PEB-Process-Environment-Block/NtGlobalFlag
| You are here | BeingDebugged
|
Description
The PEB has a field called NtGlobalFlag (offset 0x68) which programs can challenge to identify whether they are being debugged. Normally, when a process is not being debugged, the NtGlobalFlag field contains the value 0x0. When the process is being debugged, the field will usually contain the value 0x70 which indicates that the following flags are set:
| Flag | Value |
|---|---|
| FLG_HEAP_ENABLE_TAIL_CHECK | 0x10 |
| FLG_HEAP_ENABLE_FREE_CHECK | 0x20 |
| FLG_HEAP_VALIDATE_PARAMETERS | 0x40 |
| Total | 0x70 |
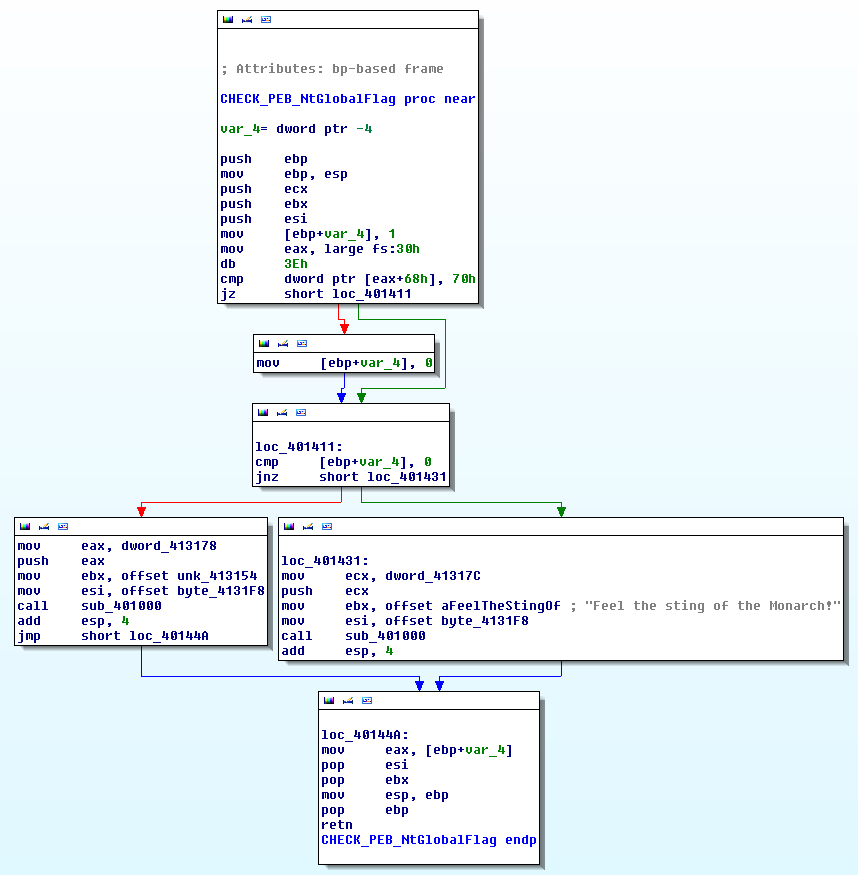
Here is an example of such detection:
Overcome the NtGlobalFlag detection
Are are some ways to thwart the detection:
- Manually change the value of the flags (FLG_HEAP_ENABLE_TAIL_CHECK, FLG_HEAP_ENABLE_FREE_CHECK, FLG_HEAP_VALIDATE_PARAMETERS)
- In OllyDbg, use a hide-debug plugin
- In WinDbg, start the program with the debug heap disabled (windbg -hd program.exe)
Below is an example that depicts how to overcome this check manually. Given the below code:
.text:00403594 64 A1 30 00 00 00 mov eax, large fs:30h ; PEB struct loaded into EAX
.text:0040359A db 3Eh ; IDA Pro display error (the byte is actually used in the next instruction)
.text:0040359A 3E 8B 40 68 mov eax, [eax+68h] ; NtGlobalFlag (offset 0x68 relative to PEB) saved to EAX
.text:0040359E 83 E8 70 sub eax, 70h ; Value 0x70 corresponds to all flags on (FLG_HEAP_ENABLE_TAIL_CHECK, FLG_HEAP_ENABLE_FREE_CHECK, FLG_HEAP_VALIDATE_PARAMETERS)
.text:004035A1 89 85 D8 E7 FF FF mov [ebp+var_1828], eax
.text:004035A7 83 BD D8 E7 FF FF 00 cmp [ebp+var_1828], 0 ; Check whether 3 debug flags were on (result of substraction should be 0 if debugged)
.text:004035AE 75 05 jnz short loc_4035B5 ; No debugger, program continues...
.text:004035B0 E8 4B DA FF FF call s_selfDelete ; ...else, malware deleted
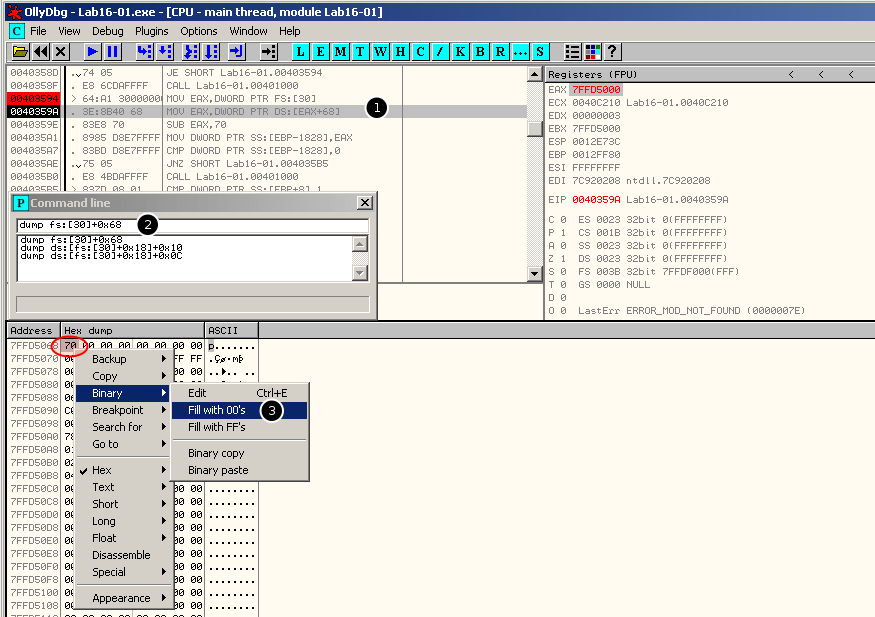
In OllyDbg, set a breakpoint at offset 0x40359A and run the malware until it reaches the breakpoint. Then open the CommandLine plugin and dump the content of the NtGlobalFlag with dump fs:[30]+0x68:
Replace the initial value (0x70 means that the process is being debugged) with 0x00 by right clicking on the byte and selecting Binary > Fill with 00's.
Comments
Keywords: anti-reverse anti-debug