Category:Digital-Forensics/Computer-Forensics/Anti-Reverse-Engineering/Packers/ASPack
| You are here | ASPack
|
Description
ASPack can be difficult to unpack because it uses self-modifying code. Hence, you should use hardware breakpoints rather than software breakpoints.
Manually unpack ASPack
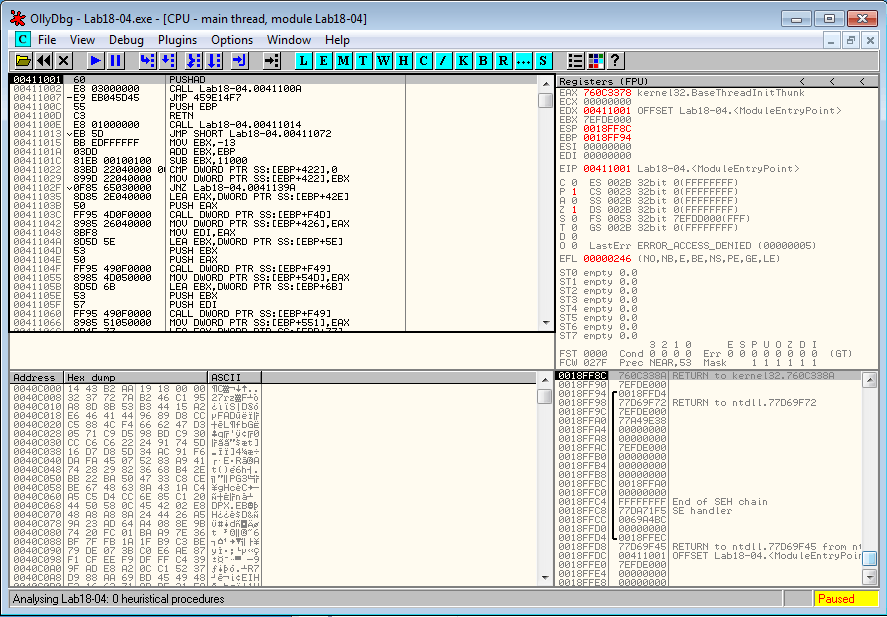
Given a malware packed with ASPack (idenyified as "ASPack 2.12 -> Alexey Solodovnikov" by PEiD). The malware starts at 0x41001 with a PUSHAD instruction, which saves all registers.
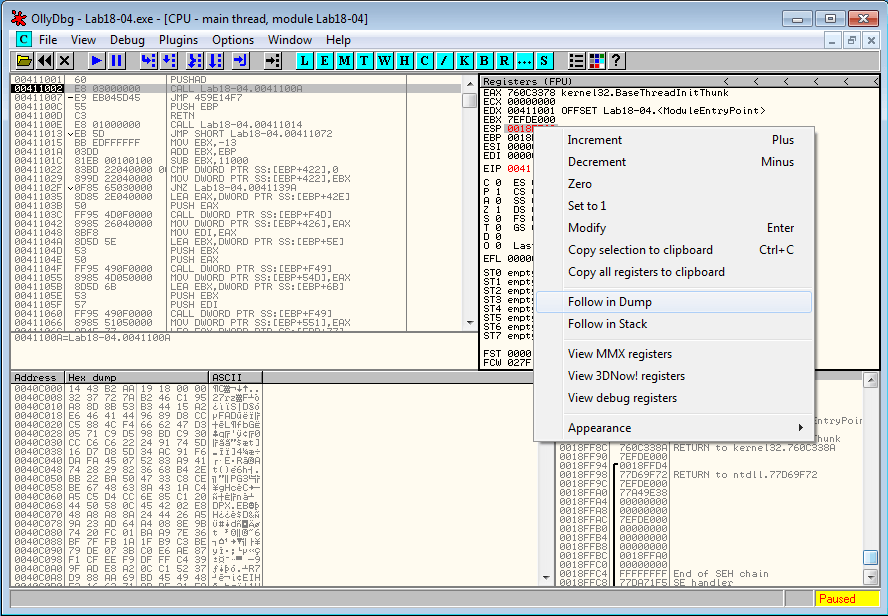
