The-FLARE-On-Challenge-01/Challenge-5
| You are here | Challenge 5
|
Identification
Download the file: http://www.flare-on.com/files/C5.zip and uncompress it using "malware" as the password:
$ 7z x C5.zip 7-Zip [64] 9.20 Copyright (c) 1999-2010 Igor Pavlov 2010-11-18 p7zip Version 9.20 (locale=fr_FR.utf8,Utf16=on,HugeFiles=on,4 CPUs) Processing archive: C5.zip Extracting 5get_it Enter password (will not be echoed) : malware Everything is Ok Size: 101376 Compressed: 39309
It results in a file named 5get_it which is a DLL:
$ file 5get_it 5get_it: PE32 executable (DLL) (GUI) Intel 80386, for MS Windows
This program is a keylogger
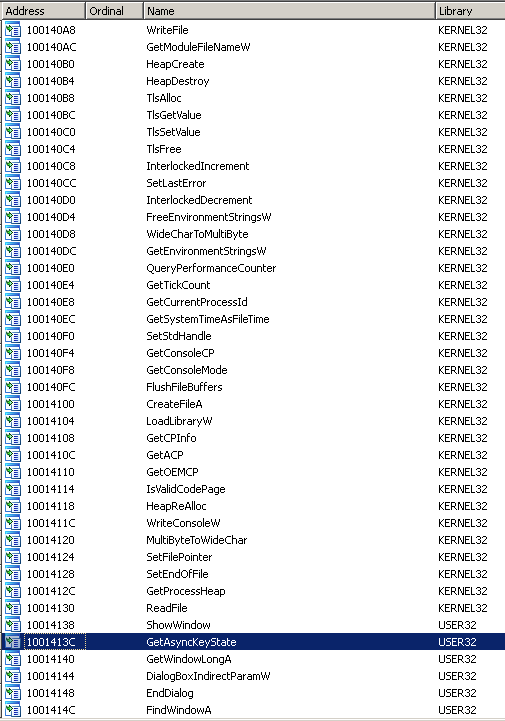
IAT
Let's open the file into IDA Pro and check what imports we find. The presence of GetAsyncKeyState indicates that we have probably to do with a keylogger.
DllMain
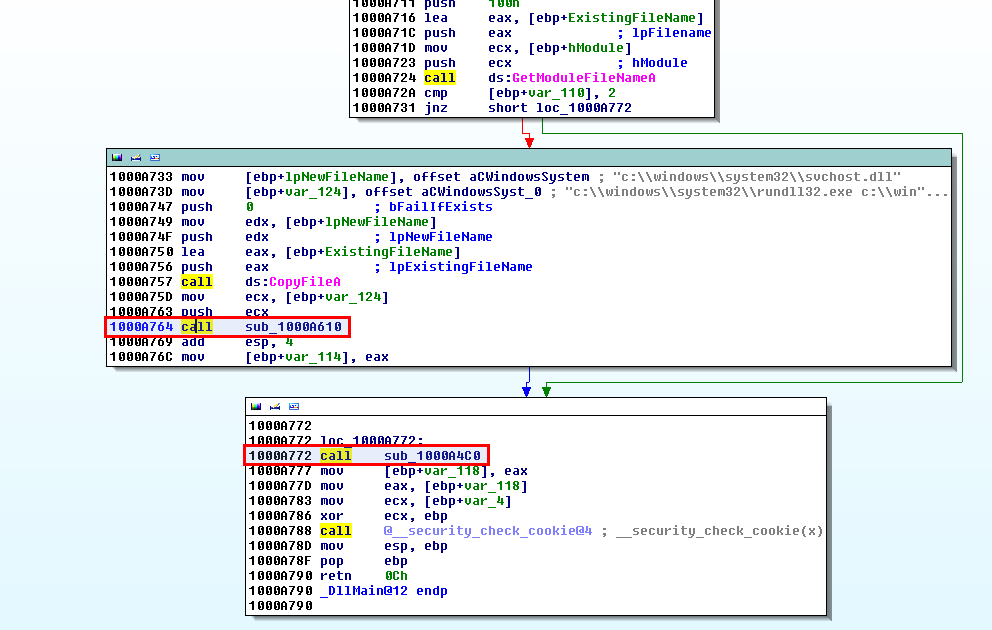
If we focus on the calls, we can see 2 interesting functions:
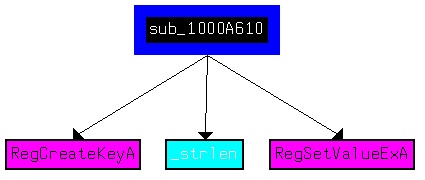
sub_1000A610 (offset 0x1000A764)
A quick "Xref from" shows that sub_1000A610 (offset 0x1000A764) sets up registry keys:
sub_1000A4C0 (offset 0x1000A772)
Let's have a look at sub_1000A4C0 (offset 0x1000A772). Again, there are two functions we want to analyze:
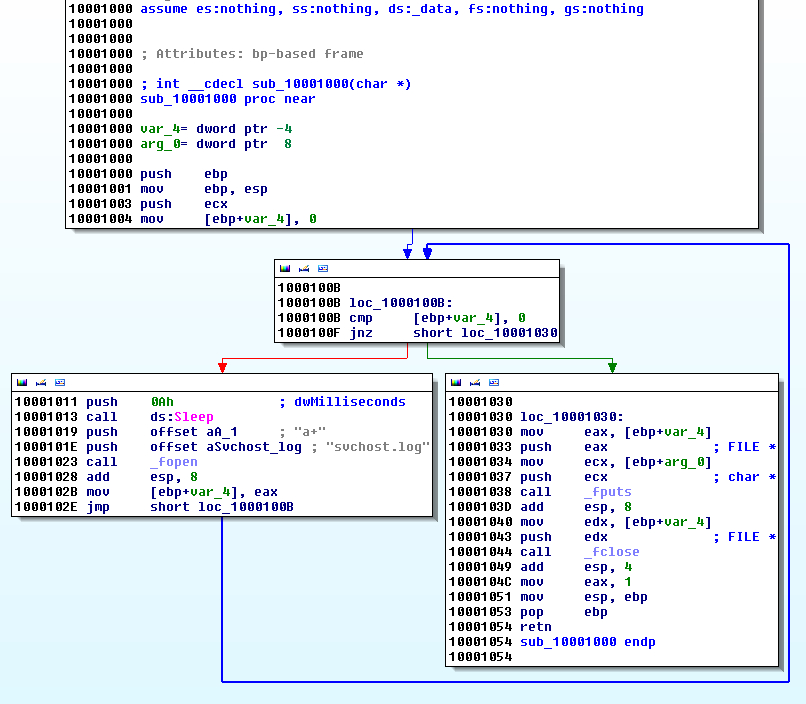
sub_10001000 (offset 0x1000A53E)
This function writes to svchost.log which is very likely to be the log file where keystrokes are written.
sub_10009EB0 (offset 0x1000A52C)
The Graph overview shows a typical switch case scenario:
Where the cases are very likely to be the keys:
The "m" key
sub_10001240 (offset 0x10001240)
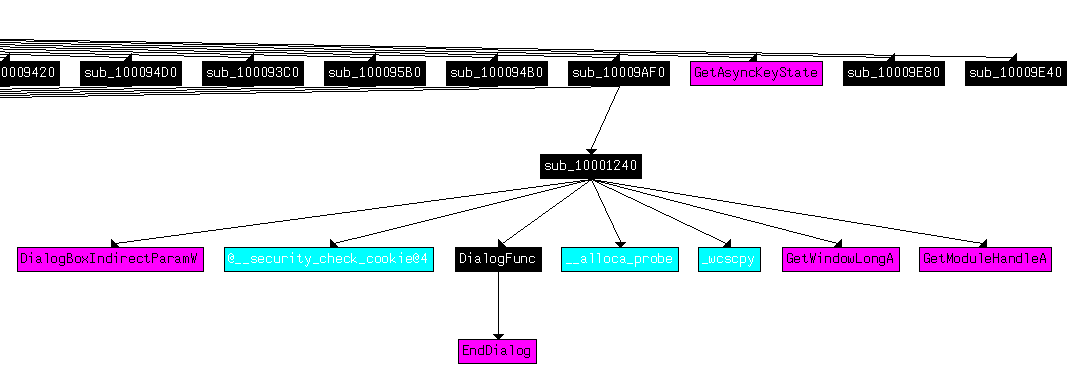
Now, we have a good overview of what this program does but it did not help us find the email (solution). So we continue our anlaysis. Doing a "Xref from" graph on sub_10009EB0 shows a zone that might be interesting:
If we zoom on the region of interest, we see a function, sub_10001240, called from sub_10009AF0, itself called from sub_10009EB0 that we have already analyzed above
sub_10001240 seems to build a huge stack string:
.text:10001240 sub_10001240 proc near ; CODE XREF: sub_10009AF0+11�p
.text:10001240
.text:10001240 var_1590 = dword ptr -1590h
.text:10001240 var_158C = word ptr -158Ch
.text:10001240 var_158A = word ptr -158Ah
.text:10001240 var_1588 = word ptr -1588h
.text:10001240 var_1586 = word ptr -1586h
.text:10001240 var_1584 = word ptr -1584h
