Web applications attacks/SQL injection
Description
Overall definition
SQL injection is certainly the most dangerous attack on web applications. Hence, it enables to gather critical data, update and delete data from a database. Hackers exploit vulnerabilities in web forms to inject a content that modifies the expected behavior of SQL requests. Suppose you have an authentication form that is programmed as follows:
Basic example 1
<?php
mysql_connect('localhost', 'test', 'test');
mysql_select_db('test');
if(isset($_POST['username']) && isset($_POST['password'])) {
$sql = "SELECT username
FROM user
WHERE username='".$_POST['username']."'
AND password='".$_POST['password']."'";
echo("<div>$sql</div>");
$query = mysql_query($sql);
$result = mysql_fetch_row($query);
if(is_array($result)) {
echo("<p>Access granted as ".$result[0]."</p>");
} else {
echo("<p>Invalid credentials</p>");
}
}
?>
<form method="post" action="test.php">
<div>Username: <input type="text" name="username" /></div>
<div>Password: <input type="password" name="password" /></div>
<div><input type="submit" value="Go" /></div>
</form>
The initial request expects two arguments (username and password) as follows:
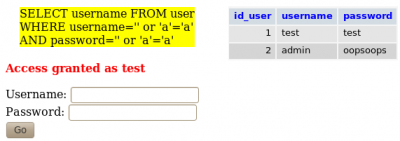
SELECT username FROM user WHERE username='myusername' AND password='mypassword'
This request only returns results if there is an existing record in table USER, corresponding to provided credentials.
But, by injecting 'or 'a'='a in both fields (username and password), request becomes:
SELECT username FROM user WHERE username=''or 'a'='a' AND password=''or 'a'='a'
The request is now always true, and returns the first login found in the USER table. This technique is called SQL injection.
Basic example 2
If a hacker now injects following content:
- username: admin'#
- password: whatever
The request becomes:
SELECT username FROM user WHERE username='admin'#' AND password='whatever'
The sharp symbol (#) indicates that everything that follows the symbol is a comment. The request will then only test the username, and the hacker won't have to provide a valid password to grant the access.
Although, for this attack to succeed, the request needs to be on one line. If the request is on several lines in the source code, it will fail.
Why do SQL injections work?
Because:
- SQL injection vulnerabilities are common and well documented on the Internet
- Many applications consider database content as trusted and fail to properly escape it.
Examples
Basic SQL injections
Basic SQL injections enable to bypass non-protected forms.
- WebGoat, Numeric SQL injection lesson will show you how to make a basic SQL injection to display all cities from an initial limited list of cities.
- WebGoat, XPATH injection is another example of a basic SQL injection.
- WebGoat SQL injection lab is a challenge that shows how to exploit a SQL injection to escalate privileges and shows an alternate way to protect against this: prepared statements.
- OWASP_WebGoat:String_SQL_Injection shows another basic SQL injection that enables to display a list of credit cards.
- HackThisSite.org, Realistic, Level 2 shows how to get valid credentials with a SQL injection.
UNION ALL SELECT injection
There is another SQL injection based on the "UNION ALL SELECT" SQL statement. It enables to concatenate the results of a normal/expected table with the results of another table.
- HackThisSite.org, Realistic, Level 4 illustrates such a SQL injection.
Blind SQL injection
- OWASP_WebGoat:Blind_SQL_Injection shows you an iterative process of SQL injections to get a valid user name. This process is called blind SQL injection.
Persistent SQL injections
- WebGoat Database Backdoors is an example of a persistent SQL injection that creates a trigger on a table.
Escalation
SQL injections may enable one to complete take control over the machine:
- Read this article: from SQL injection to complete server compromise
- See examples from Havij and Absinthe
Protection
- Don't trust data from your database; it could have been compromised.
- Control and purify data that are sent from the browser on server-side.
- Enforce coding standards: Use prepared statements and stored procedures to avoid SQL injections
- Use mysql_real_escape_string() function.
- Use white lists input validation
Tools
- Absinthe is a tool that automatizes the reverse-engineering of databases, based on a variety of SQL injections.
- GoogleHacks: the famous GHDB from Johnny Long
- Pangolin is an automatic SQL injection penetration testing tool developed by NOSEC. Its goal is to detect and take advantage of SQL injection vulnerabilities on web applications. Once it has detected one or more SQL injections on the target host, it is possible to perform an extensive back-end database management.
- Arachni is a fast asynchronous Web Application Security Scanner that detects, among others, SQL injections.
- Darkjumper will try to find every website that is hosted at the same server at your target and will check for every vulnerability of the discovered websites.
- Havij is a tool that automates SQL injections (blind SQL, SQL errors, UNION) to reverse-engineer a database and gather relevant data on a server.
- Puzlbox is a PHP fuzzing tool that scans for Arbitrary Command Execution, Arbitrary File Read/Write/Change/Rename/Delete, Local File Inclusion (LFI), Arbitrary PHP Execution, SQL Injection and Reflected Cross-site Scripting (XSS).