FU-Rootkit
Jump to navigation
Jump to search
Description
Fu is one of the most widely utilized rootkits in the wild. Other malware, such as rbot and sdbot variants, have used its features to hide themselves. Fu is a kernel-mode rootkit that modifies kernel data structures, which allows it to hide e.g. processes.
fu.exe and msdirectx.sys work as one. fu.exe passes down parameters as IOCTL's to the msdirectx.sys driver. As such, once the driver is loaded, you do not need any special privilege to run fu.exe. msdirectx.sys is the driver and does all the work of fu.exe. The driver is never unloaded until reboot.
Installation
Usage
Syntax
Usage: fu.exe [options]
Options
- -pl <#number>
- to list the first #number of processes
- -ph <#PID>
- to hide the process with #PID
- -pld
- to list the named drivers in DbgView
- -phd <DRIVER_NAME>
- to hide the named driver
- -pas <#PID>
- to set the AUTH_ID to SYSTEM on process #PID
- -prl
- to list the available privileges
- -prs <#PID> <#privilege_name>
- to set privileges on process #PID
- -pss <#PID> <#account_name>
- to add #account_name SID to process #PID token
Examples
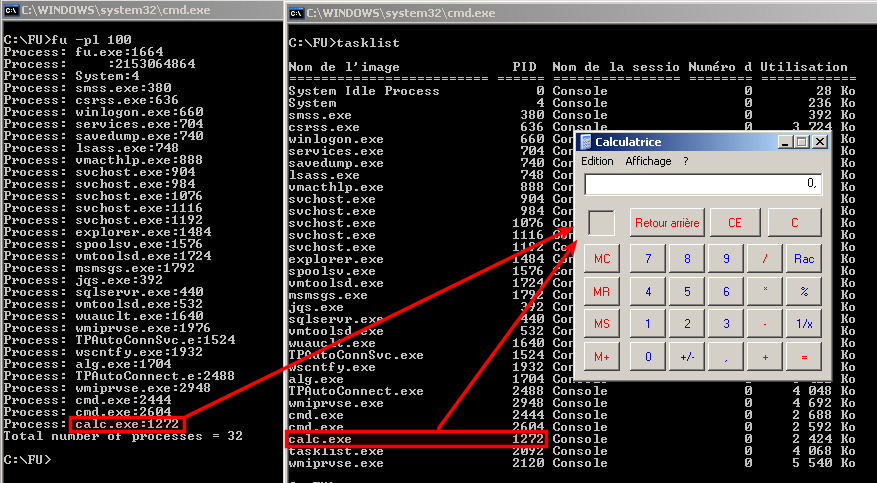
List processes
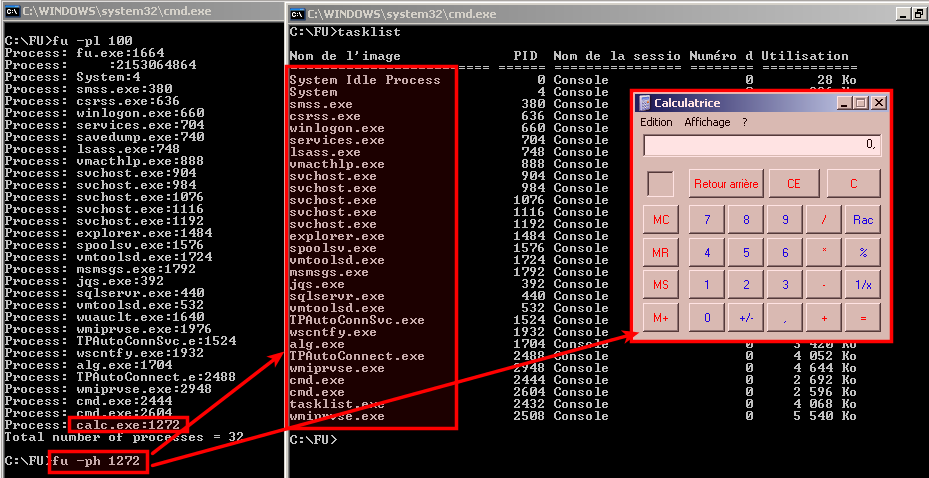
Hide process
In the below screenshot, we have hidden process 1272 (-ph 1272). As shown by the tasklist command, calc.exe does not appear anymore though the GUI is still active.
List privileges
C:\FU>fu -prl SeCreateTokenPrivilege SeAssignPrimaryTokenPrivilege SeLockMemoryPrivilege SeIncreaseQuotaPrivilege SeUnsolicitedInputPrivilege SeMachineAccountPrivilege SeTcbPrivilege SeSecurityPrivilege SeTakeOwnershipPrivilege SeLoadDriverPrivilege SeSystemProfilePrivilege SeSystemtimePrivilege SeProfileSingleProcessPrivilege SeIncreaseBasePriorityPrivilege SeCreatePagefilePrivilege SeCreatePermanentPrivilege SeBackupPrivilege SeRestorePrivilege SeShutdownPrivilege SeDebugPrivilege SeAuditPrivilege SeSystemEnvironmentPrivilege SeChangeNotifyPrivilege SeRemoteShutdownPrivilege SeUndockPrivilege SeSyncAgentPrivilege SeEnableDelegationPrivilege