SharifCTF-2016/hi
| You are here | hi (200 points)
|
Description
The file (HI2.exe) is a Windows 32 bit executable.
| MD5 | b40650660cc41ce34bd15530eb666b13 |
|---|---|
| SHA1 | 8dd906f847bc21078eeb95af69944a4d966eefec |
| SHA256 | c586a82b3cb26fd26b31a1242f0107ca870b1fc485cb7422414ce40f2fbcd597 |
| File | PE32 executable (console) Intel 80386, for MS Windows |
The description of the challenge says that the executable should be run in a very specific environment:
The Program is registerd for following system specification: - Processor type: Intel Itanium-based - Number of processors: 64 - Physical RAM => 128GB - OS version: 12.2 Build 1200
Running the executable
Ensure you have installed Redistribuable Visual C++ for Visual Studio 2015. When run, the executable shows the following output:
C:\sharifctf>HI2.exe Your system information is: OEM ID: 0 Number of processors: 1 Physical RAM => 2GB OS version: 6.1 Build 7601 The Program cannot run on this specification!
Analysis
Identify the packer
First of all, we should notice that the file is packed with VMProtect:
- Very few strings, limited to DLL names
- Very few imports (LoadLibrary, GetModuleHandle, ...)
- 8 sections, 2 of which named .vmp* (.vmp0, .vmp1)
- "The imports segment seems to be destroyed" warning message when loading executable into IDA-Pro
If not impossible to unpack, it seems very complex to reverse engineer VMProtect-ed executables. Rather than trying to unpack it, let's try to hook function calls in order to overwrite values returned by some functions.
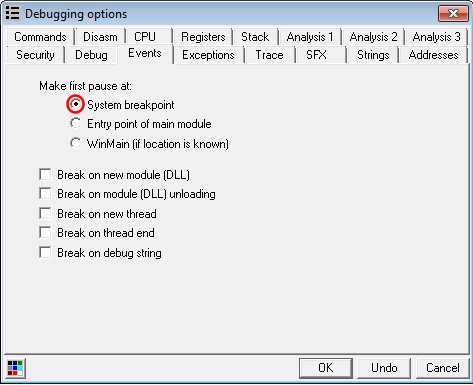
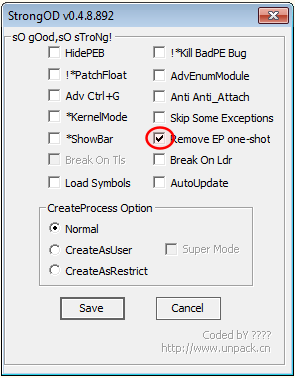
We will setup our debugging environment as follows:
Configure OllyDbg and StrongOD as follows:
| OllyDbg | StrongOD |
|---|---|
|
|
Identify interesting functions
We know that the program is gathering some information about our environment, likely provided by the following functions:
| Pre-requisite | Function |
|---|---|
| Processor type: Intel Itanium-based | GetSystemInfo |
| Number of processors: 64 | GetSystemInfo |
| Physical RAM => 128GB | GlobalMemoryStatusEx |
| OS version: 12.2 Build 1200 | GetVersion |
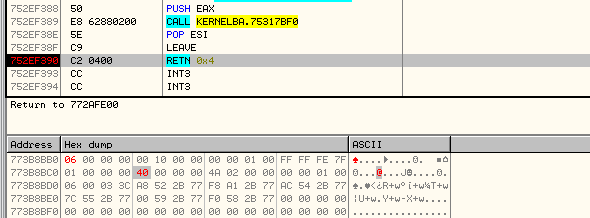
Hooking GetSystemInfo
The GetSystemInfo function has the following syntax:
void WINAPI GetSystemInfo(
_Out_ LPSYSTEM_INFO lpSystemInfo
);
Its parameter is actually a pointer to a SYSTEM_INFO structure, depicted as follows:
typedef struct _SYSTEM_INFO {
union {
DWORD dwOemId;
struct {
WORD wProcessorArchitecture;
WORD wReserved;
};
};
DWORD dwPageSize;
LPVOID lpMinimumApplicationAddress;
LPVOID lpMaximumApplicationAddress;
DWORD_PTR dwActiveProcessorMask;
DWORD dwNumberOfProcessors;
DWORD dwProcessorType;
DWORD dwAllocationGranularity;
WORD wProcessorLevel;
WORD wProcessorRevision;
} SYSTEM_INFO;
The 2 parameters we want to modify are highlighted in yellow and should have the following values:
| Parameter | Desired Value | Value (hex) |
|---|---|---|
| wProcessorArchitecture | Intel Itanium-based (PROCESSOR_ARCHITECTURE_IA64) | 0x6 |
| dwNumberOfProcessors | 64 processors | 0x40 |
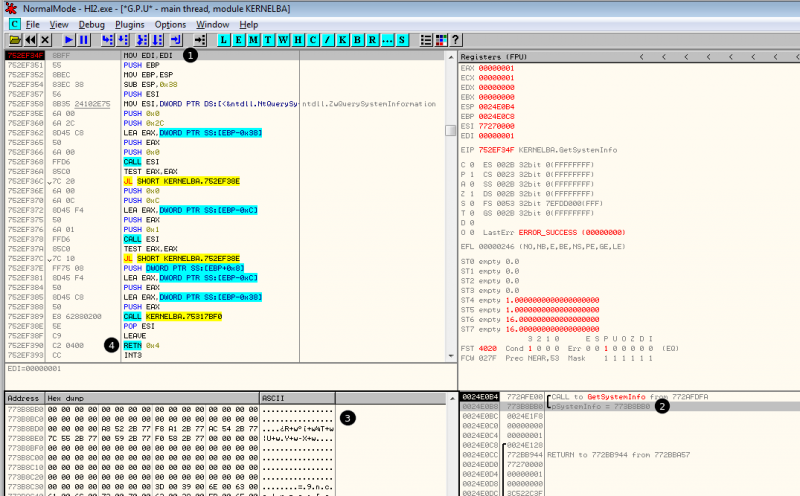
Now in OllyDbg, open the executable, press F9 once, then press Ctrl+G to search for GetSystemInfo, press F2 to set a software breakpoint and press F9 to reach the breakpoint.
Here is what it looks like once the breakpoint is reached:
Now at the end of the function, the structure can be modified as follows: ----------------------------------------- ------------- --------------
structure initial val. modified val.
----------------------------------------- ------------- --------------
typedef struct _SYSTEM_INFO {
union {
DWORD dwOemId;
struct {
WORD wProcessorArchitecture; 00 00 06 00
WORD wReserved; 00 00 00 00
};
};
DWORD dwPageSize; 00 10 00 00 00 10 00 00
LPVOID lpMinimumApplicationAddress; 00 00 01 00 00 00 01 00
LPVOID lpMaximumApplicationAddress; FF FF FE 7F FF FF FE 7F
DWORD_PTR dwActiveProcessorMask; 01 00 00 00 01 00 00 00
DWORD dwNumberOfProcessors; 01 00 00 00 40 00 00 00
DWORD dwProcessorType; 4A 02 00 00 4A 02 00 00
DWORD dwAllocationGranularity; 00 00 01 00 00 00 01 00
WORD wProcessorLevel; 06 00 06 00
WORD wProcessorRevision; 03 3C 03 3C
} SYSTEM_INFO;
----------------------------------------- ------------- --------------
|
|
Hooking GlobalMemoryStatusEx

Thank you for your comprehension.
Hooking GetVersion

Thank you for your comprehension.
Solution

Thank you for your comprehension.
Comments
Keywords: sharif 2016 challenge reversing