IsDebuggerPresent
Description
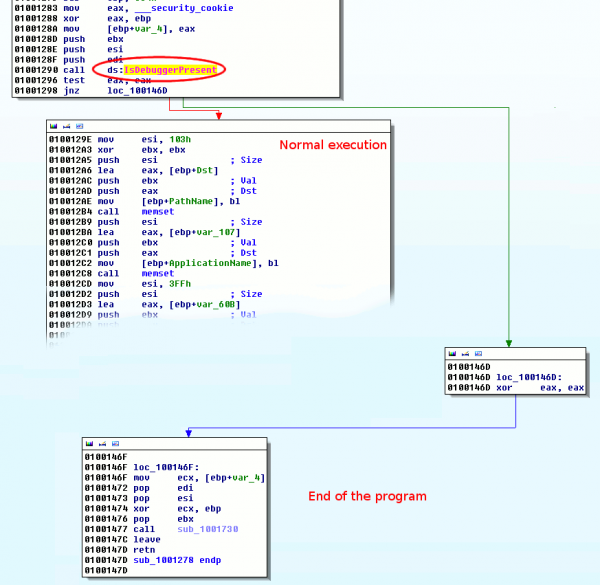
IsDebuggerPresent is a function available in the kernel32.dll library. This function is often used in malware to complexify the reverse engineering because it will take different paths in the program's flow when the malware is analyzed in a user-mode debugger such as OllyDbg.
Syntax
BOOL WINAPI IsDebuggerPresent(void);
Parameters
This function has no parameters.
Return value
If the current process is running in the context of a debugger, the return value is nonzero.
