Mac-address-virtualization-detection
Description
The first three bytes of a MAC address are typically specific to the vendor. A public list is available here: http://standards-oui.ieee.org/oui.txt.
Malware can use this technique to determine if it is run inside VMware:
$ wget http://standards-oui.ieee.org/oui.txt $ grep "00-0C-29" oui.txt 00-0C-29 (hex) VMware, Inc.
Below are some more examples of the 3 first bytes associated to VMware:
$ egrep "\(hex\)\s+VMware" oui.txt 00-05-69 (hex) VMware, Inc. 00-0C-29 (hex) VMware, Inc. 00-1C-14 (hex) VMware, Inc 00-50-56 (hex) VMware, Inc.
Example
Below is a full example that shows how malware can get the 3 first bytes of a mac address to determine whether it corresponds to VMware. This example is an extract from Lab17-03 from the "Practical Malware Analysis" book.
GetAdaptersInfo
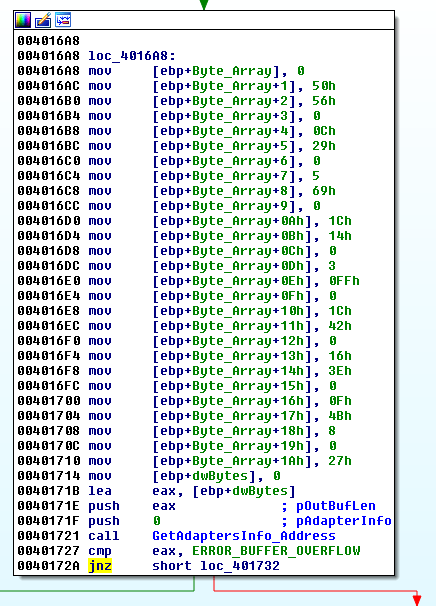
First of all, an array of possible VMware related mac addresses is built (items will be grouped by 3: {00h,50h,56h}, {00h,0Ch,29h}, ...) and GetAdaptersInfo is called with a NULL pointer (pAdapterInfo). This is a technique that will generate an error (ERROR_BUFFER_OVERFLOW) but will fill dwBytes with the number of bytes to be allocated.
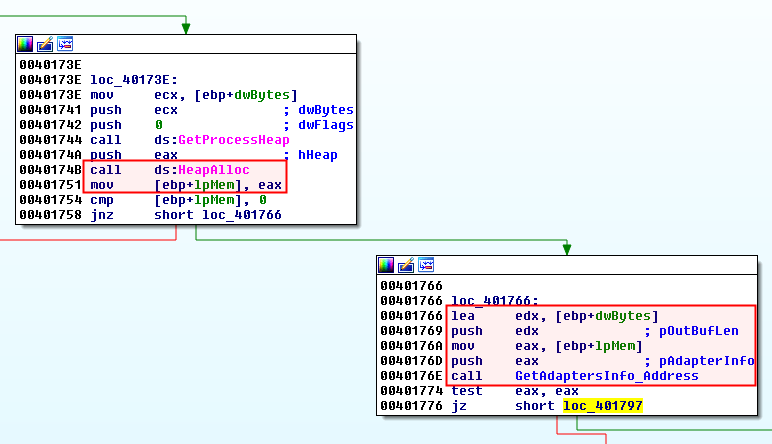
The bytes are then allocated with GetProcessHeap and HeapAlloc. GetAdaptersInfo is then called a second time, but this time, with the correct parameters:
After the call to GetAdaptersInfo_Address, the lpMem parameter is a pointer to a linked list of IP_ADAPTER_INFO structures with a size of dwBytes.
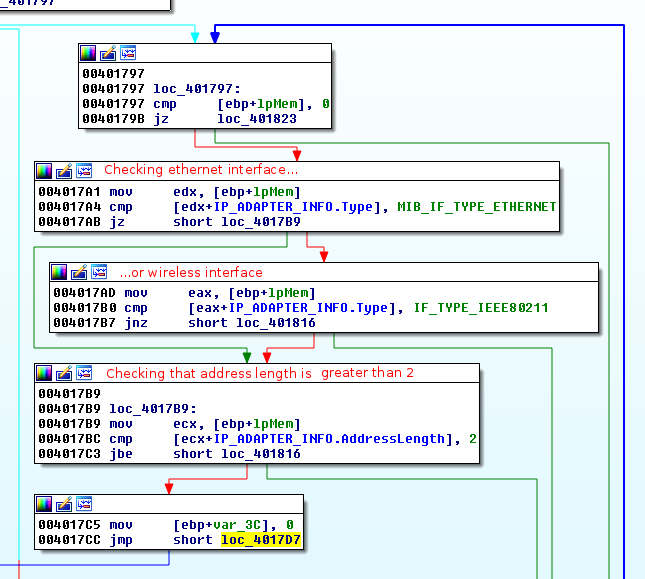
The malware is then cycling through the network interfaces:
Then the malware is checking whether the first 3 bytes of the mac address are found in the array corresponding to the VMware vendor.
.text:004017CC jmp short loc_4017D7
.text:004017CE ; ---------------------------------------------------------------------------
.text:004017CE
.text:004017CE loc_4017CE:
.text:004017CE mov edx, [ebp+var_3C]
.text:004017D1 add edx, 3 ; groups of 3 items in the array
.text:004017D4 mov [ebp+var_3C], edx
.text:004017D7
.text:004017D7 loc_4017D7:
.text:004017D7 cmp [ebp+var_3C], 1Bh ; Cycle thru 27 items of array
.text:004017DB jnb short loc_401816
.text:004017DD mov ecx, 3
.text:004017E2 mov eax, [ebp+var_3C]
.text:004017E5 lea edi, [ebp+eax+ByteArray]
.text:004017E9 mov esi, [ebp+lpMem]
.text:004017EC add esi, IP_ADAPTER_INFO.Address
.text:004017F2 xor edx, edx
.text:004017F4 repe cmpsb
.text:004017F6 jnz short loc_401814