Edb2ade8bca0a6b82b9d160ca40db8e5
Jump to navigation
Jump to search
Malware identification
File Identification
| MD5 | edb2ade8bca0a6b82b9d160ca40db8e5 |
|---|---|
| SHA1 | 8f78a243858d0a9a5278bd06a438023e78ba8168 |
| SHA256 | 155844dc303bae687c4a026a6d0c1e490f8284172c01e1420037144769436358 |
| ssdeep | 3072:mH8SUYJOa8S60iW05ciuQEe7O4XyVnYmpLzlplfi1eFKuPGtBJ0:mX8a8S60ecidEei4C282e8UGO |
| imphash | 22deaa3e5166e3019a02358581c9a9ee |
| File size | 190.5 KB ( 195,025 bytes ) |
| File type | Win32 EXE |
| Magic literal | PE32 executable for MS Windows (GUI) Intel 80386 32-bit |
| TrID |
|
Antivirus detection
| Antivirus | Result | Update |
|---|---|---|
| AVG | IRC/BackDoor.SdBot.TQF | 20140211 |
| Ad-Aware | IRC-Worm.Generic.5607 | 20140212 |
| Agnitum | Worm.SdBot!Iq8CvYNv5fs | 20140211 |
| AhnLab-V3 | Win32/IRCBot.worm.variant | 20140211 |
| AntiVir | TR/Crypt.XPACK.Gen | 20140212 |
| Avast | Win32:PackBot-N [Trj] | 20140212 |
| Baidu-International | Backdoor.Win32.PackBot.ARd | 20140212 |
| BitDefender | IRC-Worm.Generic.5607 | 20140212 |
| Bkav | W32.Clodff8.Trojan.d1da | 20140211 |
| ByteHero | Virus.Win32.Heur.l | 20140212 |
| CAT-QuickHeal | (Suspicious) - DNAScan | 20140212 |
| CMC | Generic.Win32.edb2ade8bc!MD | 20140211 |
| Commtouch | W32/Sdbot.JVBC-7466 | 20140212 |
| Comodo | Backdoor.IRC.SdBot | 20140212 |
| DrWeb | Win32.HLLW.MyBot.based | 20140212 |
| ESET-NOD32 | IRC/SdBot | 20140212 |
| Emsisoft | IRC-Worm.Generic.5607 (B) | 20140212 |
| F-Prot | W32/Sdbot.OEY | 20140211 |
| F-Secure | IRC-Worm.Generic.5607 | 20140212 |
| Fortinet | W32/SDBot.ALE!tr.bdr | 20140212 |
| GData | IRC-Worm.Generic.5607 | 20140212 |
| Ikarus | Backdoor.Win32.PackBot | 20140212 |
| Jiangmin | Backdoor/SdBot.cnu | 20140212 |
| K7AntiVirus | Riskware ( 8b2b4a030 ) | 20140211 |
| K7GW | Backdoor ( 0000263e1 ) | 20140211 |
| Kaspersky | Backdoor.Win32.PackBot.j | 20140212 |
| Kingsoft | Win32.Hack.SdBot.al.(kcloud) | 20140212 |
| McAfee | W32/Sdbot.worm.gen.h | 20140212 |
| McAfee-GW-Edition | W32/Sdbot.worm.gen.h | 20140212 |
| MicroWorld-eScan | IRC-Worm.Generic.5607 | 20140212 |
| Microsoft | Backdoor:Win32/IRCbot | 20140212 |
| NANO-Antivirus | Trojan.Win32.PackBot.fpld | 20140212 |
| Norman | Troj_Generic.EEAXQ | 20140212 |
| Panda | Trj/Genetic.gen | 20140211 |
| Qihoo-360 | Win32/Worm.IRC.360 | 20140212 |
| Rising | PE:Backdoor.PackBot.ag!1074796706 | 20140211 |
| Sophos | W32/Tilebot-DC | 20140212 |
| Symantec | W32.HLLW.Gaobot | 20140212 |
| TheHacker | Backdoor/SdBot.ale | 20140212 |
| TotalDefense | Win32/Petribot.LR | 20140212 |
| TrendMicro | WORM_SDBOT.DFV | 20140212 |
| TrendMicro-HouseCall | WORM_SDBOT.DFV | 20140212 |
| VBA32 | OScope.Backdoor.Sdbot.Cgen | 20140211 |
| VIPRE | Trojan.Win32.Generic!BT | 20140212 |
| ViRobot | Backdoor.Win32.PackBot.195025 | 20140212 |
| nProtect | Worm/W32.Agent.195025 | 20140212 |
| ClamAV | - | 20140212 |
| Malwarebytes | - | 20140212 |
| SUPERAntiSpyware | - | 20140212 |
Protections
Packer
Packer identification
- PEiD identifies that the malware is packed with "SVKP 1.3x -> Pavol Cerven"
- The strings function also confirms this assumption
- At last, pescanner also shows a section named svkp:
Sections
================================================================================
Name VirtAddr VirtSize RawSize Entropy
--------------------------------------------------------------------------------
0x1000 0x16000 0xa9de 7.995945 [SUSPICIOUS]
0x17000 0x2000 0x86e 7.908491 [SUSPICIOUS]
0x19000 0x68000 0x3352 7.985942 [SUSPICIOUS]
.svkp 0x81000 0x21000 0x20dd1 7.401531 [SUSPICIOUS]
Unpacking
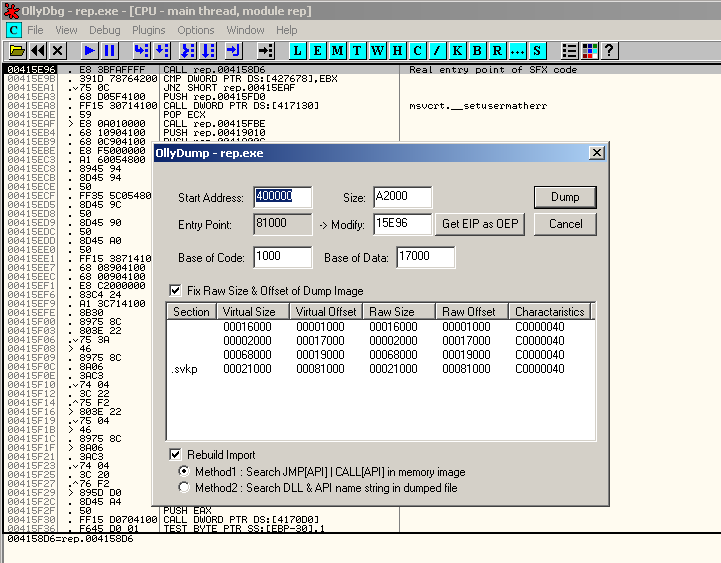
Using the SFX option in OllyDbg, we find the OEP at 0x415E96:
Detection of monitoring tools
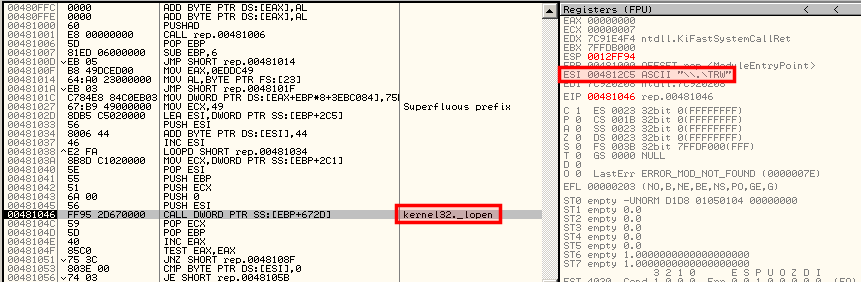
The analysis of the malware into OllyDbg confirms that it checks for the presence of various monitoring tools via the lopen function:
- \\.\TRW
- \\.\SICE
- \\.\NTICE
- \\.\FILEVXD
- \\.\FILEMON
- \\.\REGVXD
- \\.\REGMON
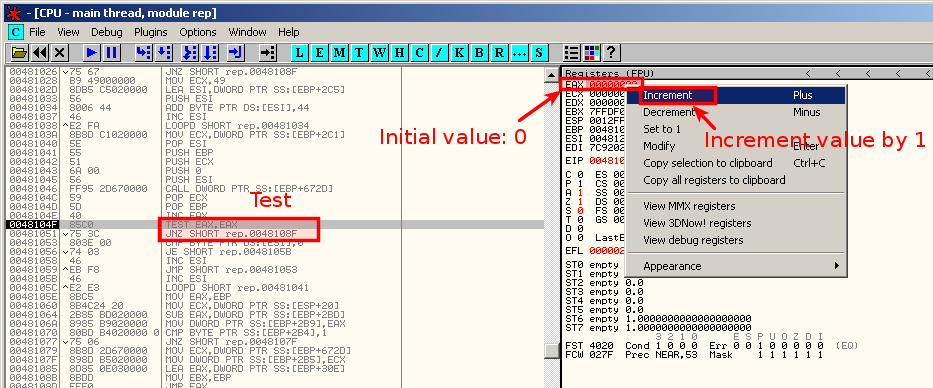
By manually modifying the value of EAX to a non-zero value:
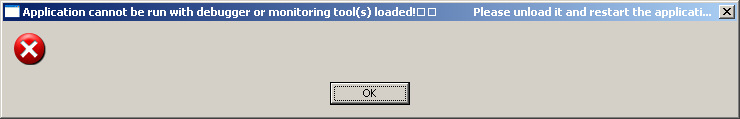
... and running the program (F9), the following error window appears:
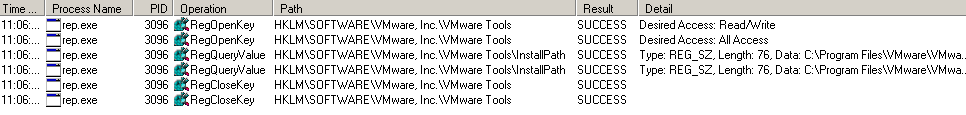
Detection of VMware registry keys
Analysis #1: with VMware registry keys
- The malware detects the presence of VMware registry keys:
- It creates and removes a file named C\Documents and Settings\%user%\Local Settings\Temp\removeMe3186.bat
@echo off :Repeat del "C:\Documents and Settings\malware\Bureau\rep.exe">nul if exist "C:\Documents and Settings\malware\Bureau\rep.exe" goto Repeat del "%0"
- It creates C:\WINDOWS\system32\SVKP.sys
- It removes the initial rep.exe that has been started from the Desktop
Analysis #2: without VMware registry keys
Without VMware registry keys (HKLM\Software\VMware Inc), the specimen behaves differently:
- No longer removed from the desktop
- Copies itself to C:\WINDOWS\win32ssr.exe
- Launches Win32Sr service:
| ImagePath | C:\WINDOWS\win32ssr.exe |
|---|---|
| DisplayName | Win32Sr |
| ObjectName | LocalSystem |
| FailureActions | 0A 00 00 00 00 00 00 00 00 00 00 00 01 00 00 00 00 00 00 00 01 00 00 00 B8 0B 00 00 |
| Description | Platform SDK Enviroment |
- (Still creates C:\WINDOWS\system32\SVKP.sys)
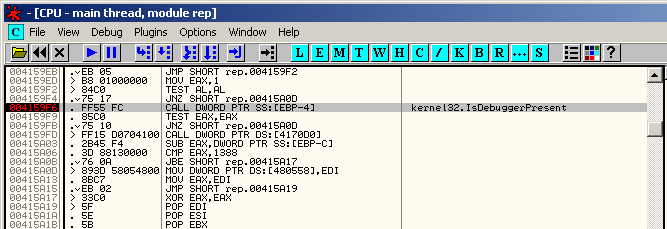
IsDebuggerPresent
Static analysis
Packed version
Strings
There are some interesting strings:
.svkp [SNIP] Application cannot be run with debugger or monitoring tool(s) loaded! Please unload it and restart the application. [SNIP] KERNEL32.DLL USER32.DLL SHELL32.DLL _lopen ExitProcess MessageBoxA ShellExecuteA [SNIP]
From the strings, we can suspect that the malware:
- is packed with SVKP
- will be likely to detect debugging and monitoring tools
IAT
| DLL | Function |
|---|---|
| KERNEL32.DLL |
|
| USER32.DLL |
|
| SHELL32.DLL |
|
Unpacked version
IAT
Once unpacked, following imports are revealed:
| DLL | Function |
|---|---|
| OLEAUT32.DLL |
|
| USER32.DLL |
|
| msvcrt.dll |
|