If the current process is not running in the context of a debugger, the return value is zero.
Bypass IsDebuggerPresent
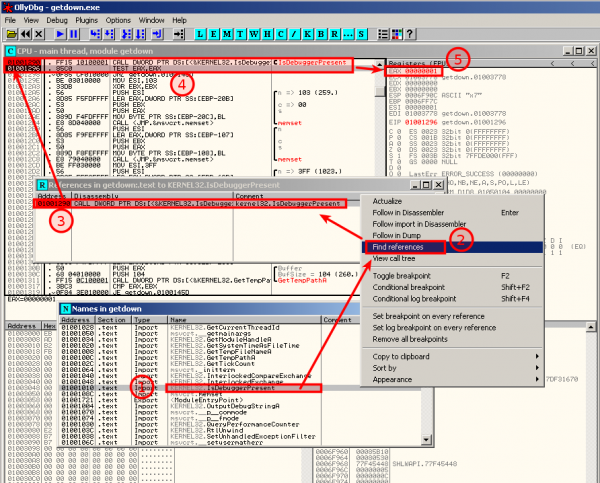
OllyDbg plugins
You can use OllyDbg plugins:
Patching
Modify the value of registers while running the malware
|
|
Permanently patch the malware
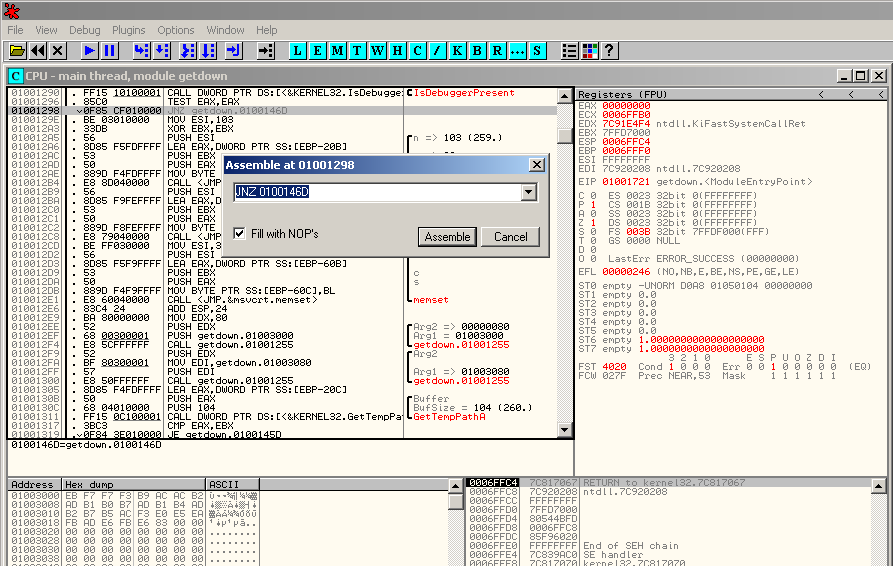
Another way consists in permanently patch the malware so that it won't have the opportunity to jump to the end of the program if IsDebuggerPresent returns a positive value. To do so, go to the function's call, select the line where the JUMP is taken, right click on it and select "Assemble", or just press "Space":
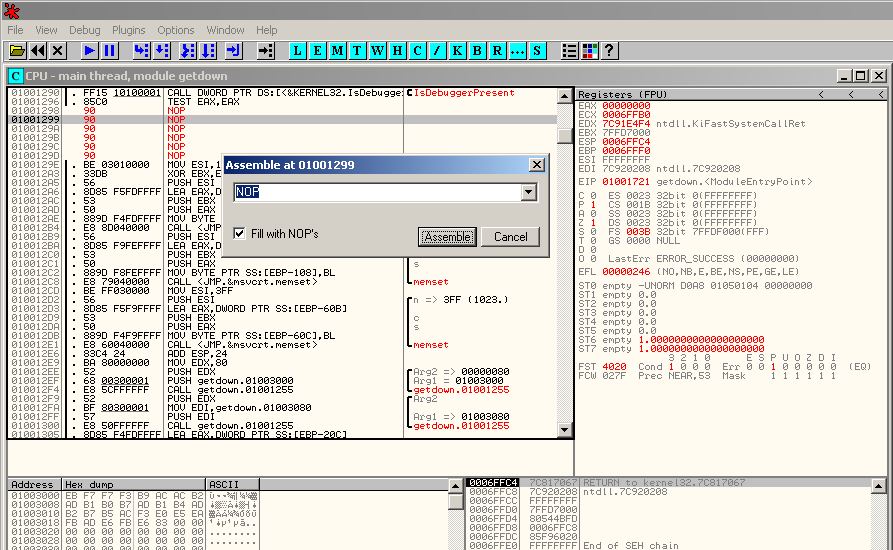
Then update the value to NOP. Press "Assemble" and then "Cancel":
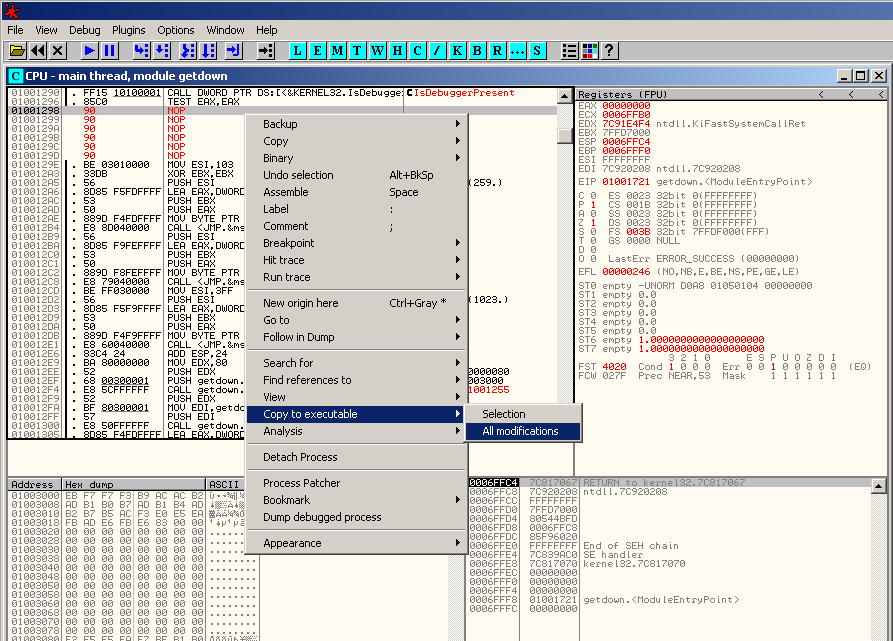
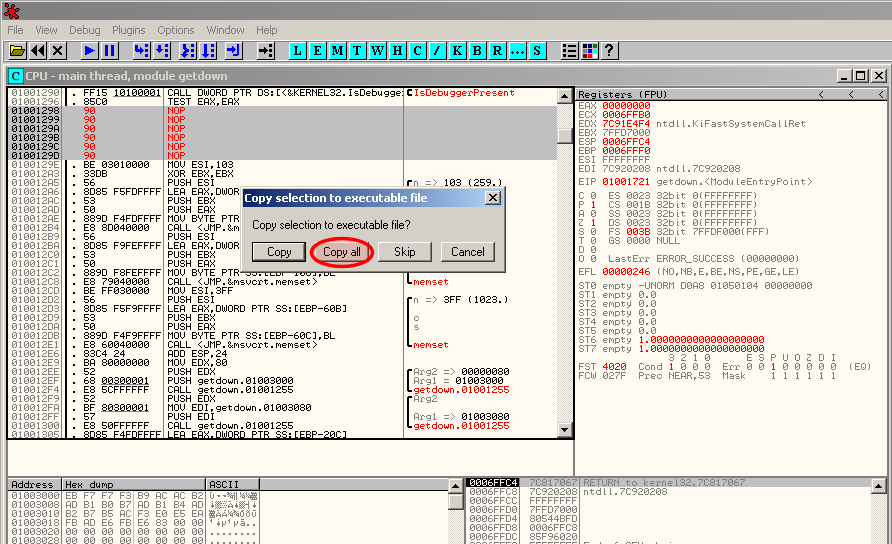
To save the modifications to disk, right click in the disassembler pane and select Copy to executable > All modifications:
Then select "Copy All":
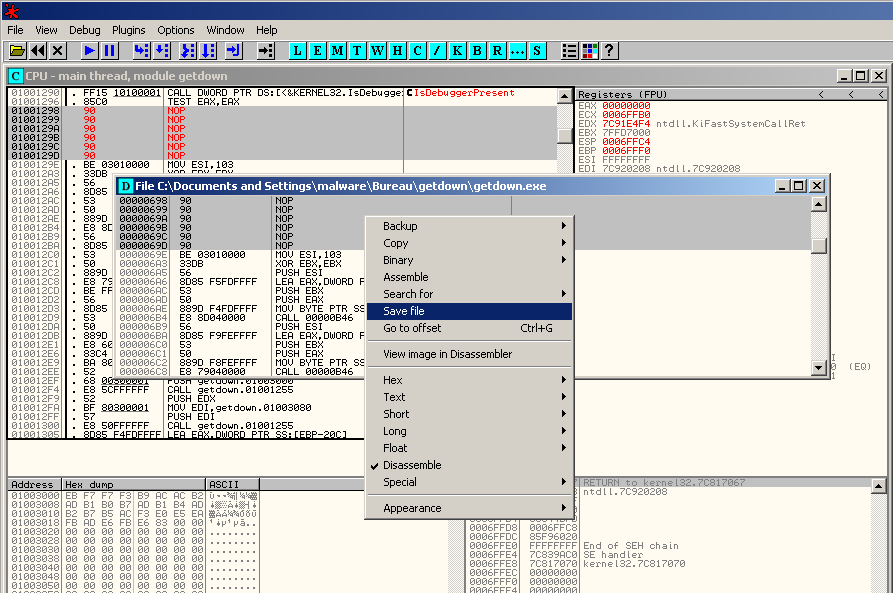
In the new window, right click and select "Save file":
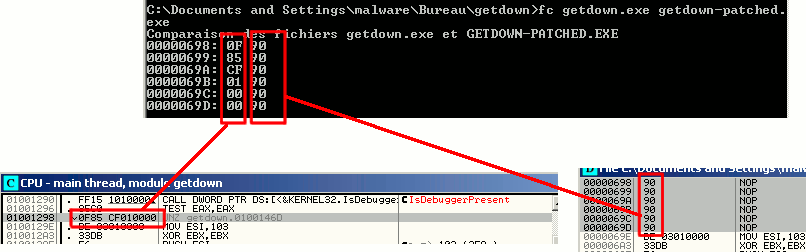
On Windows, the fc command can show the differences: