Category:Digital-Forensics/Computer-Forensics/Anti-Reverse-Engineering/Packers/NTkrnl
| You are here | NTkrnl
|
Description

Thank you for your comprehension.
Manual unpacking
Identify IAT
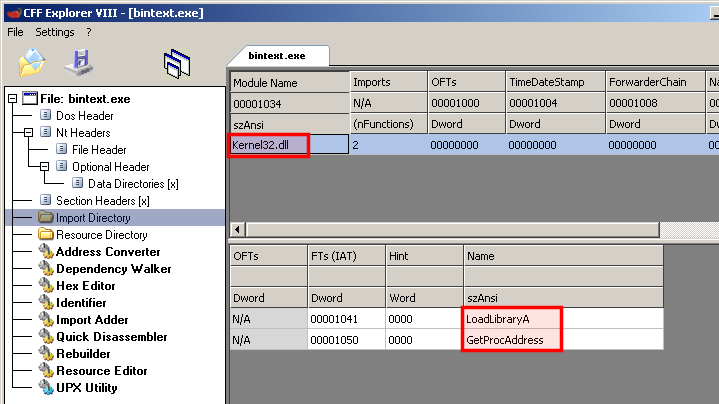
CFF Explorer identifies that the 2 following functions are imported from kernel32.dll:
- GetProcAddress
- LoadLibraryA
We will use this information to identify the address where these libraries are imported in the code. We should be close to the Original Entry Point (OEP).
Debugging options
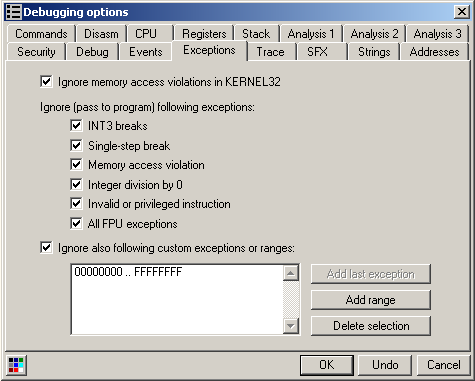
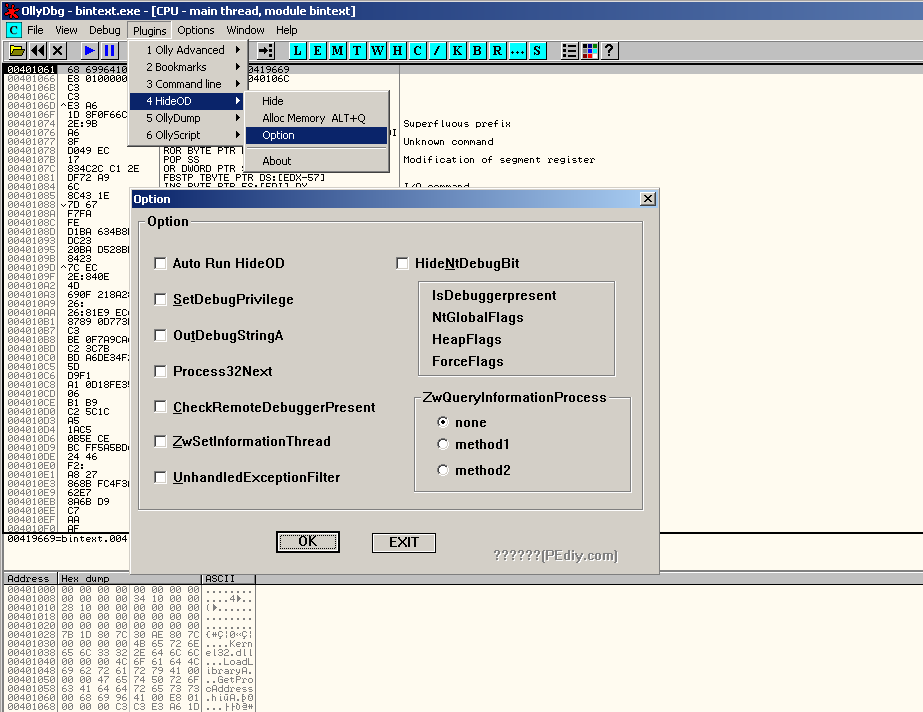
First of all, let's get rid of some anti-debugging protections with the debugging options (check all options) and the HideOD plugin (check all options):
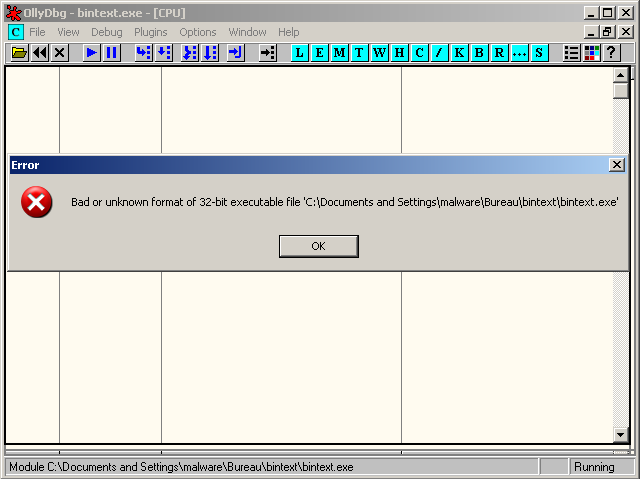
Corrupted PE header
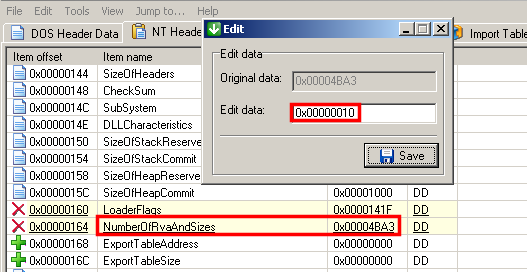
When we load the malware into OllyDbg, we notice that the PE header is incorrect. The value of the NumberOfRvaAndSizes field to an inconsistent value so that OllyDbg will display the following message:
You can fix the value of NumberOfRvaAndSizes with xPELister ("NT Header Data" tab) and updating the value to "0x00000010":
Then save the modifications (File > Save).
Fake breakpoint
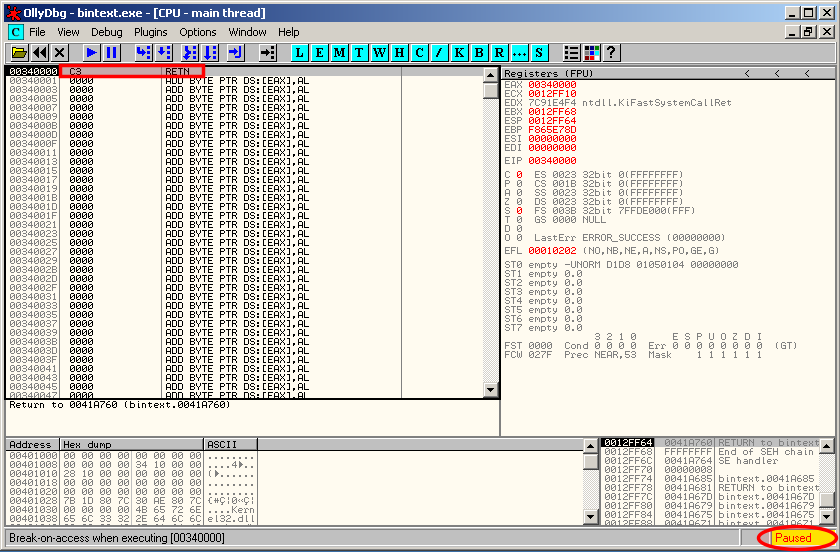
Now, load the updated malware into OllyDbg and run it (F9). We notice that the program stops tough we haven't defined any breakpoint.
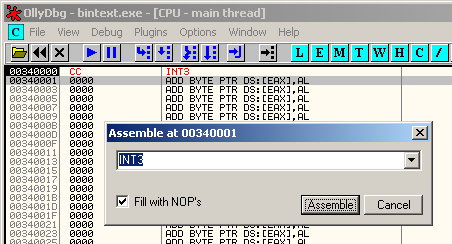
To bypass this, patch the RETN into INT3:
Identify address of LoadLibraryA
Now, we can locate where LoadLibraryA is called and set a breakpoint. Press Ctrl+G and enter "LoadLibraryA":
Bypass timing defenses

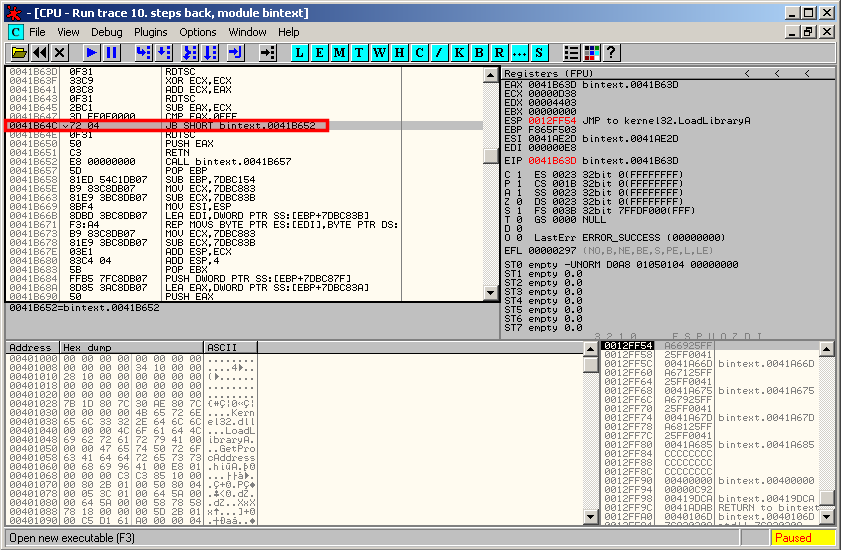
At this stage, there is a timing defense: RDTSC at address 0x41B64C:
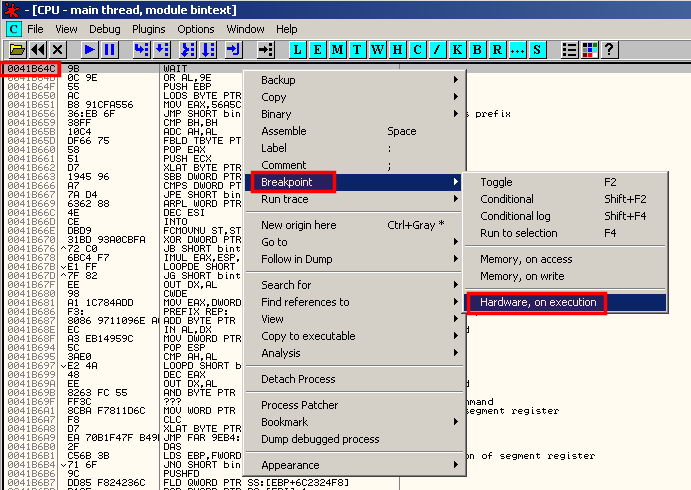
Press Ctrl+G and go to B4164C, then set a harware on execution breakpoint so that we will have a chance to patch the code before the timing defense is reached:
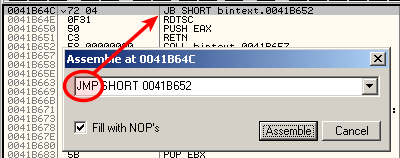
Then run (F9) and patch the jump as follows when you reach it:
Reaching LoadLibrary
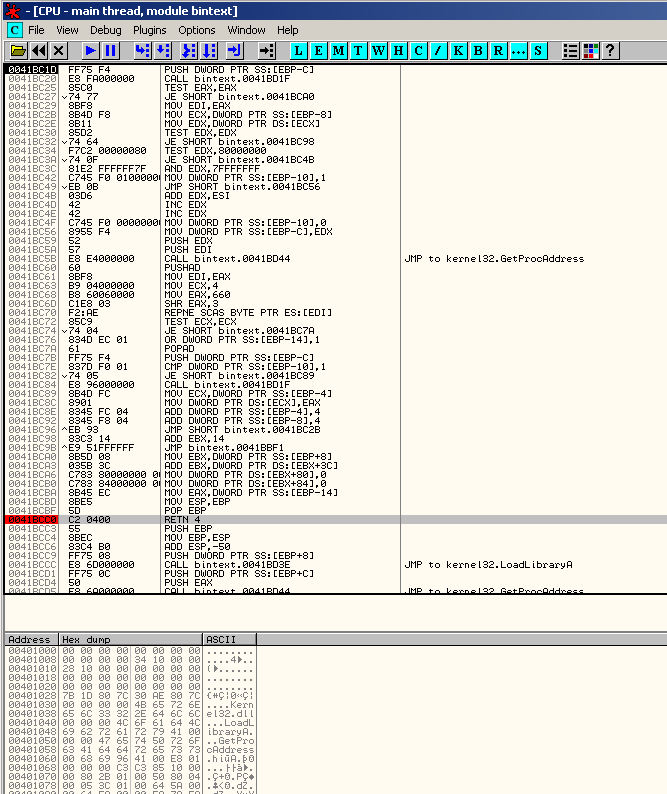
Once you have bypassed all timing defenses, you should arrive at the LoadLibrary breakpoint previously defined. Remove it and run till user code (Alt+F9).
To determine who is using LoadLibraryA, we need to set a breakpoint on the next RETN instruction within the function, so we can see which code block is getting the result. Set a breakpoint to the RETN instruction and press F9.
