WackoPicko/Stored-SQL-Injection
Jump to navigation
Jump to search
| You are here: | Stored SQL Injection
|
Description
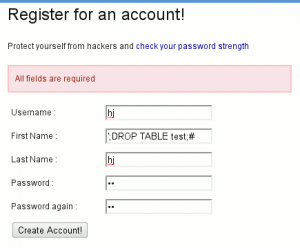
When users create an account, they are asked to supply their first name. This supplied value is then used unsanitized on a page that shows other users who have a similar first name. An attacker can exploit this vulnerability by creating a user with the name "';DROP TABLE users;#" then visiting the similar users page.
Proof of Concept

Note
Notice that you are unlikely to be able to realize this attack unless you use an old version of MySQL. Indeed, MySQL has now a protection mechanism that prevents from concatenating requests with a semi-column.
How to detect?
- See these tools.
- Refer to this article for more information on SQL injections.
How to protect against it?
Code
As we can see in the similar_login() function of the include/users.php script, the first request (tagged with the comment VULNERABLE REQUEST) is not properly sanitized):
function similar_login($login, $vuln = False)
{
if ($vuln)
{
/*** VULNERABLE REQUEST ***/
$query = "SELECT * from `users` where `firstname` like '%{$login}%' and firstname != '{$login}'";
}
else
{
/*** SANITIZED REQUEST ***/
$query = sprintf("SELECT * from `users` where `firstname` like '%%%s%%' and firstname != '%s'",
mysql_real_escape_string($login),
mysql_real_escape_string($login));
}
$res = mysql_query($query);
if ($res)
{
while ($row = mysql_fetch_assoc($res))
{
$to_ret[] = $row;
}
return $to_ret;
}
else
{
if ($vuln)
{
die(mysql_error());
}
return False;
}
}