XORSearch
Description
XORSearch V1.9.2 is a tool developed by Didier Stevens. It searches for a XOR (0-255), ROL (0-7), ROT (1-25) or SHIFT encoded strings in a file using brute-force.
Installation
Windows
- Download XORSearch here: http://didierstevens.com/files/software/XORSearch_V1_9_2.zip
- Uncompress
- Run XORSearch.exe in command line
Linux
$ mkdir -p /data/src/xorsearch/ $ cd /data/src/xorsearch/ $ wget http://didierstevens.com/files/software/XORSearch_V1_9_2.zip $ unzip XORSearch_V1_9_2.zip $ gcc -o xorsearch XORSearch.c
Usage
Syntax
Usage: XORSearch [-siuh] [-l length] [-n length] [-f search-file] file string
Options
- -s
- save the XOR, ROL, ROT or SHIFT encoded file containing the string
- -l <length>
- limit the number of printed characters (50 by default). Can't be used in combination with -n.
- -i
- ignore the case when searching
- -u
- search for Unicode strings (limited support). Can't be used in combination with -h.
- -f
- provide a file with search strings
- -n <length>
- print the length neighbouring charaters (before & after the found keyword). Can't be used in combination with -l.
- -h
- search for hex strings. Can't be used in combination with -u.
- -k
- decode with embedded keys
Examples
Decrypting strings with XORSearch in a malware
Let's see where the string "http:" appears in a malware named getdown.exe that we have collected:
$ ./xorsearch -i /data/tmp/getdown.exe http: Found XOR 83 position 1800: http://1.234.27.146/pcfix.exe
You can even go further and save the file (-s parameter) to display other interesting strings that would have been encoded with the same key:
$ ./xorsearch -i -s /data/tmp/getdown.exe http: Found XOR 83 position 1800: http://1.234.27.146/pcfix.exe $ strings /data/tmp/getdown.exe.XOR.83 [SNIP] http://1.234.27.146/pcfix.exe affid=23456732-34459 [SNIP]
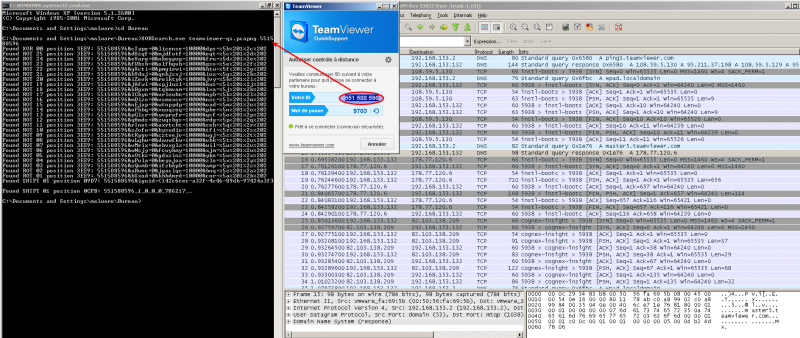
TeamViewer's remote access protocol
When you run TeamViewer, your machine gets an ID ("551 588 596" in the below example)
A network traffic capture has been run while starting TeamViewer Quick Support and saved in a *.pcapng file. I've then used XORSearch to search my ID in the traffic capture:
And as you can see, XORSearch finds this ID by left-shifting the content of the pcap file with one bit:
$ ./xorsearch /data/tmp/teamviewer-qs.pcapng 551588596
Found XOR 00 position 3EE9: 551588596&cType=0&license=10000&dps=%5b%201%2c%202
Found ROT 25 position 3EE9: 551588596&dUzqf=0&mjdfotf=10000&eqt=%5c%201%2d%202
Found ROT 24 position 3EE9: 551588596&eVarg=0&nkegpug=10000&fru=%5d%201%2e%202
Found ROT 23 position 3EE9: 551588596&fWbsh=0&olfhqvh=10000&gsv=%5e%201%2f%202
Found ROT 22 position 3EE9: 551588596&gXcti=0&pmgirwi=10000&htw=%5f%201%2g%202
Found ROT 21 position 3EE9: 551588596&hYduj=0&qnhjsxj=10000&iux=%5g%201%2h%202
Found ROT 20 position 3EE9: 551588596&iZevk=0&roiktyk=10000&jvy=%5h%201%2i%202
Found ROT 19 position 3EE9: 551588596&jAfwl=0&spjluzl=10000&kwz=%5i%201%2j%202
Found ROT 18 position 3EE9: 551588596&kBgxm=0&tqkmvam=10000&lxa=%5j%201%2k%202
Found ROT 17 position 3EE9: 551588596&lChyn=0&urlnwbn=10000&myb=%5k%201%2l%202
Found ROT 16 position 3EE9: 551588596&mDizo=0&vsmoxco=10000&nzc=%5l%201%2m%202
Found ROT 15 position 3EE9: 551588596&nEjap=0&wtnpydp=10000&oad=%5m%201%2n%202
Found ROT 14 position 3EE9: 551588596&oFkbq=0&xuoqzeq=10000&pbe=%5n%201%2o%202
Found ROT 13 position 3EE9: 551588596&pGlcr=0&yvprafr=10000&qcf=%5o%201%2p%202
Found ROT 12 position 3EE9: 551588596&qHmds=0&zwqsbgs=10000&rdg=%5p%201%2q%202
Found ROT 11 position 3EE9: 551588596&rInet=0&axrtcht=10000&seh=%5q%201%2r%202
Found ROT 10 position 3EE9: 551588596&sJofu=0&bysudiu=10000&tfi=%5r%201%2s%202
Found ROT 09 position 3EE9: 551588596&tKpgv=0&cztvejv=10000&ugj=%5s%201%2t%202
Found ROT 08 position 3EE9: 551588596&uLqhw=0&dauwfkw=10000&vhk=%5t%201%2u%202
Found ROT 07 position 3EE9: 551588596&vMrix=0&ebvxglx=10000&wil=%5u%201%2v%202
Found ROT 06 position 3EE9: 551588596&wNsjy=0&fcwyhmy=10000&xjm=%5v%201%2w%202
Found ROT 05 position 3EE9: 551588596&xOtkz=0&gdxzinz=10000&ykn=%5w%201%2x%202
Found ROT 04 position 3EE9: 551588596&yPula=0&heyajoa=10000&zlo=%5x%201%2y%202
Found ROT 03 position 3EE9: 551588596&zQvmb=0&ifzbkpb=10000&=%5y%201%2z%202
Found ROT 02 position 3EE9: 551588596&aRwnc=0&jgaclqc=10000&bnq=%5z%201%2a%202
Found ROT 01 position 3EE9: 551588596&bSxod=0&khbdmrd=10000&cor=%5a%201%2b%202
Found SHIFT 01 position 09D7: 551588596&iguid={142c6cec-a32f-4c46-89db-97424a3f3
Found SHIFT 01 position 0CFB: 551588596_1_0_0_0_786217_.