Volatility
Description
The Volatility Framework is a completely open collection of tools, implemented in Python under the GNU General Public License, for the extraction of digital artifacts from volatile memory (RAM) samples. The extraction techniques are performed completely independent of the system being investigated but offer visibility into the runtime state of the system. The framework is intended to introduce people to the techniques and complexities associated with extracting digital artifacts from volatile memory samples and provide a platform for further work into this exciting area of research.
See here the procedure to build custom profiles.
The official documentation is very complete and is available here: http://code.google.com/p/volatility/wiki/VolatilityIntroduction?tm=6
Plugins are grouped into following categories. Additional plugins are described here.
| Windows Core | |||||||
|---|---|---|---|---|---|---|---|
| Image Identification |
Processes and DLLs |
Process Memory |
Kernel Memory and Objects |
Networking | Registry | Crash Dumps, Hibernation and Conversion |
Miscellaneous |
|
|
Installation
$ cd /data/src/ $ wget https://www.volatilesystems.com/volatility/2.1/volatility-2.1.tar.gz $ tar xzvf volatility-2.1.tar.gz $ cd volatility-2.1/ $ python vol.py --help

Usage
Syntax
General usage:
python vol.py plugin options
Help on a given plugin:
python vol.py plugin -h
Example:
$ python vol.py yarascan -h
Volatile Systems Volatility Framework 2.2
Usage: Volatility - A memory forensics analysis platform.
[REMOVED]
-Y YARA_RULES, --yara-rules=YARA_RULES
Yara rules (as a string)
-y YARA_FILE, --yara-file=YARA_FILE
Yara rules (rules file)
-D DUMP_DIR, --dump-dir=DUMP_DIR
Directory in which to dump the files
---------------------------------
Module YaraScan
---------------------------------
Scan process or kernel memory with Yara signatures
Environment variables
You can define some environment variables (VOLATILITY_PROFILE, VOLATILITY_LOCATION) prior to calling volatility in order to save time. Here is an example:
$ export VOLATILITY_PROFILE=Win7SP0x86 $ export VOLATILITY_LOCATION=file:///tmp/myimage.img $ ./vol.py pslist $ ./vol.py files
Options
- -h, --help
- list all available options and their default values.
- Default values may be set in the configuration file (/etc/volatilityrc)
- --conf-file=.volatilityrc
- User based configuration file
- -d, --debug
- Debug volatility
- --plugins=PLUGINS
- Additional plugin directories to use (colon separated)
- --info
- Print information about all registered objects
- --cache-directory=~/.cache/volatility
- Directory where cache files are stored
- --cache
- Use caching
- --tz=TZ
- Sets the timezone for displaying timestamps
- -f FILENAME, --filename=FILENAME
- Filename to use when opening an image
- --profile=WinXPSP2x86
- Name of the profile to load. Supported profiles are:
- VistaSP0x64 (Windows Vista SP0 x64)
- VistaSP0x86 (Windows Vista SP0 x86)
- VistaSP1x64 (Windows Vista SP1 x64)
- VistaSP1x86 (Windows Vista SP1 x86)
- VistaSP2x64 (Windows Vista SP2 x64)
- VistaSP2x86 (Windows Vista SP2 x86)
- Win2003SP0x86 (Windows 2003 SP0 x86)
- Win2003SP1x64 (Windows 2003 SP1 x64)
- Win2003SP1x86 (Windows 2003 SP1 x86)
- Win2003SP2x64 (Windows 2003 SP2 x64)
- Win2003SP2x86 (Windows 2003 SP2 x86)
- Win2008R2SP0x64 (Windows 2008 R2 SP0 x64)
- Win2008R2SP1x64 (Windows 2008 R2 SP1 x64)
- Win2008SP1x64 (Windows 2008 SP1 x64)
- Win2008SP1x86 (Windows 2008 SP1 x86)
- Win2008SP2x64 (Windows 2008 SP2 x64)
- Win2008SP2x86 (Windows 2008 SP2 x86)
- Win7SP0x64 (Windows 7 SP0 x64)
- Win7SP0x86 (Windows 7 SP0 x86)
- Win7SP1x64 (Windows 7 SP1 x64)
- Win7SP1x86 (Windows 7 SP1 x86)
- WinXPSP1x64 (Windows XP SP1 x64)
- WinXPSP2x64 (Windows XP SP2 x64)
- WinXPSP2x86 (Windows XP SP2 x86)
- WinXPSP3x86 (Windows XP SP3 x86)
- -l LOCATION, --location=LOCATION
- A URN location from which to load an address space
- -w, --write
- Enable write support
- --use-old-as
- Use the legacy address spaces
- --dtb=DTB
- DTB Address
- --cache-dtb
- Cache virtual to physical mappings
- --output=text
- Output in this format (format support is module specific)
- --output-file=OUTPUT_FILE
- write output in this file
- -v, --verbose
- Verbose information
- -k KPCR, --kpcr=KPCR
- Specify a specific KPCR address
- -g KDBG, --kdbg=KDBG
- Specify a specific KDBG virtual address
Supported Plugin Commands
For a more detailed document, go here: http://code.google.com/p/volatility/wiki/CommandReference
apihooks
- Description
- Detect API hooks in process and kernel memory
- Requires
- Install distorm3 code.google.com/p/distorm/
pip install distorm3
- Options
- -o OFFSET, --offset=OFFSET
- EPROCESS offset (in hex) in the physical address space
- -p PID, --pid=PID
- Operate on these Process IDs (comma-separated)
- -u, --unsafe
- Bypasses certain sanity checks when creating image
- -N, --no-whitelist
- No whitelist (show all hooks, can be verbose)
- -R, --skip-kernel
- Skip kernel mode checks
- -P, --skip-process
- Skip process checks
- -Q, --quick
- Work faster by only analyzing critical processes and dlls
- Output example
$ python vol.py -f /data/tmp/memory.056f443f.img --profile=Win2003SP2x86 apihooks -p 1080 Volatile Systems Volatility Framework 2.2 ************************************************************************ Hook mode: Usermode Hook type: Inline/Trampoline Process: 1080 (svchost.exe) Victim module: ntdll.dll (0x7c800000 - 0x7c8c3000) Function: ntdll.dll!<unknown> at 0x7c826c4d Hook address: 0x4fb0000 Hooking module: <unknown> Disassembly(0): 0x7c826c4d e9ae937888 JMP 0x4fb0000 0x7c826c52 ba0003fe7f MOV EDX, 0x7ffe0300 0x7c826c57 ff12 CALL DWORD [EDX] 0x7c826c59 c22c00 RET 0x2c 0x7c826c5c 90 NOP 0x7c826c5d b828000000 MOV EAX, 0x28 0x7c826c62 ba DB 0xba 0x7c826c63 0003 ADD [EBX], AL Disassembly(1): 0x4fb0000 6825b8e9c4 PUSH DWORD 0xc4e9b825 0x4fb0005 e8d37b8777 CALL 0x7c827bdd 0x4fb000a 58 POP EAX 0x4fb000b c22c00 RET 0x2c 0x4fb000e c3 RET 0x4fb000f 0f DB 0xf 0x4fb0010 00b827000000 ADD [EAX+0x27], BH 0x4fb0016 e9 DB 0xe9 0x4fb0017 37 AAA
atoms
- Description
- Print session and window station atom tables
- Output example
$ python vol.py -f ~/tmp/infected.img atoms Volatile Systems Volatility Framework 2.2 Offset(P) Session WindowStation Atom RefCount HIndex Pinned Name ---------- ---------- ------------------ ---------- ---------- ---------- ---------- ---- 0xcc06c18 0 Service-0x0-3e5$ 0xc00c 1 12 1 Protocols 0xcc06c18 0 Service-0x0-3e5$ 0xc00d 1 13 1 Topics 0xcc06c18 0 Service-0x0-3e5$ 0xc00e 1 14 1 Formats 0xcc06c18 0 Service-0x0-3e5$ 0xc007 1 7 1 StdShowItem 0xcc06c18 0 Service-0x0-3e5$ 0xc011 1 17 1 True 0xcc06c18 0 Service-0x0-3e5$ 0xc010 1 16 1 EditEnvItems 0xcc06c18 0 Service-0x0-3e5$ 0xc012 1 18 1 False 0xcc06c18 0 Service-0x0-3e5$ 0xc015 1 21 1 Close 0xcc06c18 0 Service-0x0-3e5$ 0xc004 1 4 1 StdEditDocument 0xcc06c18 0 Service-0x0-3e5$ 0xc008 1 8 1 StdDoVerbItem 0xcc06c18 0 Service-0x0-3e5$ 0xc003 1 3 1 StdOpenDocument 0xcc06c18 0 Service-0x0-3e5$ 0xc005 1 5 1 StdNewfromTemplate 0xcc06c18 0 Service-0x0-3e5$ 0xc014 1 20 1 Save [REMOVED]
atomscan
- Description
- Pool scanner for _RTL_ATOM_TABLE
- Options
- -S offset, --sort-by=offset
- Sort by [offset | atom | refcount]
- Output example
$ python vol.py -f ~/tmp/infected.img atomscan Volatile Systems Volatility Framework 2.2 TableOfs(P) AtomOfs(V) Atom Refs Pinned Name ----------- ---------- ---------- ------ ------ ---- 0x31c4da8 0xe1000d48 0xc007 1 1 FileNameW 0x31c4da8 0xe1009148 0xc004 1 1 Native 0x31c4da8 0xe1013340 0xc146 2 0 wuauclt_icon 0x31c4da8 0xe101b2e0 0xc106 1 0 AFX_WM_ON_BEFORE_SHOW_RIBBON_ITEM_MENU 0x31c4da8 0xe1022810 0xc037 1 1 SysShadow 0x31c4da8 0xe108c620 0xc0a6 4 0 C:\WINDOWS\system32\NETSHELL.dll 0x31c4da8 0xe10e7488 0xc159 2 0 MdmDevChg 0x31c4da8 0xe1106478 0xc148 1 0 C:\WINDOWS\system32\wucltui.dll 0x31c4da8 0xe1116e10 0xc157 1 0 MS Forms Text 0x31c4da8 0xe1116e40 0xc098 2 0 MS_WebcheckMonitor 0x31c4da8 0xe1121270 0xc13e 2 0 Progman 0x31c4da8 0xe112fe20 0xc156 2 0 Rich Text Format Without Objects 0x31c4da8 0xe134fbd8 0xc01e 1 1 ComboLBox 0x31c4da8 0xe13575e8 0xc020 1 1 DDEMLMom [REMOVED]
bioskbd
- Description
- Reads the keyboard buffer from Real Mode memory
- Output example
$ python vol.py -f ~/tmp/infected.img bioskbd Volatile Systems Volatility Framework 2.1 Ascii Scancode
callbacks
- Description
- Print system-wide notification routines
- Output example
$ python vol.py -f ~/tmp/infected.img callbacks Volatile Systems Volatility Framework 2.1 Type Callback Module Details ------------------------------------ ---------- -------------------- ------- IoRegisterFsRegistrationChange 0xf84d5876 sr.sys - IoRegisterFsRegistrationChange 0xf84d5876 sr.sys - IoRegisterFsRegistrationChange 0xf84d5876 sr.sys - IoRegisterFsRegistrationChange 0xf84d5876 sr.sys - KeBugCheckCallbackListHead 0xf83fd5ef NDIS.sys Ndis miniport KeBugCheckCallbackListHead 0xf83fd5ef NDIS.sys Ndis miniport KeBugCheckCallbackListHead 0x806d87cc hal.dll ACPI 1.0 - APIC platform UP IoRegisterShutdownNotification 0xf8bba5be Fs_Rec.SYS \FileSystem\Fs_Rec IoRegisterShutdownNotification 0xb250c15e vmhgfs.sys \FileSystem\vmhgfs IoRegisterShutdownNotification 0xf831fc6a VIDEOPRT.SYS \Driver\VgaSave IoRegisterShutdownNotification 0xf8bba5be Fs_Rec.SYS \FileSystem\Fs_Rec IoRegisterShutdownNotification 0xf831fc6a VIDEOPRT.SYS \Driver\vmx_svga IoRegisterShutdownNotification 0xf853b2be ftdisk.sys \Driver\Ftdisk IoRegisterShutdownNotification 0xf8bba5be Fs_Rec.SYS \FileSystem\Fs_Rec IoRegisterShutdownNotification 0xf8bba5be Fs_Rec.SYS \FileSystem\Fs_Rec IoRegisterShutdownNotification 0xf879dc74 Cdfs.SYS \FileSystem\Cdfs IoRegisterShutdownNotification 0xf831fc6a VIDEOPRT.SYS \Driver\mnmdd [REMOVED]
clipboard
- Description
- Extract the contents of the windows clipboard
- Output example
$ python vol.py -f ~/memdump/stuxnet.vmem clipboard
Volatile Systems Volatility Framework 2.2
Session WindowStation Format Handle Object Data
---------- ------------- ------------------ ---------- ---------- --------------------------------------------------
0 WinSta0 CF_UNICODETEXT 0x136012b 0xe29b0c68 74ddc49a7c121a61b8d06c03f92d0c13.exe
0 WinSta0 CF_LOCALE 0x270101 0xe1bdab58
0 WinSta0 CF_TEXT 0x1 ----------
0 WinSta0 CF_OEMTEXT 0x1 ----------
cmdscan
- Description
- Extract command history by scanning for _COMMAND_HISTORY
- Options
- -M 50, --max_history=50
- CommandCountMax (default = 50)
- Output example
$ python vol.py -f ~/tmp/infected.img cmdscan Volatile Systems Volatility Framework 2.1 ************************************************** CommandProcess: csrss.exe Pid: 772 CommandHistory: 0x10c87f0 Application: mdd_1.3.exe Flags: Allocated CommandCount: 0 LastAdded: -1 LastDisplayed: -1 FirstCommand: 0 CommandCountMax: 50 ProcessHandle: 0x3fc ************************************************** CommandProcess: csrss.exe Pid: 772 CommandHistory: 0x10c8e50 Application: TPAutoConnect.exe Flags: Allocated CommandCount: 0 LastAdded: -1 LastDisplayed: -1 FirstCommand: 0 CommandCountMax: 50 ProcessHandle: 0x714 ************************************************** CommandProcess: csrss.exe Pid: 772 CommandHistory: 0x10fc700 Application: cmd.exe Flags: Allocated, Reset CommandCount: 13 LastAdded: 12 LastDisplayed: 12 FirstCommand: 0 CommandCountMax: 50 ProcessHandle: 0x434 Cmd #0 @ 0x4f1f90: dir Cmd #1 @ 0x4f2ef8: cd .idlerc Cmd #2 @ 0x4f2f30: dir Cmd #3 @ 0x4f1f78: more Cmd #4 @ 0x1108b98: more breakpoints.lst Cmd #5 @ 0x4f2f40: more recent-files.lst Cmd #6 @ 0x1108cc8: cd .. Cmd #7 @ 0x10d4b40: dir Cmd #8 @ 0x10d4888: cd "Mes documents" Cmd #9 @ 0x10c8c40: dir Cmd #10 @ 0x4f1eb8: cd Downloads Cmd #11 @ 0x4f2360: dir Cmd #12 @ 0x10d4948: mdd_1.3.exe -q -o image.img
connections
- Description
- Print list of open connections [Windows XP and 2003 Only] at the time the memory dump was taken.
- This module follows the handle table in tcpip.sys and prints current connections.
- Note that if you are using a hibernated image this might not work because Windows closes all connections before hibernating. You might find it more effective to do connscan instead.
- Options
- -P, --physical-offset
- Physical Offset
- Output example
$ python vol.py -f ~/tmp/infected.img connections Volatile Systems Volatility Framework 2.1 Offset(V) Local Address Remote Address Pid ---------- ------------------------- ------------------------- ------ 0x81c6b008 192.168.1.27:1226 91.195.240.107:80 532 0x81c21008 192.168.1.27:1254 62.212.130.115:80 600 0x81c84008 192.168.1.27:1235 204.13.162.116:80 532 0x822ffc08 192.168.1.27:1224 195.216.243.2:80 532 0x81cdabc8 192.168.1.27:1255 62.212.130.115:80 600 0x81c20ba0 192.168.1.27:1298 67.215.65.132:31960 2944 0x81c71700 192.168.1.27:1237 46.45.171.124:80 532 0x81c1c910 192.168.1.27:1256 62.212.130.115:80 600 0x81e73008 192.168.1.27:1257 62.212.130.115:80 600 0x81cd0a50 192.168.1.27:1261 213.175.193.143:80 600 0x81cd9008 192.168.1.27:1236 87.248.203.254:80 532
connscan
- Description
- Scan Physical memory for _TCPT_OBJECT objects (tcp connections)
- Output example
$ python vol.py -f ~/tmp/infected.img connscan Volatile Systems Volatility Framework 2.1 Offset(P) Local Address Remote Address Pid ---------- ------------------------- ------------------------- --- 0x01e14338 192.168.1.27:1170 74.125.230.198:80 2760 0x01e17c60 192.168.1.27:1178 173.194.70.157:80 2760 0x01e18348 192.168.1.27:1150 95.101.227.172:80 2760 0x01e18738 192.168.1.27:1141 95.101.239.144:443 2760 0x01e18a48 192.168.1.27:1127 216.34.181.69:80 2760 0x01e1ba48 192.168.1.27:1192 173.194.70.157:443 2760 0x01e1c910 192.168.1.27:1256 62.212.130.115:80 600 0x01e20ba0 192.168.1.27:1298 67.215.65.132:31960 2944 0x01e21008 192.168.1.27:1254 62.212.130.115:80 600 0x01e28930 40.120.205.129:0 78.68.97.109:0 2944 0x01e6aa98 192.168.1.27:1146 173.194.44.41:80 2760 0x01e6b008 192.168.1.27:1226 91.195.240.107:80 532 0x01e6c708 192.168.1.27:1125 95.101.227.172:80 2760 0x01e6d280 72.163.24.130:61569 0.0.0.0:49296 2177290912 0x01e71700 192.168.1.27:1237 46.45.171.124:80 532 0x01e71a10 192.168.1.27:1177 95.101.239.144:80 2760 0x01e81330 192.168.1.27:1098 74.125.230.231:443 314769412 [REMOVED]
consoles
- Description
- Extract command history by scanning for _CONSOLE_INFORMATION
- Options
- -M 50, --max_history=50
- CommandCountMax (default = 50)
- -B 4, --history_buffers=4
- HistoryBufferMax (default = 4)
- Output example
$ python vol.py consoles -f ~/tmp/infected.img
Volatile Systems Volatility Framework 2.1
**************************************************
ConsoleProcess: csrss.exe Pid: 772
Console: 0x10c8958 CommandHistorySize: 50
HistoryBufferCount: 1 HistoryBufferMax: 4
OriginalTitle: C:\Program Files\VMware\VMware Tools\TPAutoConnSvc.exe
Title: C:\Program Files\VMware\VMware Tools\TPAutoConnSvc.exe
AttachedProcess: TPAutoConnect.e Pid: 2420 Handle: 0x714
----
CommandHistory: 0x10c8e50 Application: TPAutoConnect.exe Flags: Allocated
CommandCount: 0 LastAdded: -1 LastDisplayed: -1
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x714
----
Screen 0x10c8c50 X:80 Y:25
Dump:
ThinPrint AutoConnect component, Copyright (c) 1999-2012 Cortado AG, 8.8.734.1
**************************************************
ConsoleProcess: csrss.exe Pid: 772
Console: 0x10d4008 CommandHistorySize: 50
HistoryBufferCount: 1 HistoryBufferMax: 4
OriginalTitle: ?O?O?m??O?O\system32\CMD.exe
Title:
**************************************************
ConsoleProcess: csrss.exe Pid: 772
Console: 0x10f04c0 CommandHistorySize: 50
HistoryBufferCount: 3 HistoryBufferMax: 4
OriginalTitle: %SystemRoot%\system32\cmd.exe
Title: C:\WINDOWS\system32\cmd.exe - mdd_1.3.exe -q -o image.img
AttachedProcess: mdd_1.3.exe Pid: 2908 Handle: 0x3fc
AttachedProcess: cmd.exe Pid: 2164 Handle: 0x434
----
CommandHistory: 0x10c87f0 Application: mdd_1.3.exe Flags: Allocated
CommandCount: 0 LastAdded: -1 LastDisplayed: -1
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x3fc
----
CommandHistory: 0x10c86f8 Application: more.com Flags:
CommandCount: 0 LastAdded: -1 LastDisplayed: -1
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x0
----
CommandHistory: 0x10fc700 Application: cmd.exe Flags: Allocated, Reset
CommandCount: 13 LastAdded: 12 LastDisplayed: 12
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x434
Cmd #0 at 0x4f1f90: dir
Cmd #1 at 0x4f2ef8: cd .idlerc
Cmd #2 at 0x4f2f30: dir
Cmd #3 at 0x4f1f78: more
Cmd #4 at 0x1108b98: more breakpoints.lst
Cmd #5 at 0x4f2f40: more recent-files.lst
Cmd #6 at 0x1108cc8: cd ..
Cmd #7 at 0x10d4b40: dir
Cmd #8 at 0x10d4888: cd "Mes documents"
Cmd #9 at 0x10c8c40: dir
Cmd #10 at 0x4f1eb8: cd Downloads
Cmd #11 at 0x4f2360: dir
Cmd #12 at 0x10d4948: mdd_1.3.exe -q -o image.img
----
Screen 0x10d4988 X:80 Y:300
Dump:
Microsoft Windows XP [version 5.1.2600]
(C) Copyright 1985-2001 Microsoft Corp.
C:\Documents and Settings\pilou>dir
Le volume dans le lecteur C n'a pas de nom.
Le num?ro de s?rie du volume est E0F1-D8A1
R?pertoire de C:\Documents and Settings\pilou
15/09/2012 21:57 <REP> .
15/09/2012 21:57 <REP> ..
15/09/2012 21:57 <REP> .idlerc
24/12/2012 13:03 <REP> Bureau
18/03/2012 08:44 <REP> Favoris
08/12/2011 21:44 <REP> Menu D?marrer
03/06/2012 09:35 <REP> Mes documents
0 fichier(s) 0 octets
7 R?p(s) 3?217?035?264 octets libres
[REMOVED]
crashinfo
- Description
- Dump crash-dump information
- Output example
$ python vol.py -f win7_x64.dmp --profile=Win7SP0x64 crashinfo Volatile Systems Volatility Framework 2.1_alpha _DMP_HEADER64: Majorversion: 0x0000000f (15) Minorversion: 0x00001db0 (7600) KdSecondaryVersion 0x00000000 DirectoryTableBase 0x32a44000 PfnDataBase 0xfffff80002aa8220 PsLoadedModuleList 0xfffff80002a3de50 PsActiveProcessHead 0xfffff80002a1fb30 MachineImageType 0x00008664 NumberProcessors 0x00000002 BugCheckCode 0x00000000 KdDebuggerDataBlock 0xfffff800029e9070 ProductType 0x00000001 SuiteMask 0x00000110 WriterStatus 0x00000000 Comment PAGEPAGEPAGEPAGEPAGEPAGE[snip] Physical Memory Description: Number of runs: 3 FileOffset Start Address Length 00002000 00001000 0009e000 000a0000 00100000 3fde0000 3fe80000 3ff00000 00100000 3ff7f000 3ffff000
deskscan
- Description
- Poolscaner for tagDESKTOP (desktops)
- Output example
$ python vol.py -f ~/memdump/infected.img deskscan Volatile Systems Volatility Framework 2.2 ************************************************** Desktop: 0x23c6288, Name: Service-0x0-3e5$\Default, Next: 0x0 SessionId: 0, DesktopInfo: 0xbc230650, fsHooks: 0 spwnd: 0xbc2306e8, Windows: 17 Heap: 0xbc230000, Size: 0x80000, Base: 0xbc230000, Limit: 0xbc2b0000 1556 (svchost.exe 1504 parent 840) 1444 (svchost.exe 1428 parent 840) 1432 (svchost.exe 1428 parent 840) 1336 (svchost.exe 1332 parent 840) 1508 (svchost.exe 1504 parent 840) ************************************************** Desktop: 0x23fb330, Name: SAWinSta\SADesktop, Next: 0x0 SessionId: 0, DesktopInfo: 0xbc640650, fsHooks: 0 spwnd: 0xbc6406e8, Windows: 20 Heap: 0xbc640000, Size: 0x80000, Base: 0xbc640000, Limit: 0xbc6c0000 ************************************************** Desktop: 0x20b48b0, Name: WinSta0\Default, Next: 0x81dc6168 SessionId: 0, DesktopInfo: 0xbbe30650, fsHooks: 0 spwnd: 0xbbe306e8, Windows: 145 Heap: 0xbbe30000, Size: 0x300000, Base: 0xbbe30000, Limit: 0xbc130000 492 (mdd_1.3.exe 2908 parent 2164) 2336 (explorer.exe 600 parent 796) 2612 (explorer.exe 600 parent 796) 2680 (vmtoolsd.exe 532 parent 272) 2156 (cmd.exe 2164 parent 600) [REMOVED]
devicetree
- Description
- Show device tree
- Output example
$ python vol.py -f ~/tmp/infected.img devicetree Volatile Systems Volatility Framework 2.1 DRV 0x01f13720 \Driver\IpFilterDriver ---| DEV 0x82295030 IPFILTERDRIVER FILE_DEVICE_NETWORK DRV 0x01fbcb10 \Driver\swenum ---| DEV 0x81f74138 KSENUM#0000000b FILE_DEVICE_UNKNOWN ------| ATT 0x81cb8f10 KSENUM#0000000b - \Driver\kmixer FILE_DEVICE_KS ---| DEV 0x821de258 KSENUM#00000002 FILE_DEVICE_UNKNOWN ------| ATT 0x821d98d0 KSENUM#00000002 - \Driver\sysaudio FILE_DEVICE_KS ---| DEV 0x821dd590 KSENUM#00000001 FILE_DEVICE_UNKNOWN ------| ATT 0x8232d7e0 KSENUM#00000001 - \Driver\wdmaud FILE_DEVICE_KS ---| DEV 0x81dbc6c0 FILE_DEVICE_BUS_EXTENDER DRV 0x01fbfda0 \Driver\mssmbios ---| DEV 0x82197020 FILE_DEVICE_UNKNOWN DRV 0x01fc33b8 \FileSystem\vmhgfs ---| DEV 0x81e6d348 hgfsInternal UNKNOWN ---| DEV 0x81e65600 hgfs FILE_DEVICE_NETWORK_FILE_SYSTEM DRV 0x01fc8f38 \FileSystem\MRxSmb ---| DEV 0x821bed80 LanmanDatagramReceiver FILE_DEVICE_NETWORK_BROWSER ---| DEV 0x81e55c00 LanmanRedirector FILE_DEVICE_NETWORK_FILE_SYSTEM DRV 0x01fda648 \Driver\Beep [REMOVED]
dlldump
- Description
- Dump DLLs from a process address space
- Options
- -p PID, --pid=PID
- Operate on these Process IDs (comma-separated)
- -D DUMP_DIR, --dump-dir=DUMP_DIR
- Directory in which to dump executable files
- -u, --unsafe
- Bypasses certain sanity checks when creating image
- -r REGEX, --regex=REGEX
- Dump dlls matching REGEX
- -i, --ignore-case
- Ignore case in pattern match
- -o OFFSET, --offset=OFFSET
- Dump DLLs for Process with physical address OFFSET
- -b BASE, --base=BASE
- Dump DLLS at the specified BASE offset in the process address space
- Output example
$ python vol.py -f ~/tmp/infected.img dlldump -p 532 --dump-dir=output/ Volatile Systems Volatility Framework 2.1 Process(V) Name Module Base Module Name Result ---------- -------------------- ----------- -------------------- ------ 0x81f015d0 vmtoolsd.exe 0x000400000 vmtoolsd.exe OK: module.532.21015d0.400000.dll 0x81f015d0 vmtoolsd.exe 0x07c910000 ntdll.dll OK: module.532.21015d0.7c910000.dll 0x81f015d0 vmtoolsd.exe 0x040d30000 ieframe.dll Error: DllBase is paged 0x81f015d0 vmtoolsd.exe 0x000f70000 dndcp.dll Error: DllBase is paged 0x81f015d0 vmtoolsd.exe 0x010000000 intl.dll Error: DllBase is paged 0x81f015d0 vmtoolsd.exe 0x0719d0000 wshtcpip.dll OK: module.532.21015d0.719d0000.dll 0x81f015d0 vmtoolsd.exe 0x07e210000 shdocvw.dll Error: DllBase is paged 0x81f015d0 vmtoolsd.exe 0x076f80000 CLBCATQ.DLL Error: DllBase is paged 0x81f015d0 vmtoolsd.exe 0x076e30000 rtutils.dll OK: module.532.21015d0.76e30000.dll [REMOVED}
dlllist
- Description
- Print list of loaded dlls for each process
- Options
- -o OFFSET, --offset=OFFSET
- EPROCESS offset (in hex) in the physical address space
- -p PID, --pid=PID
- Operate on these Process IDs (comma-separated)
- Output example
$ python vol.py -f ~/tmp/infected.img dlllist -p 532 Volatile Systems Volatility Framework 2.1 ************************************************************************ vmtoolsd.exe pid: 532 Command line : "C:\Program Files\VMware\VMware Tools\vmtoolsd.exe" -n vmusr Service Pack 3 Base Size Path ---------- ---------- ---- 0x00400000 0x11000 C:\Program Files\VMware\VMware Tools\vmtoolsd.exe 0x7c910000 0xb9000 C:\WINDOWS\system32\ntdll.dll 0x7c800000 0x106000 C:\WINDOWS\system32\kernel32.dll 0x77da0000 0xac000 C:\WINDOWS\system32\ADVAPI32.dll 0x77e50000 0x93000 C:\WINDOWS\system32\RPCRT4.dll 0x77fc0000 0x11000 C:\WINDOWS\system32\Secur32.dll 0x774a0000 0x13e000 C:\WINDOWS\system32\ole32.dll 0x77ef0000 0x49000 C:\WINDOWS\system32\GDI32.dll 0x7e390000 0x91000 C:\WINDOWS\system32\USER32.dll 0x77be0000 0x58000 C:\WINDOWS\system32\msvcrt.dll 0x77bd0000 0x8000 C:\WINDOWS\system32\VERSION.dll 0x78520000 0xa3000 C:\WINDOWS\WinSxS\x86_Microsoft.VC90.CRT_1fc8b3b9a1e18e3b_9.0.30729.4148_x-ww_d495ac4e\MSVCR90.dll [REMOVED]
driverirp
- Description
- Driver IRP hook detection
- Options
- -r REGEX, --regex=REGEX
- Analyze drivers matching REGEX
- Output example
$ python vol.py -f ~/tmp/infected.img driverirp Volatile Systems Volatility Framework 2.1 -------------------------------------------------- DriverName: IpFilterDriver DriverStart: 0xb1a2b000 DriverSize: 0x8080 DriverStartIo: 0x0 0 IRP_MJ_CREATE 0xb1a2c2b4 ipfltdrv.sys 1 IRP_MJ_CREATE_NAMED_PIPE 0xb1a2c2b4 ipfltdrv.sys 2 IRP_MJ_CLOSE 0xb1a2c2b4 ipfltdrv.sys 3 IRP_MJ_READ 0xb1a2c2b4 ipfltdrv.sys 4 IRP_MJ_WRITE 0xb1a2c2b4 ipfltdrv.sys 5 IRP_MJ_QUERY_INFORMATION 0xb1a2c2b4 ipfltdrv.sys 6 IRP_MJ_SET_INFORMATION 0xb1a2c2b4 ipfltdrv.sys 7 IRP_MJ_QUERY_EA 0xb1a2c2b4 ipfltdrv.sys 8 IRP_MJ_SET_EA 0xb1a2c2b4 ipfltdrv.sys 9 IRP_MJ_FLUSH_BUFFERS 0xb1a2c2b4 ipfltdrv.sys 10 IRP_MJ_QUERY_VOLUME_INFORMATION 0xb1a2c2b4 ipfltdrv.sys 11 IRP_MJ_SET_VOLUME_INFORMATION 0xb1a2c2b4 ipfltdrv.sys 12 IRP_MJ_DIRECTORY_CONTROL 0xb1a2c2b4 ipfltdrv.sys [REMOVED]
driverscan
- Description
- Scan for driver objects _DRIVER_OBJECT
- Output example
$ python vol.py -f ~/tmp/infected.img driverscan Volatile Systems Volatility Framework 2.1 Offset(P) #Ptr #Hnd Start Size Service Key Name Driver Name ---------- ---- ---- ---------- ---------- -------------------- ------------ ----------- 0x01f13720 3 0 0xb1a2b000 0x8080 IpFilterDriver IpFil...iver \Driver\IpFilterDriver 0x01fbcb10 9 0 0xf8bb4000 0x1100 swenum swenum \Driver\swenum 0x01fbfda0 3 0 0xf83a6000 0x3c80 mssmbios mssmbios \Driver\mssmbios 0x01fc33b8 4 0 0xb2507000 0x22800 vmhgfs vmhgfs \FileSystem\vmhgfs 0x01fc8f38 4 0 0xb2444000 0x6f680 MRxSmb MRxSmb \FileSystem\MRxSmb 0x01fda648 3 0 0xf8bbc000 0x1080 Beep Beep \Driver\Beep 0x01fdaa70 3 0 0xf8a02000 0x5200 VgaSave VgaSave \Driver\VgaSave 0x01fdb2c0 3 0 0xf8a0a000 0x4a80 Msfs Msfs \FileSystem\Msfs 0x01fdd6e8 7 0 0xb2574000 0x58480 Tcpip Tcpip \Driver\Tcpip 0x01fddb10 6 0 0xb254c000 0x27c00 NetBT NetBT \Driver\NetBT 0x01fddf38 3 0 0xf8b5a000 0x2f00 WS2IFSL WS2IFSL \Driver\WS2IFSL
envars
- Description
- Display process environment variables
- Options
- -o OFFSET, --offset=OFFSET
- EPROCESS offset (in hex) in the physical address space
- -p PID, --pid=PID
- Operate on these Process IDs (comma-separated)
- Output example
$ python vol.py -f ~/tmp/infected.img envars -p 532
Volatile Systems Volatility Framework 2.1
Pid Process Block Variable Value
-------- -------------------- ---------- ------------------------------ -----
532 vmtoolsd.exe 0x00010000 ALLUSERSPROFILE C:\Documents and Settings\All Users
532 vmtoolsd.exe 0x00010000 APPDATA C:\Documents and Settings\pilou\Application Data
532 vmtoolsd.exe 0x00010000 CLIENTNAME Console
532 vmtoolsd.exe 0x00010000 CommonProgramFiles C:\Program Files\Fichiers communs
532 vmtoolsd.exe 0x00010000 COMPUTERNAME OZ-C06A6A6F2D3C
532 vmtoolsd.exe 0x00010000 ComSpec C:\WINDOWS\system32\cmd.exe
532 vmtoolsd.exe 0x00010000 FP_NO_HOST_CHECK NO
532 vmtoolsd.exe 0x00010000 HOMEDRIVE C:
532 vmtoolsd.exe 0x00010000 HOMEPATH \Documents and Settings\pilou
532 vmtoolsd.exe 0x00010000 LOGONSERVER \\OZ-C06A6A6F2D3C
532 vmtoolsd.exe 0x00010000 NUMBER_OF_PROCESSORS 1
532 vmtoolsd.exe 0x00010000 OS Windows_NT
532 vmtoolsd.exe 0x00010000 Path C:\WINDOWS\system32;C:\WINDOWS;C:\WINDOWS\System32\Wbem;c:\pstools;c:\python27;C:\Program Files\Nmap
[REMOVED]
eventhooks
- Description
- Print details on windows event hooks
- Output example
$ python vol.py -f win7x64.dd --profile=Win7SP1x64 eventhooks Volatile Systems Volatility Framework 2.1_alpha Handle: 0x300cb, Object: 0xfffff900c01eda10, Session: 1 Type: TYPE_WINEVENTHOOK, Flags: 0, Thread: 1516, Process: 880 eventMin: 0x4 EVENT_SYSTEM_MENUSTART eventMax: 0x7 EVENT_SYSTEM_MENUPOPUPEND Flags: none, offPfn: 0xff567cc4, idProcess: 0, idThread: 0 ihmod: -1
evtlogs
- Description
- Extract Windows Event Logs (XP/2003 only)
- Options
- -S, --save-evt
- Save the raw .evt files also
- -D DUMP_DIR, --dump-dir=DUMP_DIR
- Directory in which to dump executable files
- Output example
$ python vol.py -f ~/memdump/infected.img evtlogs --dump-dir=output/ Volatile Systems Volatility Framework 2.2 Parsed data sent to internet.txt Parsed data sent to sysevent.txt Parsed data sent to secevent.txt Parsed data sent to thinprint.txt Parsed data sent to appevent.txt $ cat output/appevent.txt 2011-12-08 19:49:19|appevent.evt|OZ-C06A6A6F2D3C|N/A|LoadPerf|1000|Info|RSVP;QoS RSVP 2011-12-08 19:49:42|appevent.evt|OZ-C06A6A6F2D3C|N/A|LoadPerf|1000|Info|PSched;PSched 2011-12-08 19:49:43|appevent.evt|OZ-C06A6A6F2D3C|N/A|LoadPerf|1000|Info|RemoteAccess;Routage et accs distant 2011-12-08 19:50:01|appevent.evt|OZ-C06A6A6F2D3C|N/A|LoadPerf|1000|Info|TermService;Services Terminal Server 2011-12-08 19:50:02|appevent.evt|OZ-C06A6A6F2D3C|N/A|LoadPerf|1000|Info|MSDTC;MSDTC 2011-12-08 19:50:02|appevent.evt|OZ-C06A6A6F2D3C|N/A|MSDTC|4104|Info|N/A 2011-12-08 19:50:02|appevent.evt|OZ-C06A6A6F2D3C|N/A|MSDTC|2444|Info|0;0;0;0;0;0 2011-12-08 19:50:07|appevent.evt|OZ-C06A6A6F2D3C|N/A|LoadPerf|1000|Info|WmiApRpl;WmiApRpl 2011-12-08 19:50:07|appevent.evt|OZ-C06A6A6F2D3C|N/A|LoadPerf|1001|Info|WmiApRpl;WmiApRpl 2011-12-08 19:50:07|appevent.evt|OZ-C06A6A6F2D3C|N/A|LoadPerf|1000|Info|WmiApRpl;WmiApRpl 2011-12-08 19:50:11|appevent.evt|OZ-C06A6A6F2D3C|S-1-5-18 (Local System)|WinMgmt|63|Warning|HiPerfCooker_v1;Root\WMI 2011-12-08 19:50:12|appevent.evt|OZ-C06A6A6F2D3C|S-1-5-18 (Local System)|WinMgmt|63|Warning|CmdTriggerConsumer;Root\cimv2 2011-12-08 19:50:12|appevent.evt|OZ-C06A6A6F2D3C|S-1-5-18 (Local System)|WinMgmt|63|Warning|CmdTriggerConsumer;Root\cimv2 2011-12-08 19:50:12|appevent.evt|OZ-C06A6A6F2D3C|S-1-5-18 (Local System)|WinMgmt|5603|Warning|Rsop Planning Mode Provider;root\RSOP [REMOVED]
filescan
- Description
- Scan Physical memory for _FILE_OBJECT pool allocations
- Output example
$ python vol.py -f ~/memdump/infected.img filescan Volatile Systems Volatility Framework 2.2 Offset(P) #Ptr #Hnd Access Name ---------- ------ ------ ------ ---- 0x01e1d5d8 3 0 RWD--- \Device\HarddiskVolume1\$Directory 0x01e1d670 1 0 -W---- \Device\HarddiskVolume1\Documents and Settings\pilou\Local Settings\Application Data\Google\Chrome\User Data\chrome_shutdown_ms.txt 0x01e1e970 3 0 RWD--- \Device\HarddiskVolume1\$Directory 0x01e1f890 1 0 R--rwd \Device\HarddiskVolume1\WINDOWS\system32\d3d8thk.dll 0x01e26628 1 0 R--r-- \Device\HarddiskVolume1\WINDOWS\system32\win32k.sys 0x01e26a90 1 0 R--rw- \Device\HarddiskVolume1\Documents and Settings\pilou\Local Settings\Application Data\Google\Chrome\User Data\Default\Session Storage\000005.sst 0x01e27628 1 0 -WD--- \Device\HarddiskVolume1??INDOWS\SoftwareDistribution\Download\2b92e2dcf8ad4df7317e353becd67cd7\_useselfcontained_.state 0x01e28e70 1 0 RW-rw- \Device\HarddiskVolume1\Documents and Settings\pilou\Local Settings\Application Data\Google\Chrome\User Data\Default\Network Action Predictor 0x01e29bb8 1 0 -WD--- \Device\HarddiskVolume1????DOWS\SoftwareDistributio?????? 0x01e29c50 1 0 -WD--- \Device\HarddiskVolume1\WINDOWS\SoftwareDistribution\Download\e07b1f39ad7efdd3145745a305217a88\_unpacked_.state 0x01e29ce8 1 0 -WD--- \Device\HarddiskVolume1????DOWS\SoftwareDistribution\Download\e07b1f39ad7efdd3145745a305217a88\_downloadprogress_.state 0x01e2a1b8 1 0 R--r-d \Device\HarddiskVolume1\WINDOWS\system32\h323.tsp 0x01e2a510 1 1 R--rw- \Device\HarddiskVolume1\WINDOWS\WinSxS\x86_Microsoft.Windows.Common-Controls_6595b64144ccf1df_6.0.2600.6028_x-ww_61e65202 0x01e2b450 3 0 RWD--- \Device\HarddiskVolume1\$Directory [REMOVED]
gahti
- Description
- Dump the USER handle type information
- Output example
$ python vol.py -f ~/memdump/infected.img gahti
Volatile Systems Volatility Framework 2.2
Session Type Tag fnDestroy Flags
-------- -------------------- -------- ---------- -----
0 TYPE_FREE 0x00000000
0 TYPE_WINDOW Uswd 0xbf89dd3b OCF_DESKTOPHEAP, OCF_THREADOWNED, OCF_USEPOOLIFNODESKTOP, OCF_USEPOOLQUOTA
0 TYPE_MENU 0xbf896641 OCF_DESKTOPHEAP, OCF_PROCESSOWNED
0 TYPE_CURSOR Uscu 0xbf89ed85 OCF_MARKPROCESS, OCF_PROCESSOWNED, OCF_USEPOOLQUOTA
0 TYPE_SETWINDOWPOS Ussw 0xbf81f9c4 OCF_THREADOWNED, OCF_USEPOOLQUOTA
0 TYPE_HOOK 0xbf860442 OCF_DESKTOPHEAP, OCF_THREADOWNED
0 TYPE_CLIPDATA Uscb 0xbf91c359
0 TYPE_CALLPROC 0xbf85df2f OCF_DESKTOPHEAP, OCF_PROCESSOWNED
0 TYPE_ACCELTABLE Usac 0xbf85df2f OCF_PROCESSOWNED, OCF_USEPOOLQUOTA
0 TYPE_DDEACCESS Usd9 0xbf91c359 OCF_THREADOWNED, OCF_USEPOOLQUOTA
0 TYPE_DDECONV UsdA 0xbf922619 OCF_THREADOWNED, OCF_USEPOOLQUOTA
0 TYPE_DDEXACT UsdB 0xbf922560 OCF_THREADOWNED, OCF_USEPOOLQUOTA
0 TYPE_MONITOR Usdi 0xbf931dfd OCF_SHAREDHEAP
0 TYPE_KBDLAYOUT Uskb 0xbf912a22
0 TYPE_KBDFILE Uskf 0xbf92a5c9
0 TYPE_WINEVENTHOOK Uswe 0xbf8ebdce OCF_THREADOWNED
0 TYPE_TIMER Ustm 0xbf80e874
0 TYPE_INPUTCONTEXT Usim 0xbf92b18d OCF_DESKTOPHEAP, OCF_THREADOWNED
0 TYPE_HIDDATA Usha 0xbf93291a OCF_THREADOWNED
0 TYPE_DEVICEINFO UsDI 0xbf881c48
gditimers
- Description
- Print installed GDI timers and callbacks
- Output example
$ python vol.py -f ~/memdump/infected.img gditimers Volatile Systems Volatility Framework 2.2 Sess Handle Object Thread Process nID Rate(ms) Countdown(ms) Func ------ ---------- ---------- -------- -------------------- ---------- ---------- ------------- ---------- 0 0x20033 0xe1956800 808 -:- 0x7ffe 1000 171 0xbf8012fb 0 0x130053 0xe168ebc8 808 -:- 0x7ffd 35000 29359 0xbf8f3acc 0 0x10087 0xe1c1b818 1812 -:- 0x7ffb 60000 38093 0x74ec1070 0 0x200cf 0xe20c46f0 812 -:- 0xfff5 100 100 0xbf80a556 0 0x400d5 0xe1e8f298 556 -:- 0x15 60000 3031 0x00000000 0 0x400d9 0xe1ee3008 556 -:- 0x19 86400000 85626532 0x00000000 0 0xc00fb 0xe17b2178 896 -:- 0x3e8 14400000 13401860 0x00000000 0 0x460107 0xe185e4c0 556 -:- 0x0 60000 6625 0x00000000 0 0x2470135 0xe18206a0 508 -:- 0x1 530 437 0x00000000 0 0x740147 0xe24bea88 556 -:- 0xe 43200000 42426328 0x00000000 0 0x60153 0xe1eda860 2572 -:- 0x7fc9 1000 937 0x763ee0eb 0 0x201a1 0xe1f31e40 1656 -:- 0x0 300000 251312 0x774f2d77 0 0xa021d 0xe21e8120 896 -:- 0x3e9 86400000 85397375 0x00000000
gdt
- Description
- Display Global Descriptor Table
- Output example
$ python vol.py -f ~/memdump/infected.img gdt
Volatile Systems Volatility Framework 2.2
CPU Sel Base Limit Type DPL Gr Pr
------ ---------- ---------- ---------- -------------- ------ ---- ----
0 0x0 0x00000000 0x00000000 <Reserved> 0 By Np
0 0x8 0x00000000 0xffffffff Code RE Ac 0 Pg P
0 0x10 0x00000000 0xffffffff Data RW Ac 0 Pg P
0 0x18 0x00000000 0xffffffff Code RE Ac 3 Pg P
0 0x20 0x00000000 0xffffffff Data RW Ac 3 Pg P
0 0x28 0x80042000 0x000020ab TSS32 Busy 0 By P
0 0x30 0xffdff000 0x00001fff Data RW Ac 0 Pg P
0 0x38 0x7ffdd000 0x00000fff Data RW Ac 3 By P
0 0x40 0x00000400 0x0000ffff Data RW 3 By P
0 0x48 0x00000000 0x00000000 <Reserved> 0 By Np
0 0x50 0x8054a080 0x00000068 TSS32 Avl 0 By P
0 0x58 0x8054a0e8 0x00000068 TSS32 Avl 0 By P
0 0x60 0x00022f40 0x0000ffff Data RW Ac 0 By P
0 0x68 0x000b8000 0x00003fff Data RW 0 By P
0 0x70 0xffff7000 0x000003ff Data RW 0 By P
0 0x78 0x80400000 0x0000ffff Code RE 0 By P
0 0x80 0x80400000 0x0000ffff Data RW 0 By P
0 0x88 0x00000000 0x00000000 Data RW 0 By P
[REMOVED]
getservicesids
- Description
- Get the names of services in the Registry and return Calculated SID
- Output example
$ python vol.py -f ~/memdump/infected.img getservicesids
Volatile Systems Volatility Framework 2.2
servicesids = {
'S-1-5-80-2675092186-3691566608-1139246469-1504068187-1286574349': 'Abiosdsk',
'S-1-5-80-384935-177232180-2275229793-1867620679-4069250810': 'abp470n5',
'S-1-5-80-2200411935-3214395760-3985565908-2861215955-1226862917': 'abp480n5',
'S-1-5-80-850610371-2162948594-2204246734-1395993891-583065928': 'ACPIEC',
'S-1-5-80-3725335247-1751848567-2456254030-120447533-3735992947': 'AdobeFlashPlayerUpdateSvc',
'S-1-5-80-2838020983-819055183-730598559-323496739-448665943': 'adpu160m',
'S-1-5-80-3218321610-3296847771-3570773115-868698368-3117473630': 'aec',
'S-1-5-80-934984265-4079461471-3978616717-2318450786-290302611': 'Aha154x',
'S-1-5-80-1344778701-2960353790-662938617-678076498-4183748354': 'aic78u2',
'S-1-5-80-1076555770-1261388817-3553637611-899283093-3303637635': 'Alerter',
'S-1-5-80-1587539839-2488332913-1287008632-3751426284-4220573165': 'AliIde',
'S-1-5-80-3980410673-3391719637-2113285402-1294014731-1235999994': 'amsint',
'S-1-5-80-2636016386-2318576122-4003064359-4163118804-2687887603': 'asc',
'S-1-5-80-3570203740-1408783918-3026009114-267332295-1428103130': 'asc3350p',
[REMOVED]
getsids
- Description
- Print the SIDs owning each process
- Options
- -o OFFSET, --offset=OFFSET
- EPROCESS offset (in hex) in the physical address space
- -p PID, --pid=PID
- Operate on these Process IDs (comma-separated)
- Output example
$ python vol.py -f ~/memdump/infected.img getsids -p 532 Volatile Systems Volatility Framework 2.2 vmtoolsd.exe (532): S-1-5-21-1801674531-1647877149-682003330-1003 vmtoolsd.exe (532): S-1-5-21-1801674531-1647877149-682003330-513 (Domain Users) vmtoolsd.exe (532): S-1-1-0 (Everyone) vmtoolsd.exe (532): S-1-5-32-544 (Administrators) vmtoolsd.exe (532): S-1-5-32-545 (Users) vmtoolsd.exe (532): S-1-5-4 (Interactive) vmtoolsd.exe (532): S-1-5-11 (Authenticated Users) vmtoolsd.exe (532): S-1-5-5-0-65129 (Logon Session) vmtoolsd.exe (532): S-1-2-0 (Local (Users with the ability to log in locally)) [REMOVED]
handles
- Description
- Print list of open handles for each process
- Options
- -o OFFSET, --offset=OFFSET
- EPROCESS offset (in hex) in the physical address space
- -p PID, --pid=PID
- Operate on these Process IDs (comma-separated)
- -P, --physical-offset
- Physical Offset
- -t OBJECT_TYPE, --object-type=OBJECT_TYPE
- Show these object types (comma-separated)
- -s, --silent
- Suppress less meaningful results
- Output example
$ python vol.py -f ~/memdump/infected.img handles -p 532 -s Volatile Systems Volatility Framework 2.2 Offset(V) Pid Handle Access Type Details ---------- ------ ---------- ---------- ---------------- ------- 0xe1005448 532 0x4 0xf0003 KeyedEvent CritSecOutOfMemoryEvent 0xe182a4d8 532 0x8 0x3 Directory KnownDlls 0x8223c190 532 0xc 0x100020 File \Device\HarddiskVolume1\Documents and Settings\pilou 0x81dd4d00 532 0x10 0x100020 File \Device\HarddiskVolume1\WINDOWS\WinSxS\x86_Microsoft.VC90.CRT_1fc8b3b9a1e18e3b_9.0.30729.4148_x-ww_d495ac4e 0xe193c768 532 0x14 0xf000f Directory Windows 0x81dc6028 532 0x1c 0x100020 File \Device\HarddiskVolume1\WINDOWS\WinSxS\x86_Microsoft.VC90.CRT_1fc8b3b9a1e18e3b_9.0.30729.4148_x-ww_d495ac4e 0x81f21bb0 532 0x20 0x100020 File \Device\HarddiskVolume1\WINDOWS\WinSxS\x86_Microsoft.VC90.CRT_1fc8b3b9a1e18e3b_9.0.30729.4148_x-ww_d495ac4e 0x81e5bdb8 532 0x28 0x100020 File \Device\HarddiskVolume1\WINDOWS\WinSxS\x86_Microsoft.VC90.CRT_1fc8b3b9a1e18e3b_9.0.30729.4148_x-ww_d495ac4e 0x81dd07b0 532 0x2c 0x100020 File \Device\HarddiskVolume1\WINDOWS\WinSxS\x86_Microsoft.VC90.CRT_1fc8b3b9a1e18e3b_9.0.30729.4148_x-ww_d495ac4e 0x8227c2b0 532 0x30 0x100020 File \Device\HarddiskVolume1\WINDOWS\WinSxS\x86_Microsoft.VC90.CRT_1fc8b3b9a1e18e3b_9.0.30729.4148_x-ww_d495ac4e 0x821b5300 532 0x34 0x100020 File \Device\HarddiskVolume1\WINDOWS\WinSxS\x86_Microsoft.VC90.CRT_1fc8b3b9a1e18e3b_9.0.30729.4148_x-ww_d495ac4e 0x81e837c0 532 0x38 0x100020 File \Device\HarddiskVolume1\WINDOWS\WinSxS\x86_Microsoft.VC90.CRT_1fc8b3b9a1e18e3b_9.0.30729.4148_x-ww_d495ac4e 0xe1e7de28 532 0x40 0x20f003f Key MACHINE 0x81f722d0 532 0x44 0xf037f WindowStation WinSta0 0x81eb48b0 532 0x4c 0xf01ff Desktop Default 0x81f722d0 532 0x50 0xf037f WindowStation WinSta0 0x82285ea8 532 0x54 0x100001 File \Device\KsecDD [REMOVED]
hashdump
- Description
- Dumps passwords hashes (LM/NTLM) from memory
- Options
- -y SYS_OFFSET, --sys-offset=SYS_OFFSET
- SYSTEM hive offset (virtual)
- -s SAM_OFFSET, --sam-offset=SAM_OFFSET
- SAM hive offset (virtual)
- Output example
We need the hive list so we can get the starting location in memory where the registry information resides:
$ python vol.py -f ~/memdump/infected.img hivelist Volatile Systems Volatility Framework 2.2 Virtual Physical Name ---------- ---------- ---- 0xe2084008 0x0fe6b008 \Device\HarddiskVolume1\Documents and Settings\pilou\Local Settings\Application Data\Microsoft\Windows\UsrClass.dat 0xe1d1fb60 0x0db99b60 \Device\HarddiskVolume1\Documents and Settings\pilou\NTUSER.DAT 0xe19d8380 0x0d091380 \Device\HarddiskVolume1\Documents and Settings\LocalService\Local Settings\Application Data\Microsoft\Windows\UsrClass.dat 0xe1c19508 0x0d644508 \Device\HarddiskVolume1\Documents and Settings\LocalService\NTUSER.DAT 0xe17206d0 0x0cad76d0 \Device\HarddiskVolume1\Documents and Settings\NetworkService\Local Settings\Application Data\Microsoft\Windows\UsrClass.dat 0xe19fb008 0x0d403008 \Device\HarddiskVolume1\Documents and Settings\NetworkService\NTUSER.DAT 0xe196c6b8 0x0a9ca6b8 \Device\HarddiskVolume1\WINDOWS\system32\config\software 0xe1599b60 0x04870b60 \Device\HarddiskVolume1\WINDOWS\system32\config\default 0xe196cb60 0x0a9cab60 \Device\HarddiskVolume1\WINDOWS\system32\config\SECURITY 0xe195eb60 0x0a6e2b60 \Device\HarddiskVolume1\WINDOWS\system32\config\SAM 0xe134f350 0x02f00350 [no name] 0xe1035b60 0x02aa3b60 \Device\HarddiskVolume1\WINDOWS\system32\config\system 0xe102e008 0x02a9d008 [no name] 0x806717a8 0x006717a8 [no name]
Then dump the hashes as follows:
$ python vol.py -f ~/memdump/infected.img hashdump -s 0xe195eb60 -y 0xe1035b60 Volatile Systems Volatility Framework 2.2 Administrateur:500:e039e3178e07d0c9a6e1e67c15d6275b:b246b548b6f17e45f349aa2214a5f6aa:::
You can then use online resources or a has cracker like John to crack the hash.
hibinfo
- Description
- Dump hibernation file information
- Output example
$ python vol.py -f hiberfil.sys --profile=Win7SP1x64 hibinfo IMAGE_HIBER_HEADER: Signature: HIBR SystemTime: 2011-12-23 16:34:27 Control registers flags CR0: 80050031 CR0[PAGING]: 1 CR3: 00187000 CR4: 000006f8 CR4[PSE]: 1 CR4[PAE]: 1 Windows Version is 6.1 (7601)
hivedump
- Description
- Prints out a hive
- Options
- -o HIVE_OFFSET, --hive-offset=HIVE_OFFSET
- Hive offset (virtual)
- Output example
See hivelist to get the offset of a hive
$ python vol.py -f ~/memdump/infected.img hivedump -o 0xe196cb60 Volatile Systems Volatility Framework 2.2 Last Written Key 2013-02-18 20:54:33 \SECURITY 2012-03-17 16:29:11 \SECURITY\Cache 2011-12-08 19:49:19 \SECURITY\Policy 2011-12-08 20:00:07 \SECURITY\Policy\Accounts 2011-12-08 20:44:26 \SECURITY\Policy\Accounts\S-1-1-0 2011-12-08 20:44:58 \SECURITY\Policy\Accounts\S-1-1-0\ActSysAc 2011-12-08 20:44:58 \SECURITY\Policy\Accounts\S-1-1-0\Privilgs 2011-12-08 20:44:26 \SECURITY\Policy\Accounts\S-1-1-0\SecDesc 2011-12-08 20:44:26 \SECURITY\Policy\Accounts\S-1-1-0\Sid 2011-12-08 20:44:58 \SECURITY\Policy\Accounts\S-1-5-19 [REMOVED]
hivelist
- Description
- Print list of registry hives.
- Output example
$ python vol.py -f ~/memdump/infected.img hivelist Volatile Systems Volatility Framework 2.2 Virtual Physical Name ---------- ---------- ---- 0xe2084008 0x0fe6b008 \Device\HarddiskVolume1\Documents and Settings\pilou\Local Settings\Application Data\Microsoft\Windows\UsrClass.dat 0xe1d1fb60 0x0db99b60 \Device\HarddiskVolume1\Documents and Settings\pilou\NTUSER.DAT 0xe19d8380 0x0d091380 \Device\HarddiskVolume1\Documents and Settings\LocalService\Local Settings\Application Data\Microsoft\Windows\UsrClass.dat 0xe1c19508 0x0d644508 \Device\HarddiskVolume1\Documents and Settings\LocalService\NTUSER.DAT 0xe17206d0 0x0cad76d0 \Device\HarddiskVolume1\Documents and Settings\NetworkService\Local Settings\Application Data\Microsoft\Windows\UsrClass.dat 0xe19fb008 0x0d403008 \Device\HarddiskVolume1\Documents and Settings\NetworkService\NTUSER.DAT 0xe196c6b8 0x0a9ca6b8 \Device\HarddiskVolume1\WINDOWS\system32\config\software 0xe1599b60 0x04870b60 \Device\HarddiskVolume1\WINDOWS\system32\config\default 0xe196cb60 0x0a9cab60 \Device\HarddiskVolume1\WINDOWS\system32\config\SECURITY 0xe195eb60 0x0a6e2b60 \Device\HarddiskVolume1\WINDOWS\system32\config\SAM 0xe134f350 0x02f00350 [no name] 0xe1035b60 0x02aa3b60 \Device\HarddiskVolume1\WINDOWS\system32\config\system 0xe102e008 0x02a9d008 [no name] 0x806717a8 0x006717a8 [no name] [REMOVED]
Windows NT-based systems store the registry in a binary file format which can be exported, loaded and unloaded by the Registry Editor in these operating systems. The following system Registry files are stored in %SystemRoot%\System32\Config\:
- Sam – HKEY_LOCAL_MACHINE\SAMSecurity – HKEY_LOCAL_MACHINE\SECURITY
- Software – HKEY_LOCAL_MACHINE\SOFTWARE
- System – HKEY_LOCAL_MACHINE\SYSTEM
- Default – HKEY_USERS\.DEFAULT
- Userdiff – Not associated with a hive. Used only when upgrading operating systems.[29]
The following file is stored in each user's profile folder:
- %UserProfile%\Ntuser.dat – HKEY_USERS\<User SID> (linked to by HKEY_CURRENT_USER)
For Windows 2000, Server 2003 and Windows XP, the following additional user-specific file is used for file associations and COM information:
- %UserProfile%\Local Settings\Application Data\Microsoft\Windows\Usrclass.dat (path is localized) – HKEY_USERS\<User SID>_Classes (HKEY_CURRENT_USER\Software\Classes)
For Windows Vista and later, the path was changed to:
- %UserProfile%\AppData\Local\Microsoft\Windows\Usrclass.dat (path is not localized) alias %LocalAppData%\Microsoft\Windows\Usrclass.dat – HKEY_USERS\<User SID>_Classes (HKEY_CURRENT_USER\Software\Classes)
Windows 2000 kept an alternate copy of the registry hives (.ALT) and attempts to switch to it when corruption is detected.[30] Windows XP and Windows Server 2003 do not maintain a System.alt hive because NTLDR on those versions of Windows can process the System.log file to bring up to date a System hive that has become inconsistent during a shutdown or crash. In addition, the %SystemRoot%\Repair folder contains a copy of the system's registry hives that were created after installation and the first successful startup of Windows. Each registry data file has an associated file with a ".log" extension that acts as a transaction log that is used to ensure that any interrupted updates can be completed upon next startup.[31] Internally, registry files are split into 4 kB "bins" that contain collections of "cells".
For more information, please refer to http://en.wikipedia.org/wiki/Windows_Registry.
hivescan
- Description
- Scan Physical memory for _CMHIVE objects (registry hives)
- Output example
$ python vol.py -f ~/memdump/infected.img hivescan Volatile Systems Volatility Framework 2.2 Offset(P) ---------- 0x02a9d008 0x02aa3b60 0x02f00350 0x04870b60 0x0a6e2b60 0x0a9ca6b8 0x0a9cab60 0x0c0d6350 0x0cad76d0 0x0d091380 0x0d403008 0x0d644508 0x0db99b60 0x0fe6b008 0x13037b60 0x160dc008 0x16186380 0x16745350 0x16e85b60 0x18960b60 0x1a0f8008 0x1ebf5008
idt
- Description
- Display Interrupt Descriptor Table
- Output example
$ python vol.py -f ~/memdump/infected.img idt
Volatile Systems Volatility Framework 2.2
CPU Index Selector Value Module Section
------ ------ -------- ---------- -------------------- ------------
0 0 8 0x8053e29c ntoskrnl.exe .text
0 1 8 0x8053e414 ntoskrnl.exe .text
0 2 88 0x00000000 ntoskrnl.exe
0 3 8 0x8053e7e4 ntoskrnl.exe .text
0 4 8 0x8053e964 ntoskrnl.exe .text
0 5 8 0x8053eac0 ntoskrnl.exe .text
0 6 8 0x8053ec34 ntoskrnl.exe .text
0 7 8 0x8053f29c ntoskrnl.exe .text
0 8 80 0x00000000 ntoskrnl.exe
0 9 8 0x8053f6c0 ntoskrnl.exe .text
0 A 8 0x8053f7e0 ntoskrnl.exe .text
0 B 8 0x8053f920 ntoskrnl.exe .text
0 C 8 0x8053fb7c ntoskrnl.exe .text
0 D 8 0x8053fe60 ntoskrnl.exe .text
0 E 8 0x80540568 ntoskrnl.exe .text
0 F 8 0x80540898 ntoskrnl.exe .text
0 10 8 0x805409b8 ntoskrnl.exe .text
0 11 8 0x80540af0 ntoskrnl.exe .text
0 12 160 0x80540898 UNKNOWN
0 13 8 0x80540c58 ntoskrnl.exe .text
0 14 8 0x80540898 ntoskrnl.exe .text
0 15 8 0x80540898 ntoskrnl.exe .text
[REMOVED}
imagecopy
- Description
- convert any existing type of address space (such as a crashdump, hibernation file, or live firewire session) to a raw memory image
- Options
- -b 5242880, --blocksize=5242880
- Size (in bytes) of blocks to copy
- -O OUTPUT_IMAGE, --output-image=OUTPUT_IMAGE
- Writes a raw DD image out to OUTPUT-IMAGE
- Output example
$ python vol.py imagecopy -f win7.dmp --profile=Win7SP0x86 -O win7.raw Volatile Systems Volatility Framework 2.0 Writing data (5.00 MB chunks): |.....................................................|
imageinfo
- Description
- Identify information for the image
- Output example
$ python vol.py -f ~/tmp/infected.img imageinfo
Volatile Systems Volatility Framework 2.1
Determining profile based on KDBG search...
Suggested Profile(s) : WinXPSP2x86, WinXPSP3x86 (Instantiated with WinXPSP2x86)
AS Layer1 : JKIA32PagedMemoryPae (Kernel AS)
AS Layer2 : FileAddressSpace (/Users/sebastiendamaye/tmp/infected.img)
PAE type : PAE
DTB : 0x31e000L
KDBG : 0x80545c60
Number of Processors : 1
Image Type (Service Pack) : 3
KPCR for CPU 0 : 0xffdff000
KUSER_SHARED_DATA : 0xffdf0000
Image date and time : 2013-02-18 21:20:52 UTC+0000
Image local date and time : 2013-02-18 22:20:52 +0100
impscan
- Description
- Scan for calls to imported functions
- Options
- -p PID, --pid=PID
- Process ID (leave off to scan kernel memory)
- -b BASE, --base=BASE
- Base address in process memory if --pid is supplied, otherwise an address in kernel space
- -s SIZE, --size=SIZE
- Size of memory to scan
- Output example
$ python vol.py -f ~/memdump/infected.img impscan -p 532 Volatile Systems Volatility Framework 2.2 IAT Call Module Function ---------- ---------- -------------------- -------- 0x00407000 0x77da7cb8 ADVAPI32.dll FreeSid 0x00407004 0x77db4b05 ADVAPI32.dll SetSecurityDescriptorOwner 0x00407008 0x77da79eb ADVAPI32.dll SetSecurityDescriptorDacl 0x0040700c 0x77da79c6 ADVAPI32.dll InitializeSecurityDescriptor 0x00407010 0x77db4ec2 ADVAPI32.dll SetEntriesInAclW 0x00407014 0x77da7cc9 ADVAPI32.dll AllocateAndInitializeSid 0x00407054 0x7c81f424 kernel32.dll IsDebuggerPresent 0x00407058 0x7c864042 kernel32.dll UnhandledExceptionFilter 0x0040705c 0x7c801e1a kernel32.dll TerminateProcess 0x00407060 0x7c8017e9 kernel32.dll GetSystemTimeAsFileTime 0x00407064 0x7c8099c0 kernel32.dll GetCurrentProcessId 0x00407068 0x7c8097d0 kernel32.dll GetCurrentThreadId [REMOVED]
kdbgscan
- Description
- Search for and dump potential KDBG values
- Output example
$ python vol.py -f ~/memdump/infected.img kdbgscan Volatile Systems Volatility Framework 2.2 ************************************************** Instantiating KDBG using: Kernel AS WinXPSP2x86 (5.1.0 32bit) Offset (V) : 0x80545c60 Offset (P) : 0x545c60 KDBG owner tag check : True Profile suggestion (KDBGHeader): WinXPSP3x86 Version64 : 0x80545c38 (Major: 15, Minor: 2600) Service Pack (CmNtCSDVersion) : 3 Build string (NtBuildLab) : 2600.xpsp_sp3_gdr.120821-1629 PsActiveProcessHead : 0x8055a2d8 (35 processes) PsLoadedModuleList : 0x80554140 (124 modules) KernelBase : 0x804d7000 (Matches MZ: True) Major (OptionalHeader) : 5 Minor (OptionalHeader) : 1 KPCR : 0xffdff000 (CPU 0) [REMOVED]
kpcrscan
- Description
- Search for and dump potential KPCR (Kernel Processor Control Region) values
- Output example
$ python vol.py --profile=Win7SP0x86 -f win7.dmp kpcrscan Volatile Systems Volatility Framework 2.0 Potential KPCR structure virtual addresses: _KPCR: 0x8296dc00
ldrmodules
- Description
- Detect unlinked DLLs
- Options
- -o OFFSET, --offset=OFFSET
- EPROCESS offset (in hex) in the physical address space
- -p PID, --pid=PID
- Operate on these Process IDs (comma-separated)
- Output example
$ python vol.py -f ~/memdump/infected.img ldrmodules -p 532
Volatile Systems Volatility Framework 2.2
Pid Process Base InLoad InInit InMem MappedPath
-------- -------------------- ---------- ------ ------ ----- ----------
532 vmtoolsd.exe 0x01ef0000 True True True \WINDOWS\system32\vmhgfs.dll
532 vmtoolsd.exe 0x00400000 True False True \Program Files\VMware\VMware Tools\vmtoolsd.exe
532 vmtoolsd.exe 0x76930000 True True True \WINDOWS\system32\ntshrui.dll
532 vmtoolsd.exe 0x77f40000 True True True \WINDOWS\system32\shlwapi.dll
532 vmtoolsd.exe 0x62e40000 True True True \WINDOWS\system32\hnetcfg.dll
532 vmtoolsd.exe 0x77be0000 True True True \WINDOWS\system32\msvcrt.dll
532 vmtoolsd.exe 0x71990000 True True True \WINDOWS\system32\mswsock.dll
532 vmtoolsd.exe 0x779e0000 True True True \WINDOWS\system32\crypt32.dll
532 vmtoolsd.exe 0x778e0000 True True True \WINDOWS\system32\setupapi.dll
532 vmtoolsd.exe 0x77fc0000 True True True \WINDOWS\system32\secur32.dll
532 vmtoolsd.exe 0x719d0000 True True True \WINDOWS\system32\wshtcpip.dll
532 vmtoolsd.exe 0x71be0000 True True True \WINDOWS\system32\netrap.dll
[REMOVED]
lsadump
- Description
- Dump (decrypted) LSA secrets from the registry
- Options
- -y SYS_OFFSET, --sys-offset=SYS_OFFSET
- SYSTEM hive offset (virtual)
- -s SEC_OFFSET, --sec-offset=SEC_OFFSET
- SECURITY hive offset (virtual)
- Output example
- N/A
malfind
- Description
- Find hidden and injected code
- Options
- -o OFFSET, --offset=OFFSET
- EPROCESS offset (in hex) in the physical address space
- -p PID, --pid=PID
- Operate on these Process IDs (comma-separated)
- -D DUMP_DIR, --dump-dir=DUMP_DIR
- Directory in which to dump the VAD files
- Output example
$ python vol.py -f ~/memdump/infected.img malfind -p 532 -D output/ Volatile Systems Volatility Framework 2.2 Process: vmtoolsd.exe Pid: 532 Address: 0x3140000 Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE Flags: CommitCharge: 4147, MemCommit: 1, PrivateMemory: 1, Protection: 6 0x03140000 4d 5a 90 00 03 00 00 00 04 00 00 00 ff ff 00 00 MZ.............. 0x03140010 b8 00 00 00 00 00 00 00 40 00 00 00 00 00 00 00 ........@....... 0x03140020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0x03140030 00 00 00 00 00 00 00 00 00 00 00 00 e0 00 00 00 ................ 0x3140000 4d DEC EBP 0x3140001 5a POP EDX 0x3140002 90 NOP 0x3140003 0003 ADD [EBX], AL 0x3140005 0000 ADD [EAX], AL 0x3140007 000400 ADD [EAX+EAX], AL 0x314000a 0000 ADD [EAX], AL 0x314000c ff DB 0xff 0x314000d ff00 INC DWORD [EAX] 0x314000f 00b800000000 ADD [EAX+0x0], BH 0x3140015 0000 ADD [EAX], AL 0x3140017 004000 ADD [EAX+0x0], AL 0x314001a 0000 ADD [EAX], AL 0x314001c 0000 ADD [EAX], AL 0x314001e 0000 ADD [EAX], AL 0x3140020 0000 ADD [EAX], AL 0x3140022 0000 ADD [EAX], AL 0x3140024 0000 ADD [EAX], AL 0x3140026 0000 ADD [EAX], AL 0x3140028 0000 ADD [EAX], AL 0x314002a 0000 ADD [EAX], AL 0x314002c 0000 ADD [EAX], AL 0x314002e 0000 ADD [EAX], AL 0x3140030 0000 ADD [EAX], AL 0x3140032 0000 ADD [EAX], AL 0x3140034 0000 ADD [EAX], AL 0x3140036 0000 ADD [EAX], AL 0x3140038 0000 ADD [EAX], AL 0x314003a 0000 ADD [EAX], AL 0x314003c e000 LOOPNZ 0x314003e 0x314003e 0000 ADD [EAX], AL [REMOVED]
memdump
- Description
- Dump the addressable memory for a process
- Options
- -o OFFSET, --offset=OFFSET
- EPROCESS offset (in hex) in the physical address space
- -p PID, --pid=PID
- Operate on these Process IDs (comma-separated)
- -D DUMP_DIR, --dump-dir=DUMP_DIR
- Directory in which to dump memory
- Output example
$ python vol.py -f ~/memdump/infected.img memdump -p 532 --dump-dir output/ Volatile Systems Volatility Framework 2.2 ************************************************************************ Writing vmtoolsd.exe [ 532] to 532.dmp
memmap
- Description
- Print the memory map
- Options
- -o OFFSET, --offset=OFFSET
- EPROCESS offset (in hex) in the physical address space
- -p PID, --pid=PID
- Operate on these Process IDs (comma-separated)
- Output example
$ python vol.py -f ~/memdump/infected.img memmap -p 532 Volatile Systems Volatility Framework 2.2 vmtoolsd.exe pid: 532 Virtual Physical Size DumpFileOffset ---------- ---------- ---------- -------------- 0x00010000 0x11bb9000 0x1000 0x0 0x00020000 0x11b7a000 0x1000 0x1000 0x00126000 0x11f02000 0x1000 0x2000 0x00127000 0x12041000 0x1000 0x3000 0x00128000 0x12340000 0x1000 0x4000 0x00129000 0x11f3f000 0x1000 0x5000 0x0012a000 0x11ffe000 0x1000 0x6000 0x0012b000 0x1203d000 0x1000 0x7000 [REMOVED]
messagehooks
- Description
- List desktop and thread window message hooks
- Options
- Output example
$ python vol.py -f laqma.vmem messagehooks --output=block Volatile Systems Volatility Framework 2.1_alpha Offset(V) : 0xbc693988 Session : 0 Desktop : WinSta0\Default Thread : <any> Filter : WH_GETMESSAGE Flags : HF_ANSI, HF_GLOBAL Procedure : 0x1fd9 ihmod : 1 Module : C:\WINDOWS\system32\Dll.dll Offset(V) : 0xbc693988 Session : 0 Desktop : WinSta0\Default Thread : 1584 (explorer.exe 1624) Filter : WH_GETMESSAGE Flags : HF_ANSI, HF_GLOBAL Procedure : 0x1fd9 ihmod : 1 Module : C:\WINDOWS\system32\Dll.dll Offset(V) : 0xbc693988 Session : 0 Desktop : WinSta0\Default Thread : 252 (VMwareUser.exe 1768) Filter : WH_GETMESSAGE Flags : HF_ANSI, HF_GLOBAL Procedure : 0x1fd9 ihmod : 1 Module : C:\WINDOWS\system32\Dll.dll
moddump
- Description
- Dump a kernel driver to an executable file sample
- Options
- -D DUMP_DIR, --dump-dir=DUMP_DIR
- Directory in which to dump executable files
- -u, --unsafe
- Bypasses certain sanity checks when creating image
- -r REGEX, --regex=REGEX
- Dump modules matching REGEX
- -i, --ignore-case
- Ignore case in pattern match
- -b BASE, --base=BASE
- Dump driver with BASE address (in hex)
- Output example
$ python vol.py -f ~/memdump/infected.img moddump --dump-dir output/ Volatile Systems Volatility Framework 2.2 Module Base Module Name Result ----------- -------------------- ------ 0x0804d7000 ntoskrnl.exe OK: driver.804d7000.sys 0x0806d1000 hal.dll OK: driver.806d1000.sys 0x0f84dc000 fltMgr.sys Error: Cannot acquire AS 0x0f8bba000 Fs_Rec.SYS OK: driver.f8bba000.sys 0x0f8ce4000 dxgthk.sys OK: driver.f8ce4000.sys 0x0b239b000 dump_atapi.sys OK: driver.b239b000.sys 0x0f84fc000 atapi.sys Error: Cannot acquire AS 0x0f877a000 Fips.SYS OK: driver.f877a000.sys 0x0f8144000 mouhid.sys OK: driver.f8144000.sys [REMOVED]
modscan
- Description
- Scan Physical memory for _LDR_DATA_TABLE_ENTRY objects
- Output example
$ python vol.py -f ~/memdump/infected.img modscan Volatile Systems Volatility Framework 2.2 Offset(P) Name Base Size File ---------- -------------------- ---------- ---------- ---- 0x01ed4508 kmixer.sys 0xb1610000 0x2b000 \SystemRoot\system32\drivers\kmixer.sys 0x02087100 rasacd.sys 0xf8b52000 0x3000 \SystemRoot\system32\DRIVERS\rasacd.sys 0x02094950 flpydisk.sys 0xf89ea000 0x5000 \SystemRoot\system32\DRIVERS\flpydisk.sys 0x020a0008 vmx_fb.dll 0xbf012000 0x19c000 \SystemRoot\System32\vmx_fb.dll 0x020b9af8 HIDPARSE.SYS 0xf8a32000 0x7000 \SystemRoot\system32\DRIVERS\HIDPARSE.SYS 0x020be820 netbios.sys 0xf876a000 0x9000 \SystemRoot\system32\DRIVERS\netbios.sys 0x020bf0e8 ndisuio.sys 0xb229b000 0x4000 \SystemRoot\system32\DRIVERS\ndisuio.sys 0x020c4ef0 HTTP.sys 0xb1777000 0x41000 \SystemRoot\System32\Drivers\HTTP.sys 0x020cda08 RDPCDD.sys 0xf8bc0000 0x2000 \SystemRoot\System32\DRIVERS\RDPCDD.sys [REMOVED]
modules
- Description
- Print list of loaded modules
- Options
- -P, --physical-offset
- Physical Offset
- Output example
$ python vol.py -f ~/memdump/infected.img modules Volatile Systems Volatility Framework 2.2 Offset(V) Name Base Size File ---------- -------------------- ---------- ---------- ---- 0x823fc3a0 ntoskrnl.exe 0x804d7000 0x1f9c80 \WINDOWS\system32\ntkrnlpa.exe 0x823fc338 hal.dll 0x806d1000 0x20300 \WINDOWS\system32\hal.dll 0x823fc2d0 kdcom.dll 0xf8b9a000 0x2000 \WINDOWS\system32\KDCOM.DLL 0x823fc260 BOOTVID.dll 0xf8aaa000 0x3000 \WINDOWS\system32\BOOTVID.dll 0x823fc1f8 ACPI.sys 0xf856a000 0x2f000 ACPI.sys 0x823fc188 WMILIB.SYS 0xf8b9c000 0x2000 \WINDOWS\system32\DRIVERS\WMILIB.SYS 0x823fc120 pci.sys 0xf8559000 0x11000 pci.sys 0x823fc0b0 isapnp.sys 0xf869a000 0xa000 isapnp.sys 0x823fc040 compbatt.sys 0xf8aae000 0x3000 compbatt.sys 0x823ed008 BATTC.SYS 0xf8ab2000 0x4000 \WINDOWS\system32\DRIVERS\BATTC.SYS
mutantscan
- Description
- Scan for mutant objects _KMUTANT
- Options
- -s, --silent
- Suppress less meaningful results
- Output example
$ python vol.py -f ~/memdump/infected.img mutantscan Volatile Systems Volatility Framework 2.2 Offset(P) #Ptr #Hnd Signal Thread CID Name ---------- ---- ---- ------ ---------- --------- ---- 0x01e2ba90 1 1 1 0x00000000 0x01e2c150 2 1 1 0x00000000 RAS_MO_02 0x01e34170 1 1 1 0x00000000 0x01e3c878 2 1 1 0x00000000 jqs.exeM_1512_ 0x01e3cfe0 3 2 1 0x00000000 WininetConnectionMutex 0x01e458e0 1 1 1 0x00000000 0x01eb7160 1 1 1 0x00000000 0x01ebbe28 2 1 1 0x00000000 vmtoolsd.exeM_1732_ 0x01ecb7f8 1 1 1 0x00000000 0x01ed5640 2 1 0 0x81ea9da0 1364:1520 Instance1: ESENT Performance Data Schema Version 40 0x01ed5eb8 2 1 1 0x00000000 !PrivacIE!SharedMemory!Mutex [REMOVED]
netscan
- Description
- To scan for network artifacts in 32- and 64-bit Windows Vista, Windows 2008 Server and Windows 7 memory dumps, use the netscan command.
- Output example
$ python vol.py -f ~/Desktop/win7_trial_64bit.raw --profile=Win7SP0x64 netscan Volatile Systems Volatility Framework 2.1_alpha Offset(P) Proto Local Address Foreign Address State Pid Owner Created 0xf882a30 TCPv4 0.0.0.0:135 0.0.0.0:0 LISTENING 628 svchost.exe 0xfc13770 TCPv4 0.0.0.0:49154 0.0.0.0:0 LISTENING 916 svchost.exe 0xfdda1e0 TCPv4 0.0.0.0:49154 0.0.0.0:0 LISTENING 916 svchost.exe 0xfdda1e0 TCPv6 :::49154 :::0 LISTENING 916 svchost.exe 0x1121b7b0 TCPv4 0.0.0.0:135 0.0.0.0:0 LISTENING 628 svchost.exe 0x1121b7b0 TCPv6 :::135 :::0 LISTENING 628 svchost.exe 0x11431360 TCPv4 0.0.0.0:49152 0.0.0.0:0 LISTENING 332 wininit.exe 0x11431360 TCPv6 :::49152 :::0 LISTENING 332 wininit.exe [REMOVED]
patcher
- Description
- Patches memory based on page scans

- Options
- -x XML_INPUT, --xml-input=XML_INPUT
- Input XML file for patching binaries (example given below)
<patchfile>
<patchinfo method="pagescan" name="Some Descriptive Name">
<constraints>
<match offset="0x123">554433221100</match>
</constraints>
<patches>
<setbytes offset="0x234">001122334455</setbytes>
</patches>
</patchinfo>
<patchinfo>
...