It's likely that the unpacking stub will call POPAD to restore the registers before the tail jump. Let's put a breakpoint at the location of the stack pointer. To do that, we step over the first instruction. The program stops at 0x4111002. Now, right click on ESP and select Follow in Dump:
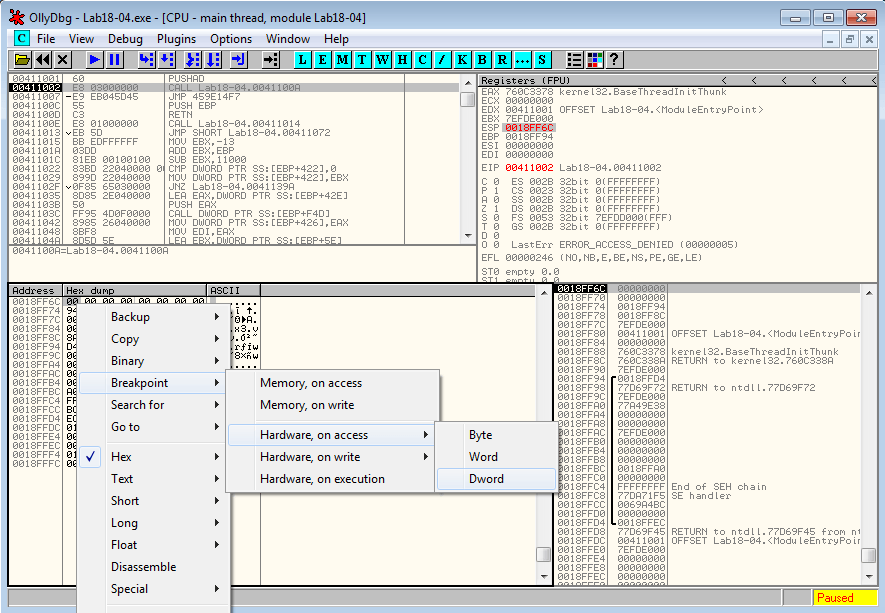
Right click on the first byte in the memory dump window and select Breakpoint > Hardware, on access > Dword and run (F9).
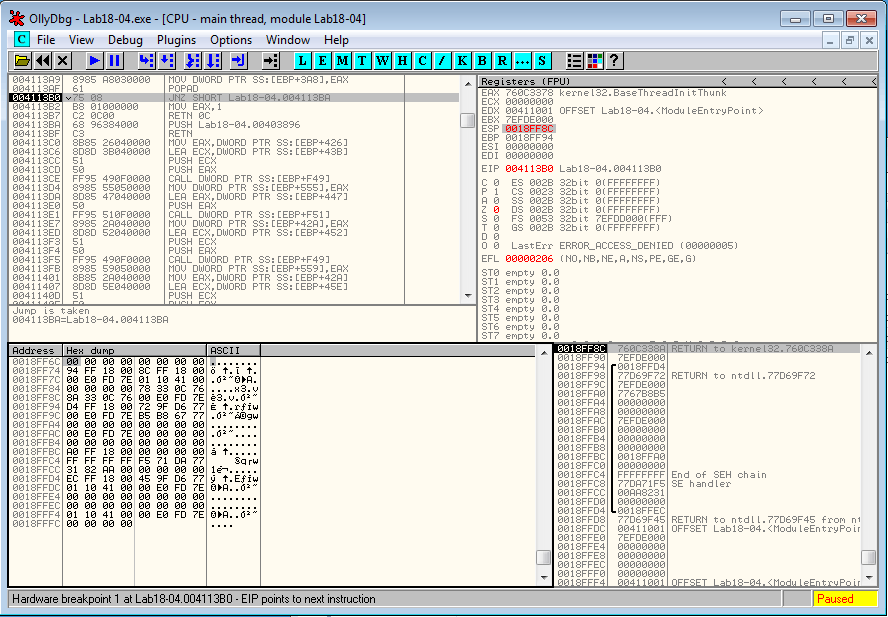
The program reaches the breakpoint and one instruction above, we see the POPAD instruction.
The code around this location is:
004113AF 61 POPAD
004113B0 75 08 JNZ SHORT Lab18-04.004113BA
004113B2 B8 01000000 MOV EAX,1
004113B7 C2 0C00 RETN 0C
004113BA 68 96384000 PUSH Lab18-04.00403896
004113BF C3 RETN
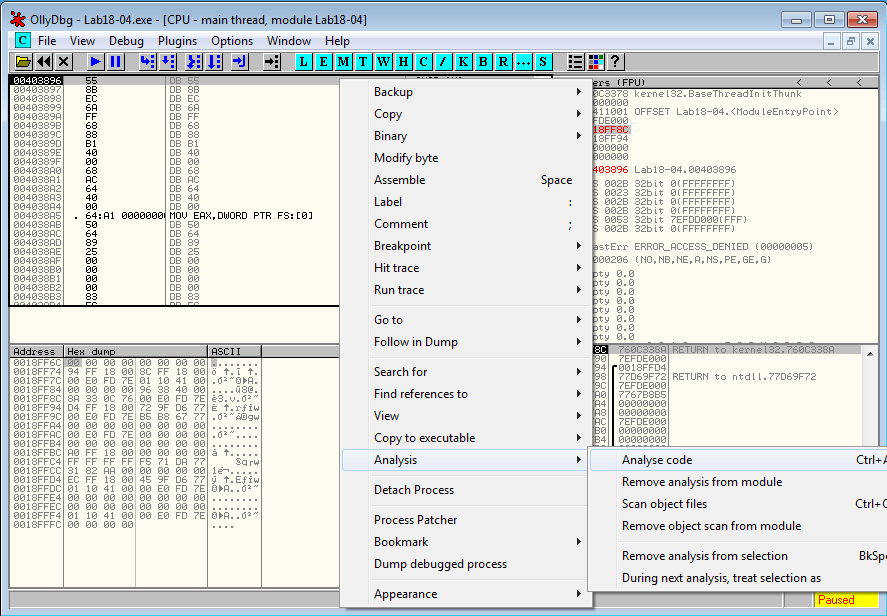
When we step over the JNZ instruction at 0x4113B0, the jump is taken and the program jumps to 0x4113BA. We now step into the return instruction at 0x4113BF. OllyDbg hasn't disassembled the code, which is easily fixed by right clicking and choosing Analysis > Analyze code.
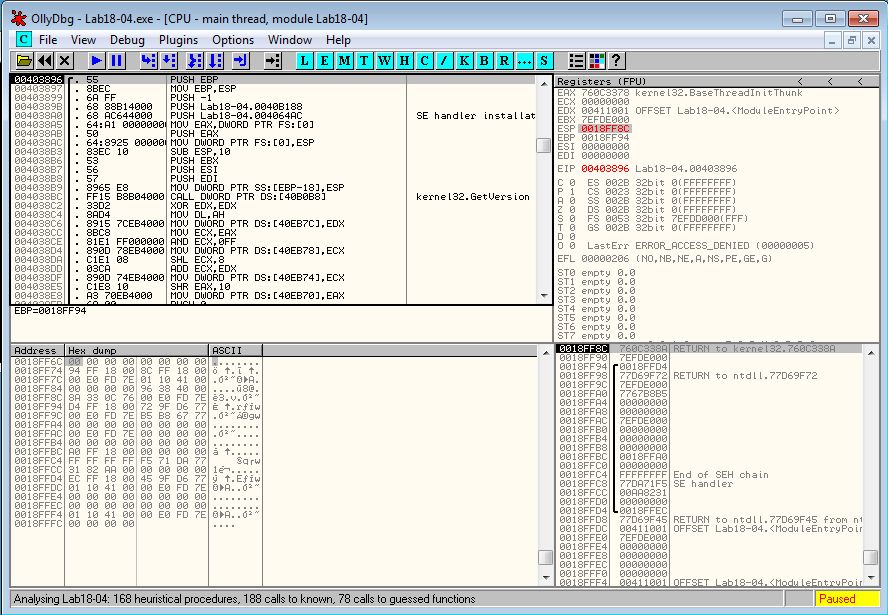
We have successfully unpacked the malware. Dump it from Plugins > OllyDump > Dump debugged process and we're done.
Pages in category "Digital-Forensics/Computer-Forensics/Anti-Reverse-Engineering/Packers/ASPack"
The following 2 pages are in this category, out of 2 total.