Category:Digital-Forensics/Computer-Forensics/Debugger/Kernel
Jump to navigation
Jump to search
| You are here: | Kernel
|
Description

INCOMPLETE SECTION OR ARTICLE
This section/article is being written and is therefore not complete.
Thank you for your comprehension.
Thank you for your comprehension.
Environment
Possible configurations
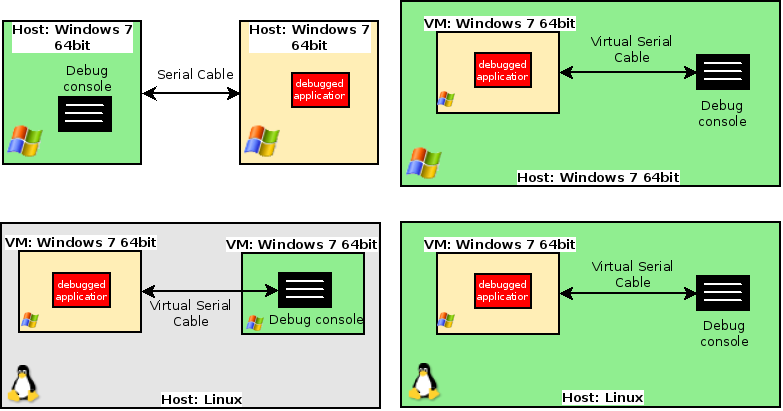
When the kernel is being debugged, the OS is frozen. Hence, the debugging console should be run on a separate host. Possible configurations are:
Connect 2 Windows virtual machines on a Linux host
Environment
This setup has been tested in the following environment:
| Physical Host | Linux Debian Jessie 64bit |
|---|---|
| Virtualisation | VMware WorkStation 11 for Linux 64bit |
| Debugger | WinDbg running on Windows 7 64bit |
| Debuggee | Windows 7 64bit |
Configuration of the debugger
On the debugger, follow the below configuration steps:
- Shut the VM down
- Edit virtual machine settings
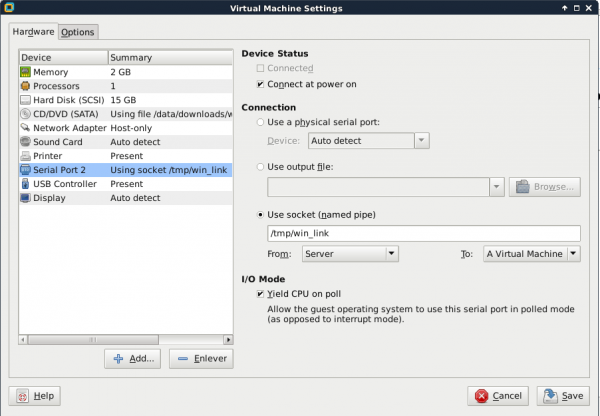
- Add Hardware > Serial Port
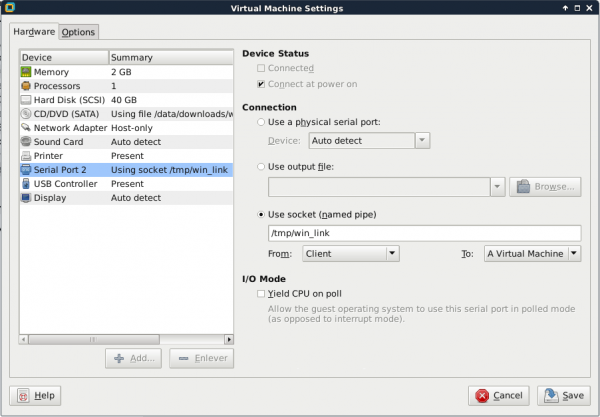
- Configure as follows:
- Start the virtual machine
- Start WinDbg
- Press Ctrl+K to invoke the kernel debugging menu.
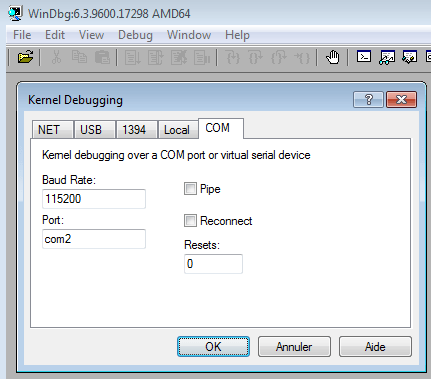
- Ensure Baud Rate and Port are respectively set to 115200 and com2 (or whatever port you has been defined previously) and that both pipe and reconnect options are unchecked:
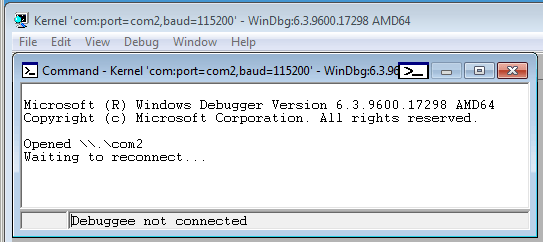
- When you click OK, you should be displayed with the following screen:
Configuration of the debuggee
Follow the below configuration steps:
- Run bcdedit. You should have 2 profiles (bootmgr and current) as follows:
C:\>bcdedit Windows Boot Manager -------------------- identificateur {bootmgr} device partition=\Device\HarddiskVolume1 description Windows Boot Manager locale fr-FR inherit {globalsettings} default {default} resumeobject {f567f5a5-ddcd-11e4-8b74-ed09eab0b322} displayorder {default} {current} toolsdisplayorder {memdiag} timeout 30 Windows Boot Loader ------------------- identificateur {current} device partition=C: path \Windows\system32\winload.exe description Windows 7 locale fr-FR inherit {bootloadersettings} recoverysequence {f567f5a7-ddcd-11e4-8b74-ed09eab0b322} recoveryenabled Yes osdevice partition=C: systemroot \Windows resumeobject {f567f5a5-ddcd-11e4-8b74-ed09eab0b322} nx OptIn - Duplicate the current profile to create a new boot profile that we will use to debug the kernel:
C:\>bcdedit.exe /copy {current} /d "Windows 7 with debug" The entry was successfully copied to {f567f5a5-ddcd-11e4-8b74-ed09eab0b322}. - Activate the debug profile (replace the profile ID with the one you got from the previous command):
C:\>bcdedit.exe /debug {f567f5a5-ddcd-11e4-8b74-ed09eab0b322} on The operation completed successfully. - Specify the port (2 for COM2, to be eventually replaced with the port defined previously) and baudrate (default to 115200) for the serial connection:
C:\>bcdedit /dbgsettings serial debugport:2 baudrate:115200 The operation completed successfully.
- Check that your settings are correct:
C:\>bcdedit /dbgsettings debugtype Serial debugport 2 baudrate 115200 The operation completed successfully. C:\>bcdedit Windows Boot Manager -------------------- identificateur {bootmgr} device partition=\Device\HarddiskVolume1 description Windows Boot Manager locale fr-FR inherit {globalsettings} default {default} resumeobject {f567f5a5-ddcd-11e4-8b74-ed09eab0b322} displayorder {default} {current} toolsdisplayorder {memdiag} timeout 30 Windows Boot Loader ------------------- identificateur {default} device partition=C: path \Windows\system32\winload.exe description Windows 7 locale fr-FR inherit {bootloadersettings} recoverysequence {f567f5a7-ddcd-11e4-8b74-ed09eab0b322} recoveryenabled Yes osdevice partition=C: systemroot \Windows resumeobject {f567f5a5-ddcd-11e4-8b74-ed09eab0b322} nx OptIn Windows Boot Loader ------------------- identificateur {current} device partition=C: path \Windows\system32\winload.exe description Windows 7 with debug locale fr-FR inherit {bootloadersettings} recoverysequence {f567f5a7-ddcd-11e4-8b74-ed09eab0b322} recoveryenabled Yes osdevice partition=C: systemroot \Windows resumeobject {f567f5a5-ddcd-11e4-8b74-ed09eab0b322} nx OptIn debug Yes - Shut the virtual machine down
- Edit virtual machine settings
- Add Hardware > Serial Port
- Configure as follows
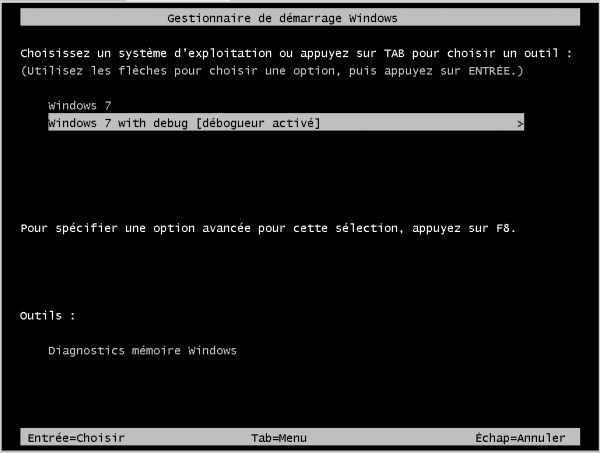
- Start the virtual machine and select the debugging profile from the boot sequence:
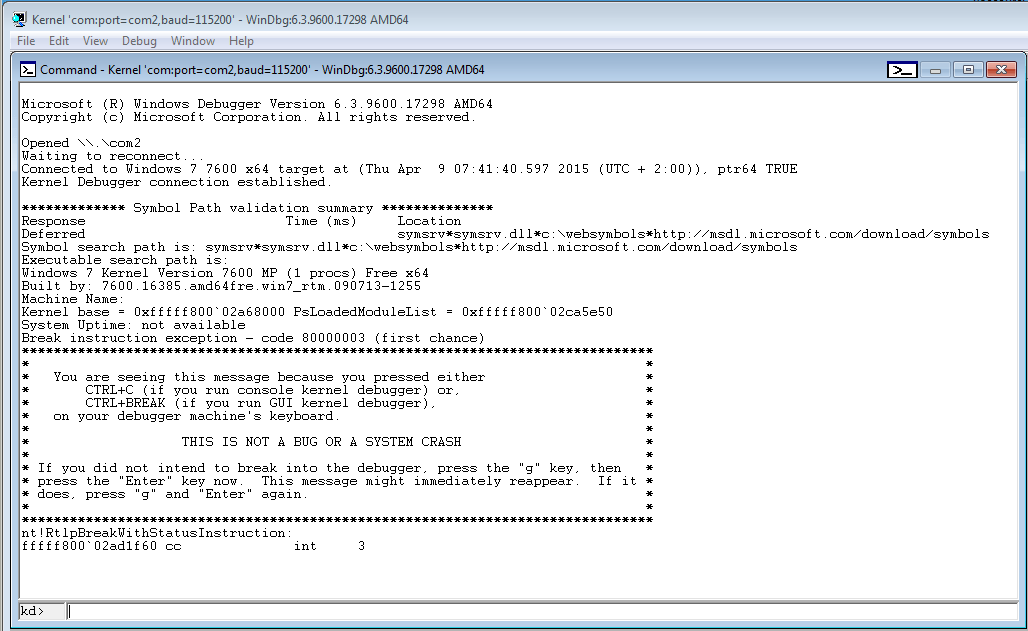
Back on the debugger virtual machine, you should be able to see the success of the connection:
Connect a Windows virtual machine to a Windows physical host

INCOMPLETE SECTION OR ARTICLE
This section/article is being written and is therefore not complete.
Thank you for your comprehension.
Thank you for your comprehension.
Comments
Pages in this category
Subcategories
This category has only the following subcategory.
Pages in category "Digital-Forensics/Computer-Forensics/Debugger/Kernel"
The following 5 pages are in this category, out of 5 total.