_type=event
regexp="(?P<date>\w{3}\s+\d{1,2}\s\d\d:\d\d:\d\d)\s+(?P<sensor>\S+)\s+3Com\sADSL\s11g\[\d{1,2}\]:+(?P<src>\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3})\s+forced\slogout"
date={normalize_date($date)}
sensor={resolv($sensor)}
plugin_sid=3
src_ip={$src}
[3com-adsl-11g-timed-out]
#Feb 12 22:39:16 192.168.1.51 3Com ADSL 11g[10]:User from 192.168.1.29 timed out
event_type=event
regexp="(?P<date>\w{3}\s+\d{1,2}\s\d\d:\d\d:\d\d)\s+(?P<sensor>\S+)\s+3Com\sADSL\s11g\[\d{1,2}\]:+User\sfrom\s(?P<src>\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3})\s+timed\sout"
date={normalize_date($date)}
sensor={resolv($sensor)}
plugin_sid=4
src_ip={$src}
If you want to test a regular expression, you can proceed as follows (example given for the “timed out message”):
# python
>>> import re
>>> r = re.match(
... "(?P<date>\w{3}\s+\d{1,2}\s\d\d:\d\d:\d\d)\s+(?P<sensor>\S+)\s+3Com\sADSL\s11g\[\d{1,2}\]:+User\sfrom\s(?P<src>\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3})\s+timed\sout",
... "Feb 12 22:39:16 192.168.1.51 3Com ADSL 11g[10]:User from 192.168.1.29 timed out"
... )
>>> r.group(0) # Check that the entire string is processed
'Feb 12 22:39:16 192.168.1.51 3Com ADSL 11g[10]:User from 192.168.1.29 timed out'
>>> r.group(1) # Check that date is successfully split
'Feb 12 22:39:16'
>>> r.group(3) # Check source IP
'192.168.1.29'
For more information on regular expresions, refer to this page: http://docs.python.org/2/library/re.html
Another way to test:
# /usr/share/ossim/scripts/regexp.py \
/var/log/3com-adsl-11g.log \
"(?P<date>\w{3}\s+\d{1,2}\s\d\d:\d\d:\d\d)\s+(?P<sensor>\S+)\s+3Com\sADSL\s11g\[\d{1,2}\]:+(?P<src>\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3})\s+login\sfail" \
/etc/ossim/agent/plugins/3com-adsl-11g.cfg
(?P<date>\w{3}\s+\d{1,2}\s\d\d:\d\d:\d\d)\s+(?P<sensor>\S+)\s+3Com\sADSL\s11g\[\d{1,2}\]:+(?P<src>\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3})\s+login\sfail
[('Feb 11 22:48:25', '192.168.1.51', '192.168.1.29')]
[('Feb 11 22:48:28', '192.168.1.51', '192.168.1.29')]
[('Feb 11 22:48:35', '192.168.1.51', '192.168.1.29')]
[('Feb 11 22:48:38', '192.168.1.51', '192.168.1.29')]
[('Feb 11 22:48:43', '192.168.1.51', '192.168.1.29')]
[('Feb 11 22:48:46', '192.168.1.51', '192.168.1.29')]
[('Feb 11 22:48:50', '192.168.1.51', '192.168.1.29')]
[('Feb 11 22:48:55', '192.168.1.51', '192.168.1.29')]
[('Feb 11 22:49:04', '192.168.1.51', '192.168.1.29')]
[('Feb 12 12:10:15', '192.168.1.51', '192.168.1.38')]
[('Feb 12 12:14:51', '192.168.1.51', '192.168.1.38')]
[('Feb 12 12:14:54', '192.168.1.51', '192.168.1.38')]
[('Feb 12 23:37:32', '192.168.1.51', '192.168.1.29')]
[('Feb 12 23:37:34', '192.168.1.51', '192.168.1.29')]
[('Feb 12 23:37:38', '192.168.1.51', '192.168.1.29')]
[('Feb 13 18:07:11', '192.168.1.51', '192.168.1.29')]
[('Feb 13 18:07:14', '192.168.1.51', '192.168.1.29')]
[('Feb 13 18:07:21', '192.168.1.51', '192.168.1.29')]
[('Feb 13 19:32:38', '192.168.1.51', '192.168.1.29')]
[('Feb 13 19:32:40', '192.168.1.51', '192.168.1.29')]
[('Feb 13 19:32:43', '192.168.1.51', '192.168.1.29')]
Counted 31 lines.
Matched 21 lines.
Give your plugin file appropriate privileges:
# cd /etc/ossim/agent/plugins/ # chown root:www-data 3com-adsl-11g.cfg
Declare your plugin
config.cfg
Edit /etc/ossim/agent/config.cfg and insert your plugin in the “plugins” section as follows:
... [plugins] ... sudo=/etc/ossim/agent/plugins/sudo.cfg whois-monitor=/etc/ossim/agent/plugins/whois-monitor.cfg wmi-monitor=/etc/ossim/agent/plugins/wmi-monitor.cfg 3com-adsl-11g=/etc/ossim/agent/plugins/3com-adsl-11g.cfg ...
Database
Create the SQL script to load the plugin as well as the messages (plugin_sid) in the database:
# cat /usr/share/doc/ossim-mysql/contrib/plugins/3com-adsl-11g.sql -- 3Com ADSL 11g -- Plugin id:9001 DELETE FROM plugin WHERE id = "9001"; DELETE FROM plugin_sid where plugin_id = "9001"; INSERT IGNORE INTO plugin (id, type, name, description) VALUES (9001, 1, '3Com ADSL 11g', '3Com ADSL 11g'); INSERT IGNORE INTO plugin_sid (plugin_id, sid, category_id, class_id, name, priority, reliability) VALUES (9001, 1, NULL, NULL, '3Com-ADSL-11g: login success', 1, 3); INSERT IGNORE INTO plugin_sid (plugin_id, sid, category_id, class_id, name, priority, reliability) VALUES (9001, 2, NULL, NULL, '3Com-ADSL-11g: login fail', 1, 3); INSERT IGNORE INTO plugin_sid (plugin_id, sid, category_id, class_id, name, priority, reliability) VALUES (9001, 3, NULL, NULL, '3Com-ADSL-11g: forced logout', 1, 3); INSERT IGNORE INTO plugin_sid (plugin_id, sid, category_id, class_id, name, priority, reliability) VALUES (9001, 4, NULL, NULL, '3Com-ADSL-11g: timed out', 1, 3);
Load it into the database:
# ossim-db < /usr/share/doc/ossim-mysql/contrib/plugins/3com-adsl-11g.sql
To activate the plugin on the Server Side, restart the OSSIM server process:
# /etc/init.d/ossim-server restart
To activate the plugin on the Agent Side, restart the OSSIM agent process:
# /etc/init.d/ossim-agent restart
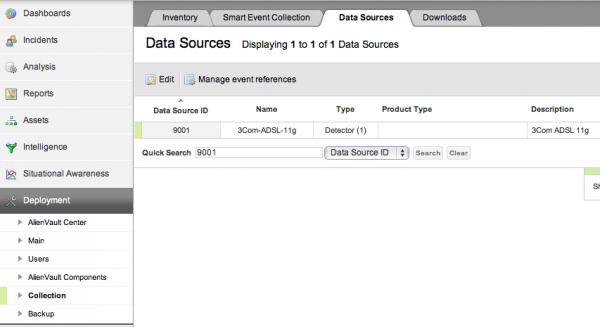
Check that the plugin has been successfully integrated:
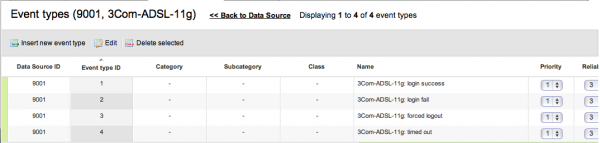
Double click on the plugin to list plugin SIDs:
Generate alarms
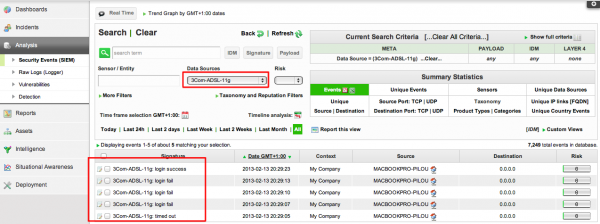
Check SIEM events
Check that you have SIEM events from the new created data source:
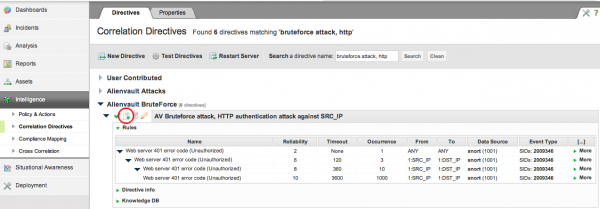
Write a correlation directive
Clone an existing directive:
Then edit the user.xml directive that as been created and adapt:
alienvault:/etc/ossim/server/7221e585-3a54-11e2-bfba-00145e16125b# cat user.xml
<?xml version="1.0" encoding="UTF-8"?>
...
<directive id="500001" name="AV Bruteforce attack, 3Com ADSL 11g" priority="4">
<rule type="detector" name="3Com ADSL 11g login failed" from="ANY" to="ANY" port_from="ANY" port_to="ANY" reliability="2" occurrence="1" plugin_id="9001" plugin_sid="2">
<rules>
<rule type="detector" name="3Com ADSL 11g login failed" from="1:SRC_IP" to="1:DST_IP" port_from="ANY" port_to="ANY" reliability="6" occurrence="3" time_out="120" plugin_id="9001" plugin_sid="2">
<rules>
<rule type="detector" name="3Com ADSL 11g login failed" from="1:SRC_IP" to="1:DST_IP" port_from="ANY" port_to="ANY" reliability="8" occurrence="10" time_out="360" plugin_id="9001" plugin_sid="2">
<rules>
<rule type="detector" name="3Com ADSL 11g login failed" from="1:SRC_IP" to="1:DST_IP" port_from="ANY" port_to="ANY" reliability="10" occurrence="1000" time_out="3600" plugin_id="9001" plugin_sid="2"/>
</rules>
</rule>
</rules>
</rule>
</rules>
</rule>
</directive>
Restart ossim-server to apply the modifications:
# /etc/init.d/ossim-server restart
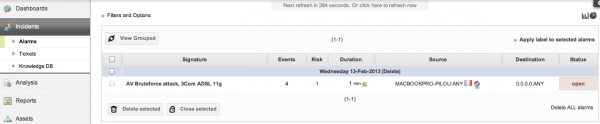
Check alarms
Test some wrong passwords against your tested device and you should see alarms: