X86-assembly/Instructions/sldt
Jump to navigation
Jump to search
| You are here: | sldt
|
Description
- The sgdt and sldt instruction technique for VMware detection is commonly known as No Pill.
- On VMware, the LDT location on the host will be non zero.
┌──────────┬──────────┬──────────┬──────────┐
┌─ │ 0xDD │ 0xCC │ 0xBB │ 0xAA │ (hex)
│ │ 11011101 │ 11001100 │ 10111011 │ 10101010 │ (bin)
SLDT ├──────────┼──────────┼──────────┼──────────┤
│ │ 0xDD │ 0xCC │ 0x00 │ 0x00 │ (hex)
└► │ 11011101 │ 11001100 │ 00000000 │ 00000000 │ (bin)
└──────────┴──────────┴──────────┴──────────┘
¦ low-order bytes ¦
¦ = 0 on native host ¦
¦ != 0 on VMware ¦
SLDT test
C source// ...SNIP...
unsigned long
get_ldtr_base (void)
{
unsigned char ldtr[5] = "\xef\xbe\xad\xde";
unsigned long ldt = 0;
_asm sldt ldtr
ldt = *((unsigned long *)&ldtr[0]);
return (ldt);
}
// ...SNIP...
void
test2 (void)
{
unsigned int ldt_base = 0;
ldt_base = get_ldtr_base ();
printf ("\n[+] Test 2: LDT\n");
printf ("LDT base: 0x%x\n", ldt_base);
if (ldt_base == 0xdead0000) {
printf ("Result : Native OS\n\n");
return;
}
else {
printf ("Result : VMware detected\n\n");
return;
}
}
|
Assembly.text:00401040 get_ldtr_base proc near
.text:00401040
.text:00401040 var_10 = dword ptr -10h
.text:00401040 var_C = byte ptr -0Ch
.text:00401040 var_8 = dword ptr -8
.text:00401040 var_4 = dword ptr -4
.text:00401040
.text:00401040 push ebp
.text:00401041 mov ebp, esp
.text:00401043 sub esp, 10h
.text:00401046 mov eax, ___security_cookie
.text:0040104B xor eax, ebp
.text:0040104D mov [ebp+var_8], eax
.text:00401050 mov eax, dword_40C000
.text:00401055 mov [ebp+var_10], eax
.text:00401058 mov cl, byte_40C004
.text:0040105E mov [ebp+var_C], cl
.text:00401061 mov [ebp+var_4], 0
.text:00401068 sldt word ptr [ebp+var_10]
.text:0040106C mov edx, [ebp+var_10]
.text:0040106F mov [ebp+var_4], edx
.text:00401072 mov eax, [ebp+var_4]
.text:00401075 mov ecx, [ebp+var_8]
.text:00401078 xor ecx, ebp
.text:0040107A call @__security_check_cookie@4 ; __security_check_cookie(x)
.text:0040107F mov esp, ebp
.text:00401081 pop ebp
.text:00401082 retn
.text:00401082 get_ldtr_base endp
[SNIP]
.text:00401140 sldt_test proc near
.text:00401140
.text:00401140 var_4 = dword ptr -4
.text:00401140
.text:00401140 push ebp
.text:00401141 mov ebp, esp
.text:00401143 push ecx
.text:00401144 mov [ebp+var_4], 0
.text:0040114B call get_ldtr_base
.text:00401150 mov [ebp+var_4], eax
.text:00401153 push offset aTest2Ldt ; "\n[+] Test 2: LDT\n"
.text:00401158 call _printf
.text:0040115D add esp, 4
.text:00401160 mov eax, [ebp+var_4]
.text:00401163 push eax
.text:00401164 push offset aLdtBase0xX ; "LDT base: 0x%x\n"
.text:00401169 call _printf
.text:0040116E add esp, 8
.text:00401171 cmp [ebp+var_4], 0DEAD0000h
.text:00401178 jnz short loc_40118B
.text:0040117A push offset aResultNative_0 ; "Result : Native OS\n\n"
.text:0040117F call _printf
.text:00401184 add esp, 4
.text:00401187 jmp short loc_401198
.text:00401189 ; ---------------------------------------------------------------------------
.text:00401189 jmp short loc_401198
.text:0040118B ; ---------------------------------------------------------------------------
.text:0040118B
.text:0040118B loc_40118B:
.text:0040118B push offset aResultVmware_0 ; "Result : VMware detected\n\n"
.text:00401190 call _printf
.text:00401195 add esp, 4
.text:00401198
.text:00401198 loc_401198:
.text:00401198 mov esp, ebp
.text:0040119A pop ebp
.text:0040119B retn
.text:0040119B sldt_test endp
|
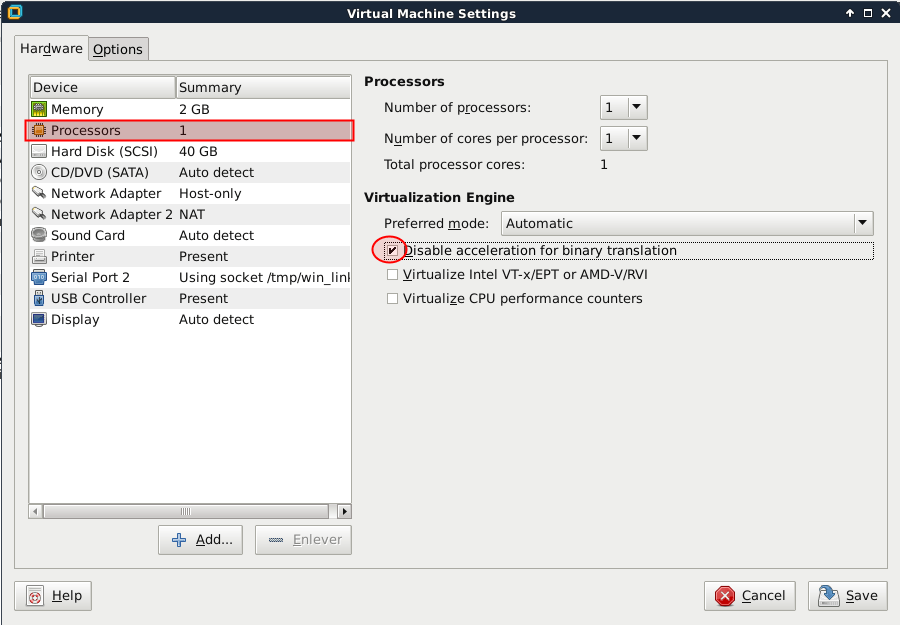
Thwart the No Pill technique
The sldt method can be subverted in VMware by disabling acceleration. To do that, change the following setting:
Comments
Keywords: sldt no-pill