Category:Digital-Forensics/Computer-Forensics/Anti-Reverse-Engineering/Packers/UPX
| You are here: | UPX
|
Description
UPX (the Ultimate Packer for eXecutables) is a free, portable, extendable, high-performance executable packer for several executable formats.
ANalyzing UPX packed executables
Manually unpacking UPX packed executables
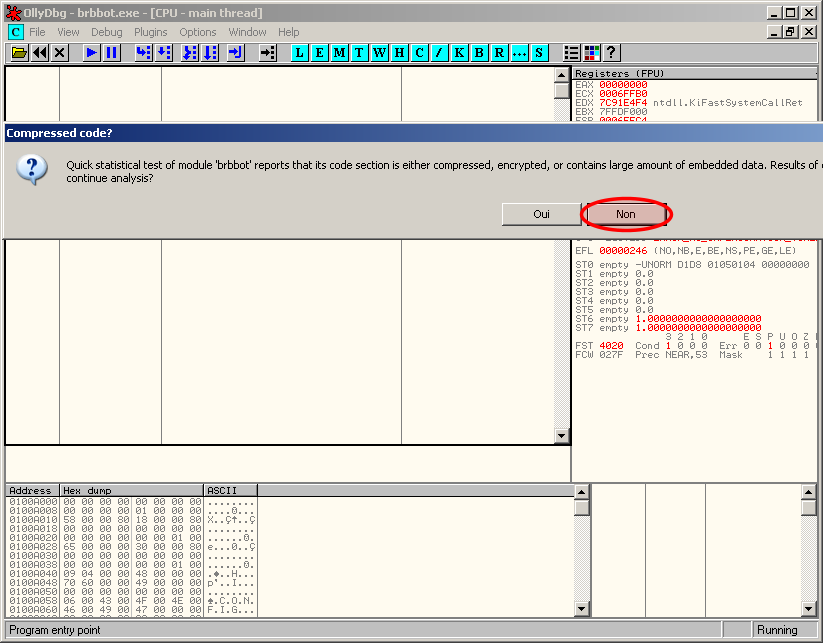
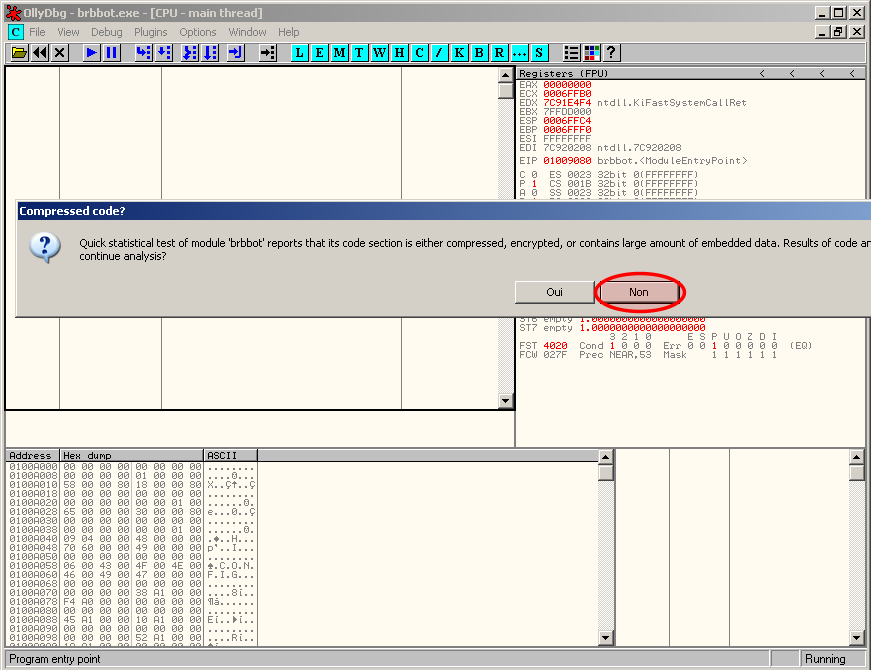
Load the malware into OllyDbg. When prompted the following message, select "No":
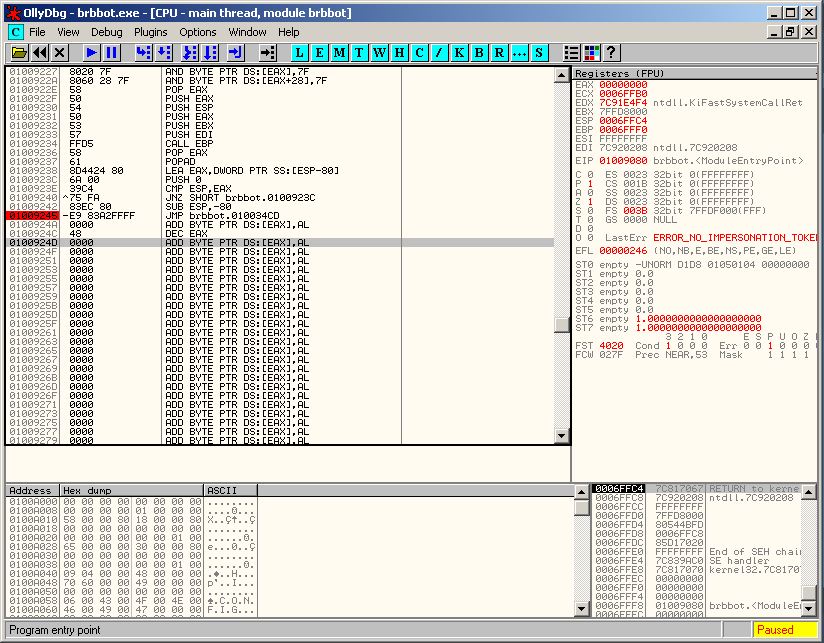
Scroll down, closed to the end of the code and place a breakpoint to the JMP instruction, just before the beginning of the "0000" instructions:
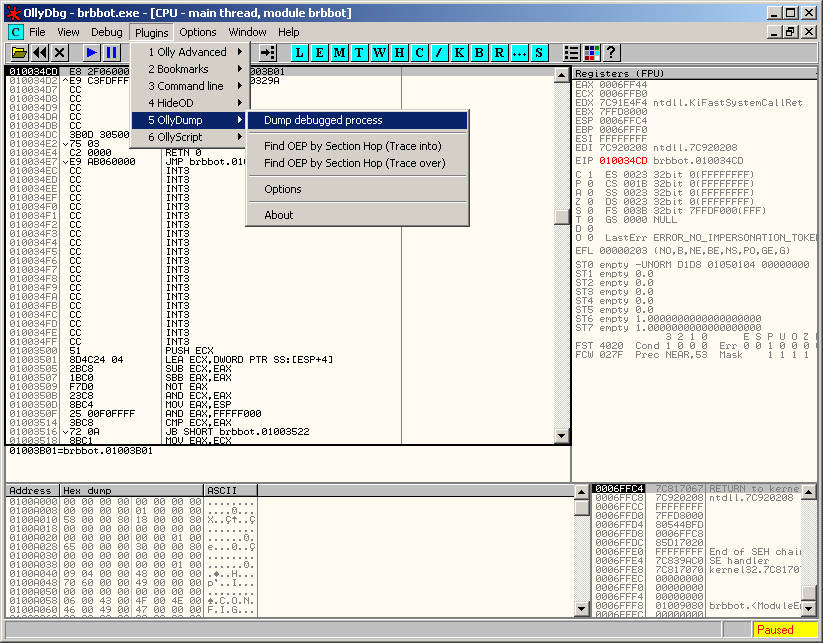
Press F9 to launch the malware. It will stop at the breakpoint (Offset 01009245 in the screenshot). Press F7 to step into the jump and you should arrive at the beginning of the unpacked code (offset 010034CD in the below screenshot):
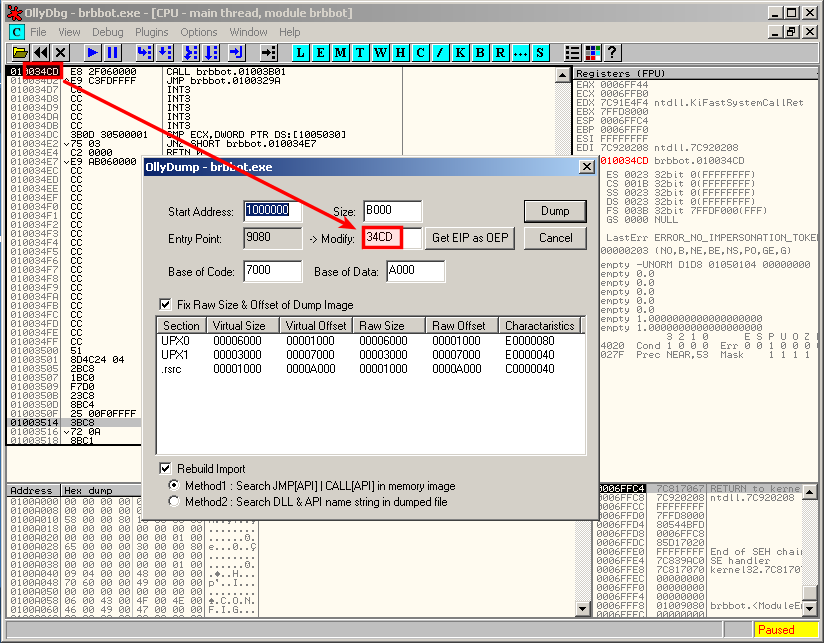
You can now dump the process in memory, using the OllyDump plugin:
Automated way of unpacking UPX packed executables
Tools:
- UPX: upx -d packed_exe.exe
Analyze UPX packed executables without dumping it
When analyzing a packed executable in OllyDbg, always remember to answer "No" to the following message:
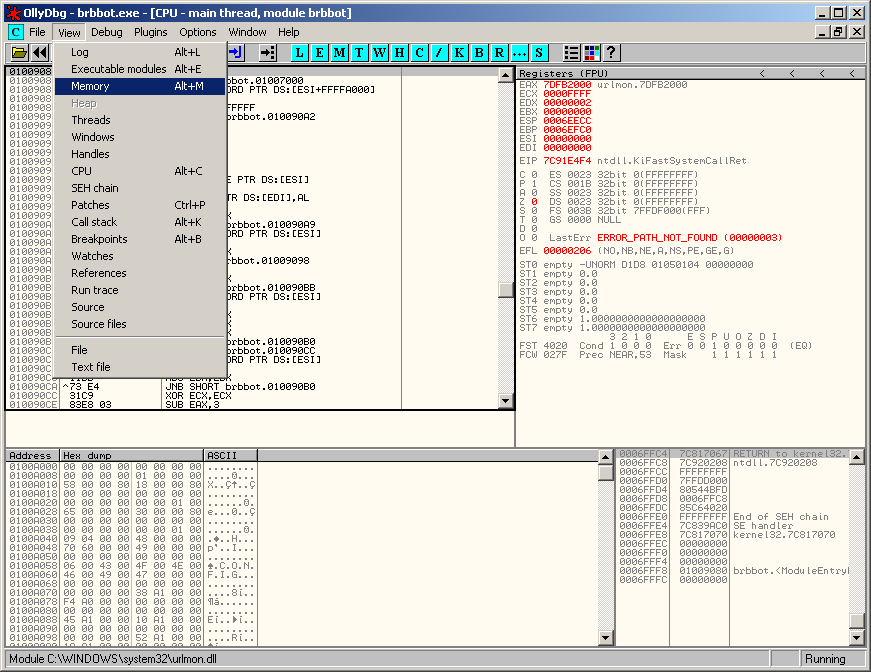
Once the malware is loaded, run it (F9) and go to View > Memory (ALT+M):
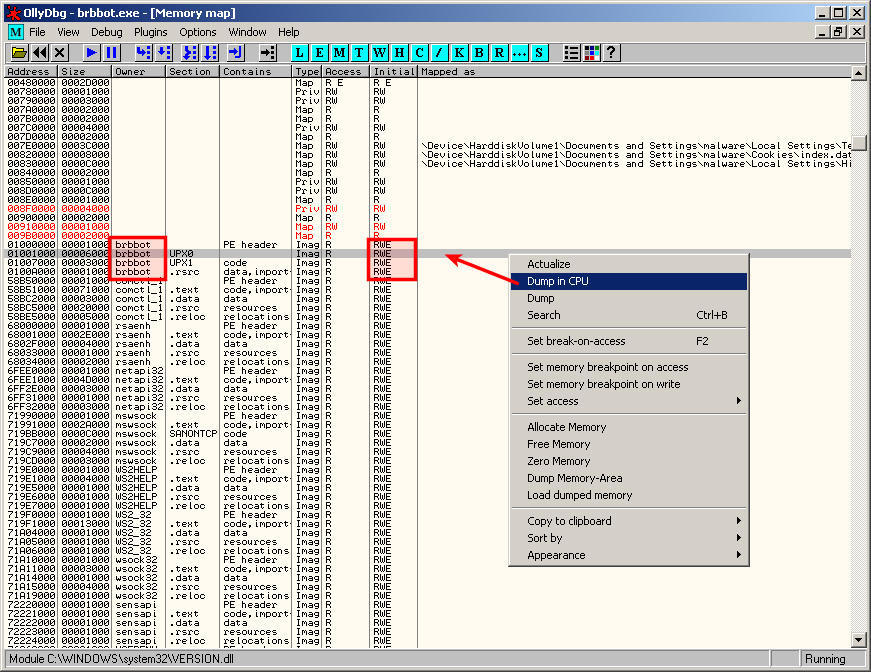
From the memory map, analyze the sections related to the malware you're analyzing (brbbot in our example) and pay attention to sections with the "RWE" (Read / Write / Execute) flags. One of these sections should contain the unpacked code. Let's try with the first one (UPX0). Right click on the line and select "Dump in CPU":
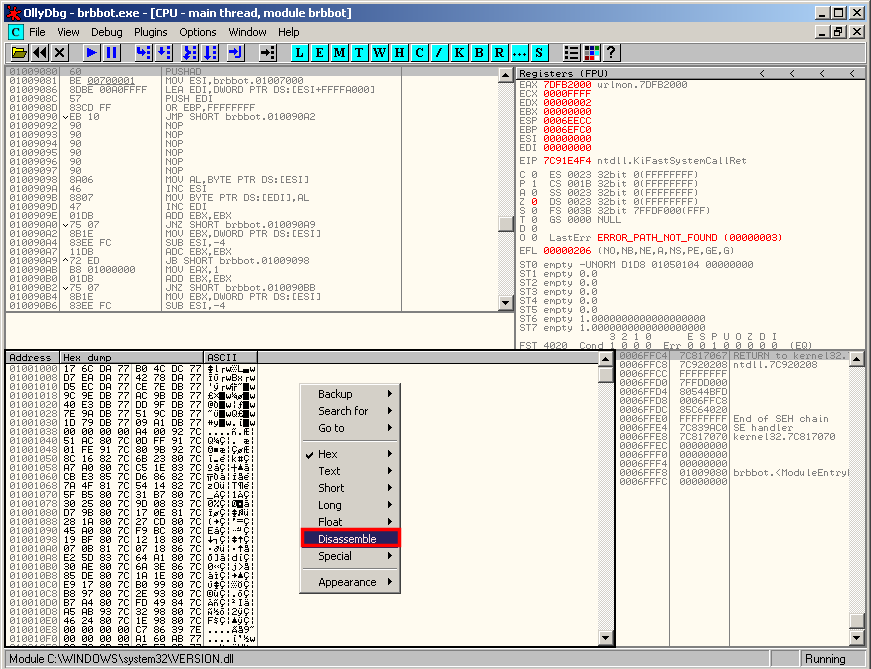
In the dump panel, right click and switch to the "Disassemble" view:
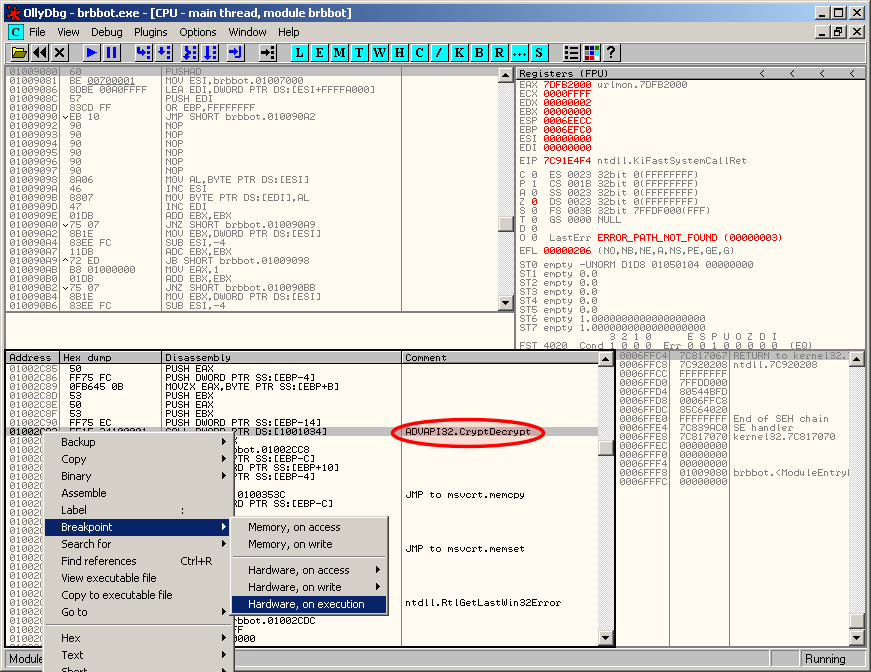
If you are in the correct section, you should see standard assembly code. If it is not the case, you're probably in the wrong section and you should try with another one. When you notice an interesting function you would like to analyze, you can set a breakpoint (hardware on execution):
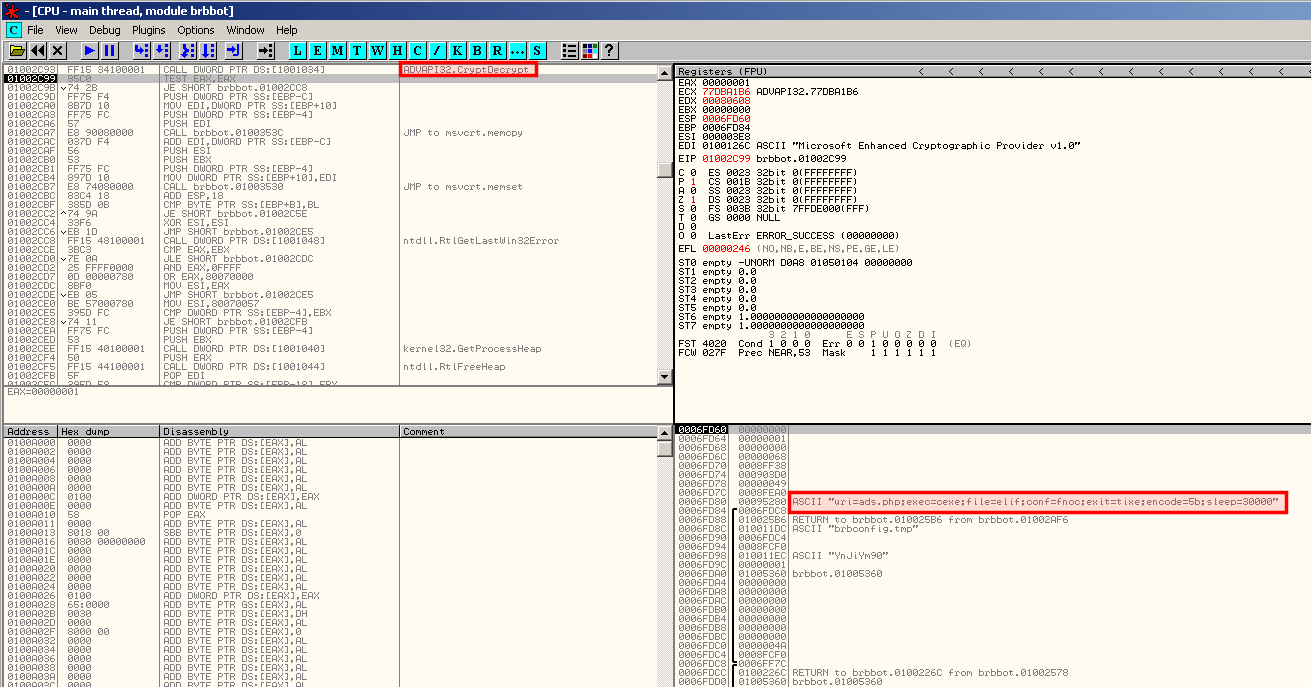
Restart the malware (Ctrl+F2). It should pause to where you've placed the breakpoint. In our example, we step over (F8) to analyze what the CryptDecrypt function has returned. We are now able to see the decrypted string:
Comments
Pages in category "Digital-Forensics/Computer-Forensics/Anti-Reverse-Engineering/Packers/UPX"
Pages in category "Digital-Forensics/Computer-Forensics/Anti-Reverse-Engineering/Packers/UPX"
The following 3 pages are in this category, out of 3 total.