7a4d1babde751f080cc65a306a0ae79c
Jump to navigation
Jump to search
Description
Summary

INCOMPLETE SECTION OR ARTICLE
This section/article is being written and is therefore not complete.
Thank you for your comprehension.
Thank you for your comprehension.
Identification
| MD5 | 7a4d1babde751f080cc65a306a0ae79c |
|---|---|
| SHA1 | dafe57b9c86466f687b91e153bdec7838fb70d35 |
| SHA256 | 398f7503ccdc6b761db1e787f41c81b91cec46f59dc9f334390905b413d42644 |
| ssdeep | 384:PQ2r/xXRVlON9pZbUJvanjBf9cY8jbubGer/yQqZ1xcQblSXFWDIWN:PQ2VBVEN/ZbUdAjNfjDijz0IDj |
| imphash | f433e7fcc51e68080022754836705744 |
| File size | 21.4 KB ( 21873 bytes ) |
| File type | Win32 EXE |
| Magic literal | PE32 executable for MS Windows (GUI) Intel 80386 32-bit |
Antivirus detection
| Antivirus | Result | Update |
|---|---|---|
| AVG | BackDoor.RBot.KB | 20140228 |
| Ad-Aware | Win32.Worm.AutoRun.KZ | 20140228 |
| Agnitum | Worm.Hamweg.A | 20140228 |
| AhnLab-V3 | Trojan/Win32.Pakes | 20140228 |
| AntiVir | TR/Autorun.21873 | 20140228 |
| Avast | Win32:AutoRun-AFC [Wrm] | 20140228 |
| Baidu-International | Trojan.Win32.Pakes.aZAx | 20140228 |
| BitDefender | Win32.Worm.AutoRun.KZ | 20140228 |
| Bkav | W32.PeerBotO.Worm | 20140227 |
| ByteHero | Trojan.Win32.Heur.087 | 20140228 |
| CAT-QuickHeal | Worm.AutoRun.dmh.n4 | 20140228 |
| CMC | Generic.Win32.7a4d1babde!MD | 20140220 |
| Commtouch | W32/Backdoor.X.gen!Eldorado | 20140228 |
| DrWeb | Trojan.Packed.162 | 20140228 |
| ESET-NOD32 | Win32/Inject.NAX | 20140228 |
| Emsisoft | Win32.Worm.AutoRun.KZ (B) | 20140228 |
| F-Prot | W32/Onlinegames.BID | 20140228 |
| F-Secure | Win32.Worm.AutoRun.KZ | 20140228 |
| Fortinet | W32/AutoRun.DMH!worm | 20140228 |
| GData | Win32.Worm.AutoRun.KZ | 20140228 |
| Ikarus | Trojan.Win32.Pakes | 20140228 |
| Jiangmin | Worm/AutoRun.ahu | 20140228 |
| K7AntiVirus | EmailWorm ( 0003b4f91 ) | 20140227 |
| K7GW | P2PWorm ( 000116c21 ) | 20140227 |
| Kaspersky | Trojan.Win32.Pakes.jzm | 20140228 |
| McAfee | W32/Autorun.worm.g | 20140228 |
| McAfee-GW-Edition | Heuristic.LooksLike.Win32.Suspicious.C | 20140228 |
| MicroWorld-eScan | Win32.Worm.AutoRun.KZ | 20140228 |
| Microsoft | Worm:Win32/Hamweq.C | 20140228 |
| NANO-Antivirus | Trojan.Win32.Pakes.bdatt | 20140228 |
| Norman | Malware | 20140228 |
| Panda | W32/Autorun.UT.worm | 20140228 |
| Qihoo-360 | Win32/Trojan.2fe | 20140228 |
| Rising | PE:Trojan.Win32.Undef.gjn!1075134976 | 20140227 |
| Sophos | W32/AutoRun-BIA | 20140228 |
| Symantec | W32.IRCBot | 20140228 |
| TheHacker | W32/AutoRun.dmh | 20140226 |
| TotalDefense | Win32/Hamweq.C | 20140227 |
| TrendMicro | WORM_SCRYPT.J | 20140228 |
| TrendMicro-HouseCall | WORM_SCRYPT.J | 20140228 |
| VBA32 | Trojan-PSW.Win32.Gomex.Gen | 20140227 |
| VIPRE | Win32.Autorun.gen (v) | 20140228 |
| nProtect | Trojan/W32.Agent.21873 | 20140227 |
| Antiy-AVL | 20140228 | |
| ClamAV | 20140227 | |
| Comodo | 20140228 | |
| Kingsoft | 20130829 | |
| Malwarebytes | 20140228 | |
| SUPERAntiSpyware | 20140228 | |
| ViRobot | 20140228 |
Defensive mechanisms
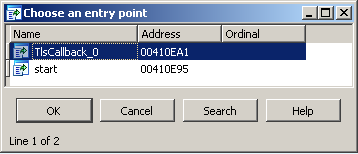
TLS callback
TLS callback is used in this malware. To bypass this defense, we locate it with IDA-Pro:
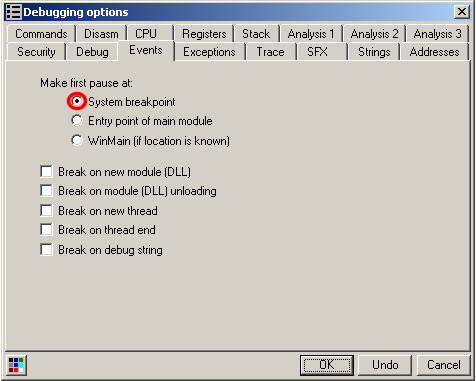
In OllyDbg, we choose to pause at the system breakpoint instead of the default WinMain:
And we go to the TLS callback location: press Ctrl+G and enter "410ea1"
Artifacts

INCOMPLETE SECTION OR ARTICLE
This section/article is being written and is therefore not complete.
Thank you for your comprehension.
Thank you for your comprehension.
Static analysis

INCOMPLETE SECTION OR ARTICLE
This section/article is being written and is therefore not complete.
Thank you for your comprehension.
Thank you for your comprehension.