The-FLARE-On-Challenge-2015/Challenge-9
| You are here | Challenge 9
|
File
Uncompress 4568CB1948CCD11DDB9B90359F7DC79A.zip (password is "flare") and you will get a file named you_are_very_good_at_this with following properties:
| MD5 | 51105503d77689facbf2b8a8b4fd040b |
|---|---|
| SHA1 | 39cf8909062d191d26bee53658906104f8121528 |
| SHA256 | 9a953f71ab89e7b6336d4efa7be7ee7a8ac466f012b459898320d211e7860b62 |
| File type | PE32 executable (console) Intel 80386, for MS Windows |
Analysis
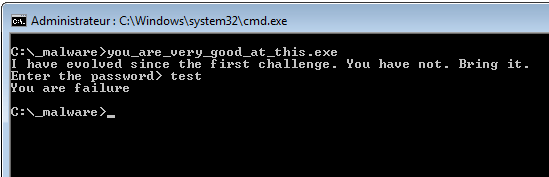
The program is actually prompting for a password interactively and immediately exits if the incorrect password is provided:
Opening the executable in IDA-Pro warns that the import segment is likely to be destroyed and then shows a huge block of obfuscated code.
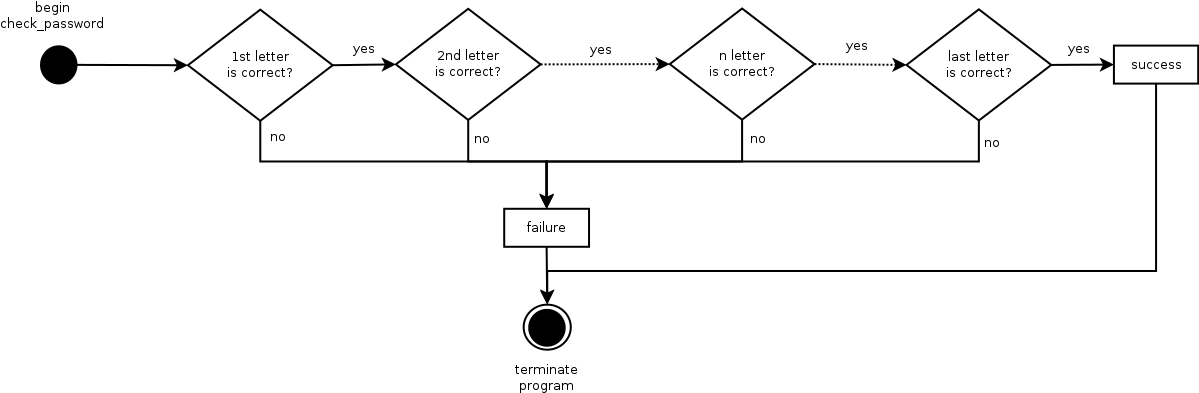
Let's rather take a simple assumption: what about if the password is checked letter by letter? We could imagine the following workflow:
Pintool
Proof of Concept
If our assumption is correct, it's very likely that the workflow associated to a successful letter will be different than the one directly terminating the program. It would imply that the number of instructions would be different for these 2 workflows.
Let's use the incount0.cpp pintool to count the number of instructions and use this as a proof of concept to confirm our initial assumption. If it is correct, we will develop a brute forcer.
Here is the initial test to challenge the 1st letter of the password:
For letter a:
C:\pin>pin.exe -t inscount0.dll -- c:\_malware\you_are_very_good_at_this.exe I have evolved since the first challenge. You have not. Bring it. Enter the password> a..... You are failure C:\pin>more inscount.out Count 32894
For letter b:
C:\pin>pin.exe -t inscount0.dll -- c:\_malware\you_are_very_good_at_this.exe I have evolved since the first challenge. You have not. Bring it. Enter the password> b..... You are failure C:\pin>more inscount.out Count 32894
...and so on, till letter I:
C:\pin>pin.exe -t inscount0.dll -- c:\_malware\you_are_very_good_at_this.exe I have evolved since the first challenge. You have not. Bring it. Enter the password> I.... You are failure C:\pin>more inscount.out Count 32856
We see that the number of instructions when the 1st letter of the password is "I" is different than the one for the other letters. We conclude that our assumption is correct and can develop a bruteforcer based on this proof of concept.
Brute forcer
Below is the code for my brute forcer. It is partially automatized because it is only brute forcing a given position.
# PowerShell script
add-type -AssemblyName System.Windows.Forms
for($i=32; $i -le 126; $i++){
# Bruteforce 1st letter
$pass_guess = [char]$i + ".........."
# Launch pin
Start-Process -FilePath "c:\pin\pin.exe" -ArgumentList "-t inscount0.dll -- ch9.exe" -NoNewWindow
# send user input
start-sleep -Milliseconds 200
[System.Windows.Forms.SendKeys]::SendWait("$pass_guess{ENTER}")
# Read content of file
start-sleep -Milliseconds 200
write-output "---"
Write-Output $pass_guess
Get-Content .\inscount.out
}
Results and solution
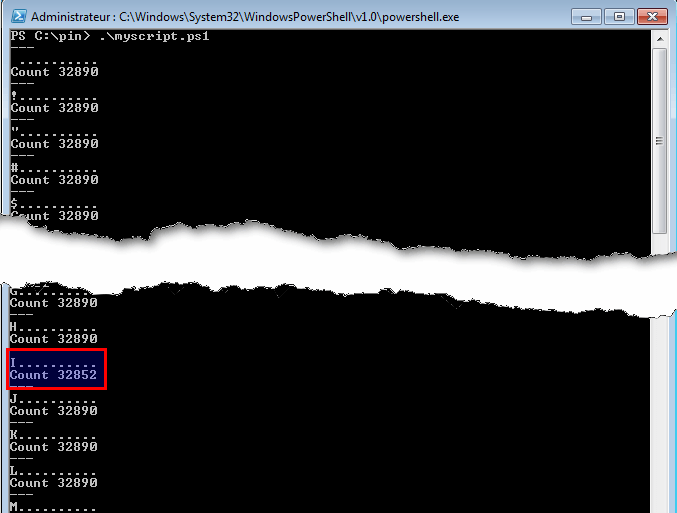
Below is the output from my script for the 1st letter:
We can guess that the 1st letter is I. Now, let's modify the code as follows:
add-type -AssemblyName System.Windows.Forms
for($i=32; $i -le 126; $i++){
# "I" is the first known letter of password. Now bruteforcing 2nd letter
$pass_guess = "I" + [char]$i + ".........."
# Launch pin
Start-Process -FilePath "c:\pin\pin.exe" -ArgumentList "-t inscount0.dll -- ch9.exe" -NoNewWindow
# send user input
start-sleep -Milliseconds 200
[System.Windows.Forms.SendKeys]::SendWait("$pass_guess{ENTER}")
# Read content of file
start-sleep -Milliseconds 200
write-output "---"
Write-Output $pass_guess
Get-Content .\inscount.out
}
Once we have the second letter (s), we change the $pass_guess as follows:
$pass_guess = "Is" + [char]$i + ".........."
Once I arrived at Is_th1s_3v3n_mai_finul_foarm@f, I took the assumption that the remaining characters would be "lare-on.com" and tested...
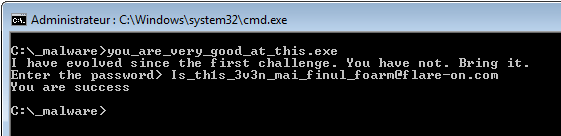
The solution is:
[email protected]
Comments
Keywords: reverse-engineering challenge flare fireeye pin pintools inscount0