Category:Digital-Forensics/Computer-Forensics/Anti-Reverse-Engineering/Packers/PECompact
| You are here: | PECompact
|
Description

Thank you for your comprehension.
Manually unpacking PECompact 2
First of all, let's get rid of all exceptions errors in OllyDbg:
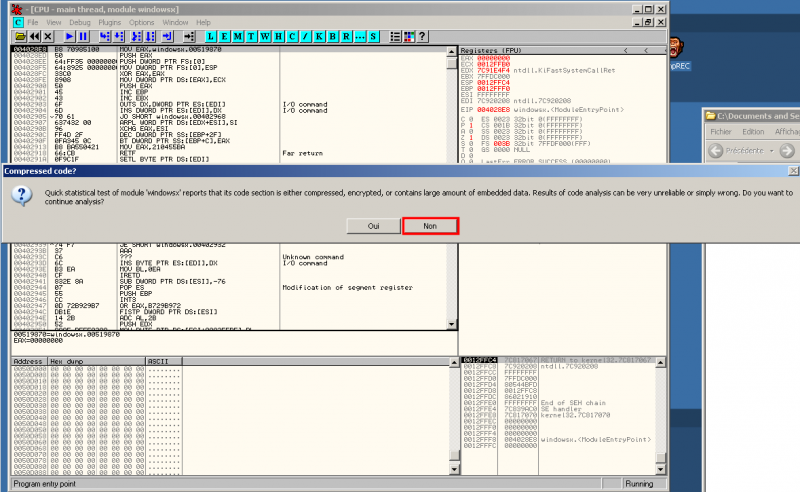
If you open a PE Compact 2 packed malware into OllyDbg, you will get a similar message. Clik "No"
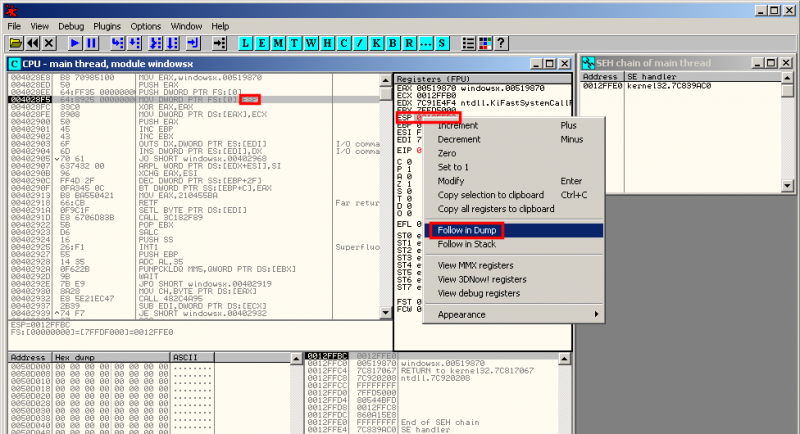
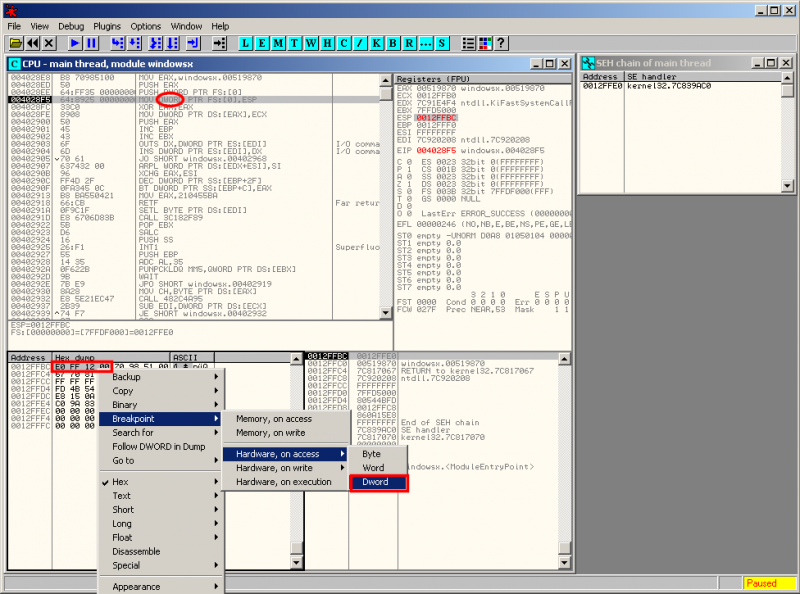
On the below screenshot, we notice that the instruction at address 0x004028F5 triggers a new SEH exception:
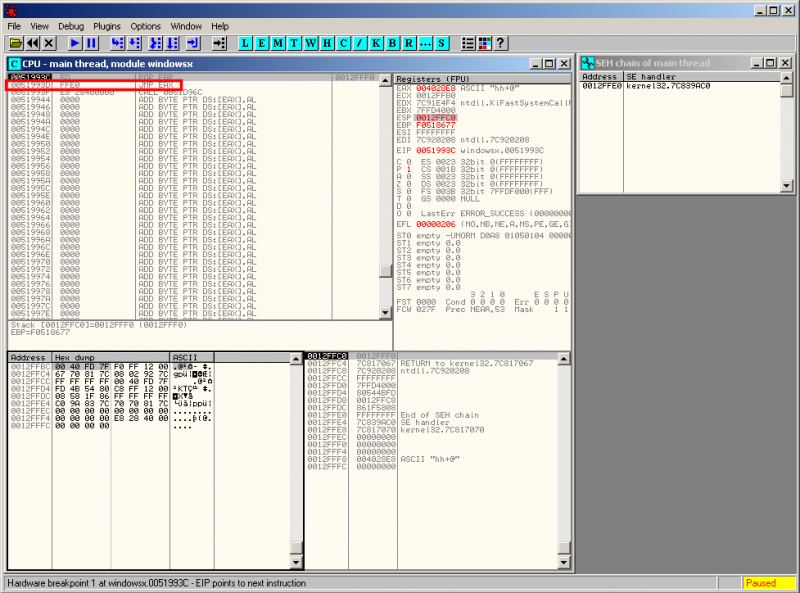
3 times "run" (F9) and we are close to the end: notice the "jump" to EAX at 0x0051993D:
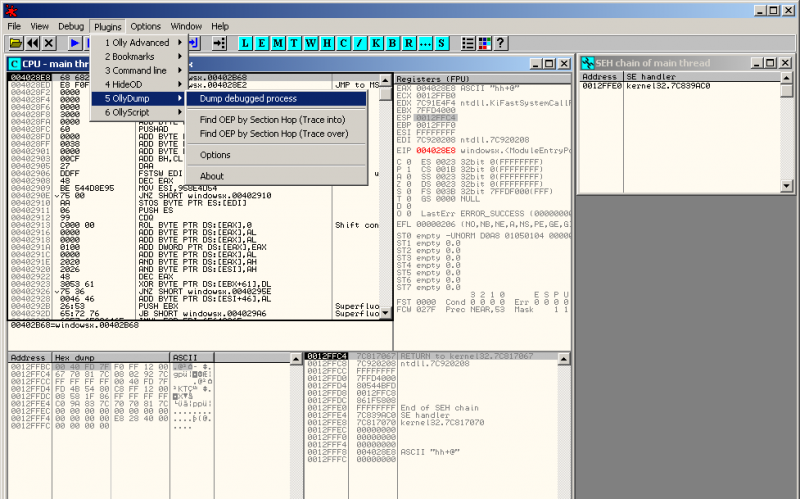
Now step over (F8) and step into (F7) and you're done. Dump the process with OllyDump:
Manually unpacking PECompact 1.68 - 1.84
Given a malware that is packed with "PECompact 1.68 - 1.84 -> Jeremy Collake". When we load the program into OllyDbg, we see that it starts at 0x405130:
As depicted below, there are pushfd / pushad instructions that will save all the registers and flags. These registers and flags are likely to be restored (with popfd / popad) before the immediately before the tail jump.
00405130 EB 06 JMP SHORT Lab18-03.00405138
00405132 68 77150000 PUSH 1577
00405137 C3 RETN
00405138 9C PUSHFD
00405139 60 PUSHAD
0040513A E8 02000000 CALL Lab18-03.00405141
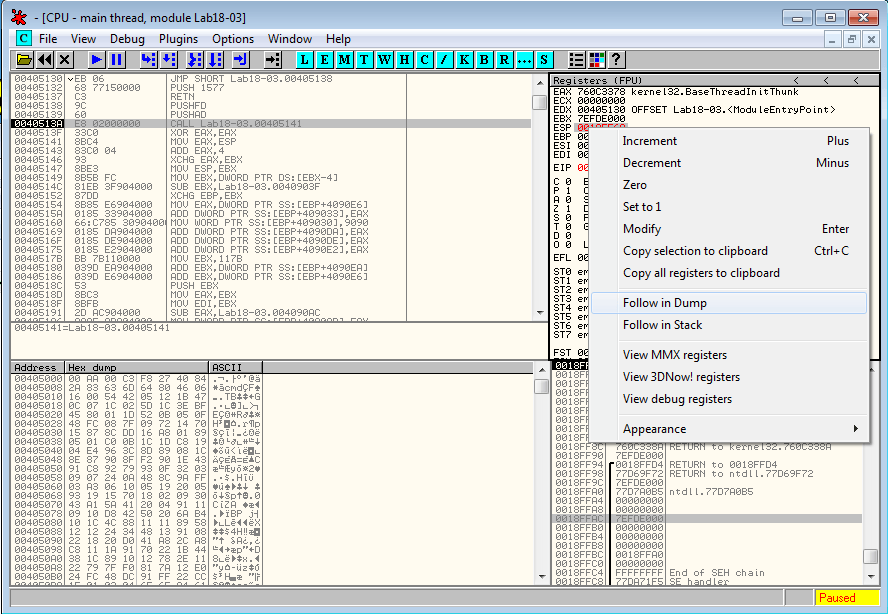
Let's step over the first 3 instructions, until the program stops at 0x50513A. Now, we want to know the value of the stack pointer and set a breakpoint. To do that, right click on the ESP register and select Follow in dump:
Now in the memory dump window, right click on the first byte and select Breakpoint > Hardware, on Access > Dword:
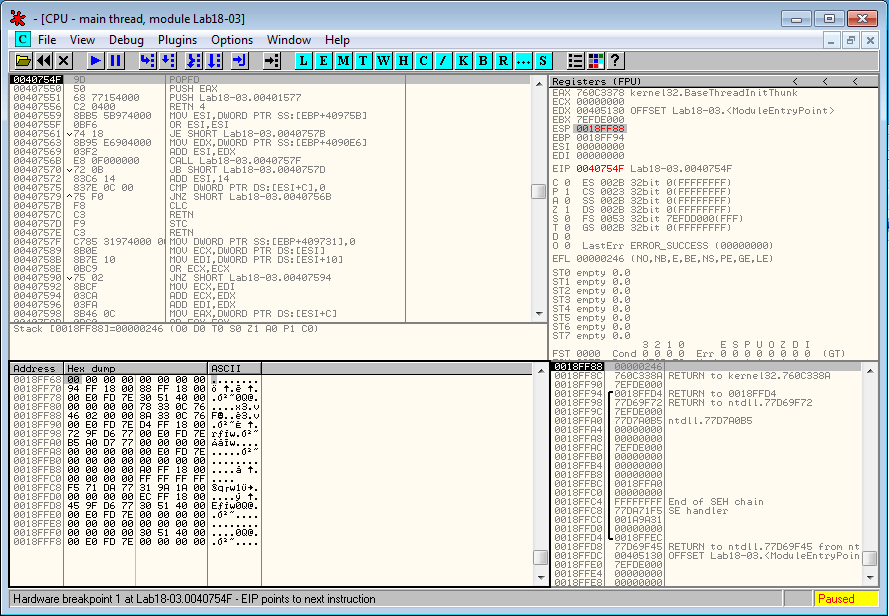
When we run the program (F9), it reaches our breakpoint:
The code is as follows. It shows a return instruction that transfers the execution to another location, which might be the tail jump.
0040754E 61 POPAD
0040754F 9D POPFD
00407550 50 PUSH EAX
00407551 68 77154000 PUSH Lab18-03.00401577
00407556 C2 0400 RETN 4
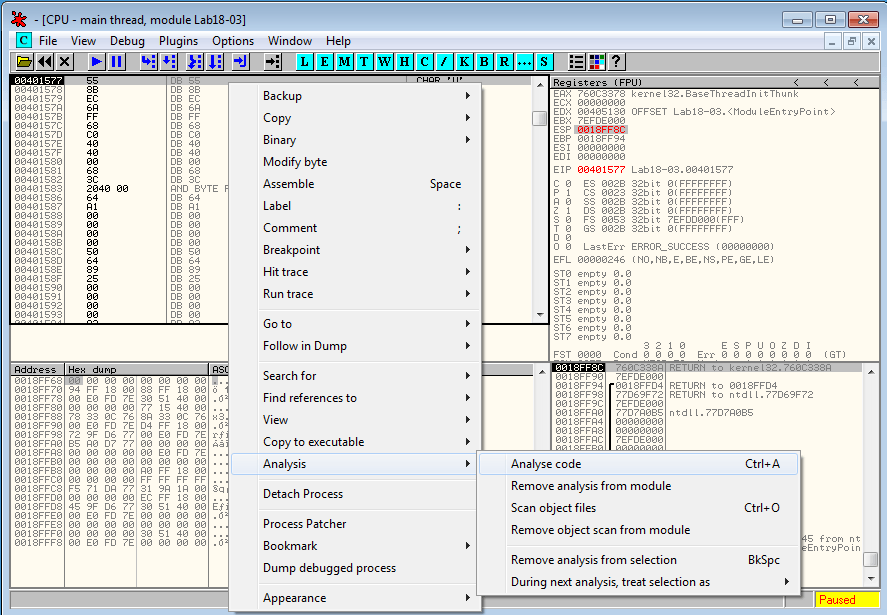
Let's step over till 0x407551 and step into 0x407556. The code hasn't been disassembled by OllyDbg, wich can be easily fixed by selecting Analysis > Analyze code:
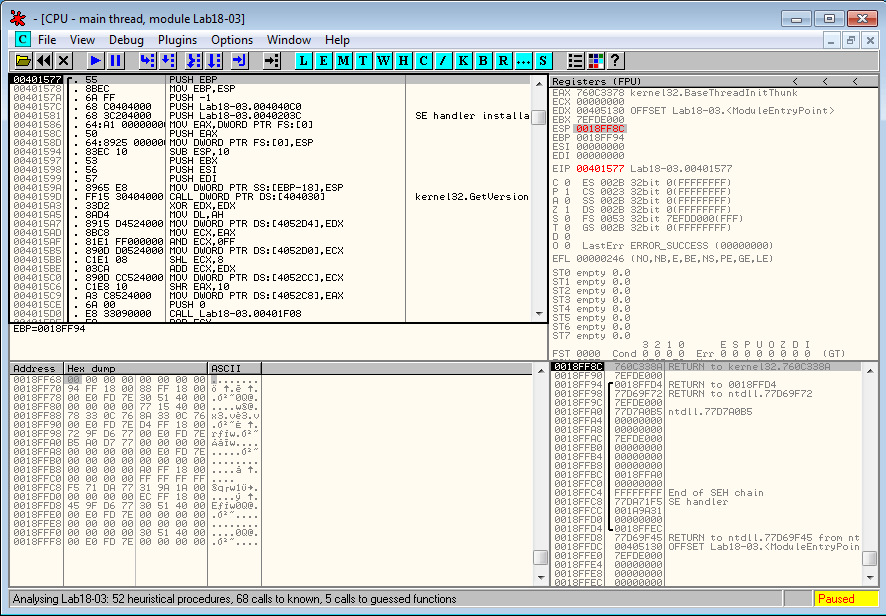
We have successfully reached the OEP:
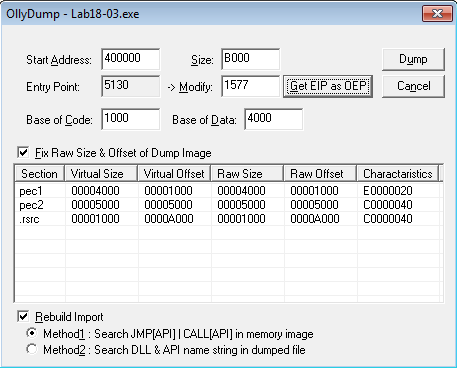
Now, use OllyDump (Plugins > OllyDump > Dump debugged process) to dump the process in memory. Click on the Get EIP as OEP button and then on the Dump button:
And we're done.
Automated unpacking
OllyScript
- PE Compact 2.xx - Find target's OEP (by hacnho/VCT2k4)
- PECompact 0.9x - Find target's OEP (by ~Hellsp@wN~)
- PEcompact 2.00-2.38 OEP Finder (by fpx)
- PECompact 2.40 - Find target's OEP (by dqtln)
- PECompact v.2.40 - OEP finder (by DWord)
This category currently contains no pages or media.