PEB-Process-Environment-Block/BeingDebugged
| You are here | BeingDebugged
|
Description
Instead of calling IsDebuggerPresent(), some packers manually check the PEB (Process Environment Block) for the BeingDebugged flag.
| Field | Size | Offset relative to PEB |
|---|---|---|
| IsDebuggerPresent | BYTE | 0x2 |
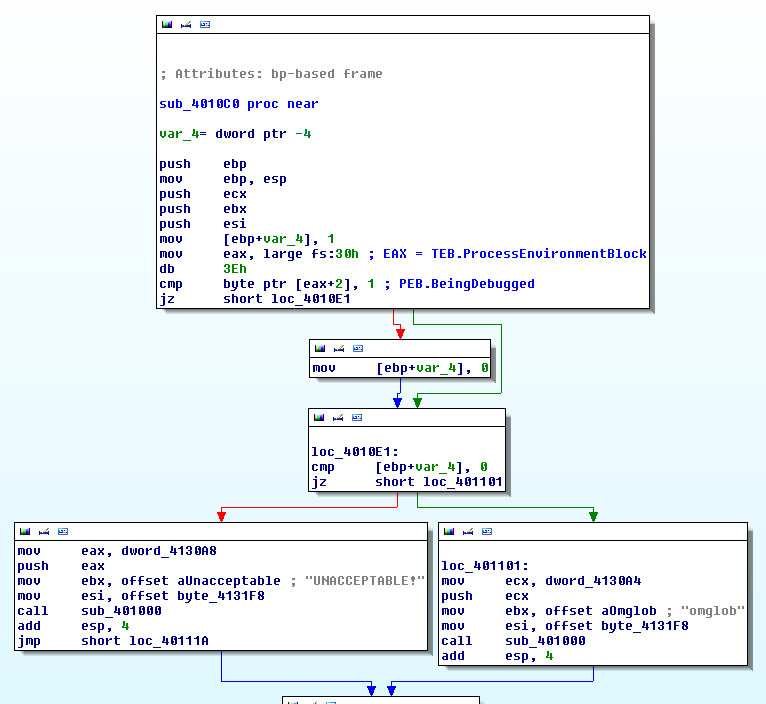
In the below example, fs:30h represents the PEB. It is saved to the EAX register at offset 0x4010CD. At offset 0x4010D3, the value 1 is compared to the offset 2 of the pointer to EAX:
.text:004010CD mov eax, large fs:30h ; PEB
.text:004010D3 db 3Eh ; IDA Pro display error (byte is actually used in next instruction)
.text:004010D3 cmp byte ptr [eax+2], 1 ; PEB.BeingDebugged
.text:004010D8 jz short loc_4010E1
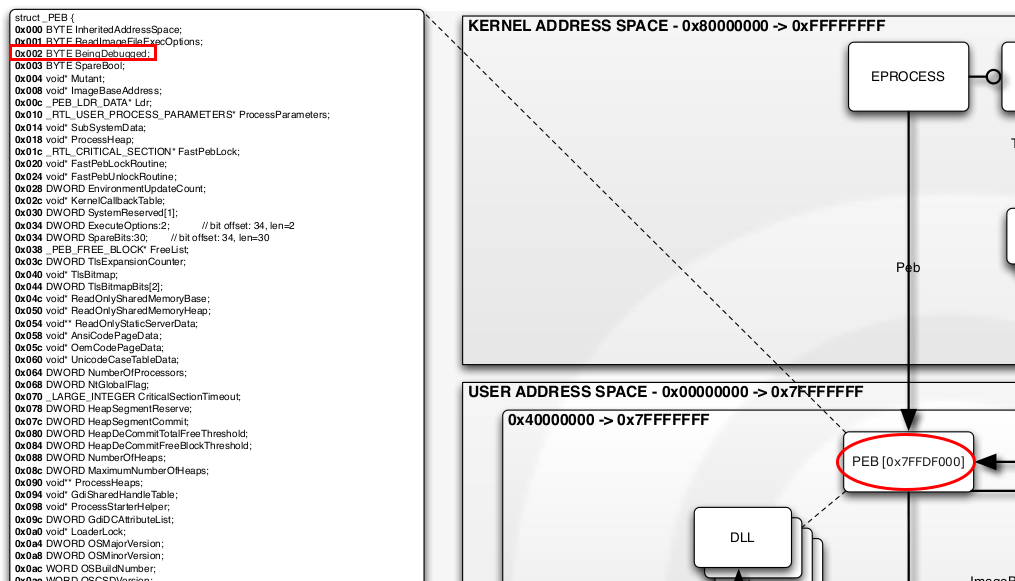
As depicted on the following extract showing the PEB structure, BeingDebugged lies at offset 0x002:
If byte ptr [eax+2] returns 1, it means the the program is being debugged and the jump at offset 0x4010D8 won't be taken.
Here is the full function:
Thwart the BeingDebugged chek
To thwart this check, you can:
- Control the jump by modifying the ZeroFlag (ZF) value before the jump instruction is executed
- Manually change the BeingDebugged flag value to zero
- In OllyDbg, use specific plugins (Hide Debugger, PhantOm, ...)
Below is an example that depicts how to manually change the BeingDebugged flag. We have the following code:
.text:00403554 mov eax, large fs:30h ; PEB struct loaded into EAX
.text:0040355A mov bl, [eax+2] ; BeingDebugged (offset 0x2 relative to PEB) moved to BL
.text:0040355D mov [ebp+var_1820], bl
.text:00403563 movsx eax, [ebp+var_1820]
.text:0040356A test eax, eax ; BeingDebugged check
.text:0040356C jz short loc_403573 ; If flag set to 0, program continues normally...
.text:0040356E call s_selfDelete ; ...else, program is deleted
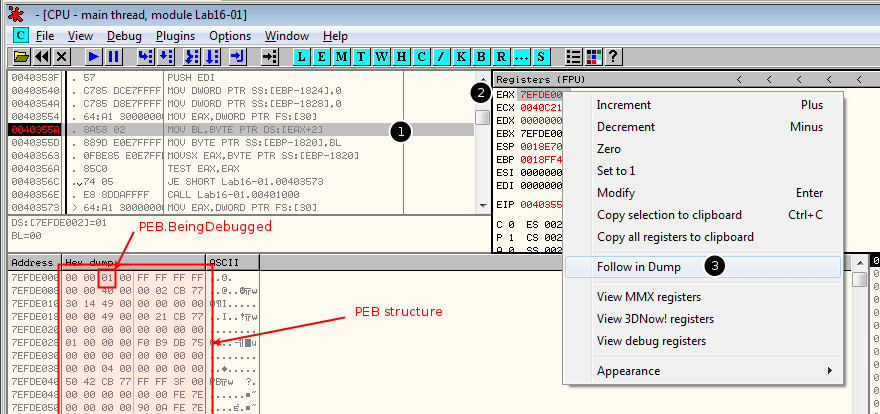
Let's open the malware in OllyDbg and set a breakpoint at 0x40355A. The PEB structure has been loaded into the EAX register. Right click on EAX and select "Follow in dump":
Notice that at offset 0x2 in the PEB structure, the value is 0x1. It corresponds to the BeingDebugged flag. Right click on it and select Binary > Fill with 00's.
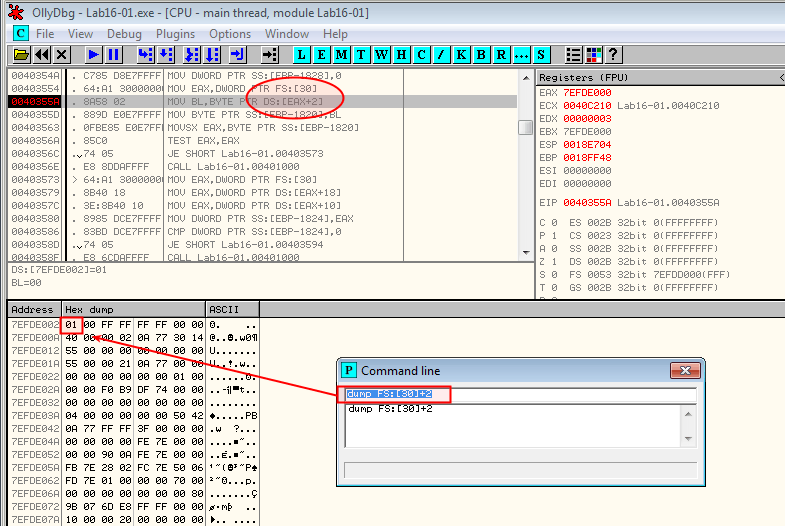
We could also have used the OllyDbg CommandLine plugin to directly reach the BeingDebugged flag: