Category:Digital-Forensics/Information-stealing-malware/Keyloggers
| You are here | Keyloggers
|
Description
- Often malware has keylogging capabilities that give the ability to steal sensitive information (passwords, credit card numbers, ...) and send it to a remote controler.
- Very often, a local file is also created to save the stolen information.
- Two common techniques are used:
- SetWindowsHookEx: Install hook for keyboard events
- GetAsyncKeyState: Poll keyboard state with GetAsyncKeyState()
SetWindowsHookEx
This method is based on the DLL injection technique using SetWindowsHookEx.
Below is an extract from a worm named "Worm:Win32/Autorun.AHA" available for download here (pass: infected).
Intercept keyboard messages:
.text:004121A8 push 0 ; dwThreadId
.text:004121AA mov eax, dword_475394
.text:004121AF mov ecx, [eax+28h]
.text:004121B2 push ecx ; hmod
.text:004121B3 push offset fn ; lpfn
.text:004121B8 push WH_KEYBOARD_LL ; idHook (Initial value: 0x0D [hex] = 13 [decimal])
.text:004121BA call ds:SetWindowsHookExA
Intercept mouse messages:
.text:00414508 push 0 ; dwThreadId
.text:0041450A mov eax, dword_475394
.text:0041450F mov ecx, [eax+28h]
.text:00414512 push ecx ; hmod
.text:00414513 push offset sub_4143C0 ; lpfn
.text:00414518 push WH_MOUSE_LL ; idHook (Initial value: 0x0E [hex] = 14 [decimal])
.text:0041451A call ds:SetWindowsHookExA
This trojan creates a text file where keystrokes are logged.
GetAsyncKeyState
Extract from spybot keylogger assembly code:
.text:004032D9 loc_4032D9:
.text:004032D9 push 10h ; nVirtKey (SHIFT key)
.text:004032DB call GetKeyState
.text:004032E0 mov edi, eax
.text:004032E2 movsx edi, di
.text:004032E5 mov [ebp+var_8], edi
.text:004032E8 mov edi, [ebp+var_4]
.text:004032EB mov ebx, vKey[edi*4]
.text:004032F2 push ebx ; vKey
.text:004032F3 call GetAsyncKeyState
.text:004032F8 mov edi, eax
.text:004032FA movsx edi, di
.text:004032FD test di, 8000h
.text:00403302 jz short loc_403382
The first function (GetKeyState) checks if the SHIFT key (0x10) is depressed. This way, the program will be able to identify upper case letters, numbers and some special characters.
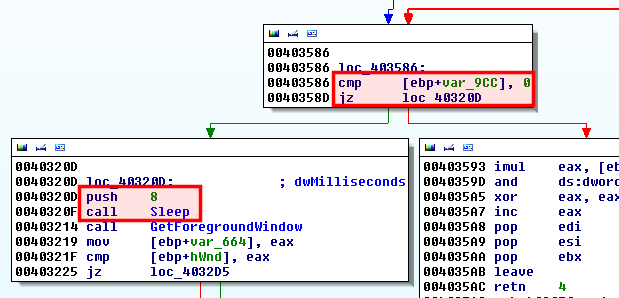
Then the GetAsyncKeyState is called in a loop, starting at address 0x40320D and ending at 0x40358D with a conditional jump (see below screenshot, keys are checked every 8 milliseconds), examining the status of each key.
Comments
Pages in this category
Pages in category "Digital-Forensics/Information-stealing-malware/Keyloggers"
The following 10 pages are in this category, out of 10 total.