Windows-userassist-keys
Description
Windows systems maintain a set of keys in the registry database (UserAssist keys) to keep track of programs that executed. The number of executions and last execution date and time are available in these keys.
The information within the binary UserAssist values contains only statistical data on the applications launched by the user via Windows Explorer. Programs launched via the commandline (cmd.exe) do not appear in these registry keys.
From a forensics perspective, being able to decode this information can be very useful.
Registry keys
Keys
Location
Userassist registry keys are saved in following locations:
- HKEY_USERS\{SID}\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{GUID}\Count\
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{GUID}\Count\
GUID for Windows XP
- {75048700-EF1F-11D0-9888-006097DEACF9}
- {5E6AB780-7743-11CF-A12B-00AA004AE837}
GUID for Windows 7
- {CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}
- {F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}
Decoding keys
Decode names
ROT 13 encoding
- Names are ROT13 encoded: http://en.wikipedia.org/wiki/ROT13
- Notice that both logging and encoding can be prevented (refer to annex #2).
Windows XP
Key names associated to userassist keys are ROT13 encoded:
It's easy to decode the names:
>>> s = "HRZR_EHACNGU:P:\Qbphzragf naq Frggvatf\haxabja\Ohernh\argjbex-gnfxznantre.rkr"
>>> s.decode("rot13")
u'UEME_RUNPATH:C:\\Documents and Settings\\unknown\\Bureau\x07etwork-taskmanager.exe'
Below is the explanation of common paths (seen here):
- UEME_CTLSESSION: This entry is for the session ID, it doesn't hold data about executed programs
- UEME_UIQCUT: Counts the programs launched via a Quick Launch menu shortcut
- UEME_UISCUT: Counts the programs launched via a Desktop shortcut
- UEME_RUNCPL: This entry keeps data about executed control applets (.cpl)
- UEME_RUNPATH: This entry keeps data about executed programs
- UEME_RUNPIDL: This entry keeps data about executed PIDLs
- UEME_UITOOLBAR: This entry keeps data about clicks on the Windows Explorer Toolbar buttons
Windows 7
As for Windows XP, names are ROT13 encoded:
It's easy to decode them in python:
>>> s = "\\iobkfei\gzc\QPbqr.rkr"
>>> s.decode("rot13")
u'\\vboxsrv\\tmp\\DCode.exe'
>>> s = "{7P5N40RS-N0SO-4OSP-874N-P0S2R0O9SN8R}\Benpyr\IveghnyObk Thrfg Nqqvgvbaf\IObkQeiVafg.rkr"
>>> s.decode("rot13")
u'{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\Oracle\\VirtualBox Guest Additions\\VB
Notice that Windows 7 uses special paths that need to be converted (refer to annex #1).
The path {7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E} is translated to %ProgramFiles% and the full path becomes:
%ProgramFiles%\Oracle\VirtualBox Guest Additions\VB
Decode values
Binary data
Binary values contained in each of these keys provide information close to the one provided by Windows prefetch files:
- number of executions
- focus time
- last execution date and time
The information contained in the keys depend on the versions:
- NT4, 95, 98: 8 bytes
- 2000, ME, XP: 16 bytes
- Vista, 7, 2008, 8: 72 bytes
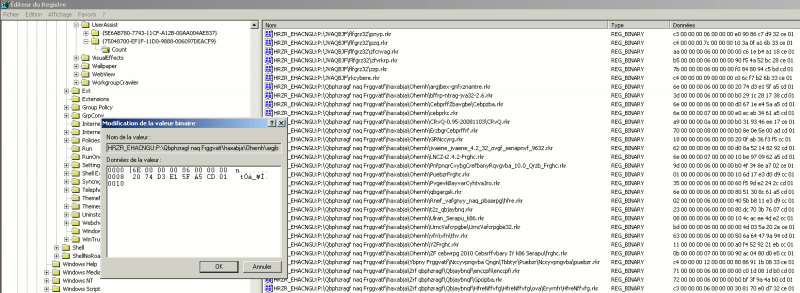
Windows XP
As an example, let's decode the value associated to following key: HRZR_EHACNGU:P:\\Qbphzragf naq Frggvatf\\haxabja\\Ohernh\\bffrp-ntrag-jva32-2.6.rkr (or UEME_RUNPATH:C:\Documents and Settings\unknown\Bureau\ossec-agent-win32-2.6.exe once decoded). Here is the binary value associated to the key:
0000 | 3D 00 00 00 06 00 00 00 0008 | B0 29 1C 28 17 38 CD 01
Following information is available:
- Session ID: unsigned int, 4 bytes
- counter: unsigned int, 4 bytes
- date time stamp: unsigned long long, 8 bytes
Here is how we could decrypt this binary string in python:
>>> from struct import unpack
>>> data = "\x3D\x00\x00\x00\x06\x00\x00\x00"
>>> data+= "\xB0\x29\x1C\x28\x17\x38\xCD\x01"
>>> len(data)
16
>>> unpack('IIQ', data)
(61, 6, 129821636371950000L)
It provides us with:
- Session ID: 61 (3d000000)
- Counter: 1 (06000000). We actually have to substract 5 to the value as the counter starts at 5
To convert the date time stamp, let's use this function (found here):
>>> from datetime import datetime >>> def convert_windate(windate): ... # Converts 8-byte Windows DateTime stamps to Unix one ... date_format = '%Y/%m/%d %H:%M:%S UTC' ... no_nano = windate/10000000 # 10000000 - 100 nanosecond intervals in windows timestamp, remove them to get to seconds since windows epoch ... unix = no_nano - 11644473600 # number of seconds between 1/1/1601 and 1/1/1970 ... return datetime.fromtimestamp(int(unix)).strftime(date_format) ... >>> convert_windate(129821636371950000) '2012/05/22 14:33:57 UTC'
Now we also know when the program was last run:
- Last run: 2012/05/22 14:33:57 UTC (b0291c281738cd01)
Windows 7
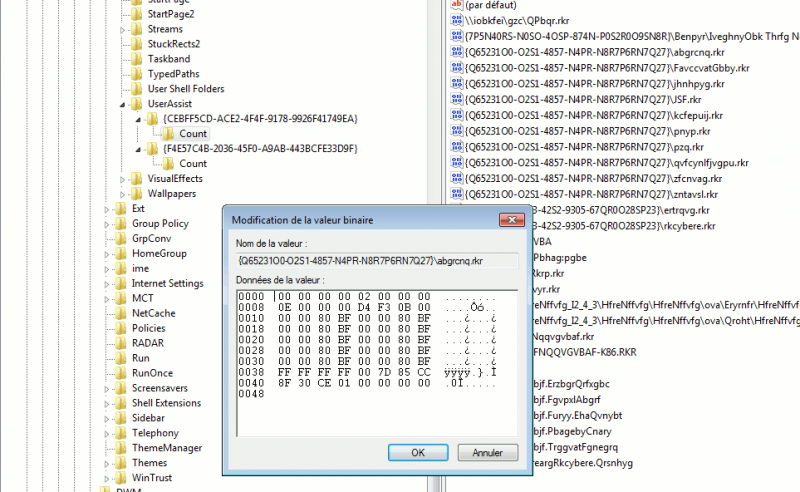
Given following key: {Q65231O0-O2S1-4857-N4PR-N8R7P6RN7Q27}\pnyp.rkr (%windir%\system32\calc.exe once fully decoded). It has following binary value:
0000 | 00 00 00 00 11 00 00 00 0008 | 00 00 00 00 CC 42 0E 00 0010 | 00 00 80 BF 00 00 80 BF 0018 | 00 00 80 BF 00 00 80 BF 0020 | 00 00 80 BF 00 00 80 BF 0028 | 00 00 80 BF 00 00 80 BF 0030 | 00 00 80 BF 00 00 80 BF 0038 | FF FF FF FF C0 D0 66 17 0040 | D5 32 CE 01 00 00 00 00
Following information is available:
- Number of executions
- Focus count?
- Focus time
- Last execution
Let's decode the information in python:
>>> data = "\x00\x00\x00\x00\x11\x00\x00\x00"
>>> data+= "\x00\x00\x00\x00\xCC\x42\x0E\x00"
>>> data+= "\x00\x00\x80\xBF\x00\x00\x80\xBF"
>>> data+= "\x00\x00\x80\xBF\x00\x00\x80\xBF"
>>> data+= "\x00\x00\x80\xBF\x00\x00\x80\xBF"
>>> data+= "\x00\x00\x80\xBF\x00\x00\x80\xBF"
>>> data+= "\x00\x00\x80\xBF\x00\x00\x80\xBF"
>>> data+= "\xFF\xFF\xFF\xFF\xC0\xD0\x66\x17"
>>> data+= "\xD5\x32\xCE\x01\x00\x00\x00\x00"
>>> unpack("I", data[4:8]) # runcount
(17,)
>>> unpack("I", data[12:16]) # focus time
(934604,)
>>> unpack("Q", data[60:68]) # datetime
(130097330042360000L,)
>>> convert_windate(130097330042360000)
'2013/04/06 16:43:24 UTC'
It provides us with:
- Number of executions: 17
- Focus time: 934604
- Last run: 2013/04/06 16:43:24 UTC
Tools
- From Volatility: userassist plugin
- Didier Stevens has written a nice tool to show userassist keys: UserAssist.
- UserAssistView (Nirsoft)
- RegistryDecoder project: https://code.google.com/p/registrydecoder/
Appendicies
Translation of directories
| Key | Translation |
|---|---|
| {de61d971-5ebc-4f02-a3a9-6c82895e5c04} | Add or Remove Programs (Control Panel) |
| {724EF170-A42D-4FEF-9F26-B60E846FBA4F} | %APPDATA%\Microsoft\Windows\Start Menu\Programs\Administrative Tools |
| {a305ce99-f527-492b-8b1a-7e76fa98d6e4} | Installed Updates |
| {9E52AB10-F80D-49DF-ACB8-4330F5687855} | %LOCALAPPDATA%\Microsoft\Windows\Burn\Burn |
| {df7266ac-9274-4867-8d55-3bd661de872d} | Programs and Features |
| {D0384E7D-BAC3-4797-8F14-CBA229B392B5} | %ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs\Administrative Tools |
| {C1BAE2D0-10DF-4334-BEDD-7AA20B227A9D} | %ALLUSERSPROFILE%\OEM Links |
| {0139D44E-6AFE-49F2-8690-3DAFCAE6FFB8} | %ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs |
| {A4115719-D62E-491D-AA7C-E74B8BE3B067} | %ALLUSERSPROFILE%\Microsoft\Windows\Start Menu |
| {82A5EA35-D9CD-47C5-9629-E15D2F714E6E} | %ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs\StartUp |
| {B94237E7-57AC-4347-9151-B08C6C32D1F7} | %ALLUSERSPROFILE%\Microsoft\Windows\Templates |
| {0AC0837C-BBF8-452A-850D-79D08E667CA7} | (My) Computer |
| {4bfefb45-347d-4006-a5be-ac0cb0567192} | Conflicts |
| {6F0CD92B-2E97-45D1-88FF-B0D186B8DEDD} | Network Connections |
| {56784854-C6CB-462b-8169-88E350ACB882} | %USERPROFILE%\Contacts |
| {82A74AEB-AEB4-465C-A014-D097EE346D63} | Control Panel |
| {2B0F765D-C0E9-4171-908E-08A611B84FF6} | %APPDATA%\Microsoft\Windows\Cookies |
| {B4BFCC3A-DB2C-424C-B029-7FE99A87C641} | Desktop |
| {5CE4A5E9-E4EB-479D-B89F-130C02886155} | %ALLUSERSPROFILE%\Microsoft\Windows\DeviceMetadataStore |
| {7B0DB17D-9CD2-4A93-9733-46CC89022E7C} | %APPDATA%\Microsoft\Windows\Libraries\Documents.library-ms |
| {374DE290-123F-4565-9164-39C4925E467B} | %USERPROFILE%\Downloads |
| {1777F761-68AD-4D8A-87BD-30B759FA33DD} | %USERPROFILE%\Favorites |
| {FD228CB7-AE11-4AE3-864C-16F3910AB8FE} | %windir%\Fonts |
| {CAC52C1A-B53D-4edc-92D7-6B2E8AC19434} | Games |
| {054FAE61-4DD8-4787-80B6-090220C4B700} | GameExplorer |
| {D9DC8A3B-B784-432E-A781-5A1130A75963} | %LOCALAPPDATA%\Microsoft\Windows\History |
| {52528A6B-B9E3-4ADD-B60D-588C2DBA842D} | Homegroup |
| {BCB5256F-79F6-4CEE-B725-DC34E402FD46} | %APPDATA%\Microsoft\Internet Explorer\Quick Launch\User Pinned\ImplicitAppShortcuts |
| {352481E8-33BE-4251-BA85-6007CAEDCF9D} | %LOCALAPPDATA%\Microsoft\Windows\Temporary Internet Files |
| {4D9F7874-4E0C-4904-967B-40B0D20C3E4B} | The Internet |
| {1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE} | %APPDATA%\Microsoft\Windows\Libraries |
| {bfb9d5e0-c6a9-404c-b2b2-ae6db6af4968} | %USERPROFILE%\Links |
| {F1B32785-6FBA-4FCF-9D55-7B8E7F157091} | %LOCALAPPDATA% (%USERPROFILE%\AppData\Local) |
| {A520A1A4-1780-4FF6-BD18-167343C5AF16} | %USERPROFILE%\AppData\LocalLow |
| {2A00375E-224C-49DE-B8D1-440DF7EF3DDC} | %windir%\resources\0409 (code page) |
| {4BD8D571-6D19-48D3-BE97-422220080E43} | %USERPROFILE%\Music |
| {2112AB0A-C86A-4FFE-A368-0DE96E47012E} | %APPDATA%\Microsoft\Windows\Libraries\Music.library-ms |
| {C5ABBF53-E17F-4121-8900-86626FC2C973} | %APPDATA%\Microsoft\Windows\Network Shortcuts |
| {D20BEEC4-5CA8-4905-AE3B-BF251EA09B53} | Network |
| {2C36C0AA-5812-4b87-BFD0-4CD0DFB19B39} | %LOCALAPPDATA%\Microsoft\Windows Photo Gallery\Original Images |
| {69D2CF90-FC33-4FB7-9A0C-EBB0F0FCB43C} | %USERPROFILE%\Pictures\Slide Shows |
| {A990AE9F-A03B-4E80-94BC-9912D7504104} | %APPDATA%\Microsoft\Windows\Libraries\Pictures.library-ms |
| {33E28130-4E1E-4676-835A-98395C3BC3BB} | %USERPROFILE%\Pictures |
| {DE92C1C7-837F-4F69-A3BB-86E631204A23} | %USERPROFILE%\Music\Playlists |
| {76FC4E2D-D6AD-4519-A663-37BD56068185} | Printers |
| {9274BD8D-CFD1-41C3-B35E-B13F55A758F4} | %APPDATA%\Microsoft\Windows\Printer Shortcuts |
| {5E6C858F-0E22-4760-9AFE-EA3317B67173} | %USERPROFILE% (%SystemDrive%\Users\%USERNAME%) |
| {62AB5D82-FDC1-4DC3-A9DD-070D1D495D97} | %ALLUSERSPROFILE% (%ProgramData%, %SystemDrive%\ProgramData) |
| {905e63b6-c1bf-494e-b29c-65b732d3d21a} | %ProgramFiles% |
| {6D809377-6AF0-444b-8957-A3773F02200E} | %ProgramFiles% |
| {7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E} | %ProgramFiles% |
| {F7F1ED05-9F6D-47A2-AAAE-29D317C6F066} | %ProgramFiles%\Common Files |
| {6365D5A7-0F0D-45E5-87F6-0DA56B6A4F7D} | %ProgramFiles%\Common Files |
| {DE974D24-D9C6-4D3E-BF91-F4455120B917} | %ProgramFiles%\Common Files |
| {A77F5D77-2E2B-44C3-A6A2-ABA601054A51} | %APPDATA%\Microsoft\Windows\Start Menu\Programs |
| {DFDF76A2-C82A-4D63-906A-5644AC457385} | %PUBLIC% (%SystemDrive%\Users\Public) |
| {C4AA340D-F20F-4863-AFEF-F87EF2E6BA25} | %PUBLIC%\Desktop |
| {ED4824AF-DCE4-45A8-81E2-FC7965083634} | %PUBLIC%\Documents |
| {3D644C9B-1FB8-4f30-9B45-F670235F79C0} | %PUBLIC%\Downloads |
| {DEBF2536-E1A8-4c59-B6A2-414586476AEA} | %ALLUSERSPROFILE%\Microsoft\Windows\GameExplorer |
| {48DAF80B-E6CF-4F4E-B800-0E69D84EE384} | %ALLUSERSPROFILE%\Microsoft\Windows\Libraries |
| {3214FAB5-9757-4298-BB61-92A9DEAA44FF} | %PUBLIC%\Music |
| {B6EBFB86-6907-413C-9AF7-4FC2ABF07CC5} | %PUBLIC%\Pictures |
| {E555AB60-153B-4D17-9F04-A5FE99FC15EC} | %ALLUSERSPROFILE%\Microsoft\Windows\Ringtones |
| {2400183A-6185-49FB-A2D8-4A392A602BA3} | %PUBLIC%\Videos |
| {52a4f021-7b75-48a9-9f6b-4b87a210bc8f} | %APPDATA%\Microsoft\Internet Explorer\Quick Launch |
| {AE50C081-EBD2-438A-8655-8A092E34987A} | %APPDATA%\Microsoft\Windows\Recent |
| {1A6FDBA2-F42D-4358-A798-B74D745926C5} | %PUBLIC%\RecordedTV.library-ms |
| {B7534046-3ECB-4C18-BE4E-64CD4CB7D6AC} | Recycle Bin |
| {8AD10C31-2ADB-4296-A8F7-E4701232C972} | %windir%\Resources |
| {C870044B-F49E-4126-A9C3-B52A1FF411E8} | %LOCALAPPDATA%\Microsoft\Windows\Ringtones |
| {3EB685DB-65F9-4CF6-A03A-E3EF65729F3D} | %APPDATA% (%USERPROFILE%\AppData\Roaming) |
| {B250C668-F57D-4EE1-A63C-290EE7D1AA1F} | %PUBLIC%\Music\Sample Music |
| {C4900540-2379-4C75-844B-64E6FAF8716B} | %PUBLIC%\Pictures\Sample Pictures |
| {15CA69B3-30EE-49C1-ACE1-6B5EC372AFB5} | %PUBLIC%\Music\Sample Playlists |
| {859EAD94-2E85-48AD-A71A-0969CB56A6CD} | %PUBLIC%\Videos\Sample Videos |
| {4C5C32FF-BB9D-43b0-B5B4-2D72E54EAAA4} | %USERPROFILE%\Saved Games |
| {7d1d3a04-debb-4115-95cf-2f29da2920da} | %USERPROFILE%\Searches |
| {ee32e446-31ca-4aba-814f-a5ebd2fd6d5e} | Offline Files |
| {98ec0e18-2098-4d44-8644-66979315a281} | Microsoft Office Outlook |
| {190337d1-b8ca-4121-a639-6d472d16972a} | Search Results |
| {8983036C-27C0-404B-8F08-102D10DCFD74} | %APPDATA%\Microsoft\Windows\SendTo |
| {7B396E54-9EC5-4300-BE0A-2482EBAE1A26} | %ProgramFiles%\Windows Sidebar\Gadgets |
| {A75D362E-50FC-4fb7-AC2C-A8BEAA314493} | %LOCALAPPDATA%\Microsoft\Windows Sidebar\Gadgets |
| {625B53C3-AB48-4EC1-BA1F-A1EF4146FC19} | %APPDATA%\Microsoft\Windows\Start Menu |
| {B97D20BB-F46A-4C97-BA10-5E3608430854} | %APPDATA%\Microsoft\Windows\Start Menu\Programs\StartUp |
| {43668BF8-C14E-49B2-97C9-747784D784B7} | Sync Center |
| {289a9a43-be44-4057-a41b-587a76d7e7f9} | Sync Results |
| {0F214138-B1D3-4a90-BBA9-27CBC0C5389A} | Sync Setup |
| {1AC14E77-02E7-4E5D-B744-2EB1AE5198B7} | %windir%\system32 |
| {D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27} | %windir%\system32 |
| {A63293E8-664E-48DB-A079-DF759E0509F7} | %APPDATA%\Microsoft\Windows\Templates |
| {9E3995AB-1F9C-4F13-B827-48B24B6C7174} | %APPDATA%\Microsoft\Internet Explorer\Quick Launch\User Pinned |
| {0762D272-C50A-4BB0-A382-697DCD729B80} | %SystemDrive%\Users |
| {5CD7AEE2-2219-4A67-B85D-6C9CE15660CB} | %LOCALAPPDATA%\Programs |
| {BCBD3057-CA5C-4622-B42D-BC56DB0AE516} | %LOCALAPPDATA%\Programs\Common |
| {f3ce0f7c-4901-4acc-8648-d5d44b04ef8f} | The user's full name |
| {A302545D-DEFF-464b-ABE8-61C8648D939B} | Libraries |
| {18989B1D-99B5-455B-841C-AB7C74E4DDFC} | %USERPROFILE%\Videos |
| {491E922F-5643-4AF4-A7EB-4E7A138D8174} | %APPDATA%\Microsoft\Windows\Libraries\Videos.library-ms |
| {F38BF404-1D43-42F2-9305-67DE0B28FC23} | %windir% |
Prevent logging and/or ROT13 encoding
It's possible to prevent both the encoding and the logging:
- Disable logging:
C:\>regwrite, REG_DWORD, HKCU, Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\Settings, NoLog, 1
- Disable ROT13 encoding:
C:\>regwrite, REG_DWORD, HKCU, Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\Settings, NoEncrypt, 1