</patchinfo>
</patchfile>
printkey
- Description
- Print a registry key, and its subkeys and values
- Options
- -o HIVE_OFFSET, --hive-offset=HIVE_OFFSET
- Hive offset (virtual)
- -K KEY, --key=KEY
- Registry Key
- Output example
$ python vol.py -f ~/memdump/zeus2x4.vmem printkey --key="Software\Microsoft\Windows\CurrentVersion\Run"
Volatile Systems Volatility Framework 2.2
Legend: (S) = Stable (V) = Volatile
----------------------------
Registry: \Device\HarddiskVolume1\Documents and Settings\Administrator\NTUSER.DAT
Key name: Run (S)
Last updated: 2010-09-09 19:56:33
Subkeys:
Values:
REG_SZ {D9A7AA9F-6631-D3B2-E89F-56E338669386} : (S) "C:\Documents and Settings\Administrator\Application Data\Obyt\ihah.exe"
----------------------------
Registry: \Device\HarddiskVolume1\Documents and Settings\LocalService\NTUSER.DAT
Key name: Run (S)
Last updated: 2009-04-04 10:33:06
Subkeys:
Values:
----------------------------
Registry: \Device\HarddiskVolume1\WINDOWS\system32\config\default
Key name: Run (S)
Last updated: 2009-04-04 02:24:52
Subkeys:
Values:
----------------------------
Registry: \Device\HarddiskVolume1\Documents and Settings\NetworkService\NTUSER.DAT
Key name: Run (S)
Last updated: 2009-04-04 10:33:03
Subkeys:
Values:
procexedump
- Description
- Dump a process to an executable file sample
- Options
- -o OFFSET, --offset=OFFSET
- EPROCESS offset (in hex) in the physical address space
- -p PID, --pid=PID
- Operate on these Process IDs (comma-separated)
- -D DUMP_DIR, --dump-dir=DUMP_DIR
- Directory in which to dump executable files
- -u, --unsafe
- Bypasses certain sanity checks when creating image
- Output example
$ python vol.py -f ~/memdump/infected.img procexedump -p 532 --dump-dir=output/ Volatile Systems Volatility Framework 2.2 Process(V) ImageBase Name Result ---------- ---------- -------------------- ------ 0x81f015d0 0x00400000 vmtoolsd.exe OK: executable.532.exe

procmemdump
- Description
- Dump a process to an executable memory sample
- Options
- -o OFFSET, --offset=OFFSET
- EPROCESS offset (in hex) in the physical address space
- -p PID, --pid=PID
- Operate on these Process IDs (comma-separated)
- -D DUMP_DIR, --dump-dir=DUMP_DIR
- Directory in which to dump executable files
- -u, --unsafe
- Bypasses certain sanity checks when creating image
- Output example
$ python vol.py -f ~/memdump/infected.img procmemdump -p 532 --dump-dir=output/ Volatile Systems Volatility Framework 2.2 Process(V) ImageBase Name Result ---------- ---------- -------------------- ------ 0x81f015d0 0x00400000 vmtoolsd.exe OK: executable.532.exe
pslist
- Description
- print all running processes by following the EPROCESS lists
- Options
- -o OFFSET, --offset=OFFSET
- EPROCESS offset (in hex) in the physical address space
- -p PID, --pid=PID
- Operate on these Process IDs (comma-separated)
- -P, --physical-offset
- Physical Offset
- Output example
$ python vol.py -f ~/tmp/infected.img pslist Volatile Systems Volatility Framework 2.1 Offset(V) Name PID PPID Thds Hnds Sess Wow64 Start Exit ---------- -------------------- ------ ------ ------ -------- ------ ------ -------------------- -------------------- 0x823c8830 System 4 0 58 599 ------ 0 0x81e0b4b0 smss.exe 412 4 3 19 ------ 0 2013-02-18 20:54:31 0x82164020 csrss.exe 772 412 12 465 0 0 2013-02-18 20:54:33 0x81eee548 winlogon.exe 796 412 21 459 0 0 2013-02-18 20:54:33 0x81f13958 services.exe 840 796 16 280 0 0 2013-02-18 20:54:33 0x821ecda0 lsass.exe 852 796 22 365 0 0 2013-02-18 20:54:33 0x81e219a0 vmacthlp.exe 1028 840 1 25 0 0 2013-02-18 20:54:33 0x81e57500 svchost.exe 1052 840 17 198 0 0 2013-02-18 20:54:34 0x81eae808 svchost.exe 1120 840 10 245 0 0 2013-02-18 20:54:34 0x82190658 svchost.exe 1364 840 81 1693 0 0 2013-02-18 20:54:34 0x82236020 svchost.exe 1412 840 6 91 0 0 2013-02-18 20:54:34 0x821687e8 svchost.exe 1504 840 13 179 0 0 2013-02-18 20:54:35 0x821e8468 spoolsv.exe 1820 840 13 145 0 0 2013-02-18 20:54:36 0x8217ac10 explorer.exe 272 212 0 -------- 0 0 2013-02-18 20:54:51 2013-02-18 21:08:03 0x81dd7da0 rundll32.exe 496 272 7 81 0 0 2013-02-18 20:54:52 0x81f015d0 vmtoolsd.exe 532 272 38 563 0 0 2013-02-18 20:54:52 0x821a47e8 svchost.exe 1332 840 6 165 0 0 2013-02-18 20:55:00 0x81e693c0 svchost.exe 1428 840 3 78 0 0 2013-02-18 20:55:00 0x8219f500 jqs.exe 1512 840 8 241 0 0 2013-02-18 20:55:00 0x81e0f980 vmtoolsd.exe 1732 840 7 307 0 0 2013-02-18 20:55:00 0x81e55778 wscntfy.exe 128 1364 4 44 0 0 2013-02-18 20:55:18 0x8221cb20 TPAutoConnSvc.e 1880 840 5 99 0 0 2013-02-18 20:55:21 0x81e457f8 TPAutoConnect.e 2420 1880 4 77 0 0 2013-02-18 20:55:25 0x82166928 wmiapsrv.exe 3160 840 3 144 0 0 2013-02-18 20:58:01 0x82241518 wuauclt.exe 4012 1364 6 120 0 0 2013-02-18 21:04:15 0x81ccb020 explorer.exe 600 796 19 481 0 0 2013-02-18 21:08:05 0x81cbdb20 netsh.exe 3860 532 0 -------- 0 0 2013-02-18 21:15:17 2013-02-18 21:15:18 0x81c75020 notepad.exe 3052 532 0 -------- 0 0 2013-02-18 21:15:20 2013-02-18 21:15:20 0x81c20620 chrome.exe 2760 600 0 -------- 0 0 2013-02-18 21:17:07 2013-02-18 21:17:44 0x81cd6630 chrome.exe 3436 2760 0 -------- 0 0 2013-02-18 21:17:08 2013-02-18 21:17:18 0x81c7b308 chrome.exe 4016 2760 0 -------- 0 0 2013-02-18 21:17:08 2013-02-18 21:17:44 0x81c76328 chrome.exe 460 2760 0 -------- 0 0 2013-02-18 21:17:17 2013-02-18 21:17:21 0x81c211c8 chrome.exe 4088 2760 0 -------- 0 0 2013-02-18 21:17:19 2013-02-18 21:17:44 0x81c88480 cmd.exe 2164 600 4 35 0 0 2013-02-18 21:17:42 0x81c6bda0 mdd_1.3.exe 2908 2164 1 28 0 0 2013-02-18 21:20:52
psscan
- Description
- Scan Physical memory for _EPROCESS pool allocations
- Output example
$ python vol.py -f ~/memdump/infected.img psscan Volatile Systems Volatility Framework 2.2 Offset(P) Name PID PPID PDB Time created Time exited ---------- ---------------- ------ ------ ---------- -------------------- -------------------- 0x01e20620 chrome.exe 2760 600 0x0ac80280 2013-02-18 21:17:07 2013-02-18 21:17:44 0x01e211c8 chrome.exe 4088 2760 0x0ac80300 2013-02-18 21:17:19 2013-02-18 21:17:44 0x01e6bda0 mdd_1.3.exe 2908 2164 0x0ac80260 2013-02-18 21:20:52 0x01e75020 notepad.exe 3052 532 0x0ac802c0 2013-02-18 21:15:20 2013-02-18 21:15:20 0x01e76328 chrome.exe 460 2760 0x0ac802a0 2013-02-18 21:17:17 2013-02-18 21:17:21 0x01e7b308 chrome.exe 4016 2760 0x0ac80440 2013-02-18 21:17:08 2013-02-18 21:17:44 0x01e88480 cmd.exe 2164 600 0x0ac802e0 2013-02-18 21:17:42 0x01ebdb20 netsh.exe 3860 532 0x0ac803e0 2013-02-18 21:15:17 2013-02-18 21:15:18 0x01ecb020 explorer.exe 600 796 0x0ac80460 2013-02-18 21:08:05 0x01ed6630 chrome.exe 3436 2760 0x0ac801c0 2013-02-18 21:17:08 2013-02-18 21:17:18 [REMOVED]
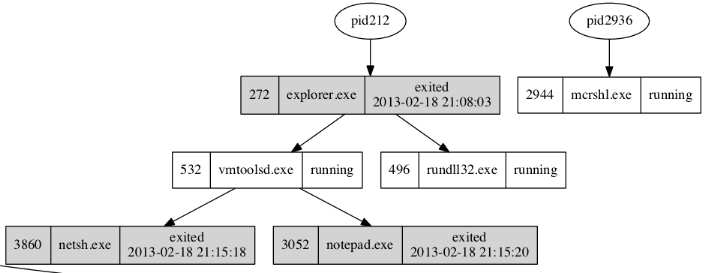
To visualize the processes and dependencies, you can install Graphviz and generate an image as follows:
$ python vol.py -f ~/memdump/infected.img psscan --output=dot --output-file=output/test.dot $ dot -Tpng test.dot -o test.png
Here is an example:
pstree
- Description
- Print process list as a tree
- Output example
$ python vol.py -f ~/tmp/infected.img pstree Volatile Systems Volatility Framework 2.1 Name Pid PPid Thds Hnds Time -------------------------------------------------- ------ ------ ------ ------ -------------------- 0x823c8830:System 4 0 58 599 1970-01-01 00:00:00 . 0x81e0b4b0:smss.exe 412 4 3 19 2013-02-18 20:54:31 .. 0x82164020:csrss.exe 772 412 12 465 2013-02-18 20:54:33 .. 0x81eee548:winlogon.exe 796 412 21 459 2013-02-18 20:54:33 ... 0x81ccb020:explorer.exe 600 796 19 481 2013-02-18 21:08:05 .... 0x81c20620:chrome.exe 2760 600 0 ------ 2013-02-18 21:17:07 ..... 0x81cd6630:chrome.exe 3436 2760 0 ------ 2013-02-18 21:17:08 ..... 0x81c7b308:chrome.exe 4016 2760 0 ------ 2013-02-18 21:17:08 ..... 0x81c76328:chrome.exe 460 2760 0 ------ 2013-02-18 21:17:17 ..... 0x81c211c8:chrome.exe 4088 2760 0 ------ 2013-02-18 21:17:19 .... 0x81c88480:cmd.exe 2164 600 4 35 2013-02-18 21:17:42 ..... 0x81c6bda0:mdd_1.3.exe 2908 2164 1 28 2013-02-18 21:20:52 ... 0x81f13958:services.exe 840 796 16 280 2013-02-18 20:54:33 .... 0x82166928:wmiapsrv.exe 3160 840 3 144 2013-02-18 20:58:01 .... 0x81e693c0:svchost.exe 1428 840 3 78 2013-02-18 20:55:00 .... 0x82236020:svchost.exe 1412 840 6 91 2013-02-18 20:54:34 .... 0x821e8468:spoolsv.exe 1820 840 13 145 2013-02-18 20:54:36 .... 0x81e219a0:vmacthlp.exe 1028 840 1 25 2013-02-18 20:54:33 .... 0x821a47e8:svchost.exe 1332 840 6 165 2013-02-18 20:55:00 .... 0x821687e8:svchost.exe 1504 840 13 179 2013-02-18 20:54:35 .... 0x81e0f980:vmtoolsd.exe 1732 840 7 307 2013-02-18 20:55:00 .... 0x82190658:svchost.exe 1364 840 81 1693 2013-02-18 20:54:34 ..... 0x81e55778:wscntfy.exe 128 1364 4 44 2013-02-18 20:55:18 ..... 0x82241518:wuauclt.exe 4012 1364 6 120 2013-02-18 21:04:15 .... 0x8221cb20:TPAutoConnSvc.e 1880 840 5 99 2013-02-18 20:55:21 ..... 0x81e457f8:TPAutoConnect.e 2420 1880 4 77 2013-02-18 20:55:25 .... 0x81eae808:svchost.exe 1120 840 10 245 2013-02-18 20:54:34 .... 0x8219f500:jqs.exe 1512 840 8 241 2013-02-18 20:55:00 .... 0x81e57500:svchost.exe 1052 840 17 198 2013-02-18 20:54:34 ... 0x821ecda0:lsass.exe 852 796 22 365 2013-02-18 20:54:33 0x8217ac10:explorer.exe 272 212 0 ------ 2013-02-18 20:54:51 . 0x81dd7da0:rundll32.exe 496 272 7 81 2013-02-18 20:54:52 . 0x81f015d0:vmtoolsd.exe 532 272 38 563 2013-02-18 20:54:52 .. 0x81cbdb20:netsh.exe 3860 532 0 ------ 2013-02-18 21:15:17 .. 0x81c75020:notepad.exe 3052 532 0 ------ 2013-02-18 21:15:20
psxview
- Description
- Find hidden processes with various process listings. If you see any that are "False" for pslist, psscan, and thrdproc it's an attempt to hide the process by DKOM (Direct Kernel Object Manipulation).
- Options
- -P, --physical-offset
- Physcal Offset
- Output example
$ python vol.py -f ~/memdump/infected.img psxview Volatile Systems Volatility Framework 2.2 Offset(P) Name PID pslist psscan thrdproc pspcdid csrss ---------- -------------------- ------ ------ ------ -------- ------- ----- 0x0239f500 jqs.exe 1512 True True False True True 0x02057500 svchost.exe 1052 True True False True True 0x01e211c8 chrome.exe 4088 True True False True False 0x020ae808 svchost.exe 1120 True True False True True 0x0237ac10 explorer.exe 272 True True False True False 0x02113958 services.exe 840 True True False True True 0x01ebdb20 netsh.exe 3860 True True False True False [REMOVED] 0x04c67500 svchost.exe 1052 False True False False False 0x16369c10 explorer.exe 272 False True False False False 0x0ce6c658 svchost.exe 1364 False True False False False 0x104ecb20 TPAutoConnSvc.e 1880 False True False False False 0x0f6db4b0 smss.exe 412 False True False False False 0x0867d020 notepad.exe 3052 False True False False False 0x09b60830 System 4 False True False False False [REMOVED]
raw2dmp
- Description
- Converts a physical memory sample to a windbg crash dump
- Options
- -b 5242880, --blocksize=5242880
- Size (in bytes) of blocks to copy
- -O OUTPUT_IMAGE, --output-image=OUTPUT_IMAGE
- Writes a raw DD image out to OUTPUT-IMAGE
- Output example
$ python vol.py -f ~/memdump/infected.img raw2dmp -O infected.dmp Volatile Systems Volatility Framework 2.2 Writing data (5.00 MB chunks): |....................
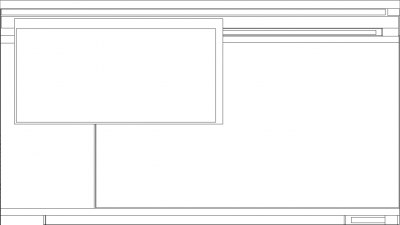
screenshot
- Description
- Save a pseudo-screenshot based on GDI windows
- Requires PIL
PIL first requires lib jpeg:
$ curl -O http://www.ijg.org/files/jpegsrc.v9.tar.gz $ tar xzvf jpegsrc.v9.tar.gz $ cd jpeg-9/ $ ./configure $ make $ sudo make install
Also install freetype:
$ sudo port install freetype
Then install PIL:
$ sudo pip install PIL
- Output example
$ python vol.py -f ~/tmp/infected.img screenshot --dump-dir=output Volatile Systems Volatility Framework 2.2 Wrote output/session_0.Service-0x0-3e5$.Default.png Wrote output/session_0.SAWinSta.SADesktop.png Wrote output/session_0.WinSta0.Default.png Wrote output/session_0.WinSta0.Disconnect.png Wrote output/session_0.WinSta0.Winlogon.png Wrote output/session_0.Service-0x0-3e7$.Default.png Wrote output/session_0.Service-0x0-3e4$.Default.png
Here is how it looks like:
sessions
- Description
- List details on _MM_SESSION_SPACE (user logon sessions)
- Output example
$ python vol.py -f ~/memdump/infected.img sessions Volatile Systems Volatility Framework 2.2 ************************************************** Session(V): f8bdc000 ID: 0 Processes: 26 PagedPoolStart: bb800000 PagedPoolEnd bbbfffff Process: 772 csrss.exe 2013-02-18 20:54:33 Process: 796 winlogon.exe 2013-02-18 20:54:33 Process: 840 services.exe 2013-02-18 20:54:33 Process: 852 lsass.exe 2013-02-18 20:54:33 Process: 1028 vmacthlp.exe 2013-02-18 20:54:33 Process: 1052 svchost.exe 2013-02-18 20:54:34 Process: 1120 svchost.exe 2013-02-18 20:54:34 Process: 1364 svchost.exe 2013-02-18 20:54:34 Process: 1412 svchost.exe 2013-02-18 20:54:34 Process: 1504 svchost.exe 2013-02-18 20:54:35 Process: 1820 spoolsv.exe 2013-02-18 20:54:36 Process: 496 rundll32.exe 2013-02-18 20:54:52 [REMOVED]
shimcache
- Description
- Parses the Application Compatibility Shim Cache registry key
- Output example
$ python vol.py -f ~/memdump/stuxnet.vmem shimcache Volatile Systems Volatility Framework 2.2 Last Modified: 2010-10-08 03:33:07 , Lastupdate: 2010-10-08 03:33:11 , Path: \??\C:\Documents and Settings\Administrator\My Documents\Downloads\setuptools-0.6c11.win32-py2.6.exe Last Modified: 2010-09-27 17:29:06 , Lastupdate: 2010-10-08 03:30:58 , Path: \??\C:\Documents and Settings\Administrator\Desktop\pydasm-1.5.win32-py2.6.exe Last Modified: 2008-04-14 12:00:00 , Lastupdate: 2010-10-29 17:08:31 , Path: \??\C:\WINDOWS\system32\wscntfy.exe Last Modified: 2008-04-14 12:00:00 , Lastupdate: 2010-10-08 04:05:22 , Path: \??\C:\WINDOWS\System32\cscui.dll Last Modified: 2008-04-14 12:00:00 , Lastupdate: 2010-10-08 03:31:48 , Path: \??\C:\WINDOWS\system32\wuaucpl.cpl\setup50.exe Last Modified: 2010-09-27 17:48:34 , Lastupdate: 2010-10-08 03:31:05 , Path: \??\C:\Documents and Settings\Administrator\Desktop\ssdeep-2.0-0.1.win32-py2.6.exe Last Modified: 2008-04-14 12:00:00 , Lastupdate: 2010-10-29 16:49:28 , Path: \??\C:\WINDOWS\system32\verclsid.exe Last Modified: 2008-04-14 12:00:00 , Lastupdate: 2010-10-29 16:49:29 , Path: \??\C:\WINDOWS\system32\SHELL32.dll [REMOVED]
sockets
- Description
- Print list of open sockets
- Options
- -P, --physical-offset
- Physical Offset
- Output example
$ python vol.py -f ~/memdump/infected.img sockets Volatile Systems Volatility Framework 2.2 Offset(V) PID Port Proto Protocol Address Create Time ---------- ------ ------ ------ --------------- --------------- ----------- 0x81ec08b0 4 137 17 UDP 192.168.1.27 2013-02-18 20:54:54 0x82295318 4 0 47 GRE 0.0.0.0 2013-02-18 21:08:01 0x81dff960 532 1291 17 UDP 0.0.0.0 2013-02-18 21:20:38 0x81efb2f0 852 500 17 UDP 0.0.0.0 2013-02-18 20:55:01 0x81c2e008 532 1224 6 TCP 0.0.0.0 2013-02-18 21:18:28 0x81c7bc58 600 1255 6 TCP 0.0.0.0 2013-02-18 21:19:25 0x81e69d08 532 1295 17 UDP 0.0.0.0 2013-02-18 21:20:40 0x81cd9c18 532 1299 17 UDP 0.0.0.0 2013-02-18 21:20:42 [REMOVED]
sockscan
- Description
- Scan Physical memory for _ADDRESS_OBJECT objects (tcp sockets)
- Output example
$ python vol.py -f ~/memdump/infected.img sockscan Volatile Systems Volatility Framework 2.2 Offset(P) PID Port Proto Protocol Address Create Time ---------- ------ ------ ------ --------------- --------------- ----------- 0x01e14d80 2760 1206 6 TCP 0.0.0.0 2013-02-18 21:17:31 0x01e17378 1412 41257 17 UDP 0.0.0.0 2013-02-18 21:18:32 0x01e17e98 2760 1178 6 TCP 0.0.0.0 2013-02-18 21:17:22 0x01e188d8 2760 1128 6 TCP 0.0.0.0 2013-02-18 21:17:19 0x01e1b4b8 2760 1163 6 TCP 0.0.0.0 2013-02-18 21:17:22 [REMOVED] 0x01fc94b0 4 445 17 UDP 0.0.0.0 2013-02-18 20:54:31 0x01fff960 532 1291 17 UDP 0.0.0.0 2013-02-18 21:20:38 0x02018660 1364 123 17 UDP 127.0.0.1 2013-02-18 20:55:12 0x02020e98 4 138 17 UDP 192.168.60.135 2013-02-18 20:54:39 0x02030e98 1504 1900 17 UDP 192.168.1.27 2013-02-18 20:55:25 [REMOVED]
ssdt
- Description
- Display SSDT entries
- Output example
$ python vol.py -f ~/memdump/infected.img ssdt Volatile Systems Volatility Framework 2.2 [x86] Gathering all referenced SSDTs from KTHREADs... Finding appropriate address space for tables... SSDT[0] at 80501bcc with 284 entries Entry 0x0000: 0x80599ade (NtAcceptConnectPort) owned by ntoskrnl.exe Entry 0x0001: 0x805e7784 (NtAccessCheck) owned by ntoskrnl.exe Entry 0x0002: 0x805eafca (NtAccessCheckAndAuditAlarm) owned by ntoskrnl.exe Entry 0x0003: 0x805e77b6 (NtAccessCheckByType) owned by ntoskrnl.exe Entry 0x0004: 0x805eb004 (NtAccessCheckByTypeAndAuditAlarm) owned by ntoskrnl.exe Entry 0x0005: 0x805e77ec (NtAccessCheckByTypeResultList) owned by ntoskrnl.exe Entry 0x0006: 0x805eb048 (NtAccessCheckByTypeResultListAndAuditAlarm) owned by ntoskrnl.exe Entry 0x0007: 0x805eb08c (NtAccessCheckByTypeResultListAndAuditAlarmByHandle) owned by ntoskrnl.exe Entry 0x0008: 0x8060c902 (NtAddAtom) owned by ntoskrnl.exe Entry 0x0009: 0x8060d646 (NtAddBootEntry) owned by ntoskrnl.exe Entry 0x000a: 0x805e2b6a (NtAdjustGroupsToken) owned by ntoskrnl.exe Entry 0x000b: 0x805e27c2 (NtAdjustPrivilegesToken) owned by ntoskrnl.exe Entry 0x000c: 0x805cb024 (NtAlertResumeThread) owned by ntoskrnl.exe [REMOVED]
strings
- Description
- Match physical offsets to virtual addresses (may take a while, VERY verbose)
- Requires
- Requires strings file generated by Sysinternals Strings (http://technet.microsoft.com/en-us/sysinternals/bb897439).
- Options
- -o OFFSET, --offset=OFFSET
- EPROCESS offset (in hex) in the physical address space
- -s STRING_FILE, --string-file=STRING_FILE
- File output in strings format (offset:string)
- -S, --scan
- Use PSScan if no offset is provided
- -p PIDS, --pids=PIDS
- Operate on these Process IDs (comma-separated)
- Output example
First generate a strings file as follows (could be performed from Windows, on a Windows based VM or via Wine):
C:\> strings.exe -q -o infected.img > infected.strings.txt
Then use your file as follows:
$ python vol.py -f ~/memdump/infected.img strings -s ~/memdump/infected.strings.txt -p 532 Volatile Systems Volatility Framework 2.2 000003c1 [kernel:f83ae3c1] (,(@ 00000636 [kernel:f83ae636] 8,t 000006c1 [kernel:f83ae6c1] w#r 000006d8 [kernel:f83ae6d8] sQOtN2 000006fc [kernel:f83ae6fc] t+a`" 00000719 [kernel:f83ae719] aas 0000072c [kernel:f83ae72c] Table de partition n 0000074a [kernel:f83ae74a] Erreur lors du chargement du syst 0000076c [kernel:f83ae76c] me d'exploitati 0000077c [kernel:f83ae77c] Syst 00000781 [kernel:f83ae781] me d'exploitation absent 000007b5 [kernel:f83ae7b5] ,J|'#(# 00001000 [kernel:f83af000] node_in_array != NULL 00001018 [kernel:f83af018] c:\toolchain\src\glib-2.22.4-1\glib-2.22.4\glib\gbsearcharray.h 00001058 [kernel:f83af058] file %s: line %d: assertion `%s' failed 00001080 [kernel:f83af080] Glib-GObject 00001090 [kernel:f83af090] index_ <= barray->n_nodes 000010b0 [kernel:f83af0b0] c:\toolchain\src\glib-2.22.4-1\glib-2.22.4\glib\gbsearcharray.h 000010f0 [kernel:f83af0f0] file %s: line %d: assertion `%s' failed [REMOVED]
svcscan
- Description
- Scan for Windows services
- Output example
$ python vol.py -f ~/memdump/infected.img svcscan Volatile Systems Volatility Framework 2.2 Offset: 0x381e90 Order: 1 Process ID: - Service Name: Abiosdsk Display Name: Abiosdsk Service Type: SERVICE_KERNEL_DRIVER Service State: SERVICE_STOPPED Binary Path: - Offset: 0x381f20 Order: 2 Process ID: - Service Name: abp480n5 Display Name: abp480n5 Service Type: SERVICE_KERNEL_DRIVER Service State: SERVICE_STOPPED Binary Path: - [REMOVED]
symlinkscan
- Description
- Scan for symbolic link objects
- Output example
$ python vol.py -f ~/memdump/infected.img symlinkscan Volatile Systems Volatility Framework 2.2 Offset(P) #Ptr #Hnd Creation time From To ---------- ------ ------ ------------------------ -------------------- ------------------------------------------------------------ 0x02a152a0 1 0 2013-02-18 20:54:16 Scsi1: \Device\Ide\IdePort1 0x02a16148 1 0 2013-02-18 20:54:16 VMCIDev \Device\VMCIHostDev 0x02a16538 1 0 2013-02-18 20:54:14 Global \GLOBAL?? 0x02a16658 1 0 2013-02-18 20:54:14 GLOBALROOT 0x02a1d6c0 1 0 2013-02-18 20:54:14 DosDevices \?? 0x02a1f4b8 1 0 2013-02-18 20:54:31 SystemRoot \Device\Harddisk0\Partition1\WINDOWS 0x02a1fe88 1 0 2013-02-18 20:54:16 Root#dmio...91efb8b} \Device\00000003 0x02a3b138 1 0 2013-02-18 20:54:17 multi(0)d...rdisk(0) \Device\Harddisk0\Partition0 0x02a51bd8 1 0 2013-02-18 20:54:16 DmLoader \Device\DmLoader 0x02a591f0 1 0 2013-02-18 20:54:17 multi(0)d...ition(1) \Device\Harddisk0\Partition1 0x02a5b0a0 1 0 2013-02-18 20:54:15 ACPI#Fixe...9062857} \Device\0000003d 0x02a60860 1 0 2013-02-18 20:54:31 IPNAT \Device\IPNAT [REMOVED]
thrdscan
- Description
- Scan physical memory for _ETHREAD objects
- Output example
$ python vol.py -f ~/memdump/spyeye.vmem thrdscan Volatile Systems Volatility Framework 2.2 Offset(P) PID TID Start Address Create Time Exit Time ---------- ------ ------ ------------- ------------------------- ------------------------- 0x01eadb30 2108 2212 0x7c8106f9 2010-11-11 22:03:54 0x01eadda8 2108 2208 0x7c8106f9 2010-11-11 22:03:54 0x01eae7e0 4 584 0xb18859f0 2010-11-11 22:03:54 0x01eb2da8 1068 2636 0x7c8106f9 2011-01-06 14:36:59 0x01eb7020 1008 1824 0x7c8106f9 2010-11-11 22:03:03 0x01eba2a8 1588 1760 0x7c8106f9 2010-11-11 22:03:01 0x01eba520 1588 1756 0x7c8106f9 2010-11-11 22:03:01 0x01ebdda8 1588 1768 0x7c8106f9 2010-11-11 22:03:02 0x01ec1a78 1232 2280 0x7c8106f9 2011-01-06 14:36:52 0x01ec28b8 1252 1328 0x7c8106f9 2010-11-11 22:03:00 0x01ec2b30 1252 1320 0x7c8106f9 2010-11-11 22:03:00 0x01ec2da8 1252 1256 0x7c810705 2010-11-11 22:02:58 0x01ec4578 1068 1688 0x7c8106f9 2010-11-11 22:03:01 0x01ec4da8 1252 1332 0x7c8106f9 2010-11-11 22:03:00 0x01ec77f0 704 2252 0x7c8106f9 2011-01-06 14:36:52 2011-01-06 14:36:52 [REMOVED]
threads
- Description
- Investigate _ETHREAD and _KTHREADs
- Options
- -o OFFSET, --offset=OFFSET
- EPROCESS offset (in hex) in the physical address space
- -p PID, --pid=PID
- Operate on these Process IDs (comma-separated)
- -F FILTER, --filter=FILTER
- Tags to filter (comma-separated)
- -L, --listtags
- List all available tags
- Output example
$ python vol.py -f ~/memdump/infected.img threads -p 532 Volatile Systems Volatility Framework 2.2 [x86] Gathering all referenced SSDTs from KTHREADs... Finding appropriate address space for tables... ------ ETHREAD: 0x821ea580 Pid: 532 Tid: 3164 Tags: Created: 2013-02-18 20:56:05 Exited: 1970-01-01 00:00:00 Owning Process: vmtoolsd.exe Attached Process: vmtoolsd.exe State: Waiting:WrLpcReceive BasePriority: 0x8 Priority: 0x9 TEB: 0x7ffdb000 StartAddress: 0x7c810729 UNKNOWN Win32StartAddress: 0x00014fe0 ServiceTable: 0x805530e0 [0] 0x80501bcc [1] 0xbf99e580 [2] 0x00000000 [3] 0x00000000 Win32Thread: 0xe1efceb0 CrossThreadFlags: Eip: 0x7c91e514 eax=0x0019ac98 ebx=0x00000000 ecx=0x001a7d48 edx=0x21380004 esi=0x0018d8b0 edi=0x0018d954 eip=0x7c91e514 esp=0x02c2fe18 ebp=0x02c2ff80 err=0x00000000 cs=0x1b ss=0x23 ds=0x23 es=0x23 gs=0x00 efl=0x00000246 dr0=0x00000000 dr1=0x00000000 dr2=0x00000000 dr3=0x00000000 dr6=0x00000000 dr7=0x00000000 [REMOVED]
timers
- Description
- Print kernel timers and associated module DPCs
- Output example
$ python vol.py -f ~/memdump/infected.img timers Volatile Systems Volatility Framework 2.2 Offset(V) DueTime Period(ms) Signaled Routine Module ---------- ------------------------ ---------- ---------- ---------- ------ 0x81c8d268 0x80000003:0x5e3cd682 0 - 0x80534f48 ntoskrnl.exe 0x8055b380 0x00000008:0x61d9dd2a 0 - 0x80534b2a ntoskrnl.exe 0x8216a978 0x00000003:0xbe8bb404 0 - 0xb253a85a afd.sys 0x81e15f08 0x00000003:0xb9da12d4 0 - 0xb253a85a afd.sys 0x80551850 0x00000003:0xc5c5d4d4 60000 Yes 0x804f3edc ntoskrnl.exe 0x821c7c20 0x00000003:0xc10847e2 0 - 0xb253a85a afd.sys 0xb25dd1c0 0x00000003:0xcf7a2728 60000 Yes 0xb25cd471 ipsec.sys 0xb25dcd08 0x00000003:0xcf7a2728 0 - 0xb25cd3e7 ipsec.sys 0xb25dcd70 0x00000008:0x6ba60702 0 - 0xb25cd3e7 ipsec.sys 0xb2435d60 0x00000003:0xcf83b090 60000 Yes 0xb242d266 ipnat.sys [REMOVED]
userassist
- Description
- Print userassist registry keys and information.
- Output example
$ python vol.py -f ~/memdump/infected.img userassist Volatile Systems Volatility Framework 2.2 ---------------------------- Registry: \Device\HarddiskVolume1\Documents and Settings\pilou\NTUSER.DAT Key name: Count Last updated: 2013-02-18 21:17:42 Subkeys: Values: REG_BINARY UEME_CTLSESSION : 0x00000000 e2 b7 6f 0e 28 00 00 00 ..o.(... REG_BINARY UEME_CTLCUACount:ctor : ID: 1 Count: 2 Last updated: 1970-01-01 00:00:00 0x00000000 01 00 00 00 02 00 00 00 00 00 00 00 00 00 00 00 ................ REG_BINARY UEME_RUNPATH : ID: 40 Count: 249 Last updated: 2013-02-18 21:17:42 0x00000000 28 00 00 00 fe 00 00 00 d0 cc 4a 63 1d 0e ce 01 (.........Jc.... REG_BINARY UEME_RUNPATH:C:\WINDOWS\system32\cmd.exe : ID: 40 Count: 51 Last updated: 2013-02-18 21:17:42 0x00000000 28 00 00 00 38 00 00 00 d0 cc 4a 63 1d 0e ce 01 (...8.....Jc.... REG_BINARY UEME_RUNPATH:C:\Program Files\Internet Explorer\iexplore.exe : ID: 36 Count: 22 Last updated: 2012-12-22 14:22:12 0x00000000 24 00 00 00 1b 00 00 00 00 ea 18 bc 4f e0 cd 01 $...........O... [REMOVED]
userhandles
- Description
- Dump the USER handle tables
- Options
- -p PID, --pid=PID
- Pid filter
- -t TYPE, --type=TYPE
- Handle type
- -F, --free
- Include free handles
- Output example
$ python vol.py -f ~/memdump/infected.img userhandles -p 532 Volatile Systems Volatility Framework 2.2 ************************************************** SharedInfo: 0xbf9af820, SessionId: 0 Shared delta: 0 aheList: 0xbbd10000, Table size: 0x2000, Entry size: 0xc Object(V) Handle bType Flags Thread Process ---------- ---------- -------------------- -------- -------- ------- 0xbbe6dc40 0x2d003f TYPE_INPUTCONTEXT 0 3340 532 0xbbe3e7a0 0x200a0 TYPE_HOOK 0 536 532 0xbbe55cb8 0x20d00a1 TYPE_INPUTCONTEXT 0 2680 532 0xbbe3b190 0x200a6 TYPE_WINDOW 0 536 532 0xbbe3afd8 0x200a8 TYPE_WINDOW 0 536 532 0xbbe3af10 0x200aa TYPE_WINDOW 0 536 532 0xbbe3ad80 0x200ac TYPE_WINDOW 0 536 532 0xbbe3ac00 0x200ae TYPE_WINDOW 0 536 532 0xbbe3aae8 0x200b0 TYPE_WINDOW 0 536 532 0xbbe5bad8 0x200b2 TYPE_WINDOW 0 536 532 0xbbe3b270 0x200b6 TYPE_WINDOW 0 536 532 0xbbe46d78 0x300cb TYPE_INPUTCONTEXT 0 536 532 0xbbe3e830 0x20102 TYPE_WINDOW 0 536 532 0xbbe3d668 0xc0108 TYPE_WINDOW 0 536 532 [REMOVED]
vaddump
- Description
- Dumps out the vad sections to a file
- Options
- -o OFFSET, --offset=OFFSET
- EPROCESS offset (in hex) in the physical address space
- -p PID, --pid=PID
- Operate on these Process IDs (comma-separated)
- -D DUMP_DIR, --dump-dir=DUMP_DIR
- Directory in which to dump the VAD files
- Output example
$ python vol.py -f ~/memdump/infected.img vaddump -p 532 -D output/
Volatile Systems Volatility Framework 2.2
Pid Process Start End Result
---------- -------------------- ---------- ---------- ------
532 vmtoolsd.exe 0x05270000 0x0536ffff output/vmtoolsd.exe.21015d0.0x05270000-0x0536ffff.dmp
532 vmtoolsd.exe 0x03140000 0x04172fff output/vmtoolsd.exe.21015d0.0x03140000-0x04172fff.dmp
532 vmtoolsd.exe 0x022e0000 0x022e0fff output/vmtoolsd.exe.21015d0.0x022e0000-0x022e0fff.dmp
532 vmtoolsd.exe 0x02090000 0x02090fff output/vmtoolsd.exe.21015d0.0x02090000-0x02090fff.dmp
532 vmtoolsd.exe 0x01f50000 0x0204ffff output/vmtoolsd.exe.21015d0.0x01f50000-0x0204ffff.dmp
532 vmtoolsd.exe 0x01ef0000 0x01efdfff output/vmtoolsd.exe.21015d0.0x01ef0000-0x01efdfff.dmp
532 vmtoolsd.exe 0x01470000 0x01d9afff output/vmtoolsd.exe.21015d0.0x01470000-0x01d9afff.dmp
[REMOVED]
vadinfo
- Description
- Dump the VAD info
- Options
- -o OFFSET, --offset=OFFSET
- EPROCESS offset (in hex) in the physical address space
- -p PID, --pid=PID
- Operate on these Process IDs (comma-separated)
- Output example
$ python vol.py -f ~/memdump/infected.img vadinfo -p 532 Volatile Systems Volatility Framework 2.2 ************************************************************************ Pid: 532 VAD node @ 0x81cd22b0 Start 0x05270000 End 0x0536ffff Tag VadS Flags: CommitCharge: 2, PrivateMemory: 1, Protection: 4 Protection: PAGE_READWRITE VAD node @ 0x81e06320 Start 0x03140000 End 0x04172fff Tag VadS Flags: CommitCharge: 4147, MemCommit: 1, PrivateMemory: 1, Protection: 6 Protection: PAGE_EXECUTE_READWRITE VAD node @ 0x81ecdaa8 Start 0x022e0000 End 0x022e0fff Tag Vadl Flags: CommitCharge: 1, MemCommit: 1, NoChange: 1, PrivateMemory: 1, Protection: 4 Protection: PAGE_READWRITE First prototype PTE: 00000000 Last contiguous PTE: 00000000 Flags2: LongVad: 1, OneSecured: 1 VAD node @ 0x81ec33d8 Start 0x02090000 End 0x02090fff Tag VadS Flags: CommitCharge: 1, PrivateMemory: 1, Protection: 4 Protection: PAGE_READWRITE [REMOVED]
vadtree
- Description
- Walk the VAD tree and display in tree format
- Options
- -o OFFSET, --offset=OFFSET
- EPROCESS offset (in hex) in the physical address space
- -p PID, --pid=PID
- Operate on these Process IDs (comma-separated)
- Output example
$ python vol.py -f ~/memdump/infected.img vadtree -p 532
Volatile Systems Volatility Framework 2.2
************************************************************************
Pid: 532
0x05270000 - 0x0536ffff
0x03140000 - 0x04172fff
0x022e0000 - 0x022e0fff
0x02090000 - 0x02090fff
0x01f50000 - 0x0204ffff
0x01ef0000 - 0x01efdfff
0x01470000 - 0x01d9afff
0x00f40000 - 0x00f40fff
0x00e10000 - 0x00e4ffff
0x00900000 - 0x00bfffff
0x00400000 - 0x00410fff
0x00030000 - 0x0012ffff
0x00010000 - 0x00010fff
0x00020000 - 0x00020fff
0x00140000 - 0x00140fff
0x00130000 - 0x00132fff
0x00250000 - 0x0025ffff
[REMOVED]
vadwalk
- Description
- Walk the VAD tree
- Options
- -o OFFSET, --offset=OFFSET
- EPROCESS offset (in hex) in the physical address space
- -p PID, --pid=PID
- Operate on these Process IDs (comma-separated)
$ python vol.py -f ~/memdump/infected.img vadwalk -p 532 Volatile Systems Volatility Framework 2.2 ************************************************************************ Pid: 532 Address Parent Left Right Start End Tag ---------- ---------- ---------- ---------- ---------- ---------- ---- 0x81cd22b0 0x00000000 0x81e06320 0x81f01d90 0x05270000 0x0536ffff VadS 0x81e06320 0x81cd22b0 0x81ecdaa8 0x8227c3e8 0x03140000 0x04172fff VadS 0x81ecdaa8 0x81e06320 0x81ec33d8 0x81f43938 0x022e0000 0x022e0fff Vadl 0x81ec33d8 0x81ecdaa8 0x81e05040 0x822008f8 0x02090000 0x02090fff VadS 0x81e05040 0x81ec33d8 0x823195b0 0x81e53b70 0x01f50000 0x0204ffff VadS 0x823195b0 0x81e05040 0x82171b18 0x8220b768 0x01ef0000 0x01efdfff Vad 0x82171b18 0x823195b0 0x821d2a78 0x82229ea8 0x01470000 0x01d9afff Vad 0x821d2a78 0x82171b18 0x8215b788 0x81e5ec00 0x00f40000 0x00f40fff Vad 0x8215b788 0x821d2a78 0x81f06870 0x822e1ed8 0x00e10000 0x00e4ffff Vad [REMOVED]
volshell
- Description
- Interactive shell to explore a memory image, offering an interface similar to WinDbg:
- List processes
- Switch into a process's context
- Display types of structures/objects
- Overlay a type over a given address
- Walk linked lists
- Disassemble code at a given address
- Options
- -o OFFSET, --offset=OFFSET
- EPROCESS Offset (in hex) in kernel address space
- -n IMNAME, --imname=IMNAME
- Operate on these Process IDs (comma-separated)
- -p PID, --pid=PID
- Operate on these Process IDs (comma-separated)
- Output example
$ python vol.py -f ~/memdump/infected.img volshell Volatile Systems Volatility Framework 2.2 Current context: process System, pid=4, ppid=0 DTB=0x31e000 Welcome to volshell! Current memory image is: file:///Users/sebastiendamaye/memdump/infected.img To get help, type 'hh()' >>> hh() ps() : Print a process listing. dq(address, length=128, space=None) : Print qwords at address. cc(offset=None, pid=None, name=None) : Change current shell context. dd(address, length=128, space=None) : Print dwords at address. list_entry(head, objname, offset=-1, fieldname=None, forward=True) : Traverse a _LIST_ENTRY. db(address, length=128, space=None) : Print bytes as canonical hexdump. dt(objct, address=None, address_space=None) : Describe an object or show type info. hh(cmd=None) : Get help on a command. dis(address, length=128, space=None, mode=None) : Disassemble code at a given address. For help on a specific command, type 'hh(<command>)' >>> ps() Name PID PPID Offset System 4 0 0x823c8830 smss.exe 412 4 0x81e0b4b0 csrss.exe 772 412 0x82164020 winlogon.exe 796 412 0x81eee548 services.exe 840 796 0x81f13958 lsass.exe 852 796 0x821ecda0 vmacthlp.exe 1028 840 0x81e219a0 svchost.exe 1052 840 0x81e57500 svchost.exe 1120 840 0x81eae808 svchost.exe 1364 840 0x82190658 svchost.exe 1412 840 0x82236020 [REMOVED]
windows
- Description
- Print Desktop Windows (verbose details)
- Output example
$ python vol.py -f ~/memdump/infected.img windows Volatile Systems Volatility Framework 2.2 ************************************************** Window context: 0\SAWinSta\SADesktop Window Handle: #10020 at 0xbc130818, Name: ClassAtom: 0xc035, Class: msctls_progress32 SuperClassAtom: 0xc035, SuperClass: msctls_progress32 pti: 0xe16ef510, Tid: 860 at 0x821e66e8 ppi: 0xe199b008, Process: csrss.exe, Pid: 772 Visible: No Left: 0, Top: 0, Bottom: 100, Right: 100 Style Flags: WS_CLIPCHILDREN,WS_OVERLAPPED,WS_POPUP,WS_CLIPSIBLINGS ExStyle Flags: WS_EX_LTRREADING,WS_EX_RIGHTSCROLLBAR,WS_EX_LEFT Window procedure: 0xbf80d28d Window Handle: #10022 at 0xbc130940, Name: ClassAtom: 0x8000, Class: - SuperClassAtom: 0x8000, SuperClass: - pti: 0xe16ef510, Tid: 860 at 0x821e66e8 ppi: 0xe199b008, Process: csrss.exe, Pid: 772 Visible: No Left: 3, Top: 3, Bottom: 97, Right: 97 Style Flags: WS_BORDER,WS_OVERLAPPED,WS_POPUP,WS_CLIPSIBLINGS ExStyle Flags: WS_EX_LTRREADING,WS_EX_TOOLWINDOW,WS_EX_RIGHTSCROLLBAR,WS_EX_DLGMODALFRAME,WS_EX_WINDOWEDGE,WS_EX_LEFT Window procedure: 0xbf860ffc [REMOVED]
wintree
- Description
- Print Z-Order Desktop Windows Tree
- Output example
$ python vol.py -f ~/memdump/infected.img wintree Volatile Systems Volatility Framework 2.2 ************************************************** Window context: 0\SAWinSta\SADesktop #10020 csrss.exe:772 msctls_progress32 .#10022 csrss.exe:772 - .OleMainThreadWndName svchost.exe:1364 msctls_hotkey32 #1001e csrss.exe:772 - .#6016c svchost.exe:1364 Tapi32WndClass .SYSTEM AGENT COM WINDOW svchost.exe:1364 SAGEWINDOWCLASS .internal window svchost.exe:1364 Bits .BadApplicationNotificationWindow svchost.exe:1364 BadApplicationNotificationWindowClass .ModemDeviceChange svchost.exe:1364 MdmDevChg .#401d6 svchost.exe:1364 HidPhoneNotifClass #1002c csrss.exe:772 msctls_progress32 .#1002e csrss.exe:772 - #2002a csrss.exe:772 - #10032 csrss.exe:772 msctls_progress32 .#10034 csrss.exe:772 - #20030 csrss.exe:772 - .#100fc svchost.exe:1428 BthServClass #1006c csrss.exe:772 msctls_progress32 .#1006e csrss.exe:772 - #5006a csrss.exe:772 - [REMOVED]
wndscan
- Description
- Pool scanner for tag WINDOWSTATION (window stations)
- Output example
$ python vol.py -f ~/memdump/infected.img wndscan Volatile Systems Volatility Framework 2.2 ************************************************** WindowStation: 0x205c318, Name: Service-0x0-3e5$, Next: 0x81f03ce8 SessionId: 0, AtomTable: 0xe19b3c18, Interactive: False Desktops: Default ptiDrawingClipboard: pid - tid - spwndClipOpen: 0x0, spwndClipViewer: 0x0 cNumClipFormats: 0, iClipSerialNumber: 0 pClipBase: 0x0, Formats: ************************************************** WindowStation: 0x2103ce8, Name: SAWinSta, Next: 0x0 SessionId: 0, AtomTable: 0xe1ee5278, Interactive: False Desktops: SADesktop ptiDrawingClipboard: pid - tid - spwndClipOpen: 0x0, spwndClipViewer: 0x0 cNumClipFormats: 0, iClipSerialNumber: 0 pClipBase: 0x0, Formats: [REMOVED]
yarascan
- Description
- Scan process or kernel memory with Yara signatures
- Requires
- Yara (http://code.google.com/p/yara-project/)
- Options
- -o OFFSET, --offset=OFFSET
- EPROCESS offset (in hex) in the physical address space
- -p PID, --pid=PID
- Operate on these Process IDs (comma-separated)
- -K, --kernel
- Scan kernel modules
- -W, --wide
- Match wide (unicode) strings
- -Y YARA_RULES, --yara-rules=YARA_RULES
- Yara rules (as a string)
- -y YARA_FILE, --yara-file=YARA_FILE
- Yara rules (rules file)
- -D DUMP_DIR, --dump-dir=DUMP_DIR
- Directory in which to dump the files
- Output example
Let's create a yara signature as follows:
$ cat ~/pentest/yara-sigs/sality.yara
rule sality
{
strings:
$a = "mirc1.net"
$b = "elaswany.com"
$c = "logos.gif"
condition:
any of them
}
Let's identify process matching the yard signature;
$ python vol.py -f ~/memdump/infected.img yarascan -y ~/pentest/yara-sigs/sality.yara Volatile Systems Volatility Framework 2.2 Rule: sality Owner: Process vmtoolsd.exe Pid 532 0x0315919d 6d 69 72 63 31 2e 6e 65 74 2f 6c 6f 67 6f 73 2e mirc1.net/logos. 0x031591ad 67 69 66 00 68 74 74 70 3a 2f 2f 77 77 77 2e 64 gif.http://www.d 0x031591bd 6f 67 75 73 2d 70 6c 61 73 74 69 6b 2e 63 6f 6d ogus-plastik.com 0x031591cd 2f 6c 6f 67 6f 73 2e 67 69 66 00 68 74 74 70 3a /logos.gif.http: Rule: sality Owner: Process vmtoolsd.exe Pid 532 0x031591a7 6c 6f 67 6f 73 2e 67 69 66 00 68 74 74 70 3a 2f logos.gif.http:/ 0x031591b7 2f 77 77 77 2e 64 6f 67 75 73 2d 70 6c 61 73 74 /www.dogus-plast 0x031591c7 69 6b 2e 63 6f 6d 2f 6c 6f 67 6f 73 2e 67 69 66 ik.com/logos.gif 0x031591d7 00 68 74 74 70 3a 2f 2f 6d 61 63 65 64 6f 6e 69 .http://macedoni Rule: sality Owner: Process vmtoolsd.exe Pid 532 0x031591ce 6c 6f 67 6f 73 2e 67 69 66 00 68 74 74 70 3a 2f logos.gif.http:/ 0x031591de 2f 6d 61 63 65 64 6f 6e 69 61 2e 6d 79 31 2e 72 /macedonia.my1.r 0x031591ee 75 2f 6d 61 69 6e 68 2e 67 69 66 00 68 74 74 70 u/mainh.gif.http 0x031591fe 3a 2f 2f 67 69 7a 61 65 64 75 2e 6f 72 67 2f 6d ://gizaedu.org/m [REMOVED]
Examples
- From AlienVault SIEM alarms to the identification of infected files on a compromised machine.
- Retrieve the hostname from a memory dump
- Retrieve the user password from a memory dump