EAX calls
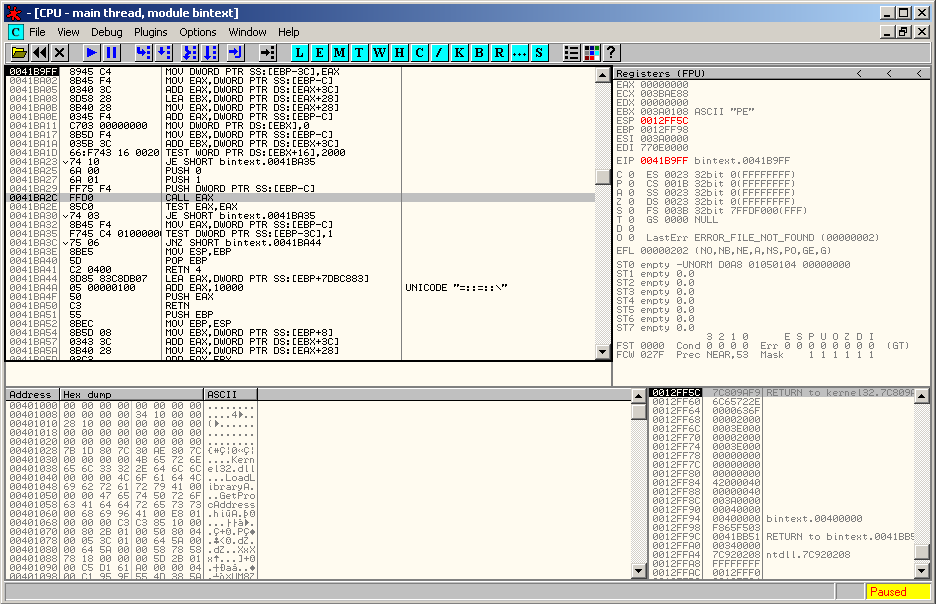
Once you reach it, remove the breakpoint (F2) and step into (F7). Scroll down to find the instruction that calls EAX:
Set a breakpoint on it (F2), run (F9) and step into (F7). This does not correspond to the OEP:
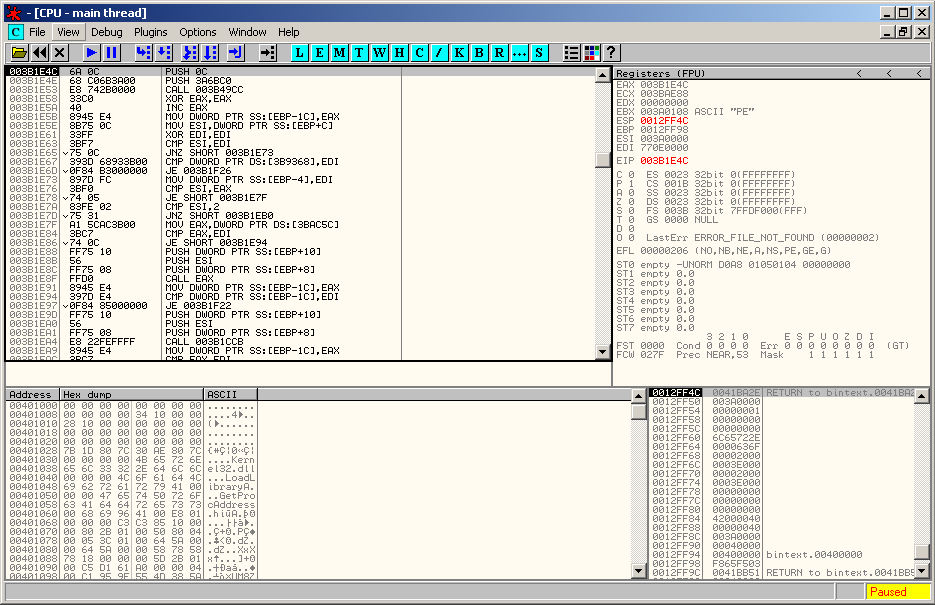
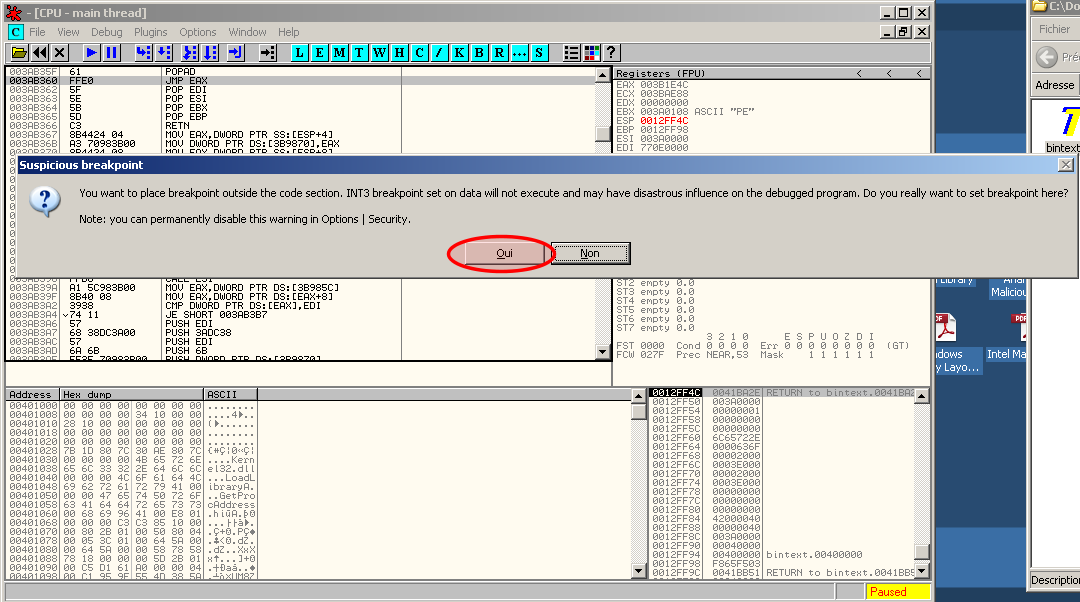
Finding the OEP with POPAD / JMP EAX
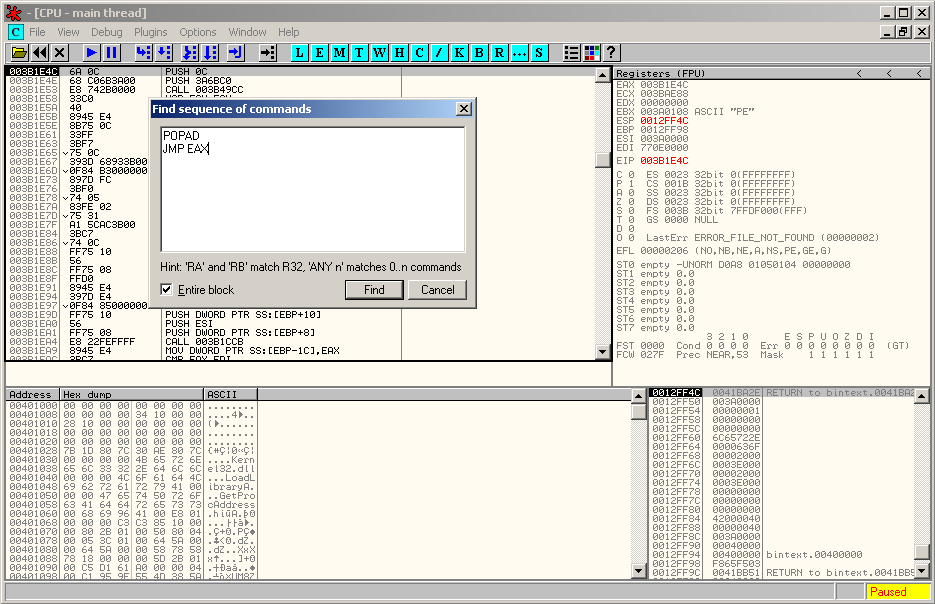
Let's use another method to find our OEP. Right click in the disassembly region and select "Search for > Sequence of commands" (Ctrl+S). Enter following strings:
The first occurence is not the good one.
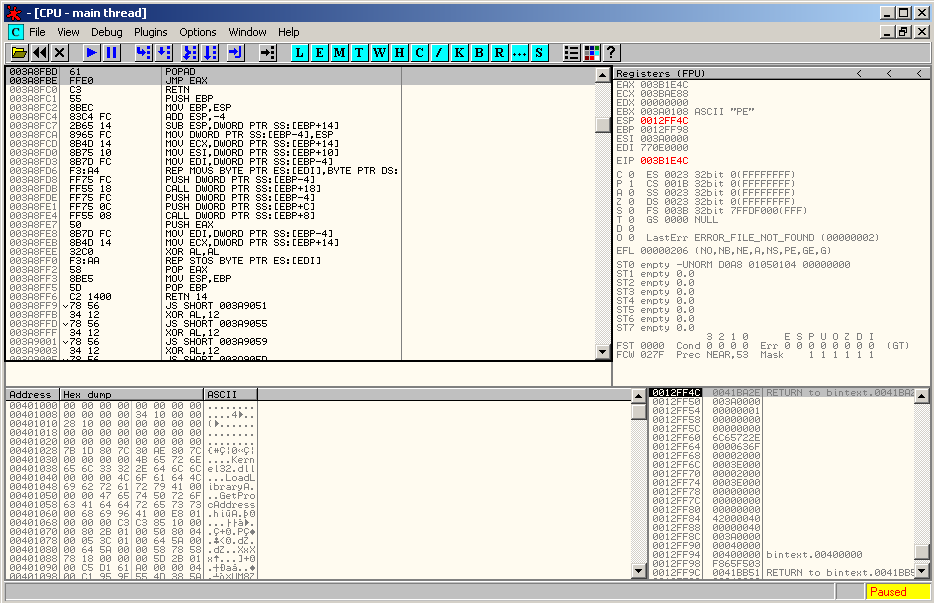
Press Ctrl+L to find the next one and set a breakpoint on the JMP EAX instruction. OllyDbg will ask you if you are sure to set this breakpoint, since it is outside the code section. It is safe to click "Yes".
Run (F9) and step into (F7):
This time, we are done. You just have to dump the process with the OllyDump plugin
Automatic unpacking
This category currently contains no pages or media.