Volatility/From-AlienVault-SIEM-alarms-to-identification-of-infected-files-on-the-compromised-machine
| You are here | From AlienVault SIEM alarms to the identification of infected files on the compromised machine
|
Description
This article shows how to dig into the memory dump using volatility to identify malware found on a Windows XP machine, initially detected with the AlienVault SIEM.
Steps
SIEM alarms
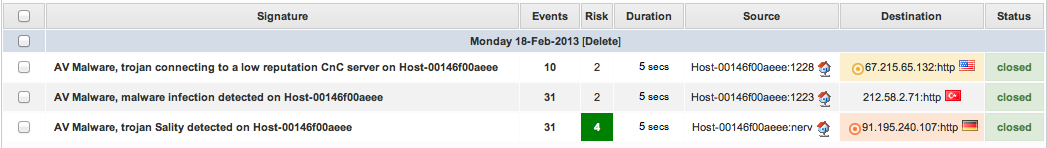
This example shows how I identified the infected files on a compromised machine from AlienVault SIEM alarms.
Here are the alarms that triggered:
Basically 2 types of payloads were available in the SIEM console:
GET /images/logos.gif?163bb6=4371234 HTTP/1.1 User-Agent: Opera/8.89 (Windows NT 6.0; U; en) Host: www.serdarsaracoglu.com Cache-Control: no-cache GET /?url=vanivilashospital%2Ecom%2Fimages%2Flogos%2Egif%3F163230%3D2909280 HTTP/1.1 User-Agent: Opera/8.89 (Windows NT 6.0; U; en) Connection: Keep-Alive Cache-Control: no-cache Host: guidetest.a.id.opendns.com
These events were triggered by following signatures:
File: emerging-trojan.rules
Rule: alert tcp $HOME_NET any -> $EXTERNAL_NET $HTTP_PORTS
msg: "ET TROJAN Sality - Fake Opera User-Agent (Opera/8.89)"
flow: established,to_server
content: "GET"
http_method:
content: "User-Agent|3a| Opera/8.89 (Windows NT 6.0|3b| U|3b| en)|0d0a|"
http_header:
reference: url,www.spywareremove.com/removeTrojanDownloaderSalityG.html
reference: url,www.microsoft.com/security/portal/beta/Threat/Encyclopedia/Entry.aspx?Name=Virus%3AWin32%2FSality.AM
reference: url,doc.emergingthreats.net/2009530
classtype: trojan-activity
sid: 2009530
rev: 4
File: emerging_pro-trojan.rules
Rule: alert tcp $HOME_NET any -> $EXTERNAL_NET $HTTP_PORTS
msg: "ETPRO TROJAN Virus.Win32.Sality.baka Checkin"
flow: to_server,established
content: ".gif?"
http_uri:
pcre: "/\x2egif\x3f([0-9a-f])+?\x3d\x2e?\d+?$/U"
content: "User-Agent|3a| Opera/8.89"
http_header:
reference: md5,ef7e7ddd7efd03f5d3aa5e4d1f806ada
reference: md5,5503babd8f756cf0b54ca96d112a2212
classtype: trojan-activity
sid: 2805494
rev: 1
Perform memory dump
In the meantime, I have dumped the memory of the machine (hopefully a virtual machine ;-) using mdd_1.3.exe.
This can be also performed remotely, using PsExec:
C:\> psexec \\192.168.1.27 -u administrator -p password -c mdd_1.3.exe -q -o D:\image.img
PS: You can also use Dumpit but I haven't found a way to use it remotely because of the interactive menu (you have to validate the menu from the console Dumpit is started from and there is no option (i.e. -y) to force the acceptance).
Process identification
Let's identify processes responsible for the connections seen in the SIEM
$ python vol.py -f ~/memdump/infected.img connscan | egrep "67\.215|212\.58|91\.195" Volatile Systems Volatility Framework 2.2 0x01e20ba0 192.168.1.27:1298 67.215.65.132:31960 2944 0x01e6b008 192.168.1.27:1226 91.195.240.107:80 532 0x01eac008 192.168.1.27:1223 212.58.2.71:80 532 0x0214b140 192.168.1.27:1262 67.215.65.132:31960 2944 0x0415b140 192.168.1.27:1262 67.215.65.132:31960 2944 0x09a68ba0 192.168.1.27:1298 67.215.65.132:31960 2944 0x14ee7ba0 192.168.1.27:1298 67.215.65.132:31960 2944 0x15eb4008 192.168.1.27:1223 212.58.2.71:80 532
The connscan plugin confirms that there are 2 processes (PID: 532 and 2944) that are responsible of the malicious traffic seen in the alarms. What are these 2 processes?
$ python vol.py -f ~/memdump/infected.img pslist | egrep "532|2944" Volatile Systems Volatility Framework 2.2 0x81f015d0 vmtoolsd.exe 532 272 38 563 0 0 2013-02-18 20:54:52 0x81cbdb20 netsh.exe 3860 532 0 -------- 0 0 2013-02-18 21:15:17 2013-02-18 21:15:18 0x81c75020 notepad.exe 3052 532 0 -------- 0 0 2013-02-18 21:15:20 2013-02-18 21:15:20
Very interesting: we can guess that process 532 is hiding in vmtoolsd.exe (PID532). And PID 2944 is hidden (confirmed by the psxview plugin)
$ python vol.py -f ~/memdump/infected.img psxview Volatile Systems Volatility Framework 2.2 Offset(P) Name PID pslist psscan thrdproc pspcdid csrss ---------- -------------------- ------ ------ ------ -------- ------- ----- [REMOVED] 0x023a6da0 mcrshl.exe 2944 False True False True True [REMOVED] 0x151b6da0 mcrshl.exe 2944 False True False False False [REMOVED]
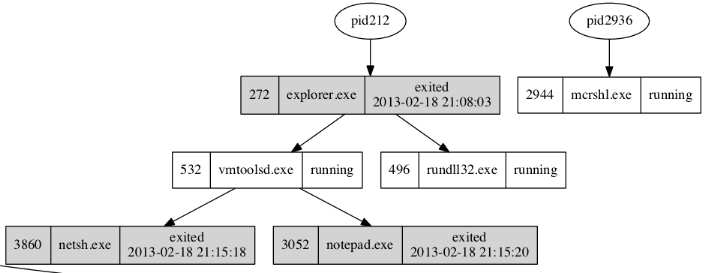
To visualize the processes and dependencies, you can install Graphviz and generate an image as follows:
$ python vol.py -f ~/memdump/infected.img psscan --output=dot --output-file=output/test.dot $ dot -Tpng test.dot -o test.png
Here is an extract:
PID 532: vmtoolsd.exe
Yara plugin
Obviously here, the presence of the strings "logos.gif" and "Opera/8.89" can be good indicators for a Yara signature:
$ cat sality.yara
rule sality
{
strings:
$a = "logos.gif"
$b = "Opera/8.89"
condition:
any of them
}
Time to identify processes containing these strings:
$ python vol.py -f ~/memdump/infected.img yarascan -y ~/pentest/yara-sigs/sality.yara Volatile Systems Volatility Framework 2.2 Rule: sality Owner: Process vmtoolsd.exe Pid 532 0x031591a7 6c 6f 67 6f 73 2e 67 69 66 00 68 74 74 70 3a 2f logos.gif.http:/ 0x031591b7 2f 77 77 77 2e 64 6f 67 75 73 2d 70 6c 61 73 74 /www.dogus-plast 0x031591c7 69 6b 2e 63 6f 6d 2f 6c 6f 67 6f 73 2e 67 69 66 ik.com/logos.gif 0x031591d7 00 68 74 74 70 3a 2f 2f 6d 61 63 65 64 6f 6e 69 .http://macedoni [REMOVED] Owner: Process vmtoolsd.exe Pid 532 0x031592ad 6c 6f 67 6f 73 2e 67 69 66 00 00 00 00 00 00 00 logos.gif....... 0x031592bd 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0x031592cd 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0x031592dd 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ Rule: sality Owner: Process vmtoolsd.exe Pid 532 0x031672c8 4f 70 65 72 61 2f 38 2e 38 39 20 28 57 69 6e 64 Opera/8.89.(Wind 0x031672d8 6f 77 73 20 4e 54 20 36 2e 30 3b 20 55 3b 20 65 ows.NT.6.0;.U;.e 0x031672e8 6e 29 00 00 4d 50 52 00 4e 74 51 75 65 72 79 53 n)..MPR.NtQueryS 0x031672f8 79 73 74 65 6d 49 6e 66 6f 72 6d 61 74 69 6f 6e ystemInformation [REMOVED] Rule: sality Owner: Process vmtoolsd.exe Pid 532 0x02073291 6c 6f 67 6f 73 2e 67 69 66 00 27 40 00 00 00 00 logos.gif.'@.... 0x020732a1 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0x020732b1 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0x020732c1 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ Rule: sality Owner: Process vmtoolsd.exe Pid 532 0x0457e8de 6c 6f 67 6f 73 2e 67 69 66 3f 31 36 33 62 62 36 logos.gif?163bb6 0x0457e8ee 3d 34 33 37 31 32 33 34 00 00 00 00 00 00 00 00 =4371234........ 0x0457e8fe 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0x0457e90e 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ [REMOVED]
Use Malfind to dump the processes
What does Malfind say about this process?
$ python vol.py -f ~/memdump/infected.img malfind -p 532 -D output/ Volatile Systems Volatility Framework 2.2 Process: vmtoolsd.exe Pid: 532 Address: 0x3140000 Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE Flags: CommitCharge: 4147, MemCommit: 1, PrivateMemory: 1, Protection: 6 0x03140000 4d 5a 90 00 03 00 00 00 04 00 00 00 ff ff 00 00 MZ.............. 0x03140010 b8 00 00 00 00 00 00 00 40 00 00 00 00 00 00 00 ........@....... 0x03140020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0x03140030 00 00 00 00 00 00 00 00 00 00 00 00 e0 00 00 00 ................ 0x3140000 4d DEC EBP 0x3140001 5a POP EDX 0x3140002 90 NOP 0x3140003 0003 ADD [EBX], AL 0x3140005 0000 ADD [EAX], AL 0x3140007 000400 ADD [EAX+EAX], AL 0x314000a 0000 ADD [EAX], AL 0x314000c ff DB 0xff 0x314000d ff00 INC DWORD [EAX] 0x314000f 00b800000000 ADD [EAX+0x0], BH 0x3140015 0000 ADD [EAX], AL 0x3140017 004000 ADD [EAX+0x0], AL 0x314001a 0000 ADD [EAX], AL 0x314001c 0000 ADD [EAX], AL 0x314001e 0000 ADD [EAX], AL 0x3140020 0000 ADD [EAX], AL 0x3140022 0000 ADD [EAX], AL 0x3140024 0000 ADD [EAX], AL 0x3140026 0000 ADD [EAX], AL 0x3140028 0000 ADD [EAX], AL 0x314002a 0000 ADD [EAX], AL 0x314002c 0000 ADD [EAX], AL 0x314002e 0000 ADD [EAX], AL 0x3140030 0000 ADD [EAX], AL 0x3140032 0000 ADD [EAX], AL 0x3140034 0000 ADD [EAX], AL 0x3140036 0000 ADD [EAX], AL 0x3140038 0000 ADD [EAX], AL 0x314003a 0000 ADD [EAX], AL 0x314003c e000 LOOPNZ 0x314003e 0x314003e 0000 ADD [EAX], AL Process: vmtoolsd.exe Pid: 532 Address: 0x2060000 Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE Flags: CommitCharge: 1, MemCommit: 1, PrivateMemory: 1, Protection: 6 0x02060000 e8 00 00 00 00 5d 81 ed 05 10 40 00 8d 85 2f 10 .....]....@.../. 0x02060010 40 00 50 6a 00 6a 00 ff 95 27 10 40 00 6a ff ff @.Pj.j...'[email protected].. 0x02060020 95 2b 10 40 00 eb f6 df e9 80 7c 46 24 80 7c 76 .+.@......|F$.|v 0x02060030 6d 74 6f 6f 6c 73 64 2e 65 78 65 4d 5f 35 33 32 mtoolsd.exeM_532 0x2060000 e800000000 CALL 0x2060005 0x2060005 5d POP EBP 0x2060006 81ed05104000 SUB EBP, 0x401005 0x206000c 8d852f104000 LEA EAX, [EBP+0x40102f] 0x2060012 50 PUSH EAX 0x2060013 6a00 PUSH 0x0 0x2060015 6a00 PUSH 0x0 0x2060017 ff9527104000 CALL DWORD [EBP+0x401027] 0x206001d 6aff PUSH -0x1 0x206001f ff952b104000 CALL DWORD [EBP+0x40102b] 0x2060025 ebf6 JMP 0x206001d 0x2060027 dfe9 FUCOMIP ST0, ST1 0x2060029 807c462480 CMP BYTE [ESI+EAX*2+0x24], 0x80 0x206002e 7c76 JL 0x20600a6 0x2060030 6d INS DWORD [ES:EDI], DX 0x2060031 746f JZ 0x20600a2 0x2060033 6f OUTS DX, DWORD [ESI] 0x2060034 6c INS BYTE [ES:EDI], DX 0x2060035 7364 JAE 0x206009b 0x2060037 2e657865 JS 0x20600a0 ;NOT TAKEN 0x206003b 4d DEC EBP 0x206003c 5f POP EDI 0x206003d 35 DB 0x35 0x206003e 3332 XOR ESI, [EDX] Process: vmtoolsd.exe Pid: 532 Address: 0x2050000 Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE Flags: CommitCharge: 2, MemCommit: 1, PrivateMemory: 1, Protection: 6 0x02050000 e8 00 00 00 00 5d 81 ed 05 10 40 00 58 2d a0 1a .....][email protected].. 0x02050010 00 00 89 85 43 12 40 00 80 bd 73 27 40 00 00 75 [email protected]'@..u 0x02050020 19 c7 85 3a 14 40 00 7b 1d 80 7c c7 85 29 14 40 ...:.@.{..|..).@ 0x02050030 00 40 ae 80 7c e9 82 00 00 00 33 db 64 67 8b 1e .@..|.....3.dg.. 0x2050000 e800000000 CALL 0x2050005 0x2050005 5d POP EBP 0x2050006 81ed05104000 SUB EBP, 0x401005 0x205000c 58 POP EAX 0x205000d 2da01a0000 SUB EAX, 0x1aa0 0x2050012 898543124000 MOV [EBP+0x401243], EAX 0x2050018 80bd7327400000 CMP BYTE [EBP+0x402773], 0x0 0x205001f 7519 JNZ 0x205003a 0x2050021 c7853a1440007b1d807c MOV DWORD [EBP+0x40143a], 0x7c801d7b 0x205002b c7852914400040ae807c MOV DWORD [EBP+0x401429], 0x7c80ae40 0x2050035 e982000000 JMP 0x20500bc 0x205003a 33db XOR EBX, EBX 0x205003c 64 DB 0x64 0x205003d 67 DB 0x67 0x205003e 8b DB 0x8b 0x205003f 1e PUSH DS
Let's scan the 3 files generated by the malfind plugin:
$ ls -lh total 33200 -rw-r--r-- 1 sebastiendamaye staff 8,0K 23 fév 23:14 process.0x81f015d0.0x2050000.dmp -rw-r--r-- 1 sebastiendamaye staff 4,0K 23 fév 23:14 process.0x81f015d0.0x2060000.dmp -rw-r--r-- 1 sebastiendamaye staff 16M 23 fév 23:14 process.0x81f015d0.0x3140000.dmp
- process.0x81f015d0.0x2050000.dmp: Virustotal 9/46 (Win32.Sality.PP)
- process.0x81f015d0.0x2060000.dmp: Virustotal 8/46 (Win32.Sality.Injected.A)
- process.0x81f015d0.0x3140000.dmp: Virustotal 13/45 (Win32:Sality-GR)
PID 2944: mcrshl.exe
Dump process
Since PID 2944 is hidden, we have to dump it using the offset found with the psxview command:
Offset(P) Name PID pslist psscan thrdproc pspcdid csrss ---------- -------------------- ------ ------ ------ -------- ------- ----- 0x023a6da0 mcrshl.exe 2944 False True False True True 0x151b6da0 mcrshl.exe 2944 False True False False False
Let's dump the processes using the offset found above:
$ python vol.py -f ~/memdump/infected.img procexedump -o 0x151b6da0 -D output/ Volatile Systems Volatility Framework 2.2 Process(V) ImageBase Name Result ---------- ---------- -------------------- ------ ---------- ---------- -------------------- Error: Cannot acquire process AS $ python vol.py -f ~/memdump/infected.img procexedump -o 0x023a6da0 -D output/ Volatile Systems Volatility Framework 2.2 Process(V) ImageBase Name Result ---------- ---------- -------------------- ------ 0x821a6da0 0x00010000 mcrshl.exe OK: executable.2944.exe
Here are the results:
| PID | Name | Virustotal | Anubis | Description |
|---|---|---|---|---|
| 2944 | mcrshl.exe | link (7/46) | link | This process is known as McAfee MISP Shell and belongs to software McAfee SecurityCenter by McAfee (www.mcafee.com). However, McAfee was not installed on the machine. The virus was hiding under a fake antivirus! |
File location
The file is located in C:\WINDOWS\system32\:
$ python vol.py -f ~/memdump/infected.img dlllist -o 0x023a6da0 Volatile Systems Volatility Framework 2.2 ************************************************************************ mcrshl.exe pid: 2944 Command line : "C:\WINDOWS\system32\mcrshl.exe" Service Pack 3 Base Size Path ---------- ---------- ---- 0x00010000 0x30000 C:\WINDOWS\system32\mcrshl.exe 0x7c910000 0xb9000 C:\WINDOWS\system32\ntdll.dll 0x7c800000 0x106000 C:\WINDOWS\system32\kernel32.dll 0x7e390000 0x91000 C:\WINDOWS\system32\user32.dll 0x77ef0000 0x49000 C:\WINDOWS\system32\GDI32.dll 0x77da0000 0xac000 C:\WINDOWS\system32\advapi32.dll 0x77e50000 0x93000 C:\WINDOWS\system32\RPCRT4.dll 0x77fc0000 0x11000 C:\WINDOWS\system32\Secur32.dll 0x774a0000 0x13e000 C:\WINDOWS\system32\ole32.dll 0x77be0000 0x58000 C:\WINDOWS\system32\msvcrt.dll 0x76320000 0x1d000 C:\WINDOWS\system32\IMM32.DLL 0x770e0000 0x8b000 C:\WINDOWS\system32\oleaut32.dll 0x7c9d0000 0x825000 C:\WINDOWS\system32\SHELL32.dll 0x77f40000 0x76000 C:\WINDOWS\system32\SHLWAPI.dll 0x77390000 0x103000 C:\WINDOWS\WinSxS\x86_Microsoft.Windows.Common-Controls_6595b64144ccf1df_6.0.2600.6028_x-ww_61e65202\comctl32.dll 0x58b50000 0x9a000 C:\WINDOWS\system32\comctl32.dll 0x45180000 0x133000 C:\WINDOWS\system32\urlmon.dll 0x40b40000 0x1eb000 C:\WINDOWS\system32\iertutil.dll 0x404a0000 0xe6000 C:\WINDOWS\system32\WININET.dll 0x009f0000 0x9000 C:\WINDOWS\system32\Normaliz.dll 0x719f0000 0x17000 C:\WINDOWS\system32\WS2_32.dll 0x719e0000 0x8000 C:\WINDOWS\system32\WS2HELP.dll 0x71990000 0x40000 C:\WINDOWS\system32\mswsock.dll 0x62e40000 0x59000 C:\WINDOWS\system32\hnetcfg.dll 0x719d0000 0x8000 C:\WINDOWS\System32\wshtcpip.dll 0x77b50000 0x22000 C:\WINDOWS\system32\Apphelp.dll 0x77bd0000 0x8000 C:\WINDOWS\system32\VERSION.dll 0x74cd0000 0x1e000 C:\WINDOWS\system32\wshbth.dll 0x778e0000 0xf8000 C:\WINDOWS\system32\SETUPAPI.dll 0x76ed0000 0x27000 C:\WINDOWS\system32\DNSAPI.dll 0x76d10000 0x19000 C:\WINDOWS\system32\iphlpapi.dll 0x76cf0000 0x18000 C:\WINDOWS\system32\MPRAPI.dll 0x77c90000 0x32000 C:\WINDOWS\system32\ACTIVEDS.dll 0x76dc0000 0x25000 C:\WINDOWS\system32\adsldpc.dll 0x6fee0000 0x55000 C:\WINDOWS\system32\NETAPI32.dll 0x76f10000 0x2d000 C:\WINDOWS\system32\WLDAP32.dll 0x76ac0000 0x11000 C:\WINDOWS\system32\ATL.DLL 0x76e30000 0xe000 C:\WINDOWS\system32\rtutils.dll 0x71b50000 0x13000 C:\WINDOWS\system32\SAMLIB.dll 0x76f60000 0x8000 C:\WINDOWS\System32\winrnr.dll 0x76f70000 0x6000 C:\WINDOWS\system32\rasadhlp.dll
Persistence
Let's dump the hivelist:
$ python vol.py -f ~/memdump/infected.img hivelist Volatile Systems Volatility Framework 2.2 Virtual Physical Name ---------- ---------- ---- 0xe2084008 0x0fe6b008 \Device\HarddiskVolume1\Documents and Settings\pilou\Local Settings\Application Data\Microsoft\Windows\UsrClass.dat 0xe1d1fb60 0x0db99b60 \Device\HarddiskVolume1\Documents and Settings\pilou\NTUSER.DAT 0xe19d8380 0x0d091380 \Device\HarddiskVolume1\Documents and Settings\LocalService\Local Settings\Application Data\Microsoft\Windows\UsrClass.dat 0xe1c19508 0x0d644508 \Device\HarddiskVolume1\Documents and Settings\LocalService\NTUSER.DAT 0xe17206d0 0x0cad76d0 \Device\HarddiskVolume1\Documents and Settings\NetworkService\Local Settings\Application Data\Microsoft\Windows\UsrClass.dat 0xe19fb008 0x0d403008 \Device\HarddiskVolume1\Documents and Settings\NetworkService\NTUSER.DAT 0xe196c6b8 0x0a9ca6b8 \Device\HarddiskVolume1\WINDOWS\system32\config\software 0xe1599b60 0x04870b60 \Device\HarddiskVolume1\WINDOWS\system32\config\default 0xe196cb60 0x0a9cab60 \Device\HarddiskVolume1\WINDOWS\system32\config\SECURITY 0xe195eb60 0x0a6e2b60 \Device\HarddiskVolume1\WINDOWS\system32\config\SAM 0xe134f350 0x02f00350 [no name] 0xe1035b60 0x02aa3b60 \Device\HarddiskVolume1\WINDOWS\system32\config\system 0xe102e008 0x02a9d008 [no name] 0x806717a8 0x006717a8 [no name]
HKLM keys are under offset 0xe196c6b8:
$ python vol.py -f ~/memdump/infected.img printkey -o 0xe196c6b8 -K "Microsoft\Windows\CurrentVersion\Run" Volatile Systems Volatility Framework 2.2 Legend: (S) = Stable (V) = Volatile ---------------------------- Registry: User Specified Key name: Run (S) Last updated: 2013-02-18 21:07:49 Subkeys: Values: REG_SZ BluetoothAuthenticationAgent : (S) rundll32.exe bthprops.cpl,,BluetoothAuthenticationAgent REG_SZ SunJavaUpdateSched : (S) "C:\Program Files\Java\jre7\bin\jusched.exe" REG_SZ VMware User Process : (S) "C:\Program Files\VMware\VMware Tools\vmtoolsd.exe" -n vmusr REG_SZ Mcafee VShield : (S) mcrshl.exe
We can notice that the identified file (mcrshl.exe) appears in the startup registry keys so that it is automatically started.