Category:Digital-Forensics/Computer-Forensics/Anti-Reverse-Engineering/Anti-VM
Description
Many Virtual Machine Environent (VME) are easily detectable:
- file system
- services (e.g. VMtools)
- hardware (e.g. mac address)
- registry keys
Read this document for more information: http://handlers.sans.edu/tliston/ThwartingVMDetection_Liston_Skoudis.pdf
Highlight Anti-VM in IDA Pro
The following python script will scan the assembly code in IDA-Pro and highlight instructions corresponding to Anti-VM techniques.
"""
Source: Practical Malware Analysis
"""
from idautils import *
from idc import *
heads = Heads(SegStart(ScreenEA()), SegEnd(ScreenEA()))
antiVM = []
for i in heads:
if (GetMnem(i) == "sidt" \
or GetMnem(i) == "sgdt" \
or GetMnem(i) == "sldt" \
or GetMnem(i) == "smsw" \
or GetMnem(i) == "str" \
or GetMnem(i) == "in" \
or GetMnem(i) == "cpuid"):
antiVM.append(i)
print "Number of potential Anti-VM instructions: %d" % (len(antiVM))
for i in antiVM:
SetColor(i, CIC_ITEM, 0x0000ff)
Message("Anti-VM: %08x\n" % i)
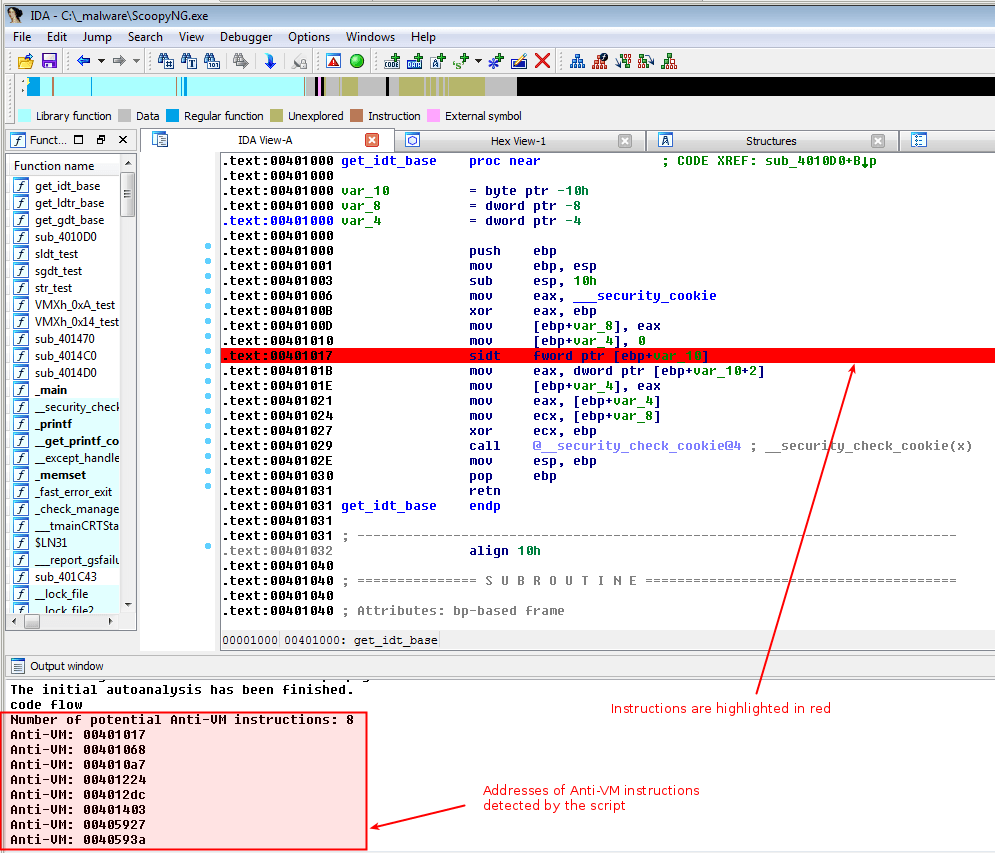
Below is the result of the script once executed:
Tweak VMware settings

You can tweak VMware settings (edit the *.vmx file) to help mitigate the detection. Add the following lines:
These settings are used by VMware backdoor commands so that VMware Tools running in the guest cannot get information about the host:
isolation.tools.getPtrLocation.disable = "TRUE" isolation.tools.setPtrLocation.disable = "TRUE" isolation.tools.setVersion.disable = "TRUE" isolation.tools.getVersion.disable = "TRUE"
The directexec parameter causes user-mode code to be emulated, instead of being run directly on the CPU, thus thwarting certain anti-VM techniques:
monitor_control.disable_directexec = "TRUE"
You can also add these settings:
monitor_control.disable_chksimd = "TRUE" monitor_control.disable_ntreloc = "TRUE" monitor_control.disable_selfmod = "TRUE" monitor_control.disable_reloc = "TRUE" monitor_control.disable_btinout = "TRUE" monitor_control.disable_btmemspace = "TRUE" monitor_control.disable_btpriv = "TRUE" monitor_control.disable_btseg = "TRUE"
Pages in category "Digital-Forensics/Computer-Forensics/Anti-Reverse-Engineering/Anti-VM"
The following 18 pages are in this category, out of 18 total.