Category:Digital-Forensics/Computer-Forensics/Anti-Reverse-Engineering/Packers
| You are here: | Packers
|
Description
Packing/Unpacking process
Malware is often packed. It produces a version of the execuatble that is smaller in size and more difficult to analyze for the malware analyst. The malware analyst will still be able to work with a packed version for a behavioral analysis but in many cases, the unpacked version will be necessary to perform a static analysis.
Fully unpacked
Executable
Original Packed (on disk)
Executable Executable ┌────────────────┐
(on disk) (in memory) │ header │
┌────────────────┐ ┌────────────────┐ ├────────────────┤
│ header │ │ header │ │ exports │
├────────────────┤ ├────────────────┤ ├────────────────┤
│ imports │ │ exports │ EP ─►│ .text │
├────────────────┤ ├────────────────┤ │ section │
│ exports │ Packed │ .text │ ├────────────────┤
├────────────────┤ Executable │ section │ │ .data │
OEP ─►│ .text │ (on disk) ├────────────────┤ │ section │
│ section │ ┌────────────────┐ │ .data │ ├────────────────┤
├────────────────┤ │ header │ │ section │ │ .rsrc │
│ .data │ ├────────────────┤ ├────────────────┤ │ section │
│ section │ EP ─►│ unpacking stub │ │ .rsrc │ ├────────────────┤
├────────────────┤ ├────────────────┤ │ section │ │ unpacking stub │
│ .rsrc │ │ packed │ ├────────────────┤ ├────────────────┤
│ section │ │ executable │ EP ─►│ unpacking stub │ │ imports │
└────────────────┘ └────────────────┘ └────────────────┘ └────────────────┘
│ ▲ │ ▲ ▲
└─────── packing ───────┘ └────── unpacking ──────┴─────────────────────────┘
Unpacking Stub
The unpacking stub performs the following actions:
- unpacks the original executable into memory
- resolves imports
- transfers execution to the OEP
Identifying packers
OllyDbg and IDA Pro
Openeing a packed executable
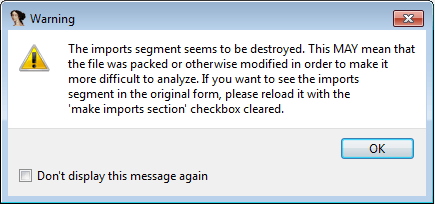
- in OllyDbg will display a warning that the executable may be packed
- in IDA-Pro may also warn and only a small amount of code will be recognized by the automatic analysis.
Imports
Packed programs have very few imports (usually LoadLibrary and GetProcAddress), even sometimes no import at all.
Strings
Many packers leave text signatures inside the packed binary. Here are a few examples:
$ strings /data/malware/storm.exe Reserved. $ UPX! [SNIP]
$ strings /data/malware/windowsxp2.exe [SNIP] PECompact2 [SNIP]
$ strings /data/malware/bintext.exe [SNIP] NTkrnl Secure Suite Version 0.1 Metamorphism Portable Executable (PE) Packer and Protector Library Copyright 2006-2007 Ashkbiz Danehkar All Rights Reserved Homepage: http://www.ntkrnl.com E-mail: [email protected] NTkrnl Geborgene Zeug [SNIP]
file command
In some cases, the file command will be able to identify the packer:
$ file /data/malware/storm.exe /data/malware/storm.exe: PE32 executable (console) Intel 80386, for MS Windows, UPX compressed, ARJ self-extracting archive
$ file /data/malware/windowsxp2.exe /data/malware/windowsxp2.exe: PE32 executable (GUI) Intel 80386, for MS Windows, PECompact2 compressed
pescanner.py / PEiD
The pescanner.py script will be able to identify some packers:
$ ./pescanner.py /data/malware/storm.exe ################################################################################ Record 0 ################################################################################ Meta-data ================================================================================ File: /data/malware/storm.exe Size: 3342142 bytes Type: PE32 executable (console) Intel 80386, for MS Windows, UPX compressed, ARJ self-extracting archive MD5: f9e28f48de73e3d49688482c77591eea SHA1: 42a92d365378e6469f71edf36a847f0417ca3a77 ssdeep: Date: 0x7730294B [Sat May 14 00:56:43 2033 UTC] [SUSPICIOUS] EP: 0x41cad0 UPX1 1/3 [SUSPICIOUS] CRC: Claimed: 0x0, Actual: 0x337f6a [SUSPICIOUS] Packers: UPX -> www.upx.sourceforge.net Sections ================================================================================ Name VirtAddr VirtSize RawSize Entropy -------------------------------------------------------------------------------- UPX0 0x1000 0x12000 0x0 0.000000 [SUSPICIOUS] UPX1 0x13000 0xa000 0x9e00 7.873877 [SUSPICIOUS] UPX2 0x1d000 0x1000 0x200 1.569615
PEiD can also detect the packer.
Tools
- PEiD
- packerid
- Protection-ID
- RDG-Packer-Detector
- Exeinfo-PE
- QuickUnpack
- AllUnpack
- FUU-Faster-Universal-Unpacker
- ...
Analyzing packed executables
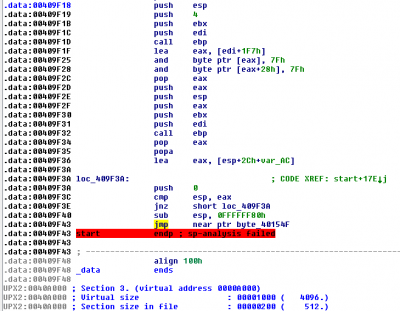
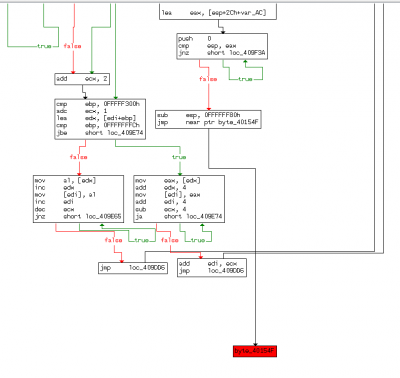
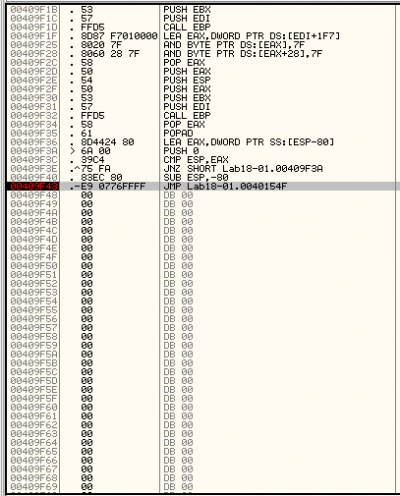
The Tail Jump
The tail jump is the instruction executed by the unpacking stub to reach the OEP:
- jump instruction
- ret or call instructions
The tail jump can be identified with IDA-Pro and OllyDbg. It sometimes appears as the last valid instruction:
|
|
|
Unpacking
The unpacking process can be fully automated (e.g. with UPX), semi-automated or fully manual.
Some examples are given below:
| Packer | Manual | Automated |
|---|---|---|
| UPX | manual | automated |
| PE Compact | manual | automated |
More generally, unpacking an executable often involves locating the tail jump (e.g. jump to EAX) to find the Original Entry Point (OEP).
Debugging packed executables without dumping
It is sometimes tricky to unpack an executable and it could be less time consuming to analyze it in memory.
Here is an example for an UPX packed malware.
Patching

Thank you for your comprehension.
Comments
Subcategories
This category has the following 13 subcategories, out of 13 total.
D
Pages in category "Digital-Forensics/Computer-Forensics/Anti-Reverse-Engineering/Packers"
The following 16 pages are in this category, out of 16 total.