OEP-Original-Entry-Point
Jump to navigation
Jump to search
Description

INCOMPLETE SECTION OR ARTICLE
This section/article is being written and is therefore not complete.
Thank you for your comprehension.
Thank you for your comprehension.
Finding the OEP (Original Entry Point)
pescanner.py
$ ./pescanner.py Lab14-02.exe ################################################################################ Record 0 ################################################################################ Meta-data ================================================================================ File: /data/documents/malware-analysis/BinaryCollection/Chapter_14L/Lab14-02.exe Size: 6656 bytes Type: PE32 executable (GUI) Intel 80386, for MS Windows MD5: 14d4bdcc5f0fe917abde4b01e39a350e SHA1: a2a7352960517502487fb46253a057f51872625e ssdeep: Date: 0x496558BC [Thu Jan 8 01:37:00 2009 UTC] EP: 0x4019fe .text 0/4 CRC: Claimed: 0x0, Actual: 0x1e86 [SUSPICIOUS] Packers: Microsoft Visual C++ v6.0 Resource entries ================================================================================ Name RVA Size Lang Sublang Type -------------------------------------------------------------------------------- RT_STRING 0x4058 0x5a LANG_ENGLISH SUBLANG_ENGLISH_US data Suspicious IAT alerts ================================================================================ CreateProcessA ShellExecuteExA InternetOpenUrlA InternetOpenA Sections ================================================================================ Name VirtAddr VirtSize RawSize Entropy -------------------------------------------------------------------------------- .text 0x1000 0xb8c 0xc00 6.052097 .rdata 0x2000 0x5f6 0x600 4.987689 .data 0x3000 0xc4 0x200 2.118812 .rsrc 0x4000 0xb8 0x200 0.912837 [SUSPICIOUS]
IDA Pro
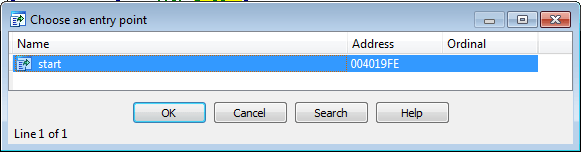
In IDA-Pro, go to Jump > Jump to entry point or press Ctrl + E to reach the entry point:
OllyDbg - SFX
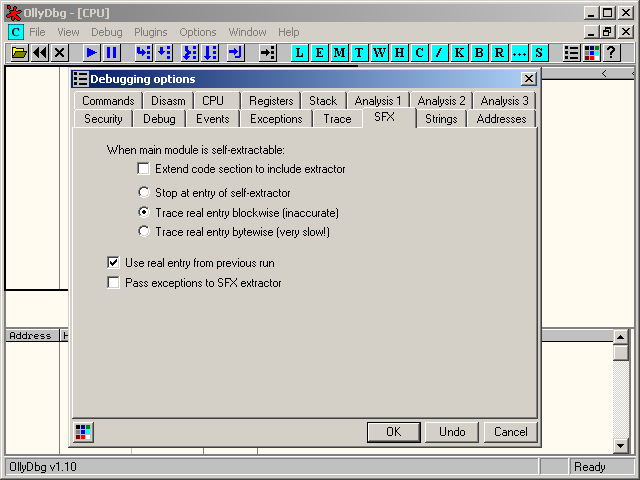
When an executable is unpacked, OllyDbg will pause at the entry point. In case of packed executable, the SFX option will help finding the OEP.
Go to Options > Debugging Options > SFX and check one of these options:
- Trace real entry blockwise: this method is quicker but inaccurate
- Trace real entry bytewise: this method will be accurate but slow
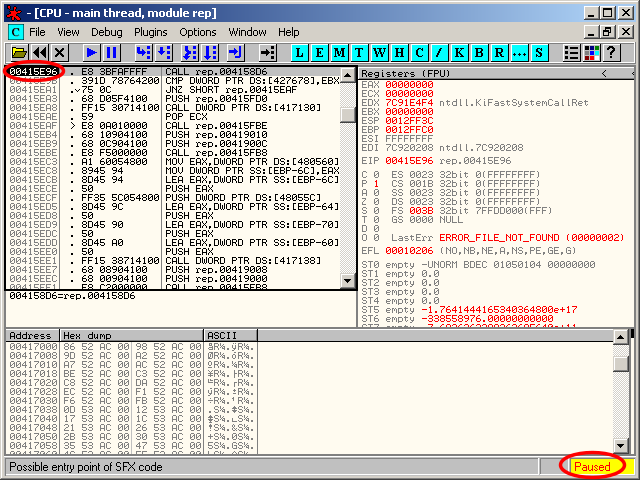
After a short while, OllyDbg pauses at the found EOP: