Dradis


Description
Dradis is a Ruby on Rails-based framework that helps pentester organize and share their results in a common database. The tool then enables to consolidate the inputs with external databases (e.g. vulnerabilities databases) and generate reports.
The tool is shipped with a set of plugins that enable to import scan results:
- Project package upload
- Project template upload
- Nmap upload
- Nikto upload
- Nessus upload
- Burp upload
Installation
In BackTrack
In BackTrack, all you need to do is type following commands:
# apt-get install dradis # cd /pentest/misc/dradis/ # ./install # ./start
Now point your browser to http://127.0.0.1:3004
From scratch
Download and uncompress Dradis
$ cd /data/src/ $ wget http://downloads.sourceforge.net/dradis/dradis-v2.5.2.tar.bz2 $ bzip2 -cd dradis-v2.5.2.tar.bz2 | tar xf - $ mkdir -p /pentest/misc/ $ mv dradis-2.5/ /pentest/misc/dradis/
Install dependencies
First install following packages:
$ apt-get install ruby1.8 rubygems1.8 irb rdoc ruby1.8-dev libopenssl-ruby
Then install Ruby dependencies via Gem:
$ sudo gem install rake $ sudo gem install sqlite3-ruby

Check the requirements
At least check that all requirements are met by issuing following commands:
$ cd /pentest/misc/dradis/
$ ./verify.sh
dradis Framework dependencies verification script
-- -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- --
This script will try to determine whether all the dependencies required to
use the dradis Framework are present in the system providing hints on how to
install the missing dependencies. The system will NOT be modified by the
script.
Please send your feedback about this script to:
feedback [you-know-what] dradisframework.org
Running Standard checks.
Looking for Ruby interpreter... found [ /usr/bin/ruby ].
Checking for support to compile native extensions... found.
Looking for RubyGems and the 'gem' command... found [ /usr/bin/gem ].
Looking for the 'rake' command... found [ /usr/bin/rake ].
Looking for SQLite3 libraries... found.
Looking for the SQLite3 ruby gem [sqlite3-ruby]... found (v1.3.1).
Congratulations. You seem to be ready to run the Dradis Framework. Enjoy!
Populate/reset the database
Then populate the database:
$ cd server/
$ rake dradis:reset
(in /pentest/misc/dradis/server)
Environment not initialized. Nothing to backup.
Dropping attachments from attachments/... done.
== CreateNodes: migrating ====================================================
-- create_table(:nodes)
-> 0.0017s
== CreateNodes: migrated (0.0019s) ===========================================
== CreateCategories: migrating ===============================================
-- create_table(:categories)
-> 0.0021s
== CreateCategories: migrated (0.0022s) ======================================
== CreateNotes: migrating ====================================================
-- create_table(:notes)
-> 0.0038s
== CreateNotes: migrated (0.0040s) ===========================================
== CreateConfigurations: migrating ===========================================
-- create_table(:configurations)
-> 0.0023s
== CreateConfigurations: migrated (0.0025s) ==================================
== CreateUsers: migrating ====================================================
-- create_table("users", {:force=>true})
-> 0.0038s
== CreateUsers: migrated (0.0040s) ===========================================
== CreateFeeds: migrating ====================================================
-- create_table(:feeds)
-> 0.0018s
== CreateFeeds: migrated (0.0019s) ===========================================
Usage
Start Dradis server
To start the server, go to /pentest/misc/dradis/ and issue following commands:
$ cd /pentest/misc/dradis/server/ $ ruby ./script/server
By default, Dradis server listens on 127.0.0.1:3004. Alternatively, you may bind to different address and port:
$ ruby ./script/server -b <ip> -p <port>
First connection
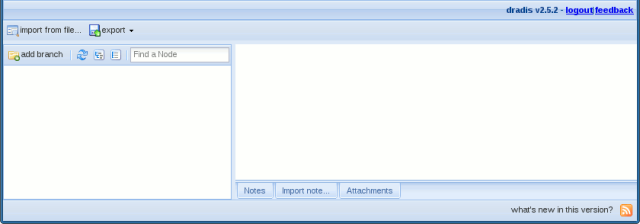
Point your web browser to: https://localhost:3004/
If everything is fine, you should see a similar screen:
Initialize Dradis
To initialize a project, go to: https://localhost:3004/sessions/init
Fill in a password and check the "New project" radio button. Then click on the "Initialize" button.
On the next screen, select a login and use the password you have defined on the previous screen.
You should now be presented with a similar screen:
Import scan results
In this example, we are going to import scan results from Nmap.
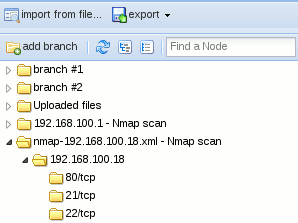
First scan a target using Nmap (e.g. 192.168.100.18) and export the results (XML format) to a file:
$ sudo nmap -sS 192.168.100.18 -oX nmap-192.168.100.18.xml
Then go to Dradis web interface and click on the "Import" button from the top menu. You will be presented with a popup window in which you will specify the type (select Nmap upload) and the path to your file. Fill in all fields and click on OK.
Once imported, the results appear in the tree:
The same way, you can import results from:
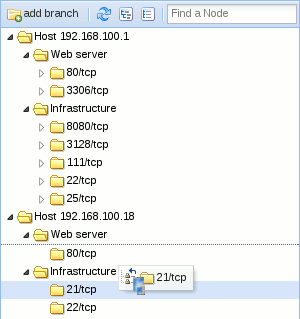
Once imported, drag and drop items from the tree to organize them as you want:
Using import note
Dradis offers the possibility to import notes from an external database. We base our example on:
- A scan result from Nikto against a WIN-XP-PRO-SP3 machine
- the Open Source Vulnerability DataBase (OSVDB)

First generate a Nikto report:
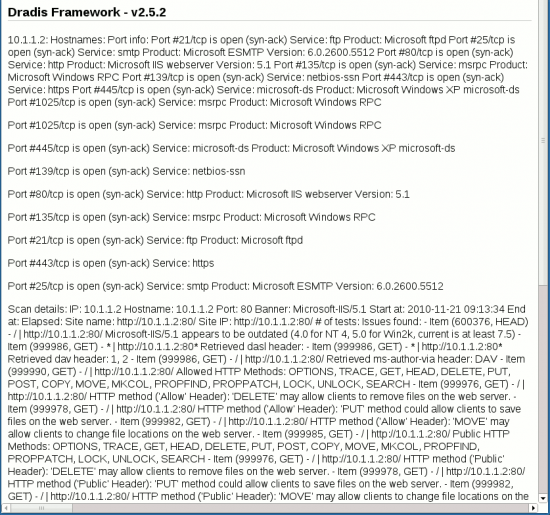
$ ./nikto.pl -output /data/tmp/nikto-10.1.1.2.xml -host 10.1.1.2
- ***** SSL support not available (see docs for SSL install) *****
- Nikto v2.1.3
---------------------------------------------------------------------------
+ Target IP: 10.1.1.2
+ Target Hostname: 10.1.1.2
+ Target Port: 80
+ Start Time: 2010-11-21 09:13:34
---------------------------------------------------------------------------
+ Server: Microsoft-IIS/5.1
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Microsoft-IIS/5.1 appears to be outdated (4.0 for NT 4, 5.0 for Win2k, current is at least 7.5)
+ Retrieved dasl header: <DAV:sql>
+ Retrieved dav header: 1, 2
+ Retrieved ms-author-via header: DAV
+ Allowed HTTP Methods: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
+ OSVDB-5646: HTTP method ('Allow' Header): 'DELETE' may allow clients to remove files on the web server.
+ OSVDB-397: HTTP method ('Allow' Header): 'PUT' method could allow clients to save files on the web server.
+ OSVDB-5647: HTTP method ('Allow' Header): 'MOVE' may allow clients to change file locations on the web server.
+ Public HTTP Methods: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
+ OSVDB-5646: HTTP method ('Public' Header): 'DELETE' may allow clients to remove files on the web server.
+ OSVDB-397: HTTP method ('Public' Header): 'PUT' method could allow clients to save files on the web server.
+ OSVDB-5647: HTTP method ('Public' Header): 'MOVE' may allow clients to change file locations on the web server.
+ WebDAV enabled (SEARCH UNLOCK LOCK MKCOL COPY PROPPATCH PROPFIND listed as allowed)
+ OSVDB-13431: PROPFIND HTTP verb may show the server's internal IP address: http://10.1.1.2/
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
+ OSVDB-877: HTTP TRACK method is active, suggesting the host is vulnerable to XST
+ ERROR: No authentication header defined:
+ 6417 items checked: 1 error(s) and 16 item(s) reported on remote host
+ End Time: 2010-11-21 09:13:48 (14 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
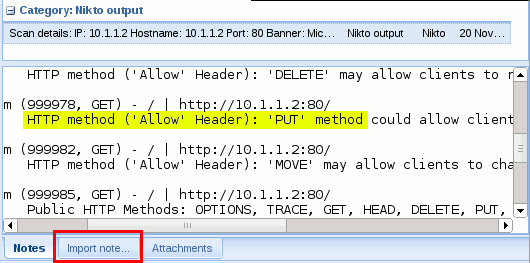
Among all detected vulnerabilities, we will focus on the one in yellow (PUT method).
Go to Dradis web interface and import your results using the method described on the section "Import scan results".
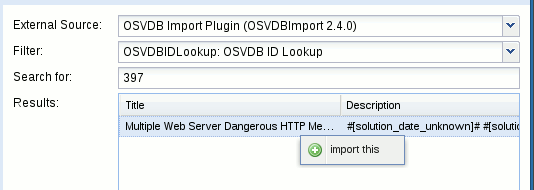
Click on the "Import note" tab and fill in the form as follows:
| External Source | Choose OSVDB Import Plugin (OSVDBImport 2.4.0) |
|---|---|
| Filter | Choose OSVDBIDLookup: OSVDB ID Lookup |
| Search for | 397 |
| Results | Right click on the entry and select "Import this" |
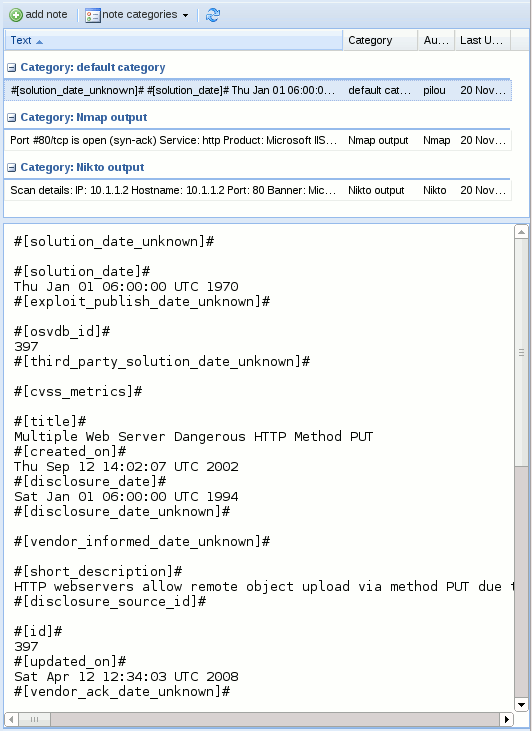
Once imported, the comments are added into Dradis:
Reports
At any time, you can export your results:
- HTML export
- Word export
- Pdf export
HTML export
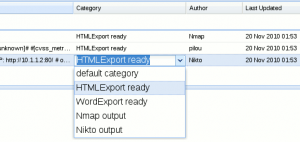
Go to Dradis web interface and tag all categories as "HtmlExport Ready".
Then click on the export and select HTML export from the top menu. Here is an example:
Word export
Refer to this tutorial: http://dradisframework.org/WordExport_templates.html
Pdf export
Refer to this tutorial: http://dradisframework.org/community/index.php?topic=6.0