OfficeMalScanner/MalHost-Setup
Jump to navigation
Jump to search
| You are here: | MalHost-Setup
|
Description
MalHost-Setup will dump an executable embedded in an Office document. You can identify the offset with OfficeMalScanner, using scan debug.
Usage
Syntax
Usage: MalHost-Setup <inputfile> <outputfile> <offset of EP to shellcode in hex> <wait>
Options
- inputfile
- Malicious file to be analyzed
- outputfile
- Name of the file that will be output by MalHost-Setup
- offset
- Offset of starting code
- wait
- Means an execution halt (0xEB 0xFE patch) at shellcode start.
- Useful if you want to attach a debugger for tracing the shellcode execution.
- After attaching the debugger you need to repatch the original bytes.
- The original bytes and the shellcode startaddr will appear on the console.
Examples
Simple extraction
You can simply extract the embedded executable with the below command:
C:\tools\OfficeMalScanner>MalHost-Setup.exe \malware\TestYourMind.ppt \malware\out.exe 0x90c53 +------------------------------------------+ | MalHost-Setup v0.12 | | Frank Boldewin / www.reconstructer.org | +------------------------------------------+ [*] Opening file \malware\TestYourMind.ppt [*] Filesize is 631296 (0x9a200) Bytes [*] Creating Malhost file now... [*] Writing 690688 bytes [*] Done!
Using this method, you will need to step over in the debugger until you find the shellcode. It's easier to use the wait option.
Using wait
Using the wait option, MalHost-Setup will patch the extracted executable so that there will be an infinite loop at the beginning of the shellcode:
C:\tools\OfficeMalScanner>MalHost-Setup.exe \malware\TestYourMind.ppt \malware\out.exe 0x90c53 wait +------------------------------------------+ | MalHost-Setup v0.12 | | Frank Boldewin / www.reconstructer.org | +------------------------------------------+ [*] WAIT option chosen [*] Opening file \malware\TestYourMind.ppt [*] Filesize is 631296 (0x9a200) Bytes [*] Original bytes [0xe8 0x00] at offset 0x90c53 [*] Original bytes are patched for debugging now [0xeb 0xfe] [*] Creating Malhost file now... [*] Writing 690688 bytes [*] Done!
Once you have exported the out.exe malicious code:
- either open it in OllyDbg (File > Open) and run the executable (F9), then pause it (F12)
- or start out.exe and attach OllyDbg to the running process (File > Attach). Then go to "Debug > Execute till user code" (ALT+F9).
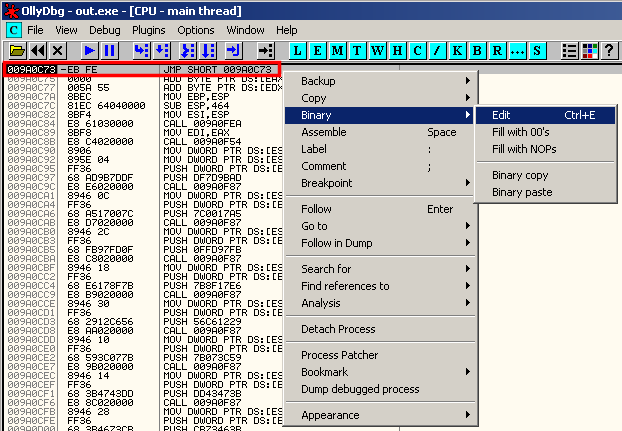
The debugger will stop at the infinite loop (patched code: 0xeb 0xfe):
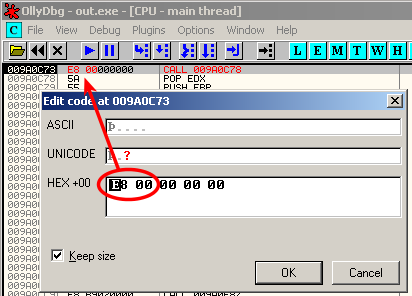
You'll need to patch the executable back to the original value (0xe8 0x00):