E9fe9148a69a1b8f70996435787609c3
Description
Identification
| MD5 | e9fe9148a69a1b8f70996435787609c3 |
|---|---|
| SHA1 | 8679002da8a6b0d31abbe61e273ff1b48a6d9a2b |
| SHA256 | 9de606047ae141a872a7ddb78782fc8a8da5518e879b2239ec931560b7983ba8 |
| ssdeep | 768:b+C4+VEwtCaLTeKYFiDxqf7WPAgLa1y4b:s+VHeKYFoqjULapb |
| imphash | 2d829b5c9f62f6971dd80406f4fc7f84 |
| File size | 28.0 KB ( 28704 bytes ) |
| File type | Win32 EXE |
| Magic literal | PE32 executable for MS Windows (GUI) Intel 80386 32-bit |
Antivirus detection
| Antivirus | Result | Udtae |
|---|---|---|
| AVG | BackDoor.Sepro | 20140219 |
| Ad-Aware | Backdoor.Sepro.C | 20140219 |
| Agnitum | Backdoor.Sepro!QTVopoddVXY | 20140218 |
| AhnLab-V3 | Win-Trojan/Sepro.28704.C | 20140218 |
| AntiVir | BDS/Sepro.b.Srv | 20140219 |
| Antiy-AVL | Trojan[Backdoor]/Win32.Sepro | 20140219 |
| Avast | Win32:Nick [Wrm] | 20140219 |
| Baidu-International | Backdoor.Win32.Sepro.AjE | 20140219 |
| BitDefender | Backdoor.Sepro.C | 20140219 |
| Bkav | W32.Clod3be.Trojan.6b0d | 20140219 |
| CAT-QuickHeal | Backdoor.Sepro.c | 20140219 |
| CMC | Generic.Win32.e9fe9148a6!MD | 20140213 |
| Commtouch | W32/Risk.WZZG-4786 | 20140219 |
| Comodo | Backdoor.Win32.Sepro.C | 20140219 |
| DrWeb | BackDoor.Sepro | 20140219 |
| ESET-NOD32 | Win32/Sepro.C | 20140219 |
| Emsisoft | Backdoor.Sepro.C (B) | 20140219 |
| F-Prot | W32/Malware!a31c | 20140219 |
| F-Secure | Backdoor.Sepro.C | 20140219 |
| Fortinet | W32/Sepro.C!tr | 20140219 |
| GData | Backdoor.Sepro.C | 20140219 |
| Ikarus | Backdoor.Win32.Sepro.F | 20140219 |
| Jiangmin | Backdoor/Sepro.c | 20140219 |
| K7AntiVirus | Trojan ( 00002cac1 ) | 20140218 |
| K7GW | Trojan ( 00002cac1 ) | 20140218 |
| Kaspersky | Backdoor.Win32.Sepro.c | 20140219 |
| Kingsoft | Win32.Hack.Senza.c.(kcloud) | 20140219 |
| Malwarebytes | Backdoor.Agent | 20140219 |
| McAfee | BackDoor-DV | 20140219 |
| McAfee-GW-Edition | Heuristic.LooksLike.Win32.Suspicious.J!80 | 20140219 |
| MicroWorld-eScan | Backdoor.Sepro.C | 20140219 |
| Microsoft | Backdoor:Win32/Dvbkd | 20140219 |
| NANO-Antivirus | Trojan.Win32.Sepro.fxoe | 20140219 |
| Norman | Backdoor | 20140219 |
| Panda | Bck/Sepro | 20140218 |
| Qihoo-360 | HEUR/Malware.QVM19.Gen | 20140219 |
| Rising | PE:Trojan.Win32.Generic.122D100D!304943117 | 20140218 |
| Sophos | Troj/Bdoor-DV | 20140219 |
| Symantec | IRC.SRVCP.Trojan | 20140219 |
| TheHacker | Backdoor/Sepro.c | 20140218 |
| TrendMicro | BKDR_SRVCP | 20140219 |
| TrendMicro-HouseCall | BKDR_SRVCP | 20140219 |
| VBA32 | Backdoor.Sepro | 20140219 |
| VIPRE | Trojan.Win32.Ircbot!cobra (v) | 20140219 |
| ViRobot | Backdoor.Win32.A.Sepro.28704 | 20140219 |
| nProtect | Backdoor/W32.Sepro.28704.B | 20140218 |
| ByteHero | 20140219 | |
| ClamAV | 20140219 | |
| SUPERAntiSpyware | 20140219 | |
| TotalDefense | 20140218 |
Behavioral analysis
IRC traffic
IRC traffic to irc.mcs.net:
NICK :mikey USER Ah Ah Ah :fight me, pussy JOIN #daFuck :remnux. NOTICE Auth :*** Looking up your hostname... :remnux. NOTICE mikey :*** Skipping host resolution (disabled by server administrator) :remnux. 451 JOIN :You have not registered :remnux. NOTICE Auth :Welcome to .REMnux IRC Network.! :remnux. 001 mikey :Welcome to the REMnux IRC Network IRC Network mikey!Ah@0::ffff:192.168.102.129 :remnux. 002 mikey :Your host is remnux., running version InspIRCd-1.1 :remnux. 003 mikey :This server was created 17:24:15 Apr 16 2012 :remnux. 004 mikey remnux. InspIRCd-1.1 inosw bhiklmnopstv bhklov :remnux. 005 mikey WALLCHOPS WALLVOICES MODES=19 CHANTYPES=# PREFIX=(ohv)@%+ MAP MAXCHANNELS=20 MAXBANS=60 VBANLIST NICKLEN=31 CASEMAPPING=rfc1459 STATUSMSG=@%+ CHARSET=ascii :are supported by this server :remnux. 005 mikey TOPICLEN=307 KICKLEN=255 MAXTARGETS=20 AWAYLEN=200 CHANMODES=b,k,l,imnpst FNC NETWORK=REMnux IRC Network MAXPARA=32 ELIST=MU :are supported by this server :remnux. 375 mikey :remnux. message of the day :remnux. 372 mikey :- :remnux. 376 mikey :End of message of the day. :remnux. 251 mikey :There are 1 users and 0 invisible on 1 server :remnux. 255 mikey :I have 1 clients and 0 servers JOIN #daFuck :mikey!Ah@0::ffff:192.168.102.129 JOIN :#daFuck :remnux. 353 mikey = #daFuck :@mikey :remnux. 366 mikey #daFuck :End of /NAMES list. NICK mikey NICK mikey NICK mikey NICK mikey NICK mikey NICK mikey NICK mikey NICK mikey
Decoded strings
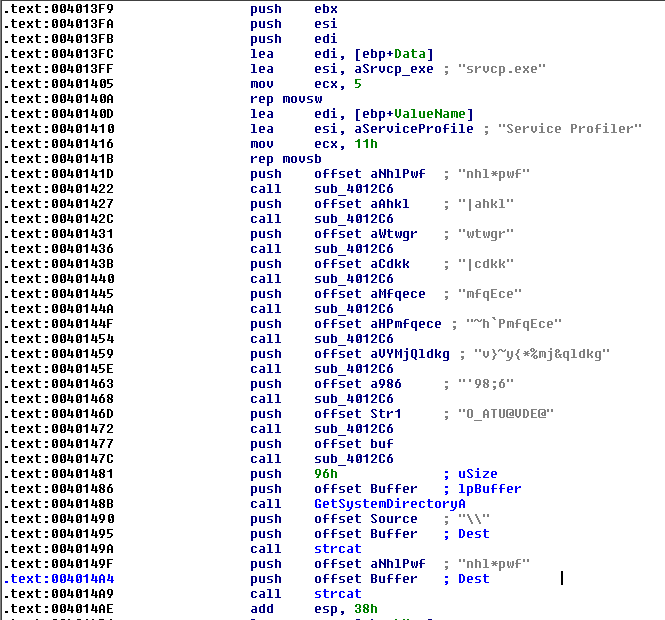
Many strings in the code are encoded:
Following the analysis here, we can write a script that will decode the strings:
#!/usr/bin/env python
import sys
def decodestring(s):
l = len(s)
tmp = ""
for counter in range(1,l+1):
tmp += chr(ord(s[l-counter])^counter )
return tmp
f = sys.stdin.readlines()
for l in f:
s = l.split("\n")[0]
print "%s\t\t| %s" % (s, decodestring(s))
Here is an extract from the decoded strings:
$ strings /data/malware/srvcp.exe | ./decodestring.py
[SNIP]
nhl*pwf gus.ini
|ahkl mikey
wtwgr setpr
[SNIP]
mfqEce daFuck
~h`PmfqEce daFuckWhat
v}~y{*%mj&qldkg fight me, pussy
[SNIP]
og&teh*`ph irc.mcs.ne
O_ATU@VDE@ AGGRESSIVE
[SNIP]
Decoded configuration file
The malware is based on a configuration file that is encoded:
JexO215WuK60H7HgI.j11vh1 Or6ZF1EY6FP/Esknw.4bCXN. Rzply/0QhQ9/Dul3j1ex9J2. jCggY1dbThf/7FoGR/5IYU/. HBtJI.zWZtP/e1zcT/nCMAf0Osi.K.vC3lT1 ZC8YD.MBoxJ.wtPW61fAKYi1Vnu6H/yPVda. YxPgS13wXdq0m4SMh/4NhJj0hN2gw/J/L.W1 fVN.20dmo331uJaSo/CoFfs1RYrQy.lHqPM.bjDB6.d22dU. YtqCd0dK7Ts1Ej1ZC0SplR2/pdxlr/i.KQu1L8JvE0iBK82/ aoQLZ/DVMQD0CWVM8.x1CkA0oEMAd.bf8PG13y62h0YUKEV. pNdkb0wdFFa.mcNo21rXfue/gz6OS/jjCvK.0fNC50tvylg0 Erre71dq9e80r/Z1k.ZxMC4/IbM24/jNtv100fNC50tvylg0 w1UOB1pMDRr.OqcNd.5sPlg/dFB9Z0p4z3J.AyQVA1f1nog. SAoWF06ysjk.ATOHB/OwpNn.GBKBQ.lT9ac.j3gqy0ZZj8T0 iS5p5.APaU918QMt5/rUrqf1CZq6V.HvXaO10fNC50tvylg0 IqmDK175dGq/Ow9v9/mf9qh0s9/Fh.peG6R.AyQVA1f1nog. N5T0C/1u1bE0U2GFX0MZh5w/fMjQP/niXB313E0aH/xnUxd1 MalYj1fUwXM.uLcZ/0.TBli1KK/Ky/4m/BN.AyQVA1f1nog. 1g5tU1fq2li/wb0G1/S6wyW/8Yvoz0NqvDQ/bjDB6.d22dU. DSvu2/EYtmt/U7Q08.WyTaM/nZ32s1RLavG/FTYri1vWkZ31 ImlGa/nWGqi0JoaQo/q/X9V04k6mG.DkBte/B5te0.IWVT.0AyQVA1f1nog. ZKo4Y/4NVr50g.CdC11I4Rb1ukUWM0VIUYi0WAuXO/aHA8//FTYri1vWkZ31 1Dnc519RXj5/ZKYj.1RgFD11X4yan/uhZ2u10fNC50tvylg0 PMAn9.Z2Ang/Z0AGn.BZBjX/SrsHz.sXA9C/bjDB6.d22dU. 4tp8F0fi5v90K4S321M.Qmk.WSrZw0TeLGA0FTYri1vWkZ31 ruWga099oyZ1Ip5Q5/q8X.x0SGIr812OzqV00fNC50tvylg0 j0M3j.dmXdW.7PMpV/js0Mb1ukUWM0VIUYi0WAuXO/aHA8//FTYri1vWkZ31 te9Vc.U0v5q.T8muJ/pos1Z/YYobk/NsEF50 aRER8.2gZ8z.pA31t0Qz2R0/UI8xj.kS45F0 a9Kbt//i7Wy.gkfbn0t8lUZ/TUkG40gfzWT0FTYri1vWkZ31 TTuC709yXN2.SwLbF0i/U1C/6UJKy.piaMQ.NNDAD/Y2LD0. PTRNt/fXRae1PAI5F.wwdIr0mgv9m1L7nSH1a5wCd1/8uAA. FnmOh0pKIfn.DZpnf1IiWbK.ZVT8I.dBehy/zpVde/NZHSL. 6BCxZ1a6a8//QGUCq/t2ooq1if/IH.VP0Uy0FTYri1vWkZ31 s7Y5O12/86o15cBz41N2RTI1JZtph1ZHoyk1a5wCd1/8uAA. Iukwg1im4L516hjV6/Qts2v/sRbJq1qOJLS.NNDAD/Y2LD0. TKc95/h7wLG16nZXa0qfCXP0NP/n614tzX1/3y62h0YUKEV. u1mwB.Pe54F0EzEoR0jQvyP.fPzG5.fqrcc/FTYri1vWkZ31 7pwcx1eO.wz/zGSxu1d8RCc/krKD8.1FtZ2/NNDAD/Y2LD0. 98tq41asCYH/L3rcJ/Fim/z0jBSPS/013o5.NNDAD/Y2LD0.
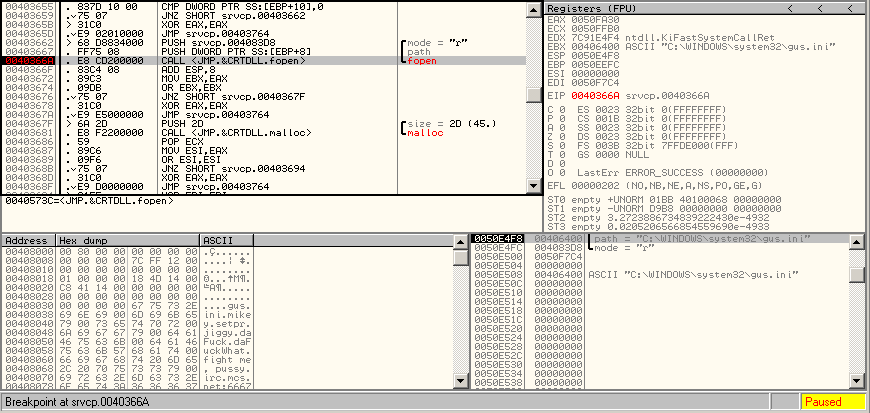
To decode it, let's use OllyDbg and set up a breakpoint where the file is called:
IDA-Pro also tells us that fscanf is called with the following parameter: %[^\n]\n. This is where the line of the configuration file is read. And loc_4036B2 is the address of the decoding function.
.text:00403732 loc_403732:
.text:00403732 lea eax, [ebp+var_414]
.text:00403738 push eax
.text:00403739 push offset asc_4083D1 ; "%[^\n]\n"
.text:0040373E push ebx ; File
.text:0040373F call fscanf
.text:00403744 add esp, 0Ch
.text:00403747 cmp eax, 0FFFFFFFFh
.text:0040374A jnz loc_4036B2
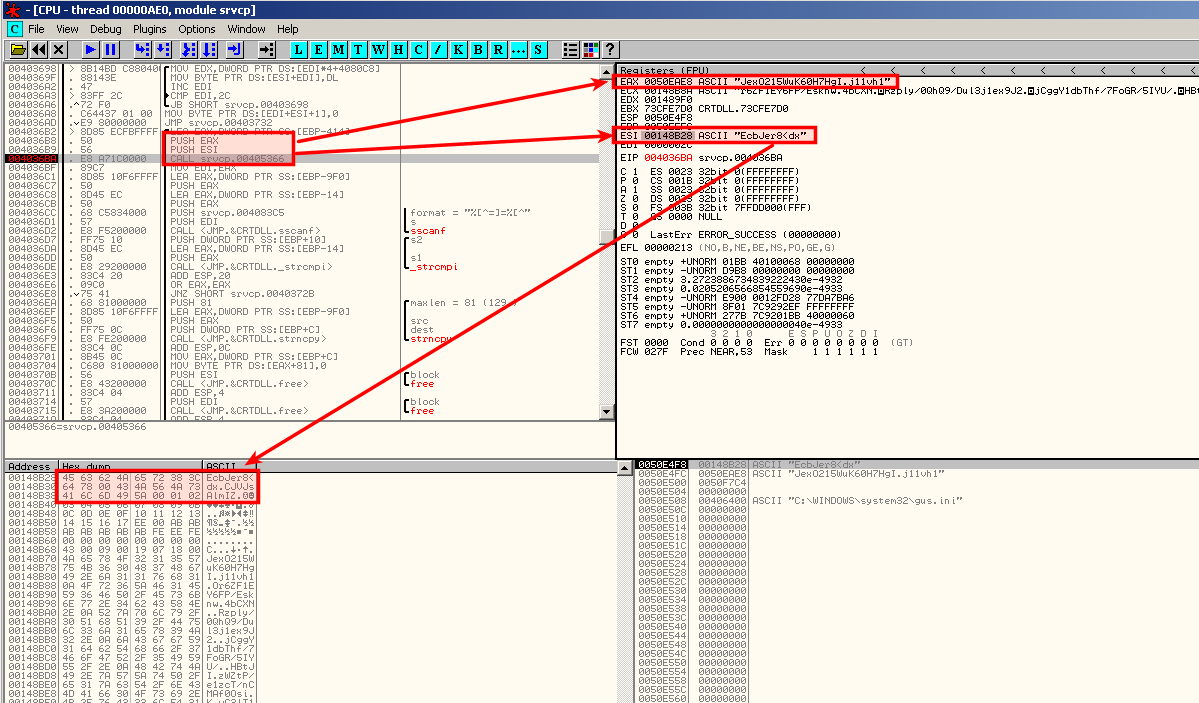
The instructions at address 0x4036B2 confirm that the function that decode the lines is sub_405366:
.text:004036B2 lea eax, [ebp+var_414]
.text:004036B8 push eax
.text:004036B9 push esi
.text:004036BA call sub_405366
.text:004036BF mov edi, eax
.text:004036C1 lea eax, [ebp+Source]
.text:004036C7 push eax
.text:004036C8 lea eax, [ebp+Str1]
.text:004036CB push eax
.text:004036CC push offset asc_4083C5 ; "%[^=]=%[^"
.text:004036D1 push edi ; Src
.text:004036D2 call sscanf
The sscanf function receives the "%[^=]=%[^" parameter that is very likely to be a kind of "parameter=value" commonly seen in configuration files.
As you can see on the above screenshot, sub_405366 accepts 2 parameters:
- EAX stores the encoded line of the configuration file
- ESI stores the decoding key (see the follow in dump complete key)
Once decoded, the configuration file is:
NICK=mikey MODE=AGGRESSIVE SETCOMMAND=setpr COMMAND=fuckedup CHANNEL=mikag soup SOUPCHANNEL=alphasoup ah SERVER0=irc.mcs.net:6666 SERVER1=efnet.cs.hut.fi:6666 SERVER2=efnet.demon.co.uk:6666 SERVER3=irc.concentric.net:6666 SERVER4=irc.etsmtl.ca:6666 SERVER5=irc.fasti.net:6666 SERVER6=irc.idle.net:6666 SERVER7=irc.powersurfr.com:6666 SERVER8=irc.total.net:6666 SERVER9=irc.core.com:6666 SERVER10=irc.inter.net.il:6666 SERVER11=irc.umn.edu:6666 SERVER12=irc.prison.net:6666 SERVER13=irc.isdnet.fr:6666 SERVER14=irc.ced.chalmers.se:6666 SERVER15=irc-e.frontiernet.net:6666 SERVER16=irc.best.net:6666 SERVER17=irc.exodus.net:6666 SERVER18=irc.enitel.no:6666 SERVER19=irc.telia.se:6666 SERVER20=irc-w.frontiernet.net:6666 SERVER21=irc.du.se:6666 SERVER22=irc.rt.ru:6666 SERVER23=irc.freei.net:6666 SERVER24=irc.homelien.no:6666 SERVER25=irc.colorado.edu:6666 SERVER26=irc.mindspring.com:6666 SERVER27=irc.umich.edu:6666 SERVER28=irc.stanford.edu:6666 SERVER29=irc.nethead.com:6666 SERVER30=irc.lightning.net:6666 SERVER31=irc.emory.edu:6666 SERVER32=irc.spynet.com:6666 SERVER33=ircd.lagged.org:6666