TLS-callback
Jump to navigation
Jump to search
Description
Among the different anti-reverse / anti-debugging techniques, there is one which is called the Thread Local Storage (TLS) callback.
TLS callback functions are actually executed before executing code at the traditional Original Entry Point (OEP).
Bypassing the TLS callback anti-debugging technique
Modifying OllyDbg's default options
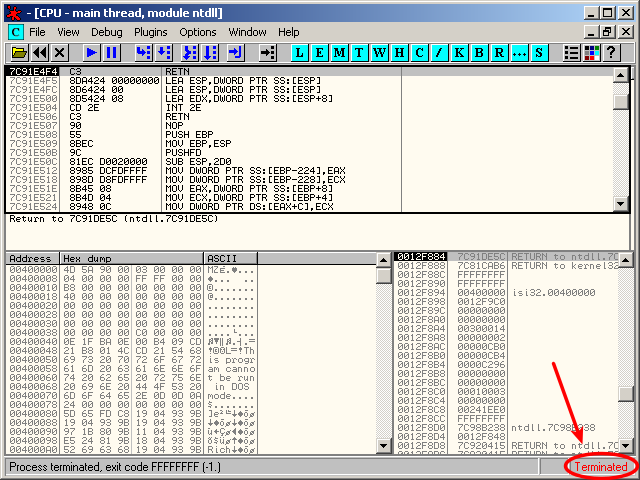
If you try to load such a malware in OllyDbg with the default options, you will notice that it stops (see the Terminated status):
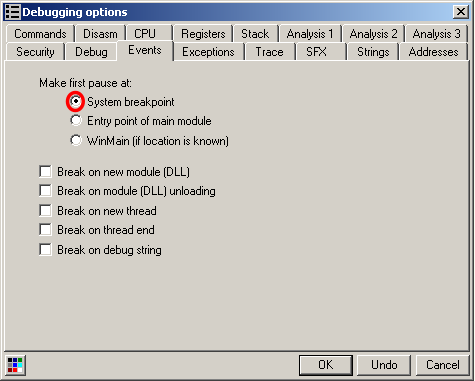
On way to bypass it is to reconfigure OllyDbg to pause at "system breakpoint" instead of the default "WinMain":
Finding the TLS callback
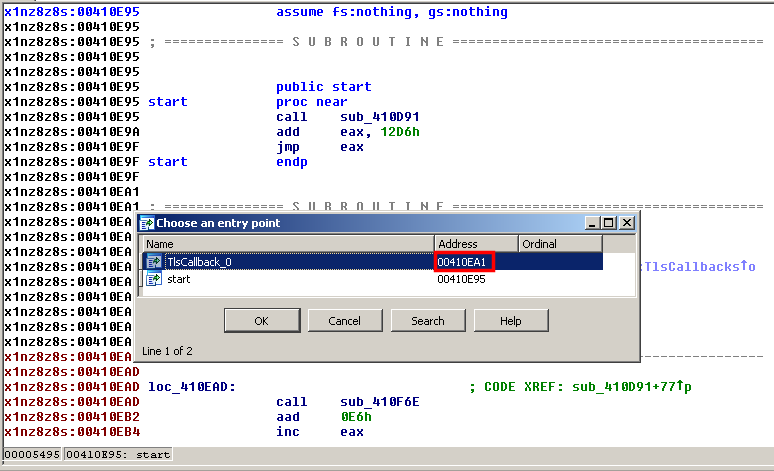
To find the TLS callback, open the malware in IDA Pro and press Ctrl+E:
You can also use pescanner.py:
$ ./pescanner.py /data/tmp/Malware/isi32.exe
################################################################################
Record 0
################################################################################
Meta-data
================================================================================
File: /data/tmp/Malware/isi32.exe
Size: 21873 bytes
Type: PE32 executable (GUI) Intel 80386, for MS Windows
MD5: 7a4d1babde751f080cc65a306a0ae79c
SHA1: dafe57b9c86466f687b91e153bdec7838fb70d35
ssdeep:
Date: 0x47EC14D6 [Thu Mar 27 21:42:46 2008 UTC]
EP: 0x410e95 x1nz8z8s 3/4 [SUSPICIOUS]
CRC: Claimed: 0x13165, Actual: 0x13165
Packers: EXECryptor 2.2.4 -> Strongbit/SoftComplete Development
TLS callbacks
================================================================================
0x410ea1
Sections
================================================================================
Name VirtAddr VirtSize RawSize Entropy
--------------------------------------------------------------------------------
.packed 0x1000 0x7000 0x0 0.000000 [SUSPICIOUS]
.RLPack 0x8000 0x3000 0x0 0.000000 [SUSPICIOUS]
10rntbk3 0xb000 0x1000 0x15 4.070656
x1nz8z8s 0xc000 0x5000 0x4f71 7.961965 [SUSPICIOUS]
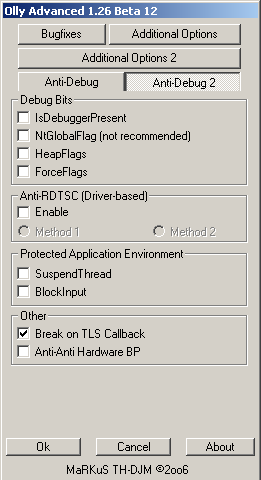
Using Olly Advanced
You can also use the Olly Advanced plugin in OllyDbg to setup the "Break on TLS Callback" option: