PEB-Process-Environment-Block/ProcessHeap
| You are here | ProcessHeap
|
Description
This flag (offset 0x18) can be used as an anti-debugging technique. This first heap contains a header with fields (ForceFlags, Flags) used to tell the kernel whether the heap was created within a debugger.
Below are the offsets (relative to ProcessHeap) for Windows XP and Windows 7.
| Field | Size | Offset relative to ProcessHeap (Windows XP) |
Offset relative to ProcessHeap (Windows 7) |
|---|---|---|---|
| ForceFlags | DWORD | 0x10 | 0x44 |
| Flags | DWORD | 0x0C | 0x40 |
Here is the assembly that checks for this value:
mov eax, large fs:30h ; PEB saved to EAX
mov eax, dword ptr [eax+18h] ; ProcessHeap (offset 0x18 relative to PEB) saved to EAX
cmp dword ptr ds:[eax+10h], 0 ; Check whether ForceFlags field (offset 0x10 relative to ProcessHeap) is 0
jne DebuggerDetected ; If previous test returned non zero, debugger is present

Thwart ProcessHeap check
To thwart ProcessHeap checks, you can:
- Manually change the ProcessHeap flag
- In OllyDbg, use a hide-debug plugin (e.g. HideOD)
- In WinDbg, start the program with the debug heap disabled (windbg -hd program.exe)
Below is an example that depicts how to manually update the flags. Given the following code:
.text:00403573 64 A1 30 00 00 00 mov eax, large fs:30h ; PEB struct loaded into EAX
.text:00403579 8B 40 18 mov eax, [eax+18h] ; ProcessHeap (offset 0x18 relative to PEB) savec to EAX
.text:0040357C db 3Eh ; IDA Pro display error (notice that 0x3E is actually used as the 1st byte in the below instruction)
.text:0040357C 3E 8B 40 10 mov eax, [eax+10h] ; ForceFlags (offset 0x10 relative to ProcessHeap) saved to EAX
.text:00403580 89 85 DC E7 FF FF mov [ebp+var_1824], eax ;
.text:00403586 83 BD DC E7 FF FF 00 cmp [ebp+var_1824], 0 ; Check whether ForceFlags set to 0
.text:0040358D 74 05 jz short loc_40 ; If ForceFlags=0, no debugger...
.text:0040358F E8 6C DA FF FF call sub_401000 ; ...else, debugger detected. Malware deleted
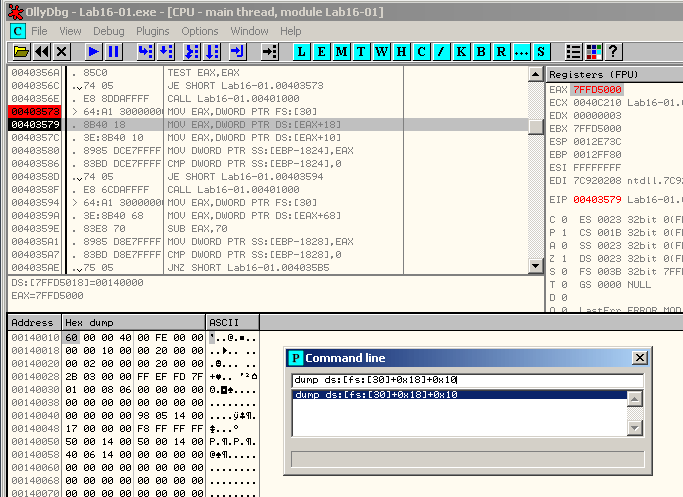
Open the malware in OllyDbg, set a breakpoint to offset 0x403579 and run the malware till it reaches the breakpoint. Then use the CommandLine plugin to reach the PEB.ProcessHeap.ForceFlags flag with the following command:
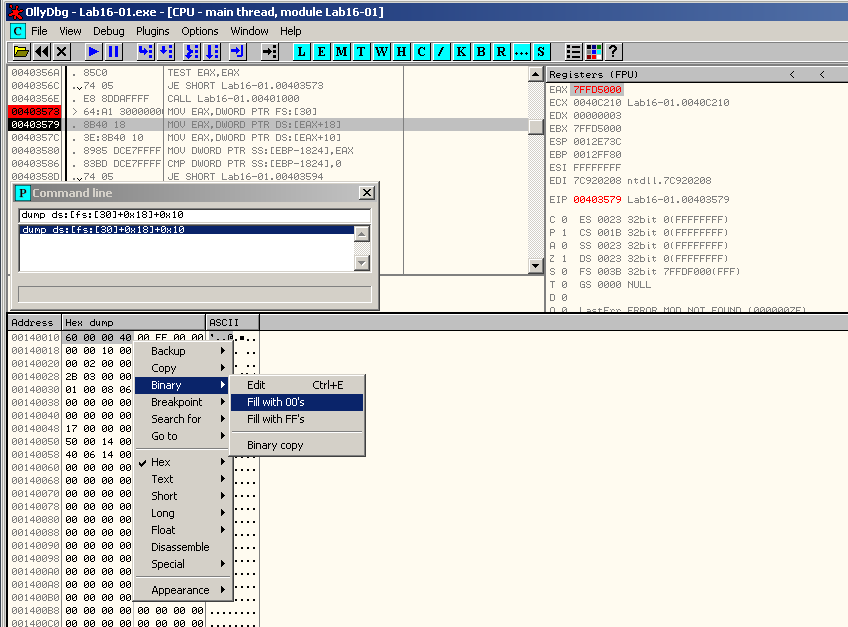
Select the 4 bytes of the ForceFlags flag, right click and select Binary > Fill with 00's:
Comments
Keywords: peb Process Environment Block processheap forceflags flags dump ds:[fs:[30]+0x18]+0x10 structure