WackoPicko/Multi-Step-Stored-XSS
Jump to navigation
Jump to search
| You are here: | Multi-Step Stored XSS
|
Description
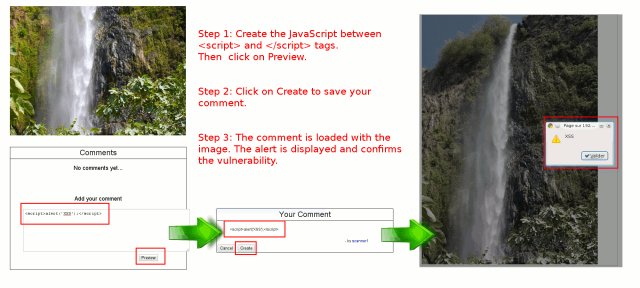
There is a stored XSS vulnerability in the comments page of the images. The comment field is not properly escaped, and therefore, an attacker can exploit this vulnerability by creating a comment containing JavaScript code. Whenever a user loads the page containing the image and its comments, the attack will be triggered and the (possibly malicious) JavaScript code executed.
More information on stored XSS attacks.
Proof of Concept
The content of the comments linked to pictures is not properly sanitized. It enables one to post persistent XSS in the database:
How to detect
How to protect against it?
Code
As you can see in /pictures/view.php, the field "comment" is not sanitized:
if (isset($_GET["picid"]))
{
$pic = Pictures::get_picture($_GET["picid"]);
if (!$pic)
{
$no_pic = True;
}
else
{
$comments = Comments::get_all_comments_picture($pic['id']);
$related = Pictures::get_some_pictures_by_tag($pic['tag'], $pic['id'], 2);
$same = Pictures::get_some_pictures_by_user($pic['user_id'], $pic['id'], 2);
}
}
else
{
$no_pic = True;
}
if ($no_pic)
{
error_404();
}
?>
<?php our_header(); ?>
<div class="column prepend-1 span-14 first" >
<h2 id="image-title"><?=h( $pic['title'] )?> </h2>
<img id="image" src="../upload/<?=h( $pic['filename'] )?>.550.jpg" width="550" />
<div class="column span-14 first last " id="comments">
<div class="column span-14 first last">
<h2 id="comment-title">Comments</h2>
</div>
<?php if ($comments) {
foreach ($comments as $comment) { ?>
<div class="column prepend-1 span-12 first last">
<p class="comment"><?= $comment['text'] ?></p>
</div>
<div class="column prepend-10 span-6 first last">
- by <a href="<?= Users::$VIEW_URL ?>?userid=<?=h( $comment['user_id'] )?>"><?=h( $comment['login'] ) ?></a>
</div>
The developer
A vulnerability is the result of the developer's mistake. Vulnerabilities come from:
- A lack of time during the development phase: Developers often have few days to develop an application. Under the pressure, mistakes and omissions are common.
- Poor testing phase: Often, testing phase focuses on the application's functionalities more than on security issues. Don't forget to cover this part.
- Lack of knowledge: Development is sometimes under the responsibility of beginners, which conducts to badly developed applications, especially for applications developed "from scratch". Use development frameworks that already implement security layers.