Archives/2013
Jump to navigation
Jump to search
|
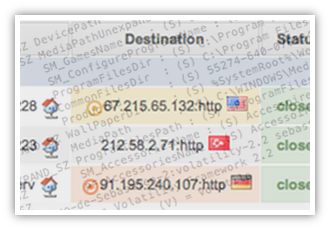
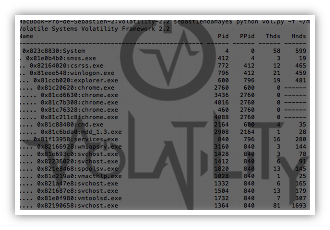
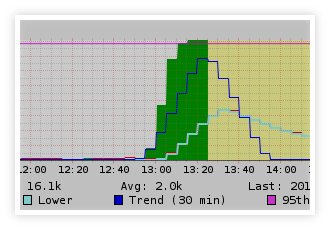
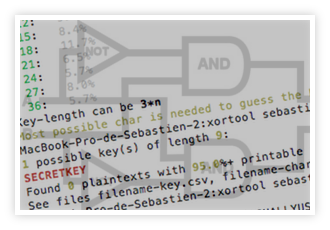
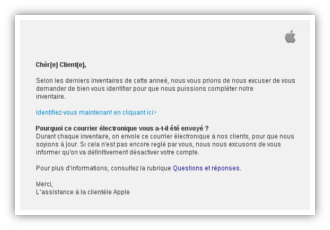
Fake Apple email campaign Wed, 13 Nov 2013 17:25:00 +0100 Analysis of a fake Apple email campaign (support.apple.com.fr.retail.ipad.verification2013.personalsetup.dalatgap.com). |
|
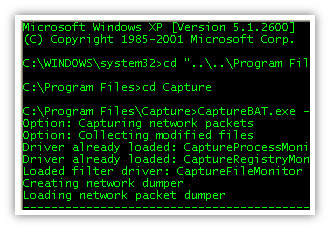
UPX (Ultimate Packer for eXecutables) Sun, 23 June 2013 22:45:00 +0200 UPX (Ultimate Packer for eXecutables) is one of the most famous packers for executables. Many malware are packed using UPX. |

|
Jsunpack-n, the CLI version of Jsunpack Sat, 09 Mar 2013 09:20:00 +0100 Jsunpack-n is a command-line Javascript unpacker that has more or less the same features as the Web version of Jsunpack |
|
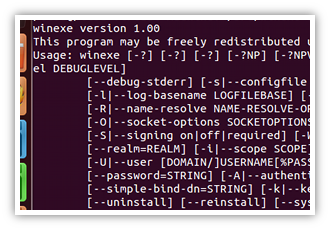
Winexe Fri, 3 August 2012 10:40:00 +0200 winexe remotely executes commands on WindowsNT/2000/XP/2003 systems from GNU/Linux (probably also other Unices capable to compile Samba4). |