WackoPicko/Command-Line-Injection
| You are here: | Command-Line Injection
|
Description
This attack aims at exploiting non-sanitized user content in form fields by injecting arbitrary content.
For web applications, it could lead to complete compromise of the server, including data loss, site defacement and data disclosure.
Proof of Concept
In WackoPicko, the script /passcheck.php suffers from command line injection attack.
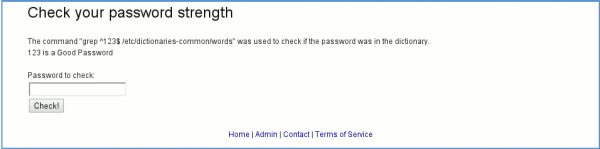
Let's see a *normal* usage. The field enables to enter a string that is then searched in the file /etc/dictionnary-common/words. If the string is found, it is considered as a bad password. On the other hand, it is considered as a good password in the other case (don't use this on a production environment. FYI, "123" is not in that file and is hence considered as a good password ;-)
Here is a portion of the code:
if (isset($_POST['password']))
{
// check the password strength
$pass = $_POST['password'];
$command = "grep ^$pass$ /etc/dictionaries-common/words";
exec($command, $output, $ret);
$checked = true;
}
And here is the *standard* usage:
The command that is sent is:
grep ^123$ /etc/dictionaries-common/words
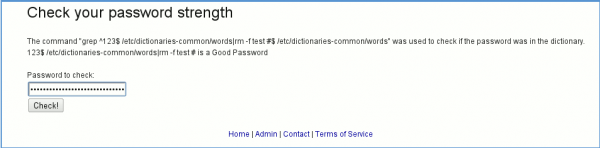
Let's be a little bit more nasty and inject some more content ;-)
This time, here is our command:
The command that is sent is:
grep ^123|rm -f index.php #$ /etc/dictionaries-common/words
How to detect?
How to protect against it?
- Control and purify data that are sent from the browser on server-side.
- Use white lists input validation
- Disable the use of dangerous functions in your php.ini file via the disable_functions directive
- Chroot/jail your server installation