KInject
Jump to navigation
Jump to search
Description
kInject allows you to inject an arbitrary DLL into an arbitrary process. For more information about injecting DLLs, please refer to this page.
Installation
- Download link: https://dl.dropboxusercontent.com/u/10761700/kinject.zip (password to unzip: malware)
Usage
Syntax
kInject.exe [process path/Pid] [dll path] [--create / --runtime] [--resolve] [--force]
Options
- --create
- program will create the process before injecting
- --runtime
- inject already existing process
- --resolve
- get process id from executable name
- --force
- load SeDebugPrivilege to break into target process
Example
Proof of Concept
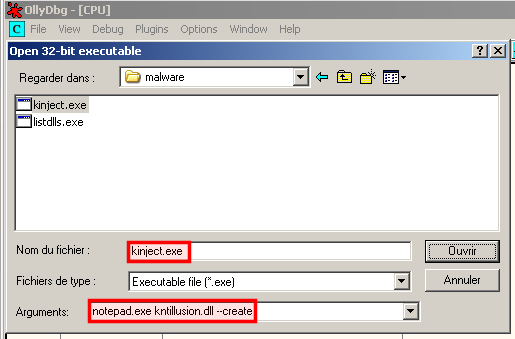
In this example, we will inject kntillusion.dll into notepad.exe. Let's do it as follows:
C:\malware>kinject.exe notepad.exe kntillusion.dll --create ** Running kInject v1.0 by Kdm ([email protected]) ** Creating process notepad.exe... OK. Injecting DLL kntillusion.dll... OK
As a consequence to the above command, notepad has been opened and, as you can see, Listdlls (Sysinternals) confirms that the DLL has successfully been injected into the process:
C:\malware>listdlls.exe -d kntillusion.dll ListDLLs v2.25 - DLL lister for Win9x/NT Copyright (C) 1997-2004 Mark Russinovich Sysinternals - www.sysinternals.com ------------------------------------------------------------------------------ notepad.exe pid: 1780 Command line: notepad.exe Base Size Version Path 0x10000000 0x10000 C:\malware\kntillusion.dll
Explanation
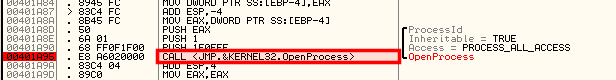
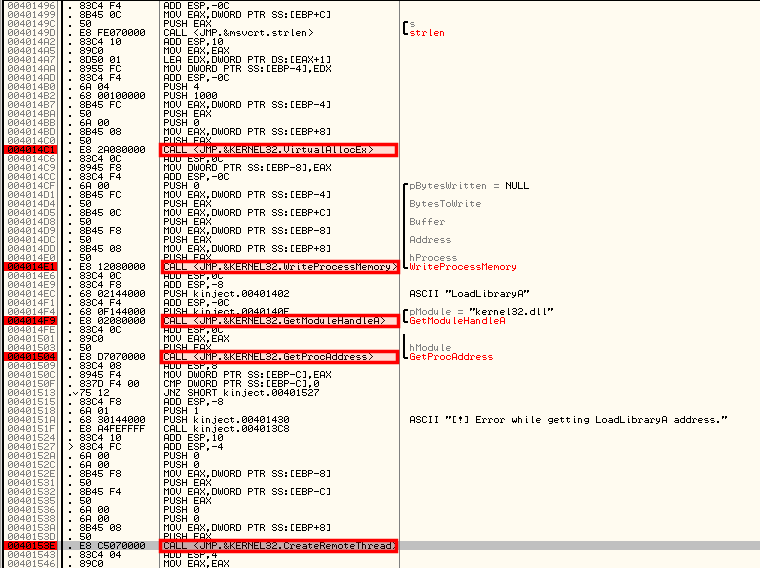
Let's open kinject.exe into OllyDbg to see what happens:
Let's try to find the different steps explained in the CreateRemoteThread technique:
|