.text:10001240 var_1582 = word ptr -1582h
.text:10001240 var_1580 = word ptr -1580h
.text:10001240 var_157E = word ptr -157Eh
.text:10001240 var_157C = word ptr -157Ch
.text:10001240 var_157A = word ptr -157Ah
[SNIP]
.text:10001240 var_C = word ptr -0Ch
.text:10001240 var_A = word ptr -0Ah
.text:10001240 var_8 = word ptr -8
.text:10001240 var_6 = word ptr -6
.text:10001240 var_4 = dword ptr -4
.text:10001240
.text:10001240 push ebp
.text:10001241 mov ebp, esp
.text:10001243 mov eax, 1590h
.text:10001248 call __alloca_probe
.text:1000124D mov eax, ___security_cookie
.text:10001252 xor eax, ebp
.text:10001254 mov [ebp+var_4], eax
.text:10001257 mov [ebp+hWndParent], 0
.text:10001261 mov [ebp+dwInitParam], 0
.text:10001268 mov eax, 43h
.text:1000126D mov [ebp+var_158C], ax
.text:10001274 mov ecx, 6Fh
.text:10001279 mov [ebp+var_158A], cx
[SNIP]
.text:10009286 mov [ebp+var_26], dx
.text:1000928A mov eax, 0Ah
.text:1000928F mov [ebp+var_24], ax
.text:10009293 xor ecx, ecx
.text:10009295 mov [ebp+var_22], cx
.text:10009299 lea edx, [ebp+var_18]
.text:1000929C push edx ; wchar_t *
.text:1000929D push offset word_1001701E ; wchar_t *
.text:100092A2 call _wcscpy
.text:100092A7 add esp, 8
.text:100092AA lea eax, [ebp+var_158C]
.text:100092B0 push eax ; wchar_t *
.text:100092B1 push offset word_10017034 ; wchar_t *
.text:100092B6 call _wcscpy
.text:100092BB add esp, 8
.text:100092BE lea ecx, [ebp+var_1570]
.text:100092C4 push ecx ; wchar_t *
.text:100092C5 push offset word_10017062 ; wchar_t *
.text:100092CA call _wcscpy
.text:100092CF add esp, 8
.text:100092D2 cmp [ebp+hWndParent], 0
.text:100092D9 jz short loc_100092F2
.text:100092DB push 0FFFFFFFAh ; nIndex
.text:100092DD mov edx, [ebp+hWndParent]
.text:100092E3 push edx ; hWnd
.text:100092E4 call ds:GetWindowLongA
.text:100092EA mov [ebp+var_1590], eax
.text:100092F0 jmp short loc_10009300
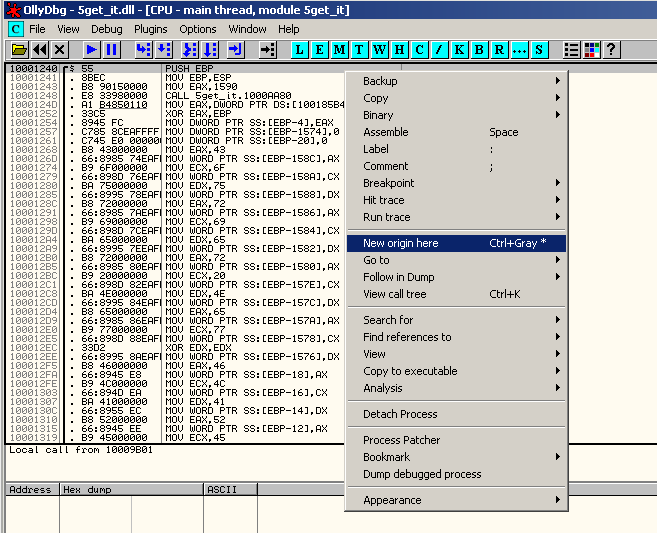
Since the function has no argument, let's run it in OllyDbg and change the EIP (to do that, go to offset 0x10001240, right click and select "New origin here"):
Once done, run the program (F9). It will pop up the following box:
sub_10009AF0 (offset 0x10009AF0)
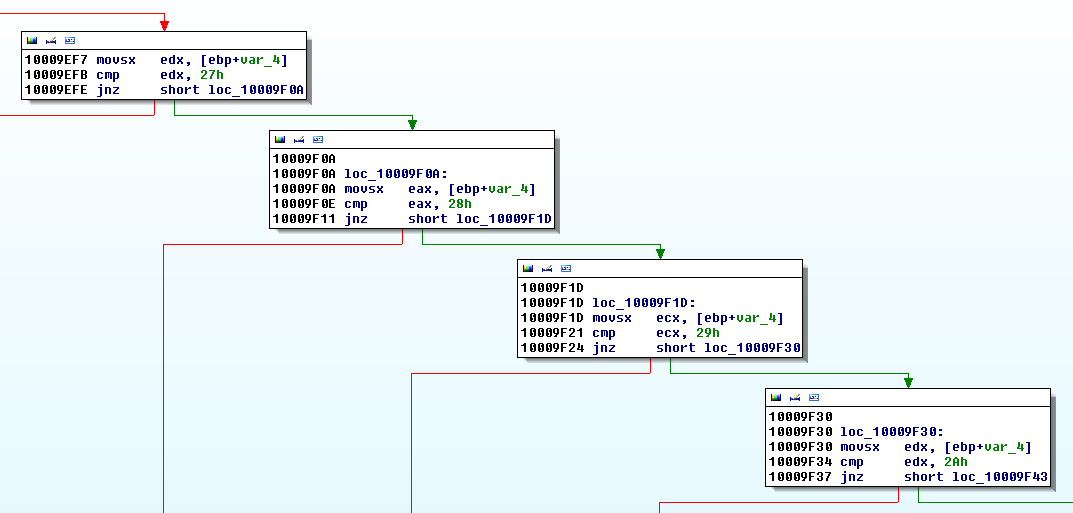
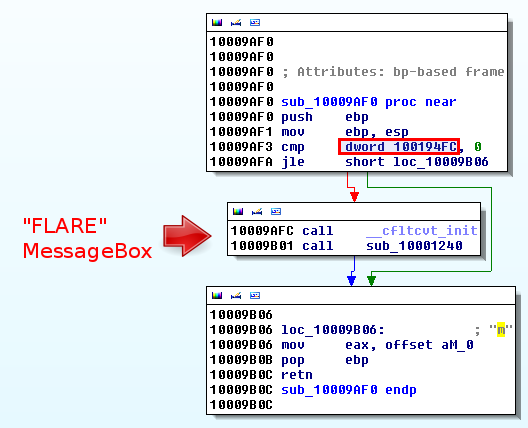
As depicted below, the sub_10009AF0 function is checking a global variable to determine whether the "FLARE" box will be displayed and then it seems to catch the "m" key.
What is this dword_100194FC variable?
The "o" key: sub_10009B60 (offset 0x10009B60)
dword_100194FC
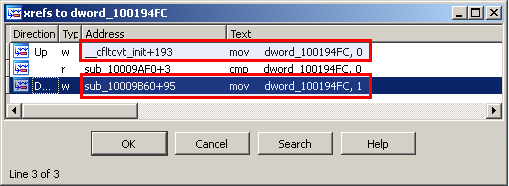
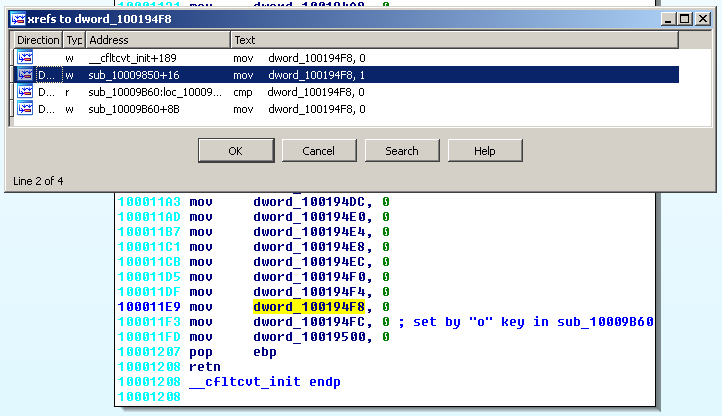
Cross references show that dword_100194FC is set to:
- 0 in __cfltcvt_init
- 1 in sub_10009B60
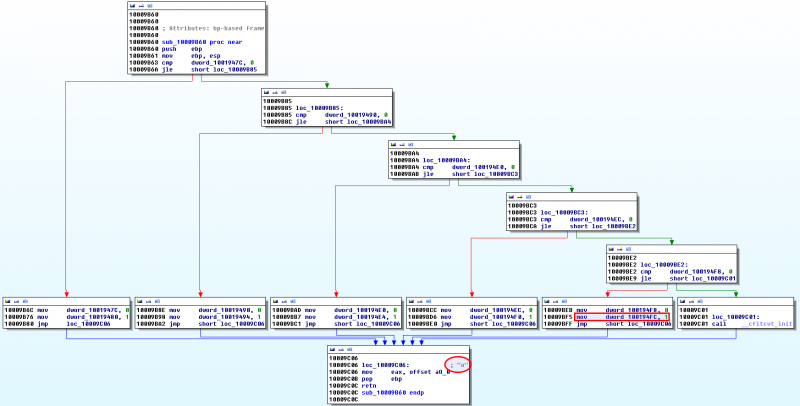
dword_100194FC is set to 1 by the "o" key
Looking at sub_10009B60 at offset 0x10009B60 shows that dword_100194FC is set when the "o" key is pressed.
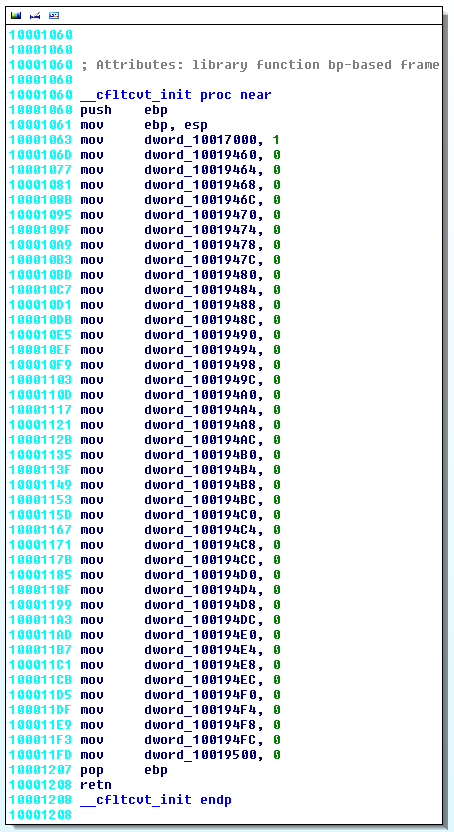
__cfltcvt_init (offset 0x10001060)
This function seems to initialize variables:
We already know that dword_100194FC is set to 1 by the "o" key. Let's check cross references for the other variables.
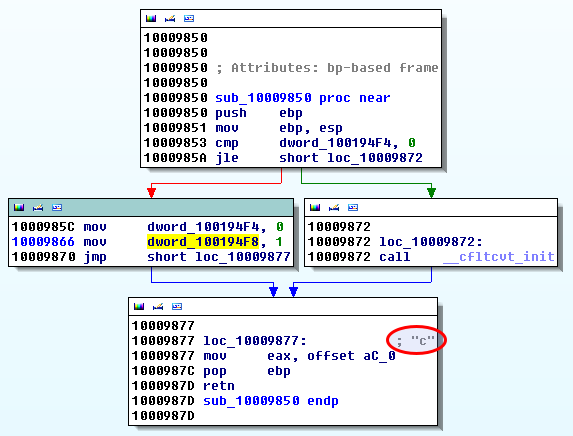
Now, let's see where dword_100194F8 is set to 1. Cross references show that it is set to 1 in sub_10009850.
And it correspond to the "c" key:
The solution
At the end, we have:
.text:10001060 __cfltcvt_init proc near
.text:10001060 push ebp
.text:10001061 mov ebp, esp
.text:10001063 mov dword_10017000, 1
.text:1000106D mov dword_10019460, 0 ; set to 1 by "l" in sub_10009AA0
.text:10001077 mov dword_10019464, 0 ; set to 1 by "0" in sub_10009440
.text:10001081 mov dword_10019468, 0 ; set to 1 by "g" in sub_10009990
.text:1000108B mov dword_1001946C, 0 ; set to 1 by "g" in sub_10009990
.text:10001095 mov dword_10019470, 0 ; set to 1 by "i" in sub_10009A30
.text:1000109F mov dword_10019474, 0 ; set to 1 by "n" in sub_10009B10
.text:100010A9 mov dword_10019478, 0 ; set to 1 by "g" in sub_10009990
.text:100010B3 mov dword_1001947C, 0 ; set to 1 by "d" in sub_10009880
.text:100010BD mov dword_10019480, 0 ; set to 1 by "o" in sub_10009B60
.text:100010C7 mov dword_10019484, 0 ; set to 1 by "t" in sub_10009CD0
.text:100010D1 mov dword_10019488, 0 ; set to 1 by "u" in sub_10009D80
.text:100010DB mov dword_1001948C, 0 ; set to 1 by "r" in sub_10009C30
.text:100010E5 mov dword_10019490, 0 ; set to 1 by "d" in sub_10009880
.text:100010EF mov dword_10019494, 0 ; set to 1 by "o" in sub_10009B60
.text:100010F9 mov dword_10019498, 0 ; set to 1 by "t" in sub_10009CD0
.text:10001103 mov dword_1001949C, 0 ; set to 1 by "5" in sub_100094D0
.text:1000110D mov dword_100194A0, 0 ; set to 1 by "t" in sub_10009CD0
.text:10001117 mov dword_100194A4, 0 ; set to 1 by "r" in sub_10009C30
.text:10001121 mov dword_100194A8, 0 ; set to 1 by "0" in sub_10009440
.text:1000112B mov dword_100194AC, 0 ; set to 1 by "k" in sub_10009A70
.text:10001135 mov dword_100194B0, 0 ; set to 1 by "e" in sub_10009910
.text:1000113F mov dword_100194B4, 0 ; set to 1 by "5" in sub_100094D0
.text:10001149 mov dword_100194B8, 0 ; set to 1 by "a" in sub_100097D0
.text:10001153 mov dword_100194BC, 0 ; set to 1 by "t" in sub_10009CD0
.text:1000115D mov dword_100194C0, 0 ; set to 1 by "f" in sub_10009960
.text:10001167 mov dword_100194C4, 0 ; set to 1 by "l" in sub_10009AA0
.text:10001171 mov dword_100194C8, 0 ; set to 1 by "a" in sub_100097D0
.text:1000117B mov dword_100194CC, 0 ; set to 1 by "r" in sub_10009C30
.text:10001185 mov dword_100194D0, 0 ; set to 1 by "e" in sub_10009910
.text:1000118F mov dword_100194D4, 0 ; set to 1 by "d" in sub_10009880
.text:10001199 mov dword_100194D8, 0 ; set to 1 by "a" in sub_100097D0
.text:100011A3 mov dword_100194DC, 0 ; set to 1 by "s" in sub_10009CA0
.text:100011AD mov dword_100194E0, 0 ; set to 1 by "h" in sub_10009A00
.text:100011B7 mov dword_100194E4, 0 ; set to 1 by "o" in sub_10009B60
.text:100011C1 mov dword_100194E8, 0 ; set to 1 by "n" in sub_10009B10
.text:100011CB mov dword_100194EC, 0 ; set to 1 by "d" in sub_10009880
.text:100011D5 mov dword_100194F0, 0 ; set to 1 by "o" in sub_10009B60
.text:100011DF mov dword_100194F4, 0 ; set to 1 by "t" in sub_10009CD0
.text:100011E9 mov dword_100194F8, 0 ; set to 1 by "c" in sub_10009850
.text:100011F3 mov dword_100194FC, 0 ; set to 1 by "o" key in sub_10009B60
.text:100011FD mov dword_10019500, 0
.text:10001207 pop ebp
.text:10001208 retn
.text:10001208 __cfltcvt_init endp
which leads to:
l0ggingdoturdot5tr0ke5atflaredashondotcom
Replacing the keywords "dot", "at", "dash" by the characters, we have:
$ echo "l0ggingdoturdot5tr0ke5atflaredashondotcom" | sed "s/dot/./g; s/at/@/; s/dash/-/" [email protected]
Comments
Keywords: reverse-engineering challenge flare fireeye pdf